| {"title": "Darktrace direct setup for Workbench", "url": "https://support.expel.io/hc/en-us/articles/1500002872742-Darktrace-direct-setup-for-Workbench", "date": "2021-02-17T20:44:51Z", "contents": "Darktrace is an Intrusion Detection Device (IDS) that leverages machine\nlearning to detect emerging threats, including insider threats, low-and-slow\nattacks, and automated viruses.\n\n#### In this article\n\n * Step 1: Enable console access\n\n * Step 2: Generate API credentials\n\n * Step 3: Configure the technology in Workbench\n\n * Step 4: Edit the device to add console access\n\n## Step 1: Enable console access\n\nExpel requires a Darktrace user account to review Alerts and Models within the\nconsole.\n\nHaving read-only access to the interface of your technology allows Expel to\ndig deeper during incident investigations. Our device health team uses this\naccess to investigate potential health issues with your tech.\n\n### Note\n\nExpel secures all login information our SOC analysts need about your devices\nin a MFA password product. Access to this login information is protected using\nour internal MFA processes. To learn more about the IP addresses all Expel\ntraffic comes from, go here.\n\n 1. From the menu located at the top left, select Add New User.\n\n 2. Username: Expel.\n\n 3. Password: set a temporary password — this is changed on initial login.\n\n 4. Account Permissions: select all available permissions, except User Admin or Group Admin. These can be left cleared.\n\n 5. Click OK.\n\n## Step 2: Generate API credentials\n\nTo integrate the technology with Workbench, we need to create secure\ncredentials to the API.\n\n### Note\n\nExpel secures all login information our SOC analysts need about your devices\nin a MFA password product. Access to this login information is protected using\nour internal MFA processes. To learn more about the IP addresses all Expel\ntraffic comes from, go here.\n\n 1. Log into the Darktrace console.\n\n 2. Navigate to Admin > System Config.\n\n 3. Near the bottom of the page, under API Token, click New.\n\n 4. The Darktrace system generates a Token and a Private Token. The Private Token can only be seen 1 time after the token pair is initially generated. Make note of the tokens for onboarding in Workbench. The system can only have 1 token pair, so if one already exists and you don't have a record of this, you must generate another token pair.\n\n### Caution\n\nIf a replacement Token pair is generated, other clients using the API must be\nreconfigured with the new credentials.\n\n## Step 3: Configure the technology in Workbench\n\nNow that we have the correct access configured and noted the credentials, we\ncan integrate your tech with Workbench.\n\n 1. In a new browser tab, login to https://workbench.expel.io.\n\n 2. On the console page, click Settings and click Security Devices.\n\n 3. At the top of the page, click Add Security Device.\n\n 4. Search for and select your technology.\n\n\n\n 5. Select an Assembler from the list. Select the assembler you set up in Getting connected to Expel Workbench.\n\n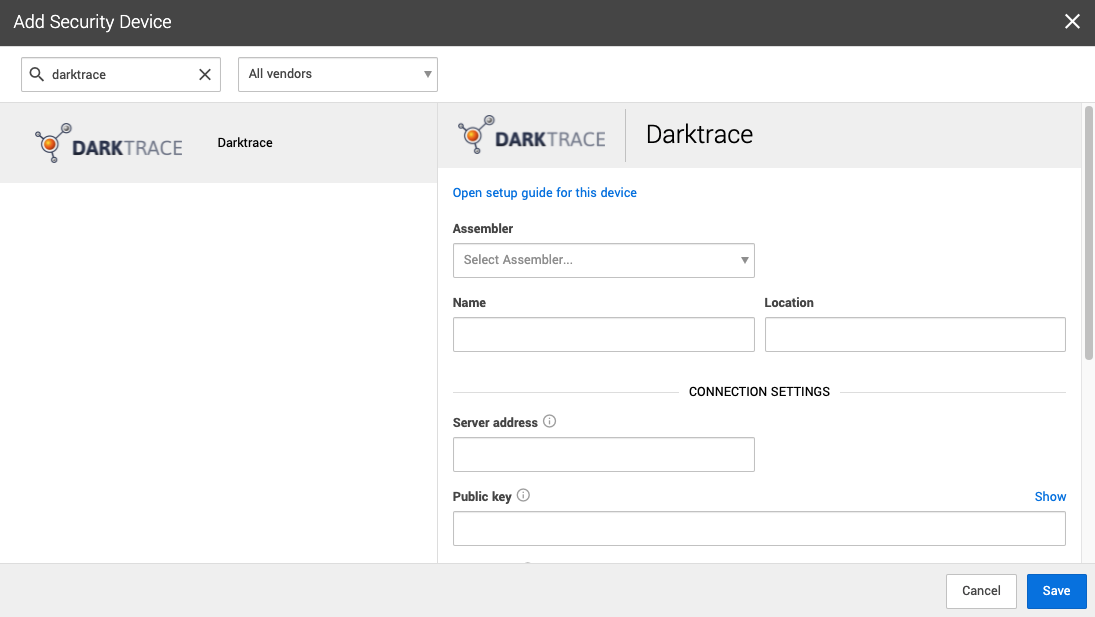\n\n * Type Name and Location.\n\n * For Server address, type the server address of the vendor’s server, which must include the port. For example: https://127.0.0.1:443 or myvendordevice.acme.com:443.\n\n * For Public key, type the API token used to authenticate to the device from Step 2.\n\n * For Private key, type the private token used to authenticate to the device from Step 2.\n\n 6. Click Save.\n\n 7. You can provide console access now or set it up later. Use the instructions below to set it up later.\n\nYou can see if the device is healthy on the Security Devices page. It may take\na few minutes to see the device listed as healthy.\n\nTo check if alerts are coming through, navigate to the Alerts Analysis page.\nScroll to the device you want to check and click View alerts. Switch to grid\nview, then check the list for device alerts. It can take 36 to 72 hours for\nalerts to appear after setup, as we tune your device.\n\n## Step 4: Edit the device to add console access\n\nExpel needs console access to your device to allow our SOC analysts to dig\ndeeper during incident investigations. Additionally, our engineering teams use\nthis access to investigate potential health issues, including proper alert\ningestion.\n\n### Note\n\nExpel secures all login information our SOC analysts need about your devices\nin a MFA password product. Access to this login information is protected using\nour internal MFA processes. To learn more about the IP addresses all Expel\ntraffic comes from, go here.\n\n 1. Open Workbench. Go to Organization Settings > Security Devices. Next to the device you just connected, click the down arrow and click Edit.\n\n 2. In the Console Login area, type these details:\n\n * Console URL: type the console URL from the Server address in the Connection Settings area above. At the end of the URL, type **/login**.\n\n * Username: type the user name you created above.\n\n * Password: type the password you created above.\n\n * Two-factor secret key (32-character code): depending on how your organization enforces log-ins, this field may not apply to you. In these cases, you can leave it blank. This field is optional and if you have questions or concerns, reach out to your engagement manager or to support.\n\n 3. Click Save.\n\n### Tip\n\nThis article was accurate at the time of writing, but changes happen. If you\nfind the instructions are outdated, leave a description in the comment field\nbelow and let us know!\n\n"} |